Reduce your threat and vulnerability exposure
An organization's exposure score is visible in the Vulnerability Management dashboard of the Microsoft Defender portal. It reflects how vulnerable your organization is to cybersecurity threats. A low exposure score means your devices are less vulnerable from exploitation. An organization's enterprise and security administrators should:
- Quickly understand and identify high-level takeaways about the state of security in their organization.
- Detect and respond to areas that require investigation or action to improve the current state.
- Communicate with peers and management about the effect of security efforts.
The exposure scorecard gives an organization a high-level view of its exposure score's trend over time. Any spikes in trend line provide a visual indication of a high cybersecurity threat exposure that needs further investigation.
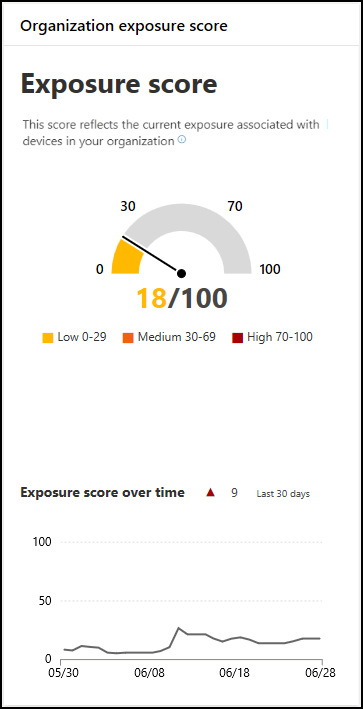
The Microsoft Defender Vulnerability Management dashboard breaks the exposure score into the following levels:
- 0-29. Low exposure score.
- 30-69. Medium exposure score.
- 70-100. High exposure score.
Reduce your threat and vulnerability exposure
The Vulnerability Management feature in Microsoft Defender XDR maps an organization's cybersecurity weaknesses to actionable security recommendations. It also prioritizes those weaknesses by their effect. Prioritized recommendations help shorten the time to mitigate or remediate vulnerabilities and drive compliance.
Organizations can lower their threat and vulnerability exposure by remediating the issues based on prioritized security recommendations. Each software has weaknesses that are transformed into recommendations and prioritized based on risk to the organization. As such, an organization can have the greatest effect on its exposure score by remediating the top security recommendations.
Security recommendations in Microsoft Defender Vulnerability Management
Each security recommendation includes actionable remediation steps. To help with task management, an organization can send the recommendation using Microsoft Intune and Microsoft Endpoint Configuration Manager. When the threat landscape changes, the recommendation also changes as it continuously collects information from your environment.
Tip
To get emails about new vulnerability events, see Configure vulnerability email notifications in Microsoft Defender for Endpoint.
Microsoft Defender XDR scores each device in an organization based on three important factors. These factors help customers focus on the right things at the right time:
Threat. Characteristics of the vulnerabilities and exploits in your organizations' devices and breach history. Based on these factors, the security recommendations show the corresponding links to:
- Active alerts
- Ongoing threat campaigns
- Their corresponding threat analytic reports
Breach likelihood. The organization's security posture and resilience against threats.
Business value. The organization's assets, critical processes, and intellectual properties.
You can access your organization's security recommendations in two ways. They both appear in the Microsoft Defender portal, under the Vulnerability Management group in the navigation pane:
- Recommendations. Selecting this option takes you to the Security recommendations page. This page contains a list of security recommendations for the threats and vulnerabilities found in the organization.
- Dashboard. Selecting this option enables you to view both the Top security recommendations and the company's Exposure score. The score is displayed side by side next to the company's Microsoft Secure Score for Devices. The goal of this comparison is to lower an organization's exposure from vulnerabilities, and increase the organization's device security to be more resilient against cybersecurity threat attacks. The top security recommendations list can help you achieve that goal. The Dashboard's Top security recommendations section lists the improvement opportunities for an organization. The opportunities are prioritized using the factors previously mentioned - threat, breach likelihood, and value. Selecting a recommendation takes you to the Security recommendations page with more details.
Security recommendations overview
The Security recommendations page displays the following information:
- Number of weaknesses found
- Related components
- Threat insights
- Number of exposed devices
- Status
- Remediation type
- Remediation activities
- Effect to your exposure score and Microsoft Secure Score for Devices
- Associated tags
On the Exposed devices graph, the colors change as the trend changes. If the number of exposed devices is on the rise, the color changes into red. If there's a decrease in the number of exposed devices, the color of the graph changes into green.
Note
Microsoft Defender Vulnerability Management shows devices that were in use up to 30 days ago. This design is different from the rest of Microsoft Defender for Endpoint. In that service, a device has an Inactive status if it hasn't been in use for more than seven days.
The Security recommendations page enables an organization to explore security recommendation options. Select the security recommendation that you want to investigate or process. The detail pane that appears for the selected recommendation allows you to choose any of the following options:
Open software page. Select the Open software page option to get more context on the software, include method of distribution. The information can include:
- Threat context
- Associated recommendations
- Weaknesses discovered
- Number of exposed devices
- Discovered vulnerabilities
- Names and details of devices with the software installed
- Version distribution
Remediation options. Submit a remediation request to open a ticket in Microsoft Intune for your IT Administrator to pick up and address. Track the remediation activity in the Remediation page.
Exception options. Submit an exception, provide justification, and set exception duration if you can't remediate the issue yet.
Note
When a user makes a software change on a Windows, Linux, or macOS device, it typically takes two to four hours for the security portal to display the data. It can take up to eight hours for the software change to appear in the security portal on iOS and Android devices. There may be situations where it takes longer. Configuration changes can take anywhere from 4 to 24 hours.
Investigate changes in device exposure or effect
A large jump in the number of exposed devices indicates a potential security vulnerability. Similarly, a sharp increase in an organization's exposure score and Microsoft Secure Score for Devices could also suggest that security risks increased. Therefore, it's essential to investigate any security recommendation that meets these criteria to ensure your organization stays protected.
- Select the recommendation and Open software page.
- Select the Event timeline tab to view all the impactful events related to that software. For example, new vulnerabilities or new public exploits. For more information, see Learn more about event timeline.
- Decide how to address the increase or your organization's exposure. For example, submitting a remediation request.
Request remediation
The Vulnerability Management's remediation capability bridges the gap between Security and IT administrators through the remediation request workflow. Security administrator can ask the IT Administrator to remediate a vulnerability from the Security recommendations
Select a security recommendation you would like to request remediation for, and then select Remediation options. Fill out the form and select Submit request. Go to the Remediation page to view the status of your remediation request.
Additional reading. For more information, see Learn more about how to request remediation.
File for exception
As an alternative to a remediation request when a recommendation isn't relevant at the moment, you can create exceptions for recommendations. Only users with "exceptions handling" permissions can add exception.
When you create an exception for a recommendation, the recommendation is no longer active. The recommendation state changes to Full exception or Partial exception (by device group).
Additional reading. For more information, see Learn more about exceptions.
To create an exception, select a security recommendation you would like to create an exception for, and then select Exception options.
Fill out the form and then submit it. To view all your exceptions (current and past), navigate to the Remediation page under the Vulnerability Management menu. Then select the Exceptions tab.
Additional reading. For more information, see Learn more about how to create an exception.
Report an inaccurate recommendation
You can report a false positive when you see any vague, inaccurate, incomplete, or already remediated security recommendation information.
Open the Security recommendation page.
Select the ellipsis icon (three dots) beside the security recommendation that you want to report, and then select Report inaccuracy.
On the detail pane that appears, select the Inaccuracy category from the drop-down menu. Then enter your email address and the details regarding the inaccuracy.
Select Submit. Microsoft Defender XDR immediately sends your feedback to Microsoft's threat and vulnerability management experts.