Investigar alertas de segurança do Defender para Identidade no Microsoft Defender XDR
Observação
O Defender para Identidade não foi concebido para servir como uma solução de auditoria ou registo que captura todas as operações ou atividades nos servidores onde o sensor está instalado. Captura apenas os dados necessários para os mecanismos de deteção e recomendação.
Este artigo explica as noções básicas sobre como trabalhar com Microsoft Defender para Identidade alertas de segurança no Microsoft Defender XDR.
Os alertas do Defender para Identidade são integrados nativamente no Microsoft Defender XDR com um formato de página de alerta de Identidade dedicado.
A página de alerta identidade proporciona aos clientes Microsoft Defender para Identidade melhor melhoramento do sinal entre domínios e novas capacidades de resposta de identidade automatizada. Garante que se mantém seguro e ajuda a melhorar a eficiência das suas operações de segurança.
Uma das vantagens de investigar alertas através de Microsoft Defender XDR é que Microsoft Defender para Identidade alertas estão ainda correlacionados com as informações obtidas de cada um dos outros produtos no conjunto de aplicações. Estes alertas melhorados são consistentes com os outros formatos de alerta Microsoft Defender XDR provenientes de Microsoft Defender para Office 365 e Microsoft Defender para Ponto de Extremidade. A nova página elimina efetivamente a necessidade de navegar para outro portal de produto para investigar alertas associados à identidade.
Os alertas provenientes do Defender para Identidade podem agora acionar a Microsoft Defender XDR capacidades de investigação e resposta automatizadas (AIR), incluindo a remediação automática de alertas e a mitigação de ferramentas e processos que podem contribuir para a atividade suspeita.
Importante
Como parte da convergência com Microsoft Defender XDR, algumas opções e detalhes foram alterados a partir da respetiva localização no portal do Defender para Identidade. Leia os detalhes abaixo para descobrir onde encontrar as funcionalidades familiares e novas.
Rever alertas de segurança
Os alertas podem ser acedidos a partir de várias localizações, incluindo a página Alertas , a página Incidentes , as páginas de Dispositivos individuais e a partir da página Investigação avançada . Neste exemplo, vamos rever a página Alertas.
No Microsoft Defender XDR, aceda a Incidentes & alertas e, em seguida, a Alertas.
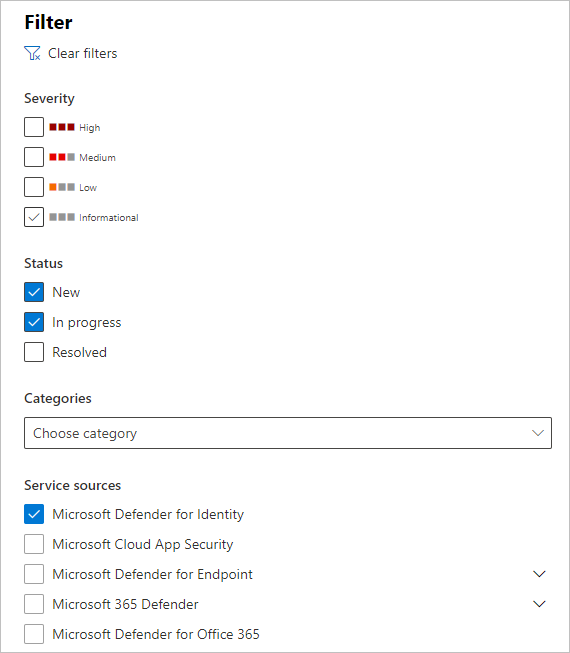
Para ver alertas do Defender para Identidade, no canto superior direito, selecione Filtrar e, em seguida, em Origens de serviço, selecione Microsoft Defender para Identidade e selecione Aplicar:
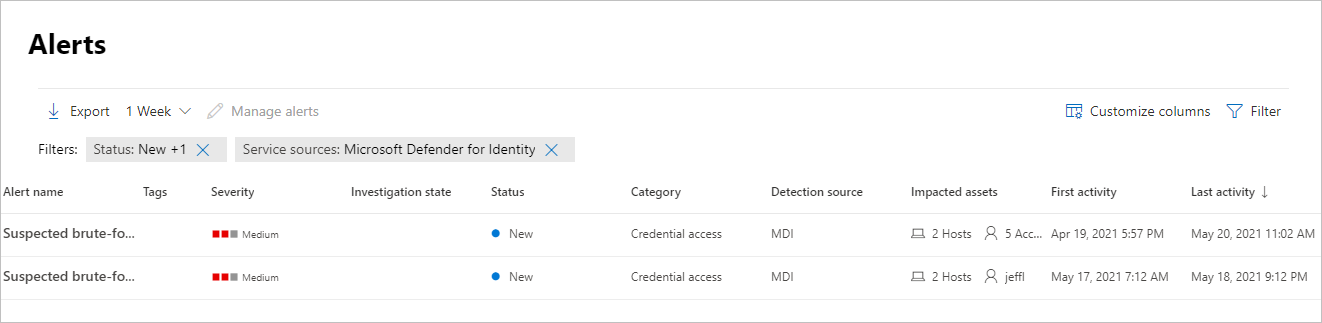
Os alertas são apresentados com informações nas seguintes colunas: Nome do alerta, Etiquetas, Gravidade, Estado da investigação, Estado, Categoria, Origem da deteção, Recursos afetados, Primeira atividade e Última atividade.
Categorias de alertas de segurança
Os alertas de segurança do Defender para Identidade estão divididos nas seguintes categorias ou fases, como as fases vistas numa cadeia de eliminação de ciberataques típica.
- Alertas de reconhecimento
- Alertas de credenciais comprometidos
- Alertas de movimento lateral
- Alertas de dominância de domínio
- Alertas de exfiltração
Gerenciar alertas
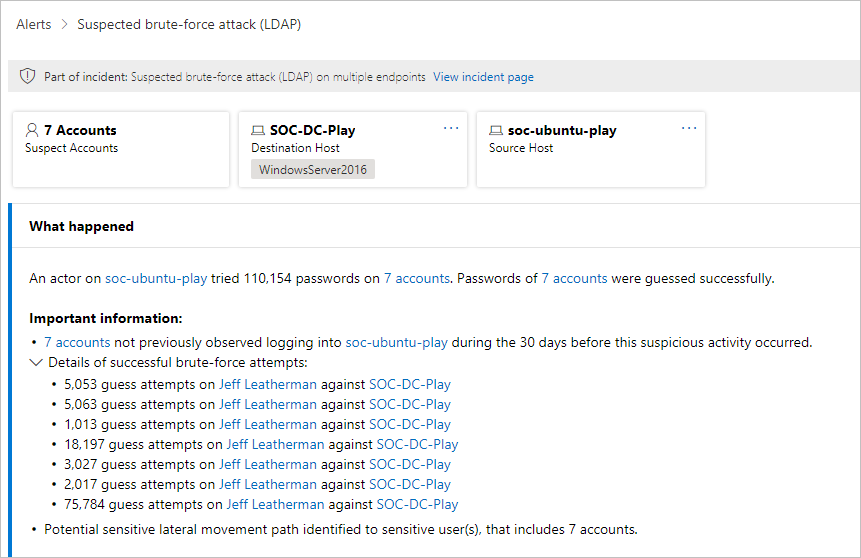
Se selecionar o Nome do alerta para um dos alertas, irá para a página com detalhes sobre o alerta. No painel esquerdo, verá um resumo de O que aconteceu:
Acima da caixa O que aconteceu estão os botões para As Contas, o Anfitrião de Destino e o Anfitrião de Origem do alerta. Para outros alertas, poderá ver botões para obter detalhes sobre anfitriões, contas, endereços IP, domínios e grupos de segurança adicionais. Selecione qualquer uma delas para obter mais detalhes sobre as entidades envolvidas.
No painel direito, verá os Detalhes do alerta. Aqui, pode ver mais detalhes e realizar várias tarefas:
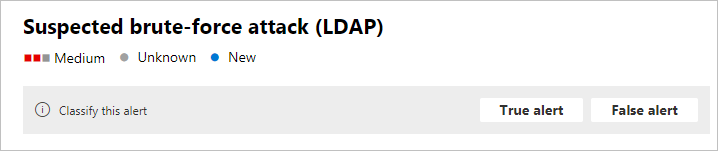
Classificar este alerta – aqui pode designar este alerta como um alerta Verdadeiro ou Falso
Estado do alerta – em Definir Classificação, pode classificar o alerta como Verdadeiro ou Falso. Em Atribuído a, pode atribuir o alerta a si próprio ou anular a atribuição.
Detalhes do alerta – em Detalhes do alerta, pode encontrar mais informações sobre o alerta específico, seguir uma ligação para a documentação sobre o tipo de alerta, ver a que incidente o alerta está associado, rever quaisquer investigações automatizadas ligadas a este tipo de alerta e ver os dispositivos e utilizadores afetados.
Comentários & histórico – aqui pode adicionar os seus comentários ao alerta e ver o histórico de todas as ações associadas ao alerta.
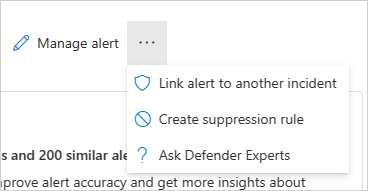
Gerir alerta – se selecionar Gerir alerta, irá para um painel que lhe permitirá editar:
Estado – pode escolher Novo, Resolvido ou Em curso.
Classificação – pode escolher Alerta verdadeiro ou Alerta falso.
Comentário – pode adicionar um comentário sobre o alerta.
Se selecionar os três pontos junto a Gerir alerta, pode Ligar alerta a outro incidente, Criar regra de supressão (disponível apenas para clientes de pré-visualização) ou Perguntar aos Especialistas do Defender.
Também pode exportar o alerta para um ficheiro do Excel. Para tal, selecione Exportar.
Observação
No ficheiro do Excel, tem agora duas ligações disponíveis: Ver no Microsoft Defender para Identidade e Ver no Microsoft Defender XDR. Cada ligação irá direcioná-lo para o portal relevante e fornecer informações sobre o alerta.
Alertas de otimização
Ajuste os alertas para os ajustar e otimizar, reduzindo os falsos positivos. A otimização de alertas permite que as suas equipas do SOC se concentrem em alertas de alta prioridade e melhorem a cobertura da deteção de ameaças em todo o sistema. No Microsoft Defender XDR, crie condições de regra com base em tipos de provas e, em seguida, aplique a regra em qualquer tipo de regra que corresponda às suas condições.
Para obter mais informações, veja Otimizar um alerta.
Confira também
Saiba mais
- Experimente o nosso guia interativo: Detetar atividades suspeitas e potenciais ataques com Microsoft Defender para Identidade