Discovering AD Security Groups in OpsMgr 2007
A common method of identifying machines for deploying overrides, etc is to place unique registry keys on them that can be discovered by Opsmgr. While this is workable it does require introducing manual config onto individual managed systems.
Folks have asked for a while for a better method - one that would allow discovery of AD Security Group membership for agent systems so that this information could be used to build these override targets.
I've finally finished putting together a sample MP (with the help of Joel from the Product Group - thanks Joel!) that will do just that.
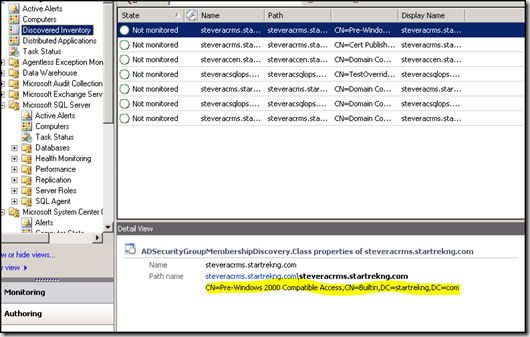
The MP works by deploying a script to every monitored agent. The script runs and makes an LDAP query to determine the agents AD security group membership. This information is posted back to the RMS and stored in the ADSecuritygroupMembershipDiscovery.Class as shown
The returned object are of type Windows Local Application so they cannot be directly used to consistently apply overrides (depending on the type of object you are trying to override, it might work, but not guaranteed). To make this object set useful for overriding you can create groups that key off of the discovered information and convert it to the corresponding windows computer type. This is done by editing the XML directly - which might sound scary but really isn't that bad.
My suggestion for creating groups is to start with the UI to create the skeleton group - create a group with a very simple expression. Then, export the modified MP. If you look in the XML you will see the group configuration
<GroupInstanceId>$MPElement[Name="UINameSpace8e14cb8716444609b6e9cb8a89224d26.Group"]$</GroupInstanceId>
<MembershipRules>
<MembershipRule>
<MonitoringClass>$MPElement[Name="Windows!Microsoft.Windows.Computer"]$</MonitoringClass>
<RelationshipClass>$MPElement[Name="MicrosoftSystemCenterInstanceGroupLibrary6062780!Microsoft.SystemCenter.InstanceGroupContainsEntities"]$</RelationshipClass>
<Expression>
<Contains>
<MonitoringClass>$MPElement[Name="ADSecurityGroupMembershipDiscovery.Class"]$</MonitoringClass>
<Expression>
<RegExExpression>
<ValueExpression>
<Property>$MPElement[Name="ADSecurityGroupMembershipDiscovery.Class"]/ADGroupMembership$</Property>
</ValueExpression>
<Operator>ContainsSubstring</Operator>
<Pattern>TestOverrideADSecGroup</Pattern>
</RegExExpression>
</Expression>
</Contains>
</Expression>
</MembershipRule>
</MembershipRules>
The bolded section above contains the group population criteria for a group that will be built based on membership in my AD group. Just replace your expression section with the one above and change the pattern field to represent your AD Group information. Reimport the MP and, magically, you now have a group that contains Windows Computer objects.
Now, depending on exactly what you are trying to do there might be some additional editing in the XML - but it shouldn't be too bad.
The sample MP is attached for download. Remember, this is a sample only and carries the normal disclaimers. Note also that this MP has not been tested in large scale production environments.
ADSecurityGroupMembershipDiscovery.xml
Comments
Anonymous
January 12, 2009
  A common method of identifying machines for deploying overrides, etc is to place unique registryAnonymous
January 13, 2009
OpsMgr 2007: Sample MP to discover AD security group membership Feed: The Operations Manager SupportAnonymous
January 13, 2009
Feed: The Operations Manager Support Team Blog Posted on: 13 January 2009 16:14 Author: jchornbe SubjectAnonymous
January 13, 2009
Feed: The Operations Manager Support Team Blog Posted on: 13 January 2009 16:14 Author: jchornbe Subject