Gerenciar a segurança do sistema com o Microsoft Defender para Nuvem (versão prévia)
Aplica-se a: Azure Local 2311.2 e posterior
Este artigo discute como usar o Microsoft Defender para Nuvem para proteger o Azure Local contra várias ameaças e vulnerabilidades cibernéticas.
O Defender para Nuvem ajuda a melhorar a postura de segurança do Azure Local e pode proteger contra ameaças existentes e em evolução.
Para obter mais informações sobre o Microsoft Defender para Nuvem, consulte a documentação do Microsoft Defender para Nuvem.
Importante
Esse recurso está em VERSÃO PRÉVIA no momento. Veja os Termos de Uso Complementares para Versões Prévias do Microsoft Azure para obter termos legais que se aplicam aos recursos do Azure que estão em versão beta, versão prévia ou que, de outra forma, ainda não foram lançados em disponibilidade geral.
Pré-requisitos
Antes de começar, certifique-se de que os seguintes pré-requisitos foram concluídos:
- Você tem acesso ao Azure Local, que está implantado, registrado e conectado ao Azure.
- Você tem pelo menos as funções de Proprietário ou Colaborador em sua assinatura do Azure para ativar o CSPM (gerenciamento de postura de segurança na nuvem fundamental).
Habilitar o Defender para Nuvem para Azure Local
Siga estas etapas para habilitar o Defender para Nuvem para Azure Local.
- Etapa 1: ative o CSPM fundamental.
- Etapa 2: Ative o Defender para Servidores para computadores individuais e VMs do Arc.
Etapa 1: ativar o CSPM fundamental
Esta etapa ativa o plano básico do Defender para Nuvem, sem custo adicional. Esse plano permite monitorar e identificar as etapas que você pode seguir para proteger o Azure Local, juntamente com outros recursos do Azure e do Arc. Para obter instruções, consulte Habilitar o Defender para Nuvem em sua assinatura do Azure.
Etapa 2: Ativar o Defender para Servidores para computadores individuais e VMs do Arc
Esta etapa oferece recursos de segurança aprimorados, incluindo alertas de segurança para computadores individuais e VMs do Arc.
Para fazer isso, siga todas as instruções na seção Habilitar o plano do Defender para Servidores, que inclui:
- Seleção de um plano
- Configurando a cobertura de monitoramento para:
- Agente do Log Analytics
- Avaliação de vulnerabilidade
- Proteção do ponto de extremidade
Aplicar a iniciativa Microsoft Cloud Security Benchmark
Depois de ativar o plano CSPM básico do Microsoft Defender para Nuvem, você deve aplicar a iniciativa MCSB (Microsoft Cloud Security Benchmark). Você pode exibir as configurações de segurança por meio do portal do Azure somente quando o MCSB é aplicado. Use um dos seguintes métodos para aplicar a iniciativa MCSB:
- Aplique o MCSB por meio do portal, conforme descrito abaixo.
- Aplique manualmente a linha de base de segurança de computação do Azure na política do Azure a todos os servidores de cluster. Consulte Linha de base de segurança do Windows.
Siga estas etapas para aplicar a iniciativa MCSB no nível da assinatura:
Entre no portal do Azure e pesquise e selecione Microsoft Defender para Nuvem.
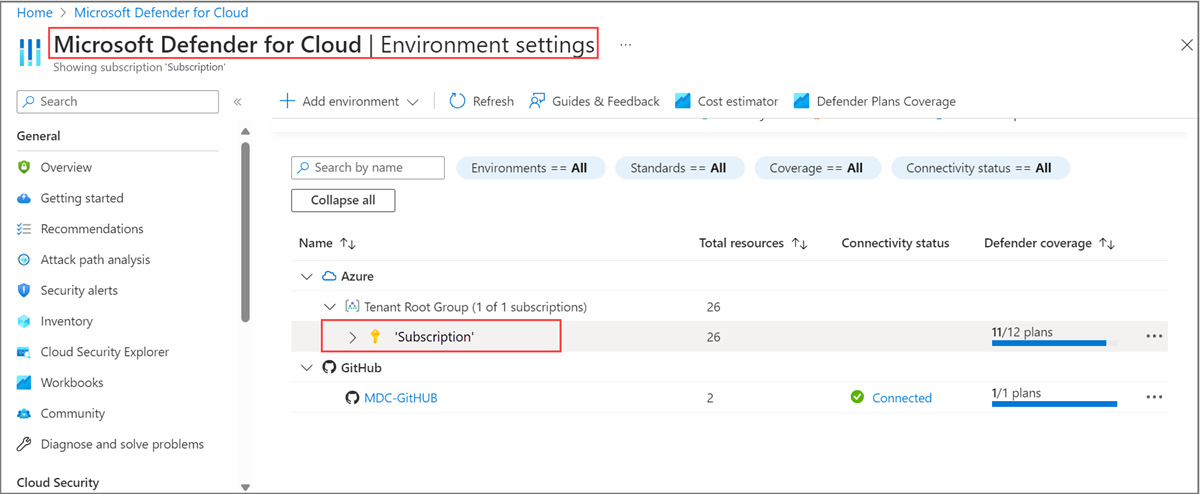
No painel esquerdo, role para baixo até a seção Gerenciamento e selecione Configurações de ambiente.
Na página Configurações do ambiente, selecione a assinatura em uso na lista suspensa.
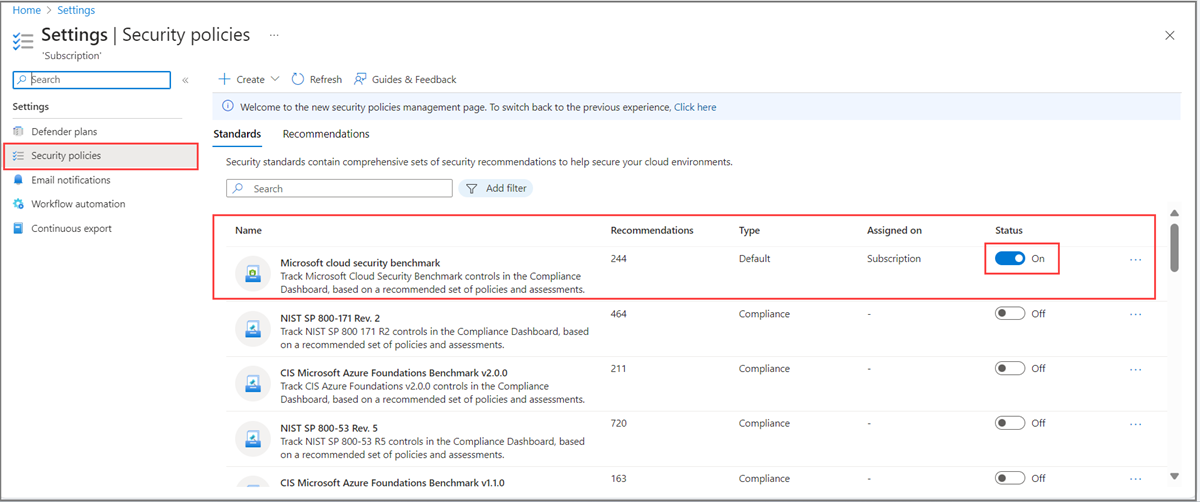
Selecione a folha Políticas de segurança.
Para o parâmetro de comparação de segurança de nuvem da Microsoft, alterne o botão Status para Ativado.
Aguarde pelo menos uma hora para que a iniciativa de política do Azure avalie os recursos incluídos.
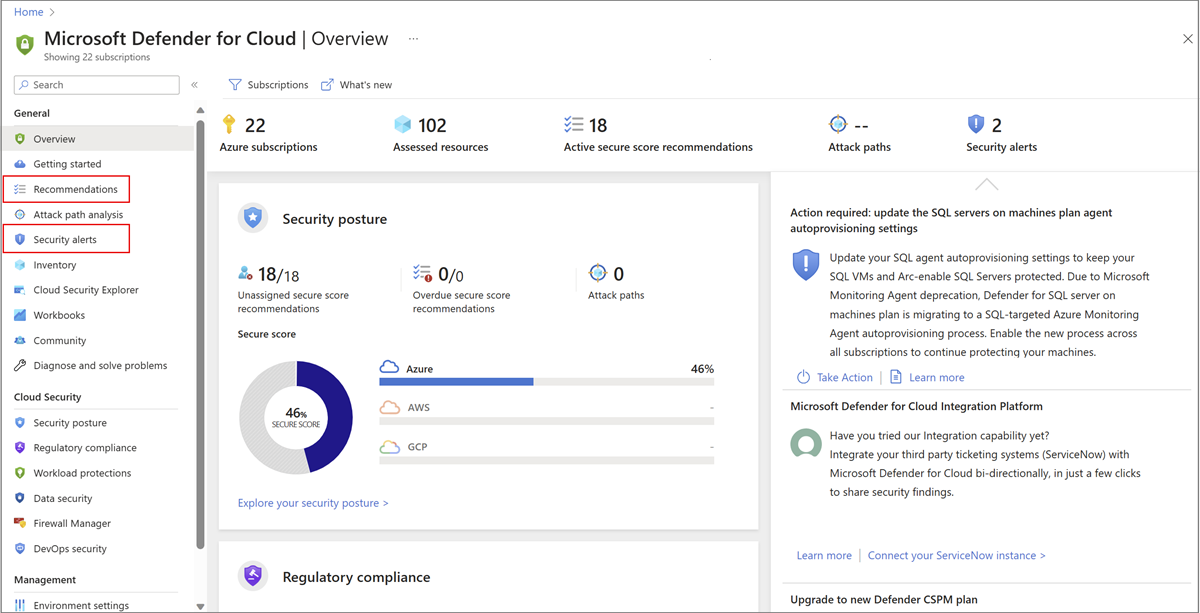
Exibir recomendações de segurança
As recomendações de segurança são criadas quando possíveis vulnerabilidades de segurança são identificadas. Essas recomendações orientam você pelo processo de configuração do controle necessário.
Depois de habilitar o Defender para Nuvem para Azure Local, siga estas etapas para exibir recomendações de segurança para o Azure Local:
No portal do Azure, acesse a página de recursos locais do Azure e selecione sua instância.
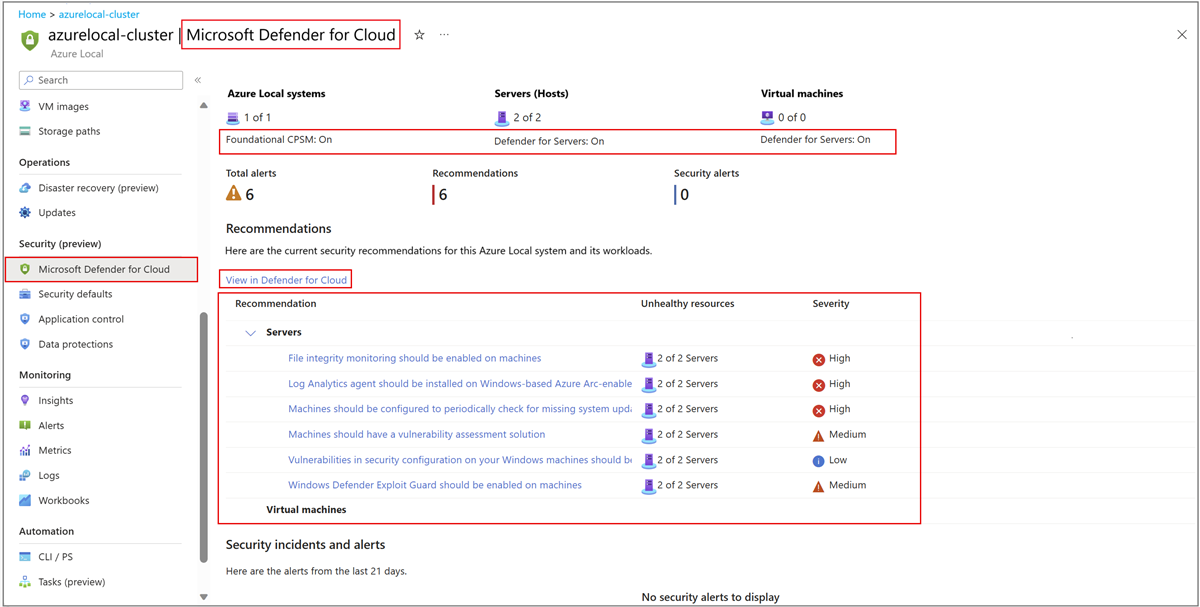
No painel esquerdo, role para baixo até a seção Segurança (versão prévia) e selecione Microsoft Defender para Nuvem.
Na página Microsoft Defender para Nuvem , em Recomendações, você pode exibir as recomendações de segurança atuais para a instância local do Azure selecionada e suas cargas de trabalho. Por padrão, as recomendações são agrupadas por tipo de recurso.
(Opcional) Para exibir as recomendações de segurança para várias instâncias locais do Azure, selecione o link Exibir no Defender para Nuvem . Isso abre a página Recomendações no portal Microsoft Defender para Nuvem. Esta página fornece recomendações de segurança em todos os seus recursos do Azure, incluindo o Azure Local.
Observação
As recomendações exclusivas do Azure Local estão disponíveis somente no Azure Local 2311 ou posterior. O Azure Stack HCI, versão 22H2, mostra as recomendações que também estão disponíveis no Windows Server.
Para saber mais sobre as recomendações de segurança específicas do Azure Local, consulte a seção Recomendações de computação do Azure no artigo Recomendações de segurança de computação.
Monitorar servidores e VMs do Arc
Acesse o portal do Microsoft Defender para Nuvem para monitorar alertas de servidores individuais e VMs do Arc em execução no Azure Local. Você pode utilizar os recursos de conformidade regulatória e análise de caminho de ataque, entre outros recursos de segurança aprimorados.
Siga estas etapas para acessar as páginas do portal do Microsoft Defender para Nuvem para monitorar servidores individuais e VMs do Arc:
Entre no portal do Azure e pesquise e selecione Microsoft Defender para Nuvem.
A página Visão geral do portal Microsoft Defender para Nuvem mostra a postura geral de segurança do seu ambiente. No painel de navegação esquerdo, navegue até várias páginas do portal, como Recomendações para exibir recomendações de segurança para servidores individuais e VMs do Arc em execução no Azure Local ou Alertas de segurança para monitorar alertas para eles.