How to Determine the CLSID of an ActiveX-Control ?
Hi Everybody!
In this blog I would like to share a method and tools used to help determine what the CLSID of an ActiveX Control that may generate a warning when using the security-option “Run ActiveX controls and plug-ins” with “Administrator approved” settings.
It is not always obvious which control a webpage from the Internet security zone wants to use, and which CLSID needs to be approved in order to run the page.
Within this particular sample, it is the webpage www.google.de, which does not display searchresults when ActiveX has been disabled but Active Scripting is enabled.
The Internet Explorer Compatibility Test Tool “ from the ACT ( https://www.microsoft.com/en-us/download/details.aspx?id=7352 ) can determine many CLSIDs when the ActiveX Blocking event are created, but in this particular case, no event was created and therefore the tool could not provide a hint.
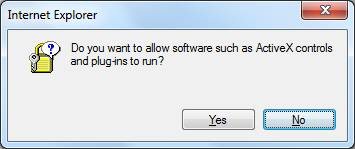
In case, that a webpage only needs one single ActiveX-control (or if the control in question is the 1st requested), it is much more easier to determine its CLSID when you configure the option “Run ActiveX controls and plug-ins” to “Prompt”, so IE will issue the following question:
The 1st approach is by using Process Monitor from https://technet.microsoft.com/de-de/sysinternals/bb896645.aspx
Before you start IE, you start the capture for the Registry in Process Monitor. Adding a filter for the Process Name “iexplore.exe” is a good start.
Then you navigate to the page until the question “Do you want to allow software such as ActiveX Controls and plug-ins to run ?” is displayed.
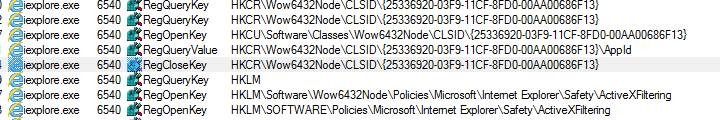
Then, you stop capturing in Process Monitor, and search from the bottom (Direction set to “Up”) for “CLSID”
In my sample the following line was found:
When looking to the registry-keys, the control with the CLSID {25336920-03F9-11CF-8FD0-00AA00686F13} has the name ”HTML Document“.
Now, I was a bit surprised, as ”HTML document” doesn’t sound like something which IE cannot perform without changing security options for ActiveX controls.
Taking this, I was using the Script Debugger from IE9 in order to determine where this has been initiated, and why “HTML Document” was requested as ActiveX control.
Using this, I closed IE again and started a new instance to the empty page „about:blank“.
The security option “Run ActiveX controls and plug-ins” was still set to “Prompt”.
I opened the Developer Tools by the F12-key, clicked the tab “Script” and enabled the Script Debugging (the button then changes its title to “Stop Debugging”).
In order to read the scripts better, I also checked the “Format JavaScript”
After navigating to the page (www.google.de) the prompt was issued. Before clicking „Yes“ or „No“, click the “Break all”-button in the DevTools:
Then you can click “Yes” or “No” to the ActiveX-prompt, and the script-debugger kicks in.
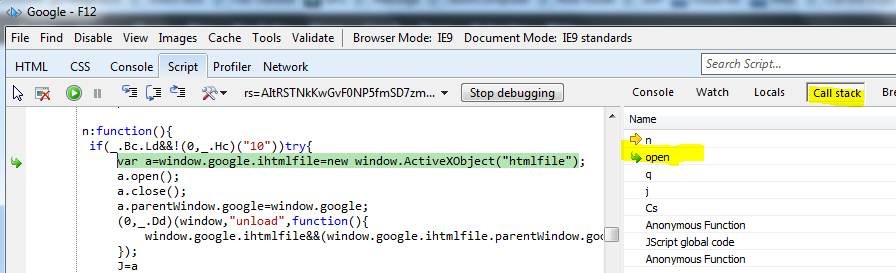
Within the call-stack, I went one level up and found the following script-code:
So, it is the instruction “new window.ActiveXObject("htmlfile")” which explicitly creates an ActiveX-control from the type “htmlfile”.
With a short view to the registry, the way to the CLSID can be determined by that way:
[HKEY_CLASSES_ROOT\htmlfile]
(default)="HTML Document"
[HKEY_CLASSES_ROOT\htmlfile\CLSID]
(Default)="{25336920-03F9-11cf-8FD0-00AA00686F13}"
When you want to use the ActiveX-Option “Administrator approved”, you then need to add the following registry-key in order to approve it:
[HKCU\Software\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\AllowedControls]
(DWORD)"{25336920-03f9-11cf-8fd0-00aa00686f13}"=0
This blog has been provided to you by Heiko Mayer, IE Escalation Engineer.
Comments
- Anonymous
May 19, 2016
And in an enterprise environment, MS introduced the Site Discovery Toolkit that allows you to collect some data using that telemetry feature embedded with IE11. Data is stored either in WMI repository or XML file and you collect all ActiveX GUIDs accessed.https://technet.microsoft.com/en-us/itpro/internet-explorer/ie11-deploy-guide/collect-data-using-enterprise-site-discovery?f=255&MSPPError=-2147217396