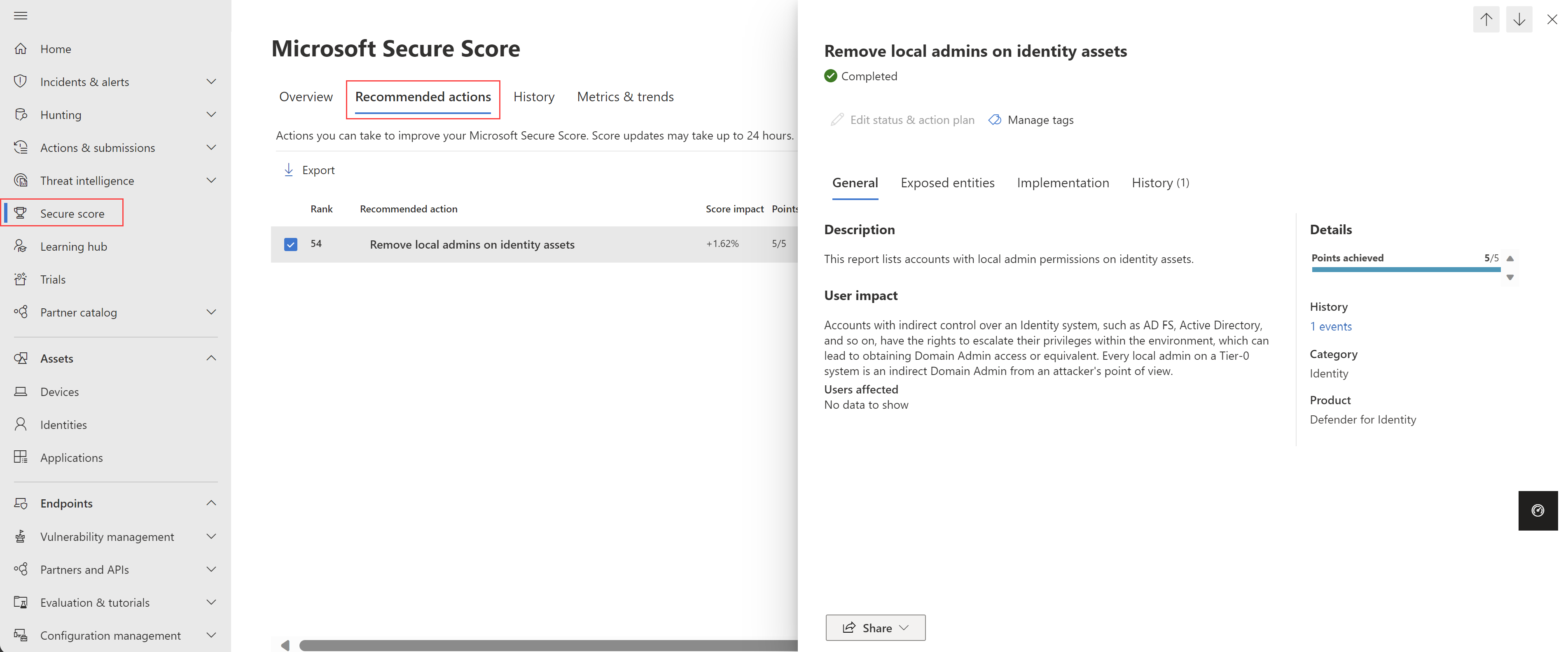
Security assessment: Remove local admins on identity assets
This article describes the Remove local admins on identity assets security assessment, which highlights local admins that pose a risk to your environment.
Why are local admins on identity assets a risk?
Accounts with indirect control over an identity system, such as AD FS, AD CS, Active Directory, and so on, have the rights to escalate their privileges within the environment, which can lead to obtaining Domain Admin access or equivalent.
Every local admin on a Tier-0 system is an indirect Domain Admin from an attacker's point of view.
How do I use this security assessment to improve my organizational security posture?
Review the recommended action at https://security.microsoft.com/securescore?viewid=actions for Remove local admins on identity assets.
For example:
Review this list of exposed entities to discover which of your accounts have local admin rights on your identity assets.
Take appropriate action on those entities by removing their privileged access rights.
To achieve a full score, you must remediate all exposed entities.
Note
While assessments are updated in near real time, scores and statuses are updated every 24 hours. While the list of impacted entities is updated within a few minutes of your implementing the recommendations, the status may still take time until it's marked as Completed.