A Guide for Enabling Federated Authentication on Windows Azure WebRoles… using Windows identity Foundation
UPDATE: the guide here has long been superceded by hands-on labs (specifically this one) and whitepapers on the topic. Please use those instead.
==========================================
Federating with customer and partners, SSO using existing company identities, authentication externalization, multiple auth factors, claims-based identity… those are all things that the good architects, developers & sysadmins want to be able to do on-premises, in the cloud and in whatever lies between.
Our products are still in prerelease status, however we know that many of you are experimenting with the new possibilities offered by the cloud… and not being able to include federated identity in your scenario can be a big limiting factor.
In order to help you with that Hervey, architect on the Federated Identity team, took a good look at the current bits at your disposal (Windows Azure July 2009 CTP, Geneva Framework Beta 2) and developed some code extending Windows Identity Foundation can help you to overcome some of the incompatibilities so that you can experiment with claims based identity in Windows Azure. Then I took that code and made it into a step-by-step guide, that can be used by *anybody* for enabling passive federation in a Windows Azure WebRole for experimental purposes and can be used by identity experts for gaining insights on what are the attention points that require workarounds in the currently available bits.
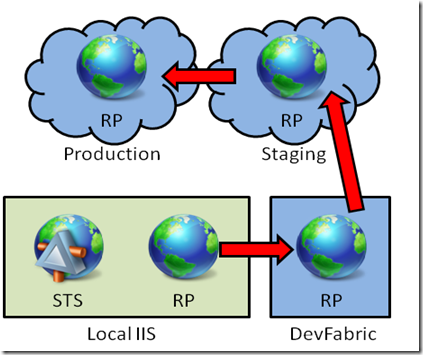
Here there’s a summary of the steps followed by the guide. You start by creating an ASP.NET website (RP) in the local IIS and auto-generate an STS for it, all by using the usual Windows Identity Foundation tools. Once verified that it works as expected in the local IIS, you create a Cloud Service project and transfer the RP settings to a new WebRole: then you test it in the DevFabric. Upon successful testing you publish & test the WebRole in staging and finally in production.
Note that the guide aims at describing the most basic of the scenarios and requiring minimal system requirements, but you can easily use it as starting point for building something more realistic, for example by using your own AD FS 2.0 as the identity provider instead of the development STS we leverage.
The guide package is available for download on Code Gallery, direct link here.
We will keep updating this guide and its supporting code (Microsoft.IdentityModelPlus) as new releases of the products involved become available; we also plan to release other guides for addressing different scenarios, such as the active case (claims-based identity with WCF services in WAz), perhaps even an STS in the cloud! We look forward to your feedback: please remember that this code is NOT production ready, and it is released to you for the sole purpose of allowing you to experiment with identity and cloud based scenarios.
That’s all: time to jump in action! Download the guide package and have fun with identity and the cloud :-) Happy coding!
Comments
Anonymous
August 04, 2009
This is an interesting scenario but I find Geneva Server in the cloud more compelling. Also, has MS ever thought about putting AD in the cloud. AD for Azure or perhaps AD LDS for Azure would be a compelling argument against what I see companies using Google for as their user store.Anonymous
August 05, 2009
Interesting guide! However, I get an error, when I am creating the local STS (in task 1, option 8) saying “Some or all identity references could not be translated”. If I then manually apply a reference to “Microsoft.IdentityModel”, then I am able to build the solution, but I get a null reference (for the IClaimsIdentity (ici in sourcecode)in Default.aspx.cs) when running it. The STS is created in IIS, but if I try and reapply it from Visual Studio (Use an existing STS), then the “test location” fails, because the XML file (FederationMetadata.xml) is empty! Any idea? Thanks! PerAnonymous
August 06, 2009
Fantastic guide Vittro. You saved my day for a POC. I have used AD FS (Formerly Geneva Server) for my Claim based azure application's identity provider. Yes, security aspects are still there to be resolved but for a POC, it is working beautifully. Thanks to Hervey and you. SusinghAnonymous
August 07, 2009
Thanks for the guide. I am trying to achieve the following: Use LiveID via the .NET Access Control Service for a Web Role in Azure. Does this guide address this fully? If not, any hints on where I can find it (the Azure Issue Tracker example is not working with latest Azure SDK).Anonymous
August 24, 2009
Very useful information! Thanks. I want to use WLID authentication using ACS for my web role on Azure. How can I configure ACS rules for this sample?