Azure Active Directory + O365 Conditional Access Scenarios Explained
Hi everyone, with all the cross integration between Azure Active Directory and Office 365 it time to explain these conditional access in detail. While Office 365 offers a level of controls by service, Azure Active Directory and Microsoft Intune can come over the top of those services an provide further controls or leverage conditional access controls configured already in O365.
Let’s dive into a few of these scenarios.
Device/App based conditional access with Microsoft Intune
Microsoft Intune offers various levels of conditional access based on device and app state. Conditional access policies may be set on whether or not a device is enrolled with Intune (i.e. MDM) or if the designated application is being used to access email (e.g. Outlook app vs. native email apps). Additional controls of may be applied based on what type of app is allowed to access the service be that a web browser or a native application. There are even application policies that may be applied to a mobile app to further control where data is moved, saved, etc. (i.e. Intune Mobile Application Management).
There are a wealth of conditional access controls available within Intune that may be used to protect company information from leaking. The device based controls go beyond O365 services to 3rd party mobile apps, customer apps, on premises web apps, and 3rd party SaaS applications.
Intune also has integration with a number of 3rd party security and mobile defense partners such as Lookout, Citrix, Cisco ISE, and Skycure
- More details here on O365 conditional access: https://docs.microsoft.com/en-us/intune/deploy-use/restrict-access-to-email-and-o365-services-with-microsoft-intune
- More details here about Azure AD Conditional Access: https://docs.microsoft.com/en-us/azure/active-directory/active-directory-conditional-access
O365 per app Conditional Access
One of many Azure Active Directory (Azure AD) differentiators from other identity providers (idps) is Azure AD can carve up O365 and apply Conditional Access (CA) policies on a service by service basis. For example, a CA policy such as requiring Multi-Factor Authentication (MFA) can be applied to Exchange Online while leaving SharePoint Online without a CA policy (e.g. not prompt for MFA or allow a certain device type to access). Azure AD can also apply conditional access policies on a per app basis for 3rd party SaaS apps and internal web apps via Azure AD Application Proxy.
- More details about Azure AD Conditional Access here: https://docs.microsoft.com/en-us/azure/active-directory/active-directory-conditional-access
SharePoint Online limited access
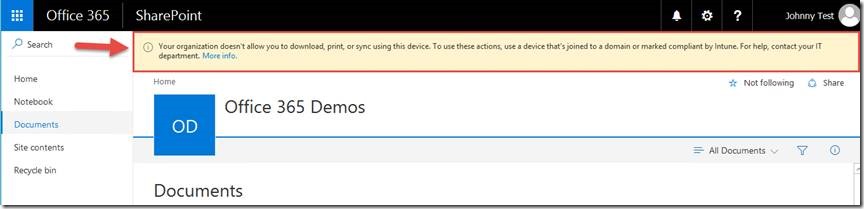
This is a new feature currently in preview, however it’s a form of Conditional Access. Coupled with Azure AD Conditional Access policies, SharePoint Online access may be granted to browser based sessions with additional service/app restrictions configured through SharePoint Online. For example, if the policies are configured in both services, and an end user attempts to access SharePoint Online on a device that isn’t enrolled with Microsoft Intune and/or SharePoint Online site is viewed as an unsecured device, the user will only have read only access. In addition, download, print, and sync may be blocked as well. This type of policy allows users to continue to be productive regardless of what type of device or browser being utilized. Note: SharePoint on-prem is not supported.
The following is an example from my environment using Tor browser. The user will receive a notification at the top of the SharePoint Online Page when accessed from an unsecured device or browser and block downloading and printing of content. In addition a conditional access policy in Azure AD can be set to block access completely if needed.
- More details here: https://blogs.technet.microsoft.com/enterprisemobility/2017/03/09/conditional-access-limited-access-policies-for-sharepoint-are-in-public-preview/
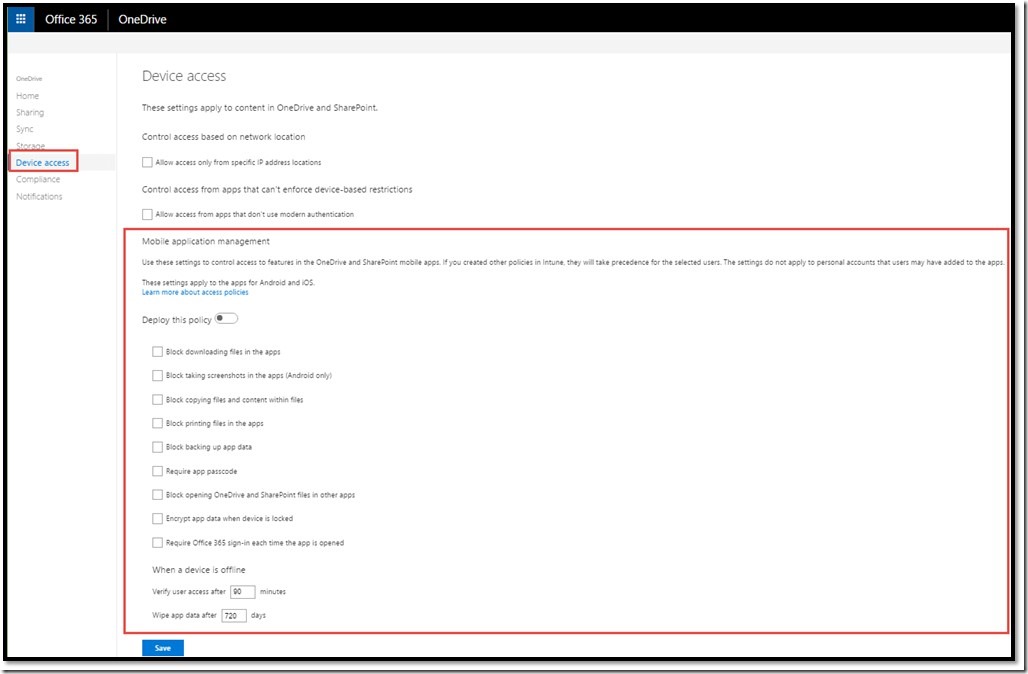
OneDrive for Business and Mobile Application Management (MAM) in service features
A number of new device based access settings have been deployed directly to the OneDrive for Business (OD4B) service. One of those is Mobile Application Management (MAM). To utilize the MAM settings within OD4B an Intune license is required. The MAM settings also are one in the same as those in Intune which means that if they’re enabled in OD4B they’ll show up in Intune and vice versa. However, MAM settings in Intune will override those set in OD4B admin portal.
- More details here: https://support.office.com/en-us/article/Control-access-to-features-in-the-OneDrive-and-SharePoint-mobile-apps-d25713bb-5cf8-4874-9b5b-e8bee3b94f13?ui=en-US&rs=en-US&ad=US
In summary, these features are all market differentiators and allow O365 and SPE or EMS customers to create unique sign-on and device based access scenarios on a per app basis across O365, 3rd party SaaS apps, and on-premises web applications.
When utilizing Office 365 I encourage everyone to consider the Enterprise Mobility and Security offering.