Azure AD Application Proxy Connector connectivity issues with a proxy
Sharing this article with you after a customer faced that issue and thought it would help many others which are using a proxy in their environment.
Symptom
After having installed the Azure AD Application Proxy Connector as explained on the MSDN site, if everything went well, the server where the connector has been installed should appear on Azure Portal.
Here is an example when it goes well (from Azure Portal > Active Directory > “your directory” > Configure > Application Proxy > “View Connector”):
But for my customer, instead of seen his connector server listed here, he got a blank list.
Troubleshooting
First thing which came to my mind was the firewall ports which have to be opened.You’ll find the complete port list here.
After asking to the network team to open all the needed ports, the connector wasn’t still listed on Azure Portal.
Azure AD Application Proxy logs are logged in the event log. While checking it we saw a repeated error 12015 saying that the configuration download failed. It must be something related to network…
Strange… Oh we forgot about the fact they are using a proxy for outbound internet connectivity! and just for information, that customer didn’t allow connectivity to Internet without going through that proxy. Then I thought, oh I found a very good blog explaining EXACTLY the same issue as mine. His solution was to modify Azure AD Application Proxy configuration file (ApplicationProxyConnectorService.exe.config) but modifying that config file makes the AAD AP service not starting anymore… maybe the dev team has changed how the config file is handled… anyway I needed another solution… back to troubleshooting!
The correct proxy server has been set in IE but the connector was still generating errors in logs.
We monitored the network to verify what happening. Result: the connector was trying to access to Internet directly without going through the proxy server specified in Internet Explorer!
Usually when applications are not using IE proxy settings, they use Winhttp proxy settings, which in our case wasn’t set on the server.
To set Winhttp proxy by command line, we need to use netsh. Here’s an example to set a proxy:
netsh winhttp set proxy proxy-server=”proxy.contoso.local:8080”
We set Winhttp proxy on that server but unfortunately it was still not working and same errors were logged.
Solution
Our problem is now clear: the connector is not using our proxy settings, neither from IE nor from Winhttp. It means the last thing we can do is to set to the service account used by Azure AD Application Proxy service the proxy settings needed to access Internet.
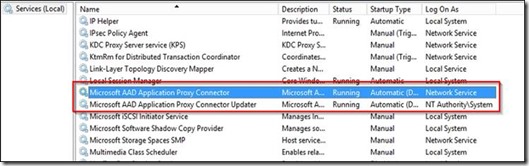
Azure AD Application Proxy has 2 services: one for the connector and one for updating the connector. The first one is using “Network Service” account, the latter “System” account.
To set proxy settings to those accounts (which can not be used to login to a Windows session), please follow that procedure:
- Download PSTools from https://technet.microsoft.com/ja-jp/sysinternals/bb897553.aspx
- Extract PSTools somewhere on the server where Azure AD AP is installed.
- Open a command prompt as an admin and move to the folder where PSTools has been extracted.
- Run the command: PsExec -i -u "NT Authority\NETWORK SERVICE" cmd.exe
- In the newly opened command prompt type: "C:\Program Files\Internet Explorer\iexplore.exe" to open Internet Exploiter.
- Set the proxy settings in IE, this will set proxy settings used by “Network Service” account.
Do the same with “NT Authority\SYSTEM” for the connector updater service.
After restarting both services, errors in logs should disappear and the connector should be listed in Azure Portal!
Comments
Anonymous
July 01, 2015
If you get prompted for a password when running these commands - type them instead of copy and paste. In my case copying them changed the character for the quotes around the account names and causes PSexec to ask for a password for system or network service (which you obviously don't have) spent far too much time on this issueAnonymous
July 06, 2015
Thanks Jeff for the comment! it's very true that copy/paste from my article changed the quote character. Sorry for that! i updated the article so now it should be fine! I add the command here again just in case :) PsExec -i -u "NT AuthorityNETWORK SERVICE" cmd.exe