Avaliação de segurança: Delegação do Kerberos não seguras
O que é a delegação kerberos?
A delegação kerberos é uma definição de delegação que permite que as aplicações solicitem credenciais de acesso do utilizador final para aceder aos recursos em nome do utilizador de origem.
Que risco representa a delegação kerberos não seguras para uma organização?
A delegação Kerberos não seguras dá a uma entidade a capacidade de o representar para qualquer outro serviço escolhido. Por exemplo, imagine que tem um site do IIS e que a conta do conjunto aplicacional está configurada com delegação sem restrições. O site do IIS também tem a Autenticação do Windows ativada, permitindo a autenticação Kerberos nativa e o site utiliza uma SQL Server de back-end para dados empresariais. Com a sua conta do Domain Administração, navega para o site do IIS e autentica-o. O site, através da delegação sem restrições, pode obter uma permissão de serviço de um controlador de domínio para o serviço SQL e fazê-lo no seu nome.
O problema main com a delegação do Kerberos é que tem de confiar na aplicação para fazer sempre o que está certo. Os atores maliciosos podem, em vez disso, forçar a aplicação a fazer a coisa errada. Se tiver sessão iniciada como administrador de domínio, o site pode criar um pedido de suporte para os outros serviços que pretender, agindo como você, o administrador de domínio. Por exemplo, o site pode escolher um controlador de domínio e fazer alterações ao grupo de administradores da empresa . Da mesma forma, o site pode adquirir o hash da conta KRBTGT ou transferir um ficheiro interessante do seu departamento de Recursos Humanos. O risco é claro e as possibilidades com a delegação não seguras são quase infinitas.
Segue-se uma descrição do risco colocado por diferentes tipos de delegação:
- Delegação sem restrições: qualquer serviço pode ser abusado se uma das respetivas entradas de delegação for sensível.
- Delegação restrita: as entidades restritas podem ser abusadas se uma das respetivas entradas de delegação for sensível.
- Delegação restrita baseada em recursos (RBCD): as entidades restritas baseadas em recursos podem ser abusadas se a própria entidade for sensível.
Como fazer utilizar esta avaliação de segurança?
Reveja a ação recomendada em https://security.microsoft.com/securescore?viewid=actions para descobrir quais das entidades que não são do controlador de domínio estão configuradas para delegação kerberos não seguras.
Tome as medidas adequadas para os utilizadores em risco, como remover o atributo não preparado ou alterá-lo para uma delegação restrita mais segura.
Observação
Embora as avaliações sejam atualizadas quase em tempo real, as classificações e os estados são atualizados a cada 24 horas. Embora a lista de entidades afetadas seja atualizada poucos minutos após a implementação das recomendações, a status ainda poderá demorar algum tempo até ser marcada como Concluída.
Remediação
Utilize a remediação adequada ao seu tipo de delegação.
Delegação sem restrições
Desative a delegação ou utilize um dos seguintes tipos de delegação restrita de Kerberos (KCD):
Delegação restrita: Restringe os serviços que esta conta pode representar.
Selecione Confiar neste computador para delegação apenas aos serviços especificados.
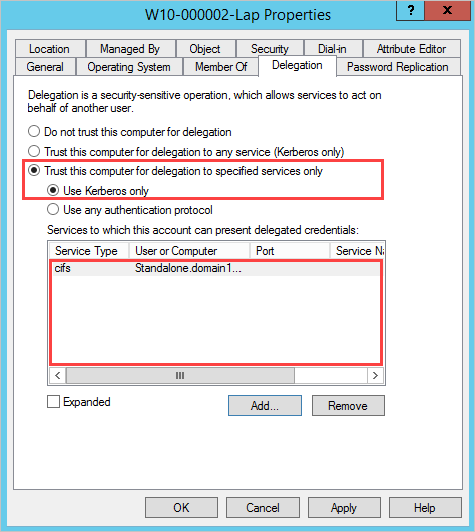
Especifique os Serviços aos quais esta conta pode apresentar credenciais delegadas.
Delegação restrita baseada em recursos: Restringe as entidades que podem representar esta conta.
O KCD baseado em recursos é configurado com o PowerShell. Utilize os cmdlets Set-ADComputer ou Set-ADUser, consoante a conta de representação seja uma conta de computador ou uma conta de utilizador/conta de serviço.
Delegação restrita
Reveja os utilizadores confidenciais listados nas recomendações e remova-os dos serviços aos quais a conta afetada pode apresentar credenciais delegadas.
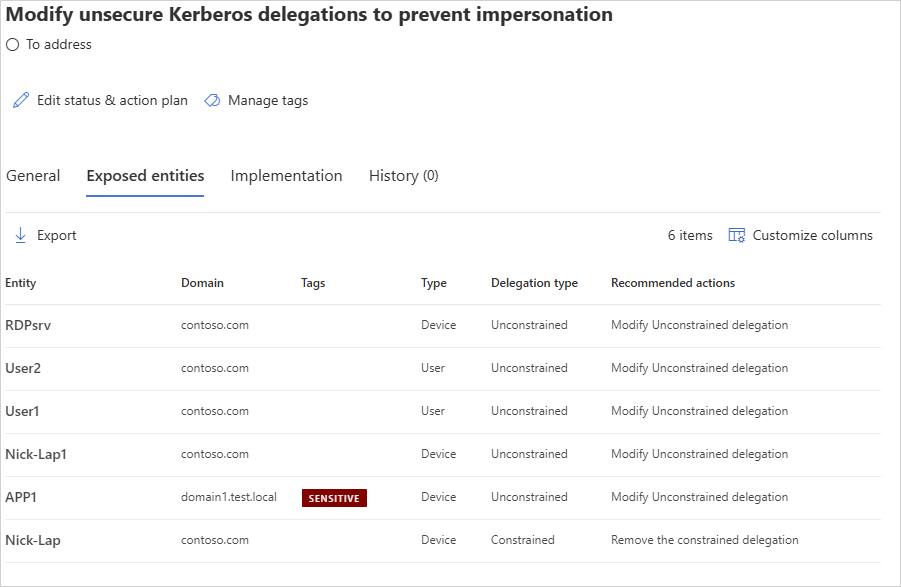
Delegação restrita baseada em recursos (RBCD)
Reveja os utilizadores confidenciais listados nas recomendações e remova-os do recurso. Para obter mais informações sobre como configurar o RBCD, veja Configurar a delegação restrita de Kerberos (KCD) no Microsoft Entra Domain Services.