Configure Microsoft Defender for Endpoint in Microsoft Intune
Organizations can integrate Microsoft Defender for Endpoint with Microsoft Intune as a Mobile Threat Defense solution. Integration can help prevent security breaches and limit the effect of breaches within an organization.
Microsoft Defender for Endpoint works with devices that run:
- Android
- iOS/iPadOS
- Windows 10/11
To successfully use Microsoft Defender for Endpoint and Microsoft Intune in concert, you must:
- Establish a service-to-service connection between Microsoft Intune and Microsoft Defender for Endpoint. This connection lets Microsoft Defender for Endpoint collect data about machine risk from supported devices an organization manages with Intune.
- Use a device configuration profile to onboard devices with Microsoft Defender for Endpoint. An organization onboards devices to configure them to communicate with Microsoft Defender for Endpoint. By doing so, the organization can collect data to help assess its risk level.
- Use a device compliance policy to set the level of risk you want to allow. Microsoft Defender for Endpoint reports risk levels. The system classifies devices that exceed the allowed risk level as noncompliant.
- Use a conditional access policy to block users from accessing corporate resources from devices that are noncompliant. Conditional access policies can also block devices that exceed an organization's expected risk levels.
- Use app protection policies for Android and iOS/iPadOS to set device risk levels. App protection polices work with both enrolled and unenrolled devices.
When an organization integrates Microsoft Intune with Microsoft Defender for Endpoint, it can take advantage of Microsoft Defender for Endpoint's Threat and Vulnerability Management (TVM) module. It can also use Intune to remediate endpoint weakness identified by TVM.
Besides managing settings for Microsoft Defender for Endpoint on devices that enroll with Intune, you can manage Defender for Endpoint security configurations on devices that aren’t enrolled with Intune. This scenario is called Security Management for Microsoft Defender for Endpoint. It requires configuring the Allow Microsoft Defender for Endpoint to enforce Endpoint Security Configurations toggle to On. For more information, see MDE Security Configuration Management.
Example of using Microsoft Defender for Endpoint with Microsoft Intune
The following example helps explain how Microsoft Intune and Microsoft Defender for Endpoint work together to help protect organizations. For this example, Contoso already integrated Microsoft Defender for Endpoint and Intune.
Consider an event where someone sends a Word attachment with embedded malicious code to a Contoso user.
- The user opens the attachment, which enables the embedded code.
- An elevated privilege attack starts. An attacker from a remote machine has administrator rights to the victim's device.
- The attacker then remotely accesses the user's other devices. This security breach can affect the entire Contoso organization.
Microsoft Defender for Endpoint can help resolve security events like this scenario.
In this example, Microsoft Defender for Endpoint detects each of the actions that occurred:
- The device executed abnormal code.
- The device experienced a process privilege escalation.
- Opening the attachment injected malicious code into the device.
- The attacker executed an external command a remote computer or device (known as issuing a suspicious remote shell). Doing so raised some concerns or doubts about the intentions or legitimacy of the action.
Based on the actions from the device, Microsoft Defender for Endpoint classified the device as high-risk. It also included a detailed report of suspicious activity in the Microsoft Defender portal.
For this example, assume Contoso has an Intune device compliance policy that classifies devices with a Medium or High level of risk as noncompliant. As such, the compliance policy classified the compromised device as noncompliant. This classification allows Contoso's conditional access policy to block access from that device to Contoso's corporate resources.
For devices that run Android, you can use an Intune policy to modify the configuration of Microsoft Defender for Endpoint on Android. For more information, see Microsoft Defender for Endpoint web protection.
Prerequisites to integrating Microsoft Defender for Endpoint and Microsoft Intune
To use Microsoft Defender for Endpoint with Microsoft Intune, an organization must have the following subscriptions:
- Microsoft Defender for Endpoint. This subscription provides you access to the Microsoft Defender Security Center (ATP portal). For Defender for Endpoint licensing options, see Licensing requirements in Minimum requirements for Microsoft Defender for Endpoint and How to set up a Microsoft 365 E5 Trial Subscription.
- Microsoft Intune. This subscription provides access to Intune and the Microsoft Endpoint Manager admin center. For Intune licensing options, see Microsoft Intune licensing.
The following platforms support Microsoft Intune with Microsoft Defender for Endpoint:
- Android
- iOS/iPadOS
- Windows 10/11 (Hybrid Microsoft Entra ID Joined or Microsoft Entra ID Joined)
Important
Microsoft Intune is ending support for Android device administrator management on devices with access to Google Mobile Services (GMS) on August 30, 2024. After that date, device enrollment, technical support, bug fixes, and security fixes won't be available. If you currently use device administrator management, Microsoft recommends switching to another Android management option in Intune before support ends. For more information, read Ending support for Android device administrator on GMS devices.
Note
Azure Active Directory (Azure AD) is now Microsoft Entra ID. Learn more.
Enable Microsoft Defender for Endpoint in Intune
To set up the service-to-service connection between Intune and Microsoft Defender for Endpoint, you only need to enable Microsoft Defender for Endpoint a single time per tenant.
Complete the following steps to enable Microsoft Defender for Endpoint with Microsoft Intune:
You must begin by navigating to the Microsoft Intune admin center. To do so, on the Microsoft 365 admin center, select Show all in the navigation pane. Under the Admin centers group, select Endpoint Manager.
In the Microsoft Intune admin center, select Endpoint security in the navigation pane.
On the Endpoint security | Overview page, under the Setup section in the middle pane, select Microsoft Defender for Endpoint.
On the Endpoint security | Microsoft Defender for Endpoint page, scroll down to the Shared settings section and select Open the Microsoft Defender Security Center. This step opens the Microsoft Defender portal.
Tip
In the Intune admin center, if the Connection status at the top of the Microsoft Defender for Endpoint page is already set to Enabled, the connection to Intune is already active and the admin center displays different UI text for the link. In this event, select Open the Microsoft Defender for Endpoint admin console to open the Microsoft Defender portal. Then you can use the guidance in the following step to confirm that the Microsoft Intune connection is set to On.
In the Microsoft Defender portal, in the left-hand navigation pane, select Settings, then Endpoints, and then Advanced features.
Set the toggle switch for the Microsoft Intune connection setting to On.
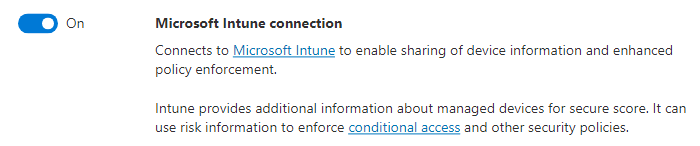
Select Save preferences.
Note
Once you establish the connection between Microsoft Defender for Endpoint and Microsoft Intune, the services should sync with each other at least once every 24 hours. You can configure the number of days without sync until Microsoft Intune considers the connection unresponsive in the Microsoft Intune admin center. Select Endpoint security, then Microsoft Defender for Endpoint, and then Number of days until partner is unresponsive.
Return to the Microsoft Defender for Endpoint page in the Microsoft Intune admin center.
To use Defender for Endpoint with compliance policies, configure the following options under Compliance policy evaluation for the platforms you support:
- Set Connect Android devices to Microsoft Defender for Endpoint to On.
- Set Connect iOS/iPadOS devices to Microsoft Defender for Endpoint to On.
- Set Connect Windows devices to Microsoft Defender for Endpoint to On.
When these configurations are On, applicable devices that you manage with Intune, and devices you enroll in the future, are connected to Microsoft Defender for Endpoint for compliance. For iOS devices, Defender for Endpoint also supports the following settings that help provide the Vulnerability Assessment of apps on Microsoft Defender for Endpoint for iOS. For more information about using the following two settings, see Configure vulnerability assessment of apps.
- Enable App Sync for iOS Devices. Set to On to allow Defender for Endpoint to request metadata of iOS applications from Intune to use for threat analysis purposes. The iOS device must be MDM-enrolled and provide updated app data during device check-in.
- Send full application inventory data on personally owned iOS/iPadOS Devices. This setting controls the application inventory data that Intune shares with Defender for Endpoint when Defender for Endpoint syncs app data and requests the app inventory list. When set to On, Defender for Endpoint can request a list of applications from Intune for personally owned iOS/iPadOS devices. This list includes unmanaged apps and apps that were deployed through Intune. When set to Off, data about unmanaged apps isn’t provided. Intune does share data for the apps that were deployed through Intune.
For more information, see Mobile Threat Defense toggle options.
To use Defender for Endpoint with app protection policies for Android and iOS/iPadOS, configure the following under App protection policy evaluation for the platforms you use:
- Set Connect Android devices to Microsoft Defender for Endpoint to On.
- Set Connect iOS/iPadOS devices to Microsoft Defender for Endpoint to On.
To set up an integration Microsoft Defender for Endpoint for compliance and app protection policy evaluation, you must have a role that includes Read and Modify for the Mobile Threat Defense permission in Intune. The Endpoint Security Manager built-in admin role for Intune has these permissions included. For more information about both MDM Compliance Policy Settings and App Protection Policy Settings, see Mobile Threat Defense toggle options.
Select Save.
When you integrate a new application to Intune Mobile Threat Defense and enable the connection to Intune, Intune creates a classic conditional access policy in Microsoft Entra ID. Each MTD app you integrate, including Microsoft Defender for Endpoint or any of Microsoft's MTD partners, creates a new classic conditional access policy. You can ignore these policies; however, you shouldn't edit, delete, or disable them.
If you delete the classic policy, you must delete the connection to Intune that was responsible for its creation. Once you delete the connection, you must then set it up again. Doing so recreates the classic policy. The system doesn't support migrating classic policies for MTD apps to the new policy type for conditional access.
Organizations should take into account the following considerations related to classic conditional access policies for MTD apps:
- Intune MTD uses them to require the registration of devices in Microsoft Entra ID. Doing so ensures they have a device ID before communicating to MTD partners. Devices require the ID to successfully report their status to Intune.
- They have no effect on any other Cloud apps or resources.
- They differ from the conditional access policies you can create to help manage MTD.
- By default, they don't interact with other conditional access policies that organizations use for evaluation.
To view classic conditional access policies, in the Microsoft Entra admin center, select Conditional Access and then Classic policies.