Protect your data: everything else is just plumbing
Take a few moments and indulge in a thought exercise with me. Consider your company’s complete collection of information processing assets—all the computers, the networks they’re connected to, the applications you use, and the data and information you manipulate. Which of those is the most valuable? Which—if it suddenly and tragically disappeared tomorrow—would jeopardize your company’s ability to remain in business?
That’s right, it’s your data. Any of the other elements could easily be replaced. But if your data vanishes, well then, you might as well close up shop and take residence on some forsaken island in the middle of the ocean. It’s your data that gives you your competitive edge, your data that constitutes a large part of your business, and your data that is most attractive to attackers.
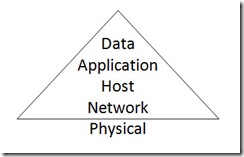
Why, then, is there still so much emphasis on protecting all the plumbing that moves the data around, but little interest in protecting the data itself? My guess: old habits die hard. For most of the history of information security, emphasis on security has roughly followed this model:
Historical approaches to security have placed most emphasis on the network, with decreasing consideration of individual computers and the applications they run, and the least amount of consideration for the security of the data. (I’ve purposefully placed the physical layer outside the triangle, partly as a joke and partly for real—when I visit data centers I routinely discover physical security problems!) Once upon a time, this was the correct approach: computers and applications weren’t designed with much regard for security, and the only way to protect the data was to protect the network. And indeed, because it was generally the network that the bad guys were after, this approach worked.
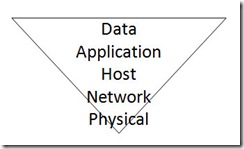
The old model is no longer appropriate today. The bad guys really don’t care about your network anymore: they’re going after your data. Attackers were once motivated by pride: Mafiaboy was notorious for bragging about bringing down large parts of the Internet in February 2000 (and his bragging became his undoing). But these days, attackers are motivated by profit: they’re out to make money. The economics of the game have changed, and along with that so have the bad guys’ skills and the capabilities of their tools. Let me repeat: they want your data. They’ll steal it and sell it to your competitors, they’ll damage it and put you out of business. The network and your computers exist only as a means to get to your data. So we, as defenders of information assets, must change our tactics to react to—and possibly get in front of—the tactics of the bad guys. We’ve got to invert the traditional thinking and now emphasize security by following this new model:
Because protecting your data is now paramount, data protection deserves the bulk of your attention. Application security—developing applications with a mind toward security and how they might be purposefully abused by an attacker—is similarly critical. Good host security will remain important in this world as well, especially the security of mobile computers of all kinds. Because people use computers to run applications that process data, it’s these layers that are crucial. If you apply this model, the network can return to doing its only true job: moving bits around as fast as possible.
Traveling to the new world
So how do you get from there to here? One word: cool technology (OK, two words).
Full drive encryption
For some time, I’ve been advocating that using host-based firewalls isn’t an option: it’s required. Ordinarily, you have no control over the traffic that appears at your Ethernet port. A host firewall gives you control. I now have a second requirement: full drive encryption, especially on portable computers. According to the 2006 Australian Computer Crime and Security Survey, for four years in a row, laptop theft is the most expensive attack weathered by the organizations who responded. The exposure (and expense) isn’t the hardware—it’s the data stored on the computers. This tells me that good-quality full drive encryption is probably one of the best investments you can make to help save your company money! So go ahead and upgrade those laptops to Windows Vista (Enterprise or Ultimate editions) right now, to take advantage of BitLocker full volume encryption, because the cost of the upgrade is most certainly less than the cost of losing your data (and your reputation).
Learn more about BitLocker: https://technet2.microsoft.com/WindowsVista/en/library/ba1a3800-ce29-4f09-89ef-65bce923cdb51033.mspx
Document protection
When Alice creates a file and wants to give Bob read/write access, give Phil read access, and deny everyone else, the traditional approach involves a lot of work on the part of someone else. Alice has to beg, cajole, and bribe the network admin to create a file share, create two security groups, add Bob to one and Phil to the other, and create access control entries on the share’s access control list. That’s a lot of work for someone who really doesn’t care about Alice’s problems. And it’s incomplete: sure, Eve can’t touch the file on the share, but she can certainly convince Phil to give her a copy—read access also permits copying. If Phil were particularly malicious, he could modify his copy of the document first. You see, network-based access control works only so long as the protected object remains within the network. As soon as someone opens the file, the local copy in the computer’s memory obeys no restrictions.
Windows Rights Management Services (RMS) and Microsoft Office Information Rights Management (IRM) give you an alternate form of access control that persists on the documents themselves regardless of where they live. When Alice assigns read/write access to Bob and read-only access to Phil, she doesn’t need to involve the network admin at all. The access she assigns is stored right in the document and enforced by IRM. When Bob opens the document, Word first checks Bob’s permissions and then disables functionality so that Bob can’t do anything more than what he’s allowed. In Bob’s case, Word will refuse to do anything other than display the content in the window.
In addition to enforcing policy through IRM, RMS protects documents by encrypting them. RMS-protected documents remain encrypted in storage and in transit. They’re decrypted only after an authorized user has been authenticated and his or her permissions have been enforced. If someone outside the RMS’s domain attempts to open a file, it’ll just appear as nonsense. Unless your computer is enrolled in RMS and you’re on the list of authorized users, this document is useless to you. It’s also useless to the friends you’ve given copies to on those ubiquitous USB drives littering the basement of your desk.
Learn more about Rights Management Services: https://www.microsoft.com/rms
Data security
One definition of news is “something that happens rarely.” Data breaches must no longer be news, then, because they seem to happen with increasing regularity. The best way to avoid a breach is not to store data you don’t need—after you process that credit card number, delete it, don’t retain it. Other sensitive data you do need to retain in some database as part of your business. The best way to keep this data secure is to encrypt it in the database. Microsoft SQL Server 2005 includes some great features to help you here—field-level encryption of data in storage, encryption of data in transit, and enterprise-level key management. An important project that you should soon consider is to evaluate all instances where your company is storing private or confidential information (especially about your customers) and add data encryption where appropriate.
Learn more about SQL Server encryption: https://download.microsoft.com/download/4/7/a/47a548b9-249e-484c-abd7-29f31282b04d/SQLEncryption.doc
Of course, there’s more to data security than just the physical storage. Equally important are policies and processes for classifying data. There’s an entire body of knowledge—too much to absorb, really—on this topic. Rather than send you off on some endless forage through your favorite search engine, I’ll share with you a classification scheme I discovered recently. It’s simple and elegant—which means it’s something you can actually use.
First, think about confidentiality classifications. These are important because they help guide your response in case of a breach. Four classifications should be sufficient: public, internal, confidential, and private.
Next, consider retention classifications. If you should ever be hauled into court for some reason, the discovery process will uncover a whole lot of your data. You could face major penalties if new information is discovered after a trial starts. Therefore, it’s necessary to follow a policy that routinely purges e-mails and file shares after a period of time. These three retention classifications are good enough for most cases: regulated data for seven years, historical business data for three years, and temporary data (like e-mail) for one year.
Finally, consider recovery classifications. How quickly, in the event of a disaster, will you need to recover certain kinds of data? Are employees allowed to store mission-critical information on home computers or portable devices? Here’s a sample recovery classification: for mission-critical data, immediate recovery; for urgent data, recovery within 72 hours; for non-urgent data, recovery within 30 days.
Security for the modern age
Attackers constantly improve their tactics as their motives become more sinister. By adjusting your tactics as well, you can be certain that you’re doing your part to keep your information secure.
Comments
Anonymous
January 01, 2003
Steve Riley posts on a topic he discussed at Tech-Ed - protecting the data, because everything else isAnonymous
July 03, 2007
Good posting. I have tried to demonstrate this since year 2000 by using a slide listing fw, routers, etc and asking what is most important entity to protect, and then animated cross over everything and telling that it is information/data and requirements from there sets requirement for others. Another issue is; will there be protection mechanisms on operating system level which put more into securing data rather than operating system? e.g Ten Immutable Laws is outdated. It solely focus on exploits, overwrite, incidents and e.g does not take into account that when attacker gets in, then the protection should still prevent attacker to access the data.Anonymous
July 03, 2007
Steve, Great post I couldn't agree with you more. Our company is currently moving through that transition of Focusing on the network to focusing on the data. But I have to disagree with the previous comment. The Ten Immutable Laws of security are not outdated and will not be outdated because they are based on the basic principles that are time tested and proven. How and where you apply them is changing.Anonymous
July 03, 2007
Very true, this change is now underway. Standard textbook training in security doesn't really address these concerns, but the primary threat models security teams should be worrying about are now in flux. It really is all about the data. I'm surprised you chose DRM and full-disk encryption as the two primary technologies to profile though. If it's about the data, shouldn't you also talk about content-aware security technologies that discover the flow of that data (i.e. Data Loss Prevention), govern access to that data (i.e. Data Governance Software), or help classify the data (i.e. Information Classification Systems.) These content aware approaches appear to be (at least to me) at the forefront of this data-centric security model.Anonymous
July 04, 2007
Loved the article! You're spot-on in saying that the data is what we need to focus on protecting. Even the terminology we use puts too much focus on protecting the "network" and I think this distracts so many people working in the field of IT into focusing on the physical bits and pieces rather than the data.Anonymous
July 10, 2007
Yes, the data (read information) is probably your prime asset. But in addition to confidentiality and integrity (addressed in this article) it is important that the data are available where you need it when you need it. Hence, you need a secure network as well. Also, for defence in depth, i would move some of the defence mechanisms away from the client (which you can't really control) to a device physically separated from the user. For instance, traffic filtering performed by a network firewall.Anonymous
July 27, 2007
Steve is right that too often backups and encryption are forgotten. And it's true that the FILES on the computer that aren't data are plumbing. But the other part of the plumbing, e.g. the free disk space and network bandwidth that can be used to sell DoS zombie attacks, spam relays and pubstro FTP servers, are I think still attacked as much as the user data is. Also, drive encryption and backups only protect the data at rest. I understand that recent attacks have monitored running processes and/or memory to glean useful user data being sent out through Internet Explorer. So I hope it's clear to all the readers that Steve isn't advocating that they can start spending less time on the other traditional countermeasures.