Security Series: Using PowerShell to Protect Your Private Cloud Infrastructure - Part 1
 In this first part of our three part series on using PowerShell to help secure your cloud infrastructure,
In this first part of our three part series on using PowerShell to help secure your cloud infrastructure, Yuri Diogenes and I (Tom Shinder) will talk about how you can secure data in flight within your cloud infrastructure using SMB 3.0 encryption. The ability to secure the data moving over the cloud infrastructure network is especially important when you consider the option of using file based storage for your virtual machine disk and configuration files. In fact, we consider this the preferred storage approach for your cloud infrastructure. This pattern is described in detail in the document set Cloud Infrastructure Solution for Enterprise IT. Note that this article was originally posted in the Hey Scripting Guy blog – I have added some additional cloud context in this post, however.
Yuri Diogenes and I (Tom Shinder) will talk about how you can secure data in flight within your cloud infrastructure using SMB 3.0 encryption. The ability to secure the data moving over the cloud infrastructure network is especially important when you consider the option of using file based storage for your virtual machine disk and configuration files. In fact, we consider this the preferred storage approach for your cloud infrastructure. This pattern is described in detail in the document set Cloud Infrastructure Solution for Enterprise IT. Note that this article was originally posted in the Hey Scripting Guy blog – I have added some additional cloud context in this post, however.
Before we get into the detail of how you can use PowerShell to enable this option, it’s important that we understand it’s  connection to cloud. This starts with the NIST definition of cloud computing. The NIST definition of cloud computing, which applies to all cloud deployment models (public cloud, private cloud, hybrid cloud, and community cloud) requires that a cloud solution enable the following essential characteristics.
connection to cloud. This starts with the NIST definition of cloud computing. The NIST definition of cloud computing, which applies to all cloud deployment models (public cloud, private cloud, hybrid cloud, and community cloud) requires that a cloud solution enable the following essential characteristics.
Note:
Source for this information: Overview of Private Cloud Architecture
- On-demand self-service The consumer of the cloud service should be able to obtain cloud services (such as compute, memory, network, and storage resources) by using a self-service mechanism (such as a web portal) so that acquiring the service does not require human intervention by the Cloud Service Provider (CSP).
- Broad network access The cloud solution should be accessible from almost anywhere (when required) and also be accessible from multiple form factors, such as smart phones, tablet computers, laptops, desktops, and any other form factor existing currently or in the future.
- Resource pooling The cloud solution should host a pool of shared resources that are provided to consumers of the cloud service. Resources such as compute, memory, network, and storage are allocated to consumers of the service from a shared pool. Resources are abstracted from their actual location, and consumers are unaware of the location of these resources.
- Rapid elasticity The cloud solution should provide rapid provisioning and release of resources as demand for the cloud service increases and decreases. This should be automatic and without the need of human intervention. In addition, the consumer of the cloud service should have the perception that there is an unlimited resource pool so that the service is able to meet demands for virtually any use case scenario.
- Metered services Sometimes referred to as the “pay-as-you-go” model, the cloud solution must make it possible to charge the consumer of the cloud service an amount that is based on actual use of cloud resources. Resource usage is monitored, reported, and controlled by the CSP and by service policy, which delivers billing transparency to both the CSP and the consumer of the service.
The cloud infrastructure network can be considered part of the pool networking resources that are required for any cloud solution. Tenant virtual machine disk and configuration files will be stored in a storage cluster that represented the pooled storage resources and access to that storage is done over a pooled (or shared) network connection. For this reason, security, through isolation, is essential. Therefore, beyond NIST essential characteristics, there is also a series of security concerns that private cloud tenants have concerning how a private cloud operates and how their data can be secure.
We advise that you read the following posts so that you’ll have a better understanding of the issues:
- Leveraging Windows Server 2012 Capabilities to Address Private Cloud Security Concerns – Part 1
- Leveraging Windows Server 2012 Capabilities to Address Private Cloud Security Concerns – Part 2
Network protection with Windows PowerShell
Of all the components of the cloud infrastructure that can be attacked, the most significant one is the network. Data of all types moves through the network. Virtual machines also could be in transit through the network when Hyper-V Replica-based replication is performed. Modern datacenters that host the compute and storage components of the cloud infrastructure depend on network connectivity to connect the tiers. These are only a few examples of how the network exposes vital corporate information to attack when the information is in flight.
There are a number of methods you can use to protect information from network-based attacks in your cloud infrastructure. Let’s take a look at a few options that are available to you by the platform capabilities in Windows Server 2012.
Scenario 1: Protecting against eavesdropping attack
As described in Leveraging Windows Server 2012 Capabilities to Address Private Cloud Security Concerns – Part 2, you need to be concerned about protecting information that moves through the cloud infrastructure network. This is especially important when you deploy a private cloud infrastructure and you host the compute component separately from the storage component. In this design, the private cloud infrastructure contains a compute Hyper-V failover cluster and a storage cluster. The virtual machines run on the Hyper-V cluster and the virtual machine disk and configuration files are stored in the storage cluster. The virtual machine disk and configuration files are exposed to the compute cluster as file-based storage.
In this scenario, all information contained in the virtual machines moves over the network between the storage and compute clusters. If an attacker gains access to the network that provides the file-based storage to the compute cluster, that attacker can potentially have access to all information contained in all virtual machines. For this reason, it’s critical that the information on this storage network be encrypted.
There are several options available when it comes to enabling network encryption. One is IPsec. However, not all scenarios lend themselves to the overhead and complexity of IPsec protection. For example, a file server might contains dozens or even hundreds of shares. However, there might be only three or four shares that contain information that requires network encryption. All the other shares can be accessed and transmitted over the network in the clear. IPsec doesn’t support this scenario. To get this level of granularity, you need to use something other than IPsec.
The good news is that “something” is Windows Server 2012 SMB 3.0 encryption. SMB 3.0 is the file sharing protocol used by Windows Server 2012, and it includes functionality that wasn’t available in previous versions. One of these features is transparent SMB encryption, which enables you to enforce network encryption on a per-folder or per-server basis.
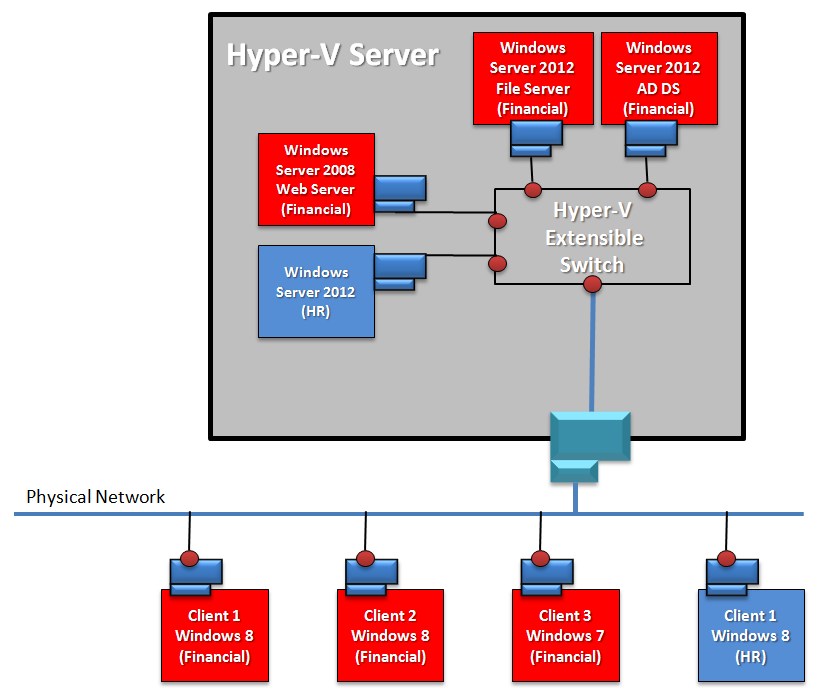
To see how SMB encryption works, let’s take a look at the network topology described in the following image.
Scenario definition: Contoso has a cloud infrastructure, and one of the tenants (in this example, the finance department) has a folder that contains PII data. This data is already encrypted when at rest, but they also require that the content is encrypted while in transit.
Scenario constraint: The finance department tenant has one workstation running Windows 7. This workstation won’t be able to access this folder because Windows 7 does not support SMB encryption. This is by design—only Windows Server 2012 and Windows 8 support SMB 3.0 encryption.
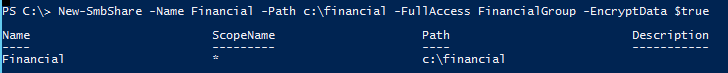
The following Windows PowerShell command can be used to enable encryption on a specific file share on the Windows Server 2012 file server:
You can use the New-SmbShare cmdlet to create the share if it’s not already in place. Notice that the EncryptionData $true is the parameter you use to set the encryption attribute for this folder. If the share already exists, you can use the following command:
Set-SmbShare –Name <sharedfoldername> -EncryptData $true
You can discover the current encryption state of a share by using the Get-SMBShare command:
Additional tips
If you want to enable network encryption for all file shares on a server, you can use the following command:
Set-SmbServerConfiguration –EncryptData $true
Keep in mind that only Windows Server 2012 and Windows 8 can access shares that require network encryption. You might want to make the shares that require network encryption available to down-level operating systems. In this scenario, unencrypted network access is available to clients running Windows 7 (and earlier). To enable this type of configuration, you can use the command:
Set-SmbServerConfiguration –RejectUnencryptedAccess $false
This example focused on a file server for users in the finance department to simplify the scenario for demonstration purposes. When thinking about how this feature is used in a cloud infrastructure, the best use is when you provide a compute failover cluster access to file-share based storage over SMB 3.0. This design pattern enables you to separately scale compute and storage, and it provides performance and security similar to or better than that found in a traditional iSCSI or Fibre Channel SAN environment.
In this first blog of our three part series, we defined the essential characteristics of cloud computing, briefly discussed some cloud security challenges, and started exploring network protection by using platform capabilities in Windows Server 2012. The next blog in this series will discuss protection against rogue DHCP servers. See you next time!
HTH,
Yuri Diogenes
Senior Technical Writer, STB CSI
Solutions Team
Tom Shinder
tomsh@microsoft.com
Principal Knowledge Engineer, SCD iX Solutions Group
Follow me on Twitter: https://twitter.com/tshinder
Facebook: https://www.facebook.com/tshinder