Introducing OMS DNS Analytics
Summary: Use DNS Analytics to get security, performance- and operations-related insights into DNS infrastructure.
Hi everyone, Abhave Sharma here, and today I’m excited to announce that DNS Analytics is available in Public Preview. In this post, I’ll take you through some of the cool capabilities that DNS Analytics provides, such as identification of clients resolving to malicious domains, stale resource records, popular domains etc., without any pre-configuration.
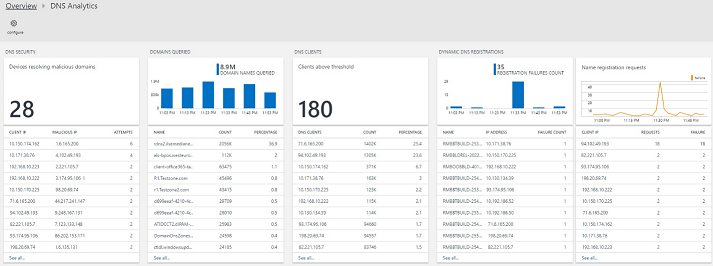
Communication with malicious domains
By using Microsoft threat intelligence feeds, DNS Analytics can detect client IPs that are trying to access the malicious domains. In many cases, malware-infected devices “dial out” to the “command and control” center of a malicious domain by resolving the malware domain name. In the following example, DNS Analytics detected that the communication was done with an IRCbot.
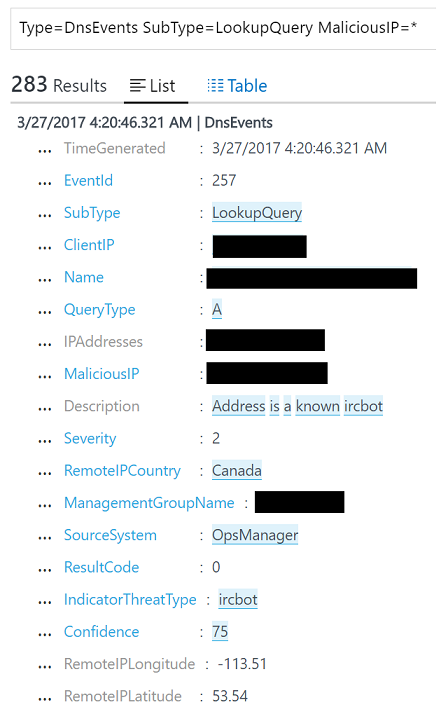
The solution enables you to identify the client IP that initiated this communication, the domain name resolving to the malicious IP, the IP addresses the domain name resolves to, the malicious IP address, the severity of the issue, the reason for blacklisting the malicious IP, and the detection time.
Note: Live IP addresses were removed from this screenshot for privacy purpose.
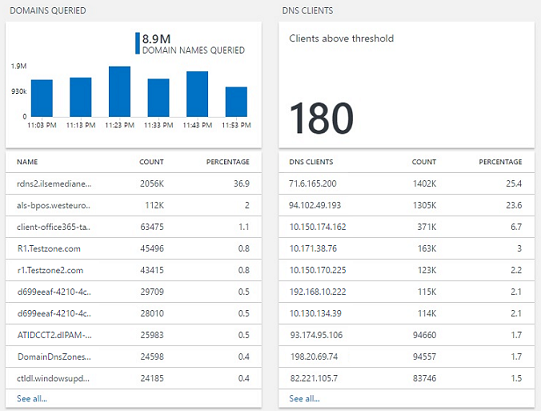
Identify frequently queried domain names and talkative DNS clients
The solution provides a view into the domain names that DNS clients in the enterprise environment frequently query. You can view the list of all the queried domain names and drill-down into the lookup request details of a domain name in Log Search.
The DNS client blade reports clients that breach the threshold for number of queries in the chosen period of time. You can view the list of all DNS clients and the details of the queries that they make in Log Search.
Track dynamic DNS registrations
The solution tracks the DNS update requests from the different clients and whether the requests were successful.
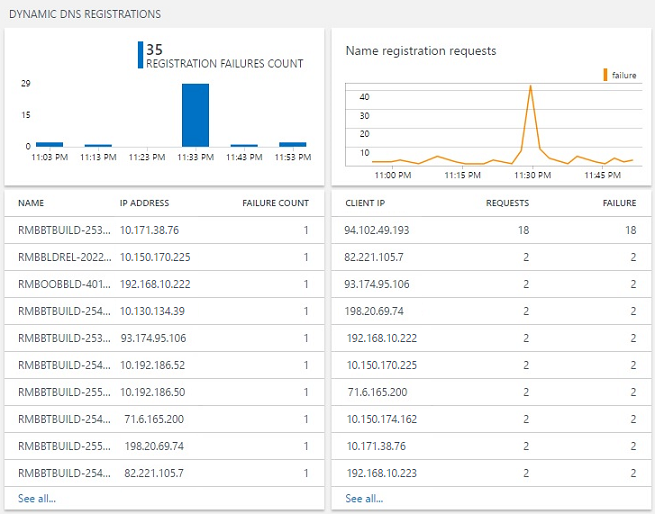
You can then use this information to find the root cause of the registration failure: find the zone that is authoritative for the name that the client is trying to update, and use the solution to check the inventory information of that zone. Verify whether the dynamic update for the zone is enabled and check whether the zone is configured for secure dynamic update.
Pin-point stale resource records
The solution provides a list of all the stale resource records for the chosen period of time in Log Search. This list contains the resource record name, resource record type, the associated DNS server, record generation time, and the zone name. Based on this information, the DNS administrator can remove the stale entries from the DNS servers.
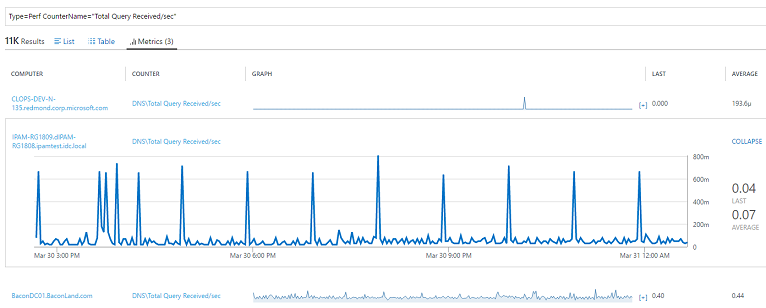
Understand load on DNS servers and zones
An understanding of the load is essential for capacity planning and performance of the DNS infrastructure. You can understand how the DNS load is distributed across your DNS servers and zones by observing the trends of DNS query rates for each server and zone.
Centralized view of DNS logs
View all the DNS events and inventory-related data of the DNS servers that the solution manages in Log Search. Type=DnsEvents query will list the log data for all events that are related to lookup query, dynamic registration, and configuration change. Type= DnsInventory query will list the log data for DNS servers, DNS zones, and resource records. Use the Log Search facet controls to analyze the data to generate actionable insights and construct meaningful reports.
How does the solution work?
The solution collects three types of data from the DNS servers on which the OMS agents are installed: DNS inventory, DNS events, and DNS performance counters. The inventory-related data (number of DNS servers, zones, resource records etc.) is collected by running the DNS PowerShell cmdlets. The event-related data (lookup queries, dynamic registrations, and configuration change) is collected from the Analytic and Audit logs provided by enhanced DNS logging and diagnostics available in Windows Server 2012 R2 and later.
This data is then uploaded to OMS, processed by the service, and presented to you on solution dashboard.
Get started
You can find detailed instructions about how to get started with DNS Analytics.
Get a free Microsoft Operations Management Suite (#MSOMS) subscription so that you can start using DNS Analytics. You can also get a free subscription for Microsoft Azure. I invite you to follow the Microsoft IT Management Twitter and the Microsoft OMS Facebook site. You can also try a fully hydrated demo environment.
Please send your feedback
There are a few different routes to give feedback:
- UserVoice: Post ideas for DNS Analytics features to work on. Visit the OMS UserVoice page.
- Join our cohorts: We’re always interested in having new customers join our cohorts to get early access to new features and help us improve DNS Analytics going forward. If you are interested in joining our cohorts, simply fill out this quick survey.
Abhave Sharma
Program Manager
Microsoft Operations Management Suite
Comments
- Anonymous
May 02, 2017
thank you - Anonymous
May 04, 2017
The comment has been removed