The Internet Explorer threat
There has been a huge amount of media regarding the current security concerns of using Internet Explorer as a browser on your machine. Reports are indicating that the French and German governments are instructing people to change to another browser to fix the problem.
Our advice for users of Internet Explorer today is to ensure they upgrade to the latest version of Internet Explorer, Internet Explorer 8.
Now the questions that everyone will ask is, will that actually make a difference? Aren’t all Internet Explorer versions at risk?
Lets start with the vulnerability itself. Essentially it involves what is called an invalid pointer reference within Internet Explorer, which a specifically crafted attack could reference to enable remote code execution.
To do this, a user would have to navigate to a website that was specifically created to take advantage of this exploit, not your average everyday site, in fact you would have to be tricked to go the site via something like though an email message or an instant message, so in most cases Junk email filters should help to block these emails and you should never click on links from anyone you don’t trust or seem suspicious.
Now lets say for instance that you managed to get tricked to going to a site that had the attack created. The code would enable the attacker to get the same level of access as the current user. It is for this reason, we encourage average users not to operate under administrative privileges. As a standard user the attacker would have less permissions to try and do things on your PC.
Now finally, if you went to the site with attack code as an administrator user, Internet Explorer 8 has another benefit that protects users called Data Execution Protection (also known as DEP). DEP essentially blocks any code that is trying to be executed in a memory space that has resulted when an error occurs. Which is essentially what this attack is trying to do. So people using IE8 are protected because of the DEP turned on by default.
Now where is DEP enabled and in what configurations. There is a good table created on the Security Research & Defense Blog, which really simplifies the evaluation of the threat.
Windows 2000 |
Windows XP |
Windows Vista |
Windows 7 |
|
Internet Explorer 6 |
Exploitable |
Exploitable (current exploit effective for code execution) |
N/A (Vista ships with IE7) |
N/A (Windows 7 ships with IE 8) |
Internet Explorer 7 |
N/A (IE 7 will not install on Windows 2000) |
Potentially exploitable (current exploit does not currently work due to memory layout differences in IE 7) |
IE Protected Mode prevents current exploit from working. |
N/A (Windows 7 ships with IE 8) |
Internet Explorer 8 |
N/A (IE 8 will not install on Windows 2000) |
DEP enabled by default on XP SP3 prevents exploit from working. |
IE Protected Mode + DEP enabled by default prevent exploit from working. |
IE Protected Mode + DEP enabled by default prevent exploit from working. |
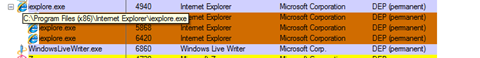
If you really want to check if you have DEP turned on for your machine, you can download a program called Process Explorer from https://technet.microsoft.com/en-us/sysinternals/bb896653.aspx, this is a small app we have via our acquisition of a company called Sysinternals, its completely free. When you run this you will be able to see all the processes running, and to check if DEP is enabled do the following;
1. Click View
2. Select Columns
3. Ensure that “DEP Status” is enabled
Then you should be able to see as in the picture below, that DEP is enabled.
As you can see there are many technologies in place that actually protect users from the vulnerability that many people are talking about in the news and blogs etc.
So in summary, the ways users can protect themselves
1. Install IE8, it has the best technologies to protect users from the threat.
2. Unless absolutely necessary try and run as a standard user on your PC and not as an administrator
3. Be extra vigilant on clicking links in emails or instant messages, and ensure your email filters are up to date. You can do this by ensuring that you turn automatic updates on in Windows.
For all the latest updates check out https://blogs.technet.com/msrc/.