Microsoft Advanced Threat Analytics Lab Setup and Demo
Hey Folks! I just got my ATA lab up and running and thought I’d share a few tips and tricks for those of you doing a lab or POC type setup and want to get up and running quickly.
First of all, here’s the ‘official’ documentation for ATA. It’s worth walking through that as I won’t really detail the setup process here since I’ve already done that and don’t have the screenshots. The setup/install for ATA is very straightforward although I’ll provide a few tidbits here that might help you not run into the same snags I did getting this up and running.
ATA Deployment Guide
ATA Architecture and Capacity Planning
ATA Operations Guide
ATA FAQ
ATA Technical Discussion Forums
If you need the 90 day trial bits – you can grab those here: https://www.microsoft.com/en-us/evalcenter/evaluate-microsoft-advanced-threat-analytics
They are also on MSDN as well if you are a subscriber there (along with a key you can use):
An example ATA Topology might look like what is represented in this diagram. But, the gist here is that you NEED to have both the ATA Center AND the gateway and they can’t be the same server.
The capacity planning guide (linked above) will give you an idea how to size your servers:
In my lab I’m running everything (DC, ATA Center and ATA Gateway) all in Hyper-V VM’s. I happen to be using the Windows Server 2016 Tech Preview 4 but most folks will, at least at the time of this writing, use 2012 R2 which will work fine of course. It is required to run 2012 R2 – 2012 R1 is not supported. The key here is that you’ll need to enable port mirroring on both your DC and ATA Gateway VM’s so keep that in mind.
NOTE: As of this writing using ATA in Microsoft Azure is not supported. So, if you have domain controllers in Azure you will not be able to configure the port mirroring (or the gateway servers for that matter) since those virtual switch capabilities are not exposed. The product teams are working on this so stay tuned…
Tip/Trick: I happen to have DC’s in both Azure and “on-prem” in my environment and have a site-to-site VPN connection pinned up so that they can communicate. I run my ATA demo Windows 7 VM’s on the same Hyper-V host as my ATA Center and Gateway VM’s and the Windows 7 VM’s are set to talk to the IP address of the DC/DNS server sitting on the same subnet so my ‘attacks’ are always against the local DC. If you have DC’s in Azure just make sure you configure AD Sites so that clients communicate with local DC’s first.
When you are installing the ATA Center you’ll need a VM configured with either 2 NIC’s or a single NIC with 2 IP addresses. If you are going with the single NIC configuration you can get more information on how to set that up in the Operations Guide. Modifying the Console IP Address should help you. One of them is to connect to the console and the other is for ATA management. Make sure you notate the IP’s correctly when you get this setup. Read the deployment guide as well – there’s a Windows Server hotfix that needs to be applied or you’ll have issues.

Now, on the DC go to the network settings on the VM and enable port mirroring and choose ‘source’ from the drop down.
On the Gateway VM you’ll connect to the ATA Center console IP address and then download the gateway installer components. Follow the instructions per the deployment guide for installing – it’s pretty straightforward.
The thing here is – you’ll need to 2 NIC’s on the Gateway VM. In this case, you’ll need 2 NIC’s – not a single NIC with one IP address like you can do with the ATA Center. Configure one for LAN and the other for CAPTURE. I like to name the NIC’s just to keep track easily.
On the CAPTURE NIC you’ll want some ‘dummy’ information in there. Pick an IP/subnet that is not routable and no DNS. Here’s what I did:
On the gateway server you’ll need to enable port mirroring on that CAPTURE NIC. Make sure you pick the right one – in the Hyper-V settings I always look for the MAC address and then do an ipconfig in the VM to match up which NIC since it’s not blatantly obvious in the settings which one is which. Make sure you choose ‘destination’ from the drop down.
In the ATA web console you’ll see the option to check the appropriate capture NIC:
You may need to check to make sure that the ATA Service is running at this point on the gateway.
Now you’ll want to make sure that you configure event forwarding on your DC so that Event ID 4776 (which deals with Pass the Hash) gets forwarded to the ATA Gateway. These steps are also documented in the installation guide (although with no screen shots or details so it can be a bit confusing to figure out what goes where)
On your DC open the event viewer and create a new subscription. In the ‘select computers’ make sure you select your ATA Gateway. Then in the query filter choose the following options:
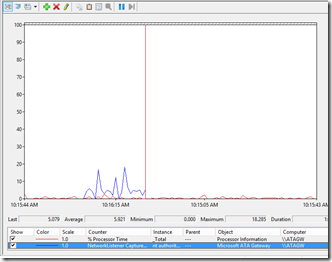
As the deployment guide states – check the perfmon counters to make sure your gateway is installed correctly.
The one that will tell you whether or not the gateway is the network listener / captures messages per second:
When you add that counter you’ll start to see some activity there:
At this point you should be able to login to the console and over on the right hand side you’ll see that ATA will start picking up some information about your environment:
You should also be able to use the ‘search’ box to look up users/computers, etc…
At this point we can do a few tests to check and make sure our environment is working properly. ATA will take 21 days to really learn your environment so you won’t see pattern behavior type activity for a period of time because ATA is in learning mode. However, there are quite a few attacks that will show up immediately. Here’s a few you can use to do some testing or demos:
Pass the Hash:
I won’t walk through all the steps – it’s pretty well documented on how to do this. Easiest way to test is with Windows 7 since newer OS’s have features to combat this. Best way is to watch this video from TechEd with Mark Russinovich and Nathan Ide.
https://www.youtube.com/watch?v=7hmTElGFWA0
DNS Recon:
Open a CMD window and do an NSLOOKUP against your protected DC:
nslookup –dc.domain.com
Now do this:
ls domain.com
You’ll see all your machines enumerated in the window. Now lets go check out the ATA Console:
We can see here that I ran this a couple times. Once at 11:33am and again for this demo at 12:28pm:
Let’s try something else…
Remote Execution:
Download the PsExec Tools from TechNet: https://technet.microsoft.com/en-us/sysinternals/bb896649.aspx
From a member server in the domain run the following command:
PsExec.exe \\DC01 Ipconfig
(DC01 of course represents one of your protected DC’s)
You’ll get an ipconfig from the DC. In your ATA console you’ll see this:
Finally let’s log into a PC with the honey token user account:
If you followed the directions in the ATA install guide you have your honey token account setup. Typically this is the good ol’ DOMAIN\Administrator account.
In my case, I have a user called ‘admin’ and I just logged into one of my Windows 7 VM’s with that identity. This is what shows up in the ATA console:
So there you go! ATA is really a pretty easy product to install and get especially when you consider the kind of information and insight it provides. Hopefully this helps you on your way to getting ATA setup and configured properly and if you are like me and doing demos and such this gives you a few things that you can show off in real time.
On a side note – I found a cool app to populate pictures in AD. Not really a requirement here – but if like me, you are in lab environment and doing demo’s it’s nice to add some context to the interface. I don’t have SharePoint or Exchange running in my lab so some of the ways to populate this aren’t available to me. So, check this site out – free download and you’ll have some fun pictures for your test users.
https://www.codetwo.com/freeware/active-directory-photos/?sts=1687
Have fun!
Comments
- Anonymous
February 11, 2016
Great walkthrough man! Just rebuilt my environment this AM with 1.5 and this was helpful.