Securing Office 365 with Conditional Access in the new Azure portal
Hello everyone,
I have been getting a lot of requests from my customers on how to use the new Azure Active Directory (AAD) Conditional Access (CA) controls to secure Office 365. The recently announced new conditional access capabilities in the new Azure portal provide more flexible and powerful polices to enable productivity while ensuring security.
For this post, I will provide instructions to allow access to Exchange Online only to trusted platforms. Keep in mind, these instructions can also be used to secure other Office 365 services as well as any 3rd party application integrated with Azure AD.
Scenario
Only allow trusted platforms to have access to Exchange Online. (In this example, the policies will block macOS and allow Android, iOS, Windows Phone, and Windows).
Requirements
- Azure Active Directory Premium
- Office 365 Exchange Online
- A Global Administrator account
- Modern Authentication enabled and supported apps
IT Admin Walk-through - Creating the Azure Active Directory Conditional Access policies
Go to the new Azure AD Portal and login with a Global Administrator account. Click on "Conditional Access" in the AAD blade.
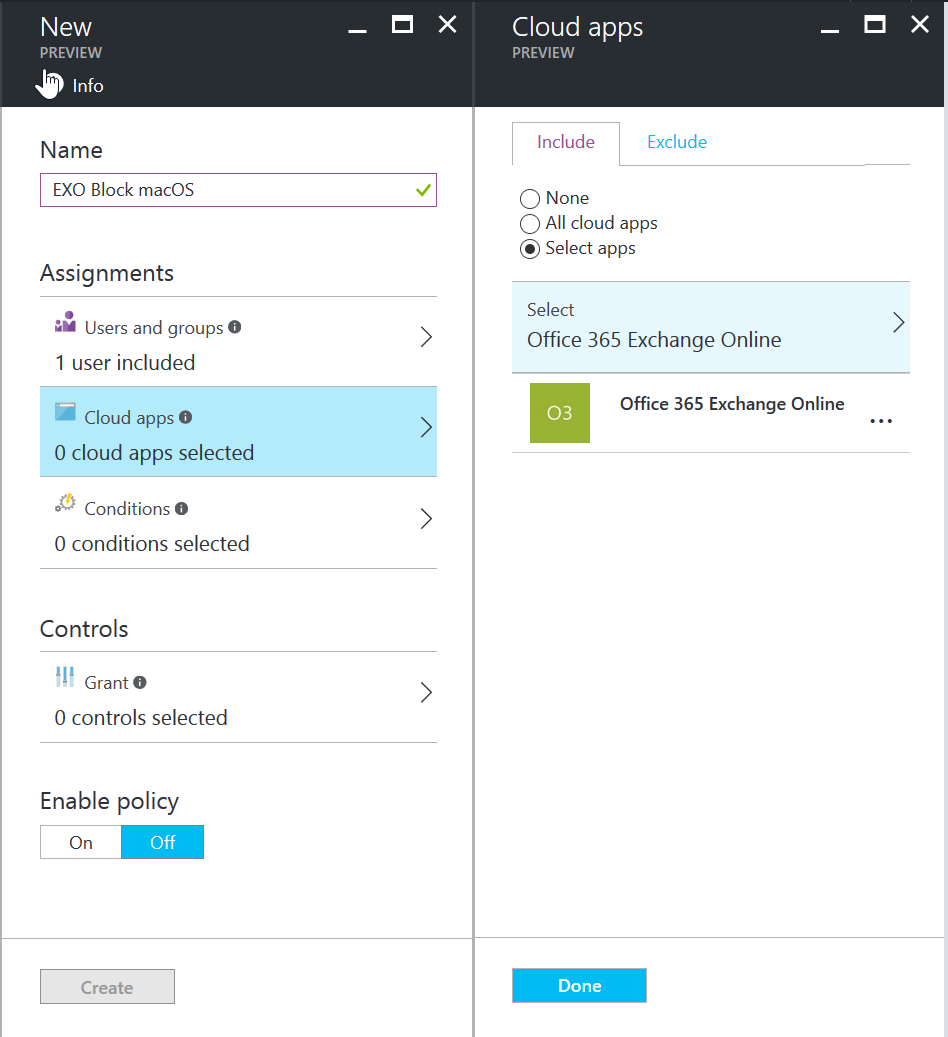
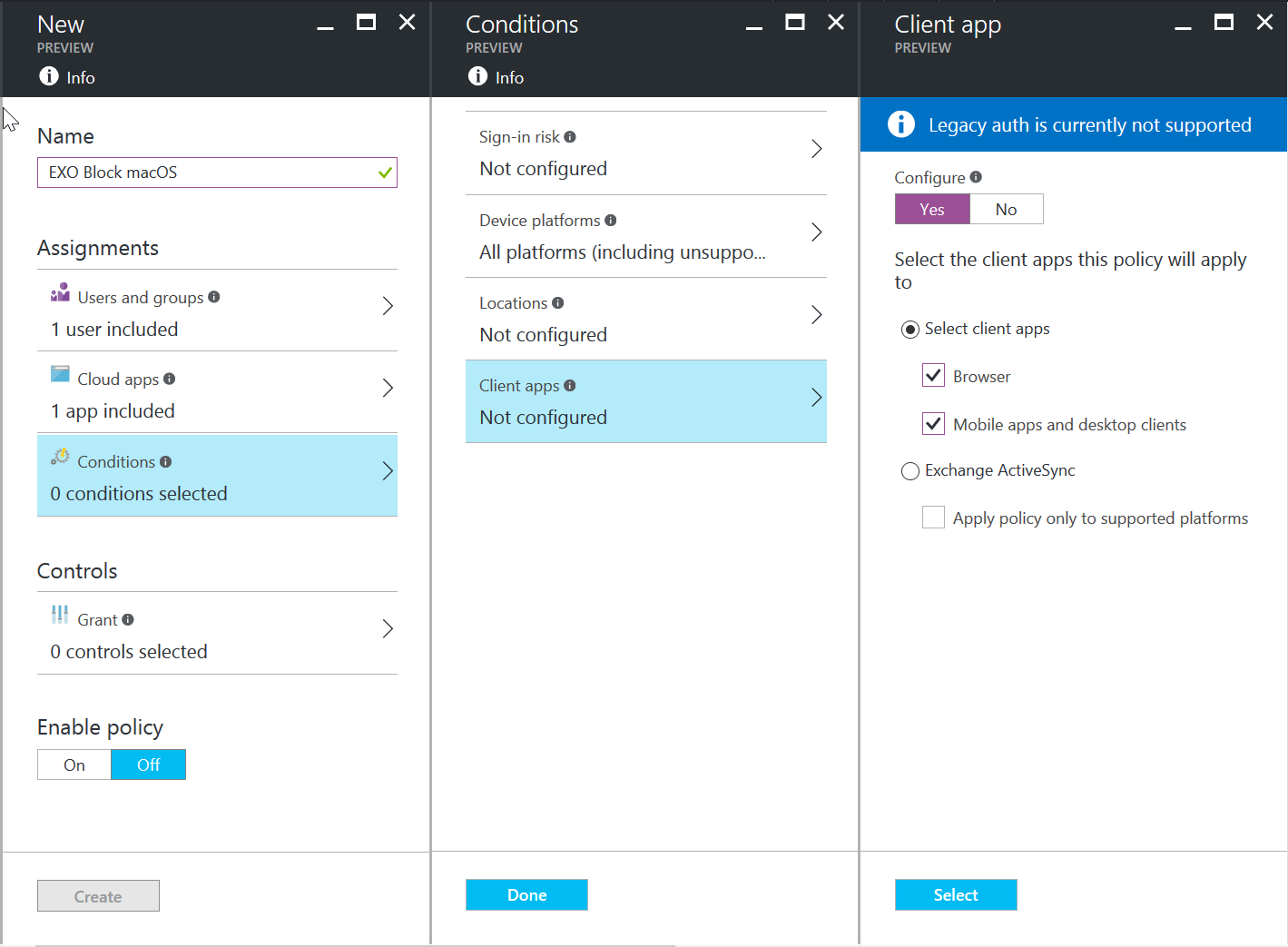
Create a new policy and select a user or group of users. In this example, I created a new policy called “EXO Block macOS” and selected NestorW to test my policy.
Select “Office 365 Exchange Online”
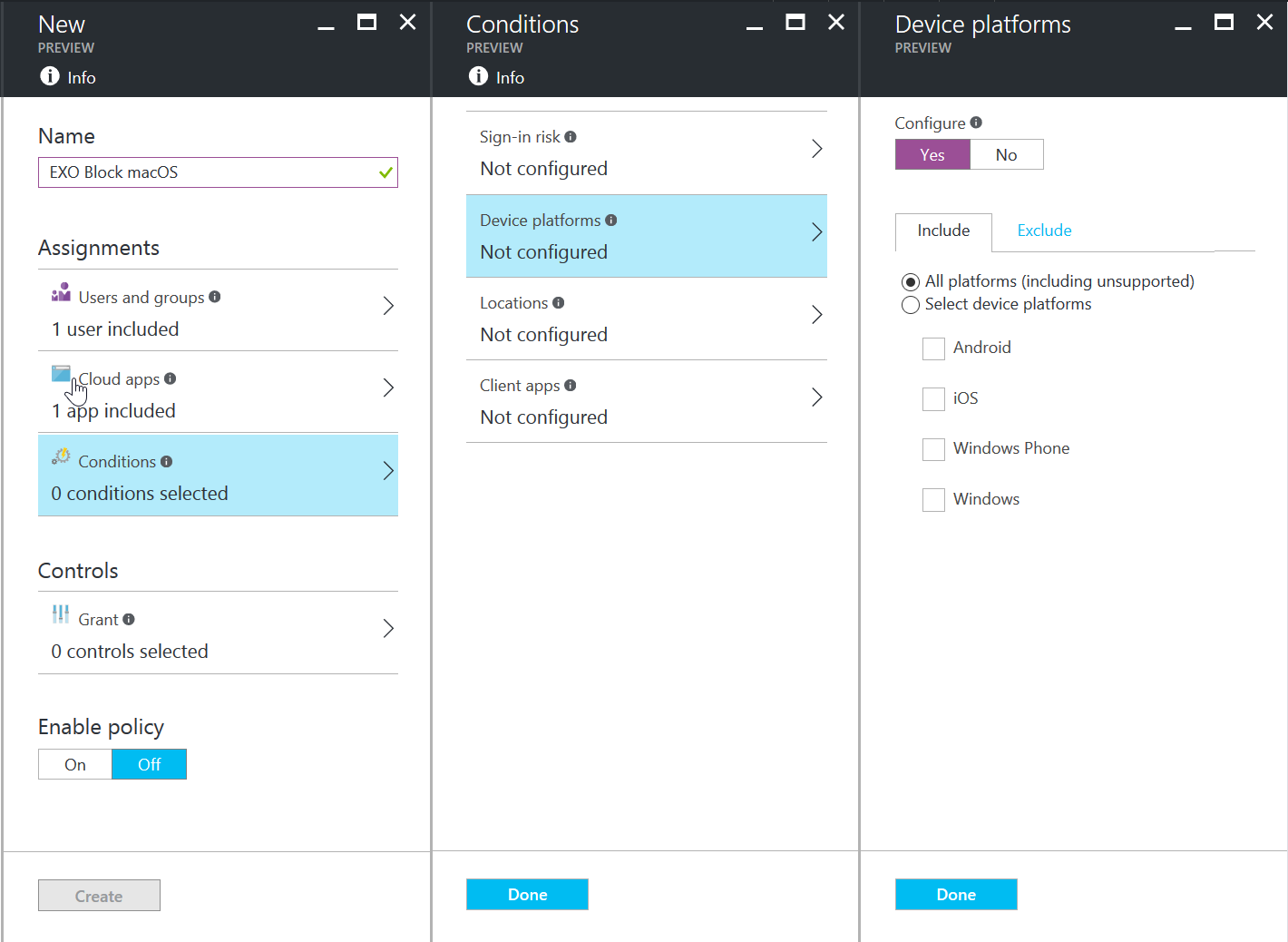
Select the Conditions to Include “All platforms (including unsupported)”
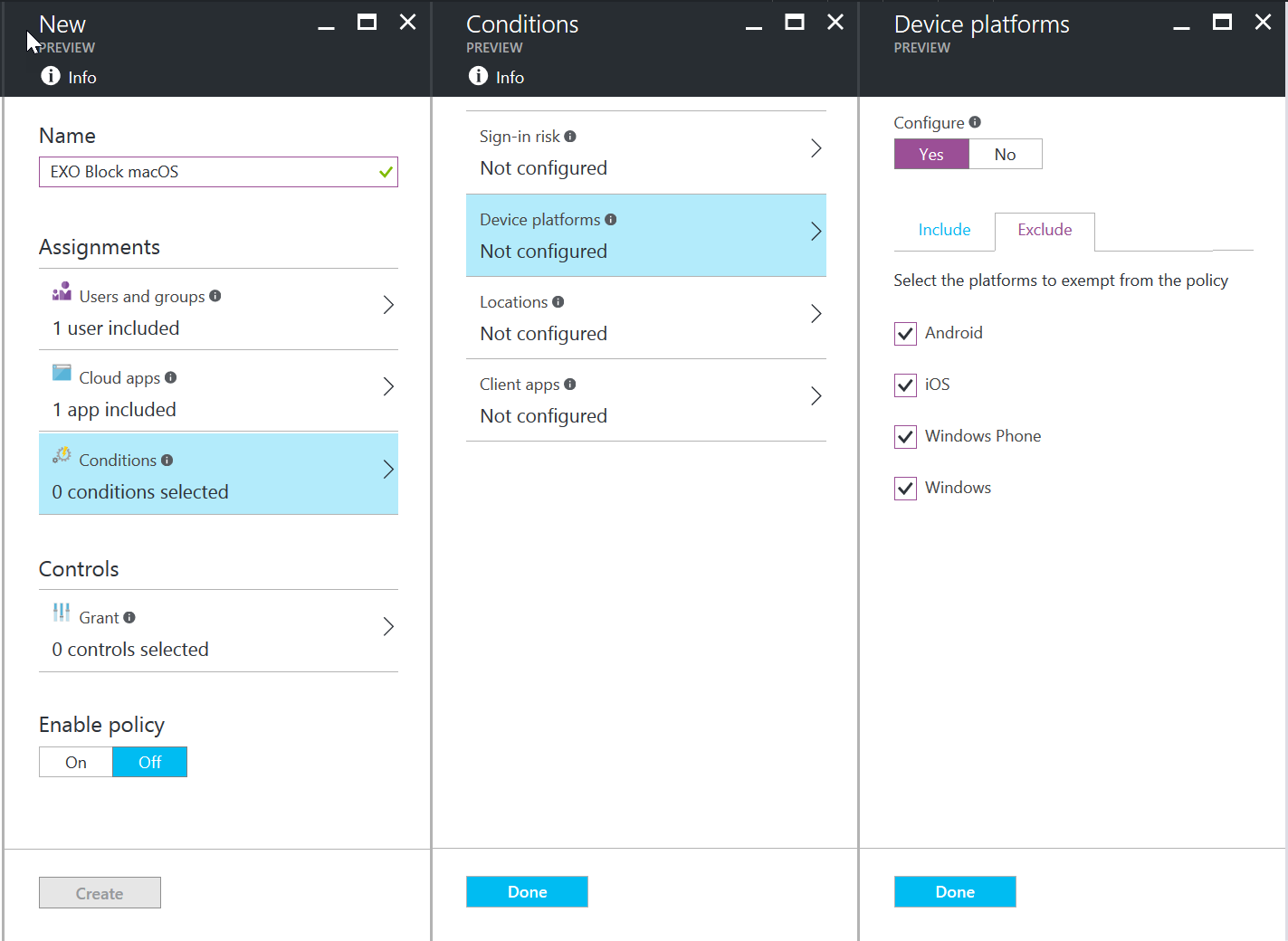
Click on the “Exclude” tab and select Android, iOS, Windows Phone, and Windows. Click on Done and Done to save the Conditions options.
For Client apps, configure the option for Browser and Mobile apps and desktop clients.
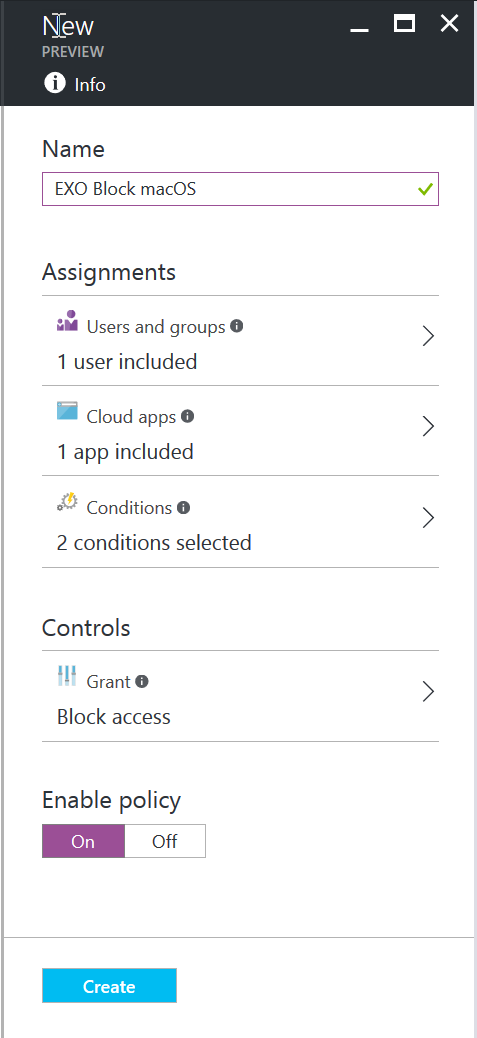
Lastly, select the controls to Block access. Enable the policy and click on Create.
User Experience
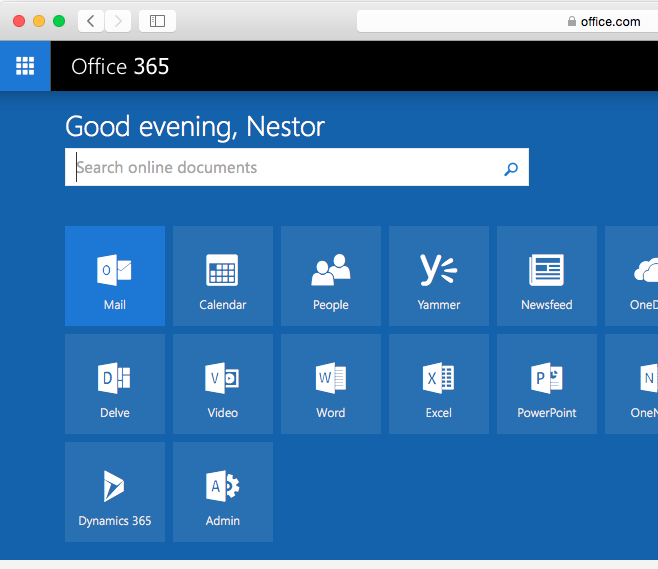
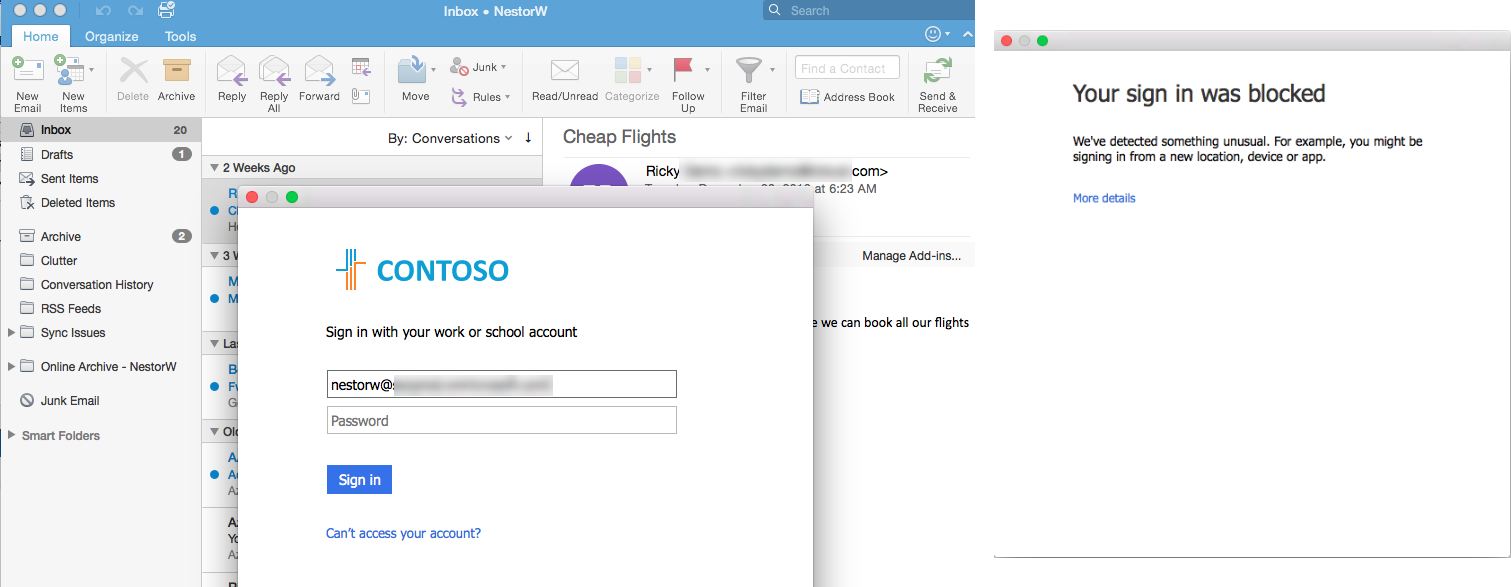
First on Safari on Mac OS X, the user can go to portal.office.com and still get access to other O365 apps.
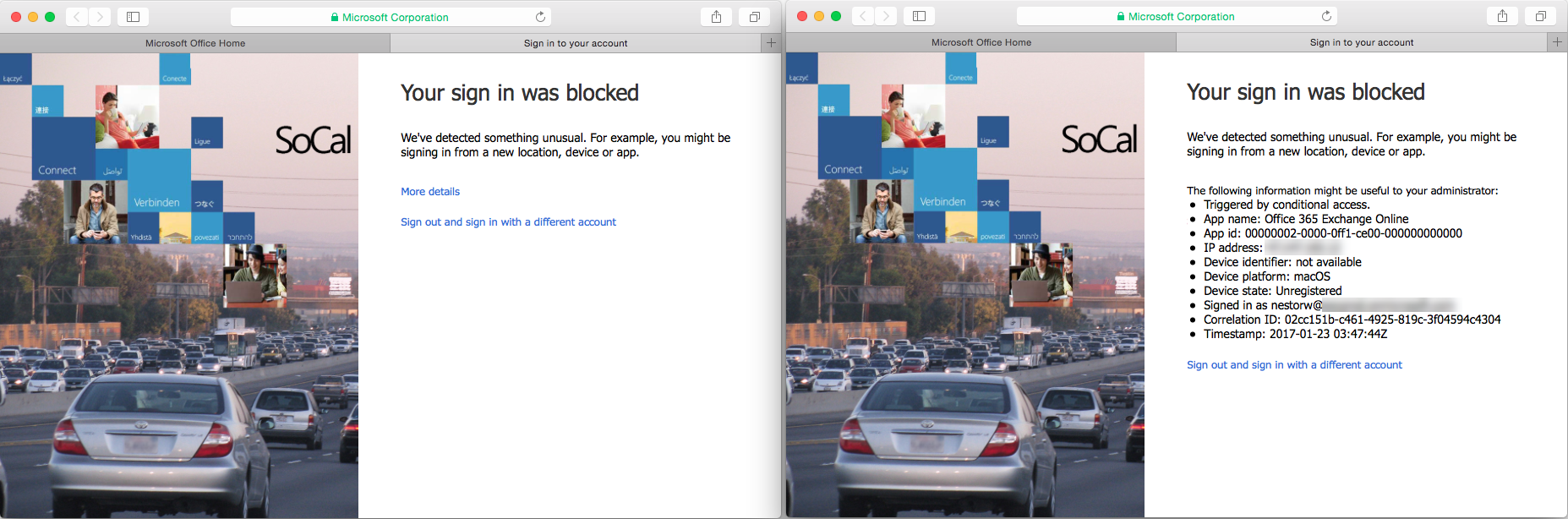
Once the user goes to Mail then access will be blocked.
User experience on Microsoft Office 2016 for Mac. After a successful sign in the end user is prompted with an error message and is blocked.
That's it! The end user can use Exchange Online on Android, iOS, Windows Phone, and Windows but will be blocked on macOS. I hope this was helpful. In my next post, I will document how IT can build policies to allow users access to Exchange Online using Office 2016 for Mac with MFA enabled. Please reach out to me if you have any questions.
Regards,
Rick Cajudo (Twitter: @rickcajudo)
References
- The #AzureAD admin experience in the new Azure portal is now in public preview!
- Conditional Access now in the new Azure portal
- Conditional access in Azure Active Directory - preview