Microsoft Teams: Limit access to only managed devices and reduce risk!
It's amazing watching the adoption journey of Microsoft teams among organizations and how it is quickly becoming a mission critical tool. For me, it's mission critical because of the collaboration and teamwork that's occurring inside, and the data that is being stored is quickly becoming the heartbeat of many organizations and their project teams. There is one challenge however with storing proprietary and sensitive data in Microsoft Teams, as users are accessing the data using the Teams app on not just their PC or laptop, but mobile devices and other (even unmanaged) computers as they perform their job – if that data is leaked/spilled/exposed or compromised, it could put the organization at risk, and as IT Professionals we need to help protect against this risk.
Not to worry – Azure Active Directory Conditional Access to the rescue! Using AzureAD Conditional Access, we will ensure Microsoft Teams is only accessed on devices that are managed, whether they are Active Directory domain joined, Azure AD joined or managed by Intune. This is very easy and straight forward to setup, let's take a look together.
Important: Conditional Access requires AzureAD Premium. I won't be discussing licensing requirements in this blog post, please reference this article for more information.
In the Azure Portal, I am going to create a new AzureAD Conditional Access policy with the following configuration:
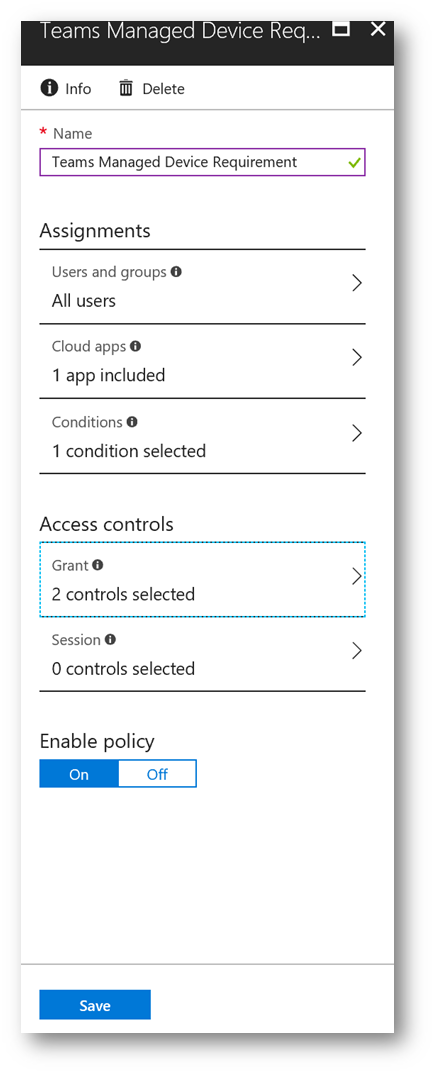
Users and Groups: "All Users"
Cloud apps: (Include) "Microsoft Teams"
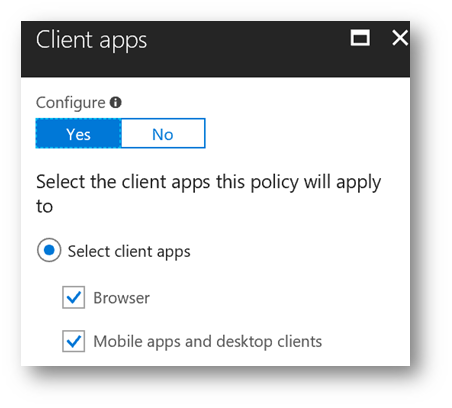
Conditions: Client Apps -> Configure "Yes" -> Select Client Apps -> check "Browser" and "Mobile apps and desktop clients"
Access Controls: Grant Access -> Check "Require Domain Joined" and "Require device to be marked as compliant"

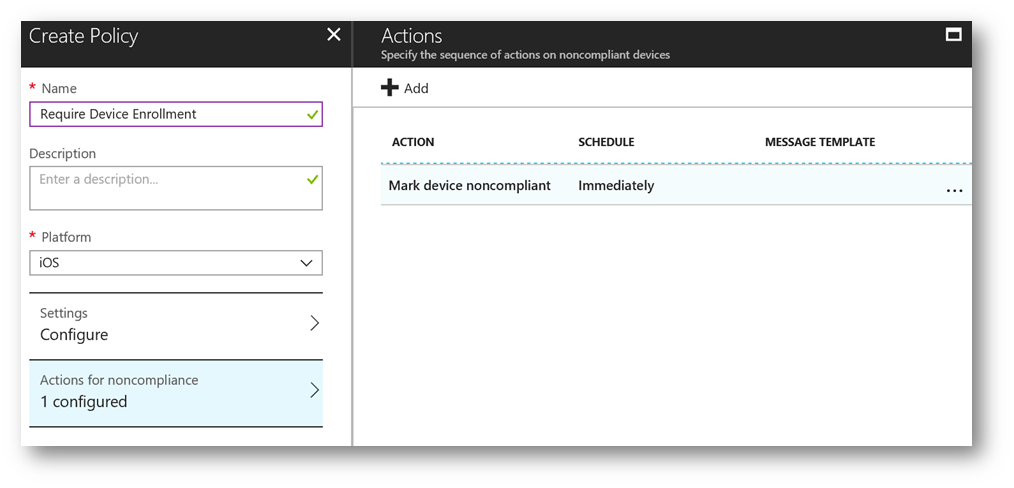
Important: If you check "Require device to be marked as compliant" you must create a device compliance policy in Intune. This will ensure devices such as iOS, Android, Windows, Mac that try to access Microsoft Teams using either the app, client or website must be Intune MDM enrolled (which requires an Intune subscription). If accessed from a Windows PC and is Active Directory domain joined or Azure AD joined, require MDM enrollment will not apply. Here's what an example Device Compliance policy looks like in Intune:
Back to Conditional Access…
Enable Policy: "On"
Now the policy is created, let's test this out. It should deny access to Microsoft Teams.
From a Windows PC that is unmanaged (not joined to Azure AD, Active Directory, or MDM enrolled):
From a Web browser:
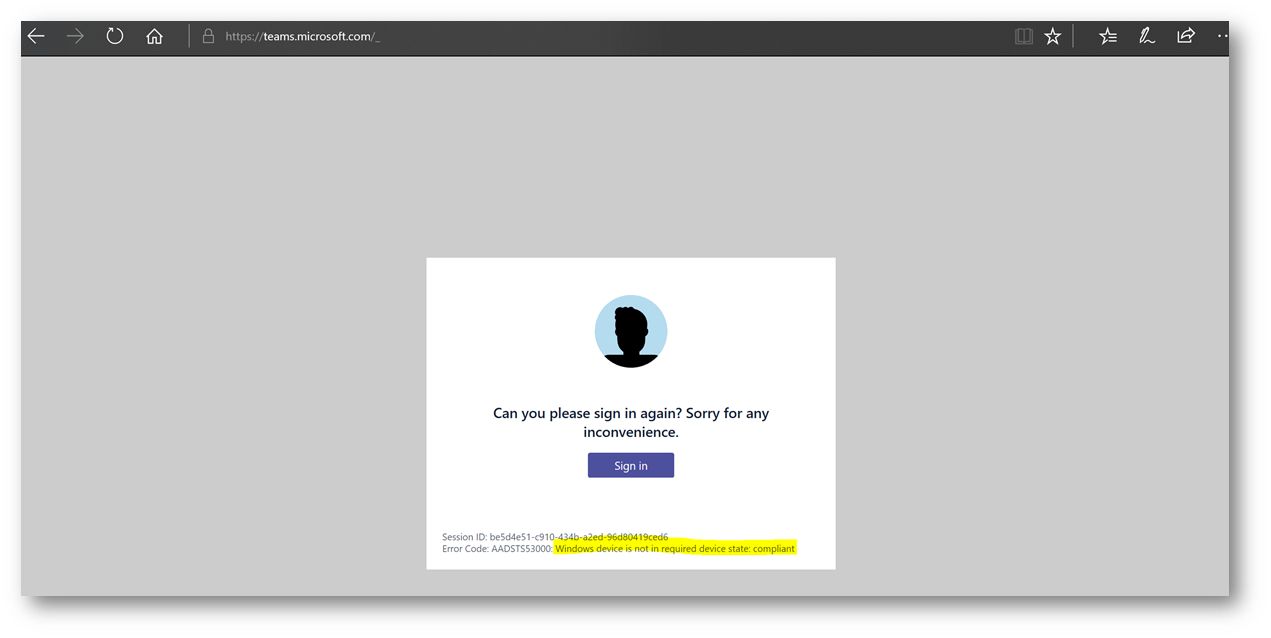
Notice the error reads "Windows device is not in required device state: compliant"
From the Microsoft Teams Windows Desktop Application:
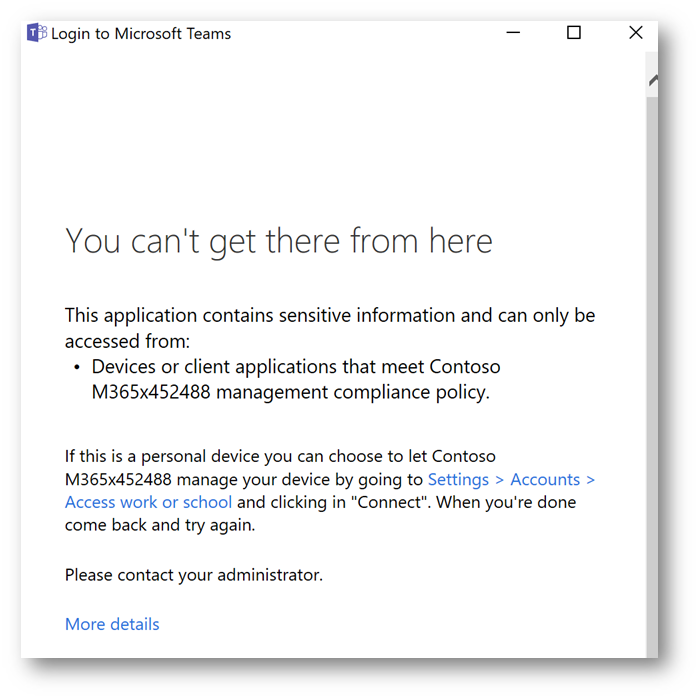
Next, from an iPad Pro (iOS) that is unmanaged (not MDM enrolled):
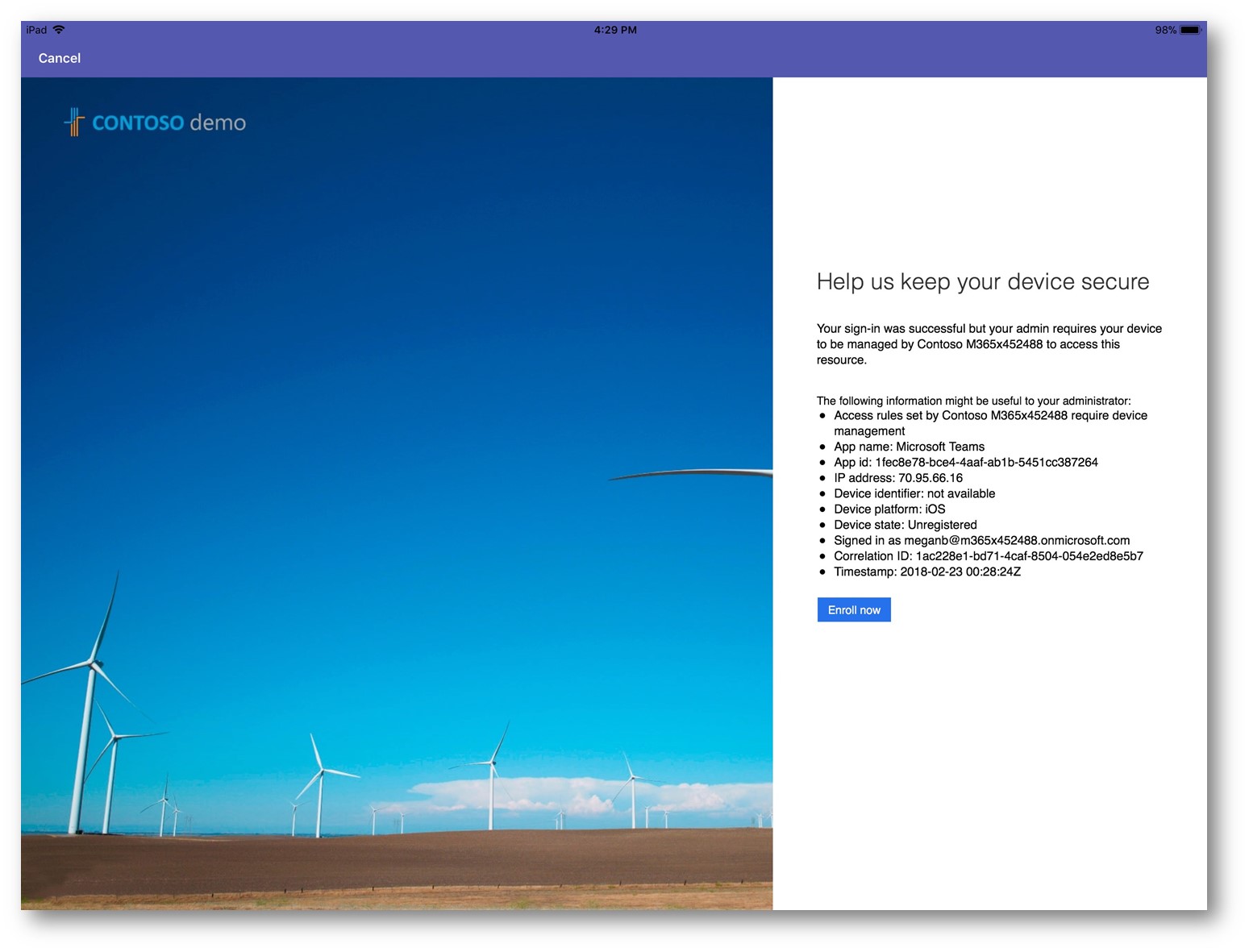
Notice it gives me the option to enroll in MDM (Intune), pretty cool!
This is a quick and easy way to ensure that users are using Microsoft Teams on managed devices, where IT can control the configuration of the device and ensure the device is healthy and compliant. What's more is this policy can be reversed and disallow users from using the Teams web client if that becomes a requirement. For additional fun, check out Microsoft Teams: Manage it using Mobile Application Management (MAM) and Microsoft Teams: Restrict Usage with Azure AD Conditional Access
If you have questions or feedback, let me know in the comments below. Enjoy and have fun!