Gaining visibility to “shadow IT” and discovering cloud apps in use today
You may not realize it, but your organization is already operating in the cloud. Even if your IT department hasn't deployed cloud services yet, your employees already have, and your organization is 100% responsible for the security and compliance of that data. This is known as "shadow IT", where an organization is using application services, but IT has not yet approved their use – and it creates a major challenge for IT and a major risk for the organization.
As an IT professional for 15+ years, one of my top priorities is to help my fellow IT professionals understand shadow IT. This represents a major threat to us, individually, because as business groups and teams within our organizations continue to go outside of IT for their technology needs – this contributes to the growing irrelevance of us (IT) and de-values what we do for the organization. In addition, if the data stored or used by these cloud applications is compromised – the business will turn back to IT to "solve and fix" the problem (which can be challenging when you have no control over that application and didn't realize it was being used in the first place).
(In my experience, many IT professionals and senior IT leadership such as the IT Director or CIO may already be aware there is a shadow IT problem – but they may not know it's severity or where to start the remediation process)
Sure, you can attempt to "block" shadow IT – but blocking won't solve the issue. Users will always find another way, and blocking will just inhibit innovation, productivity and creativity that your users want (among other more important things such as employee recruiting/retention, and organization competitiveness). Therefore, it's important we discover what apps are in use today and develop a strategy to control those apps and to protect the data they access and use – then we can talk about what other apps we may want to block that aren't approved.
There's three steps for which to create an action plan to mitigate this challenge and risk of shadow IT:
- Gain visibility and discover what applications are in use, authentication being used, and security and compliance of those applications. From here you can associate a level of risk and determine if controlling or blocking makes sense.
- Through control of applications use, policies can be developed (that are aligned to your organization's compliance requirements) that define which applications are approved and how/what data can be in the cloud.
- By protecting against threats, define a baseline for application access, and analyze abnormal patterns/behaviors that stray from that baseline. Understand if anomalies are actual threats and develop a strategy to address them.
(for an additional overview on shadow IT, download the free Microsoft ebook here)
In this blog post, I will take you through the first step in this three step process of Visibility using Microsoft Cloud App Security (CAS) that is part of the Enterprise Mobility + Security (EMS) suite of products. For a quick overview of CAS, watch this 2-minute video. The goal of this post is to inspire you to learn more about how you can develop a strategy for addressing shadow IT in your environment – and will not be a complete "how to" guide.
IMPORTANT:
I will not be discussing licensing and how to purchase CAS nor will I be discussing a detailed approach for how to plan, deploy and operate CAS in your environment. However, I do need to note that for the cloud application ranking to work, you must have Cloud App Security (E5) – this will not work with E3 (for more information see this ). For additional CAS topics, please refer to the excellent documentation we have located here.
Visibility – Discovering cloud applications users are accessing
To discover the cloud applications your users are accessing, Microsoft Cloud App Security (CAS) can be used. This provides an agentless and unobtrusive way to gain the visibility required, and is fast and easy to do. This is performed by uploading (manually or automatically) logs from your internet proxies or firewalls to CAS for an analysis. CAS will analyze the traffic using a catalog of some 15,000 cloud applications and provide a risk score to help you assess the risk of that app within your organization. For more information on the firewalls and proxies that are supported, see Set Up Cloud Discovery.
As an example, let's take a look at how to do this:
Login to the Cloud App Security portal at https://portal.cloudappsecurity.com. Click the Discover menu, then select Create snapshot report
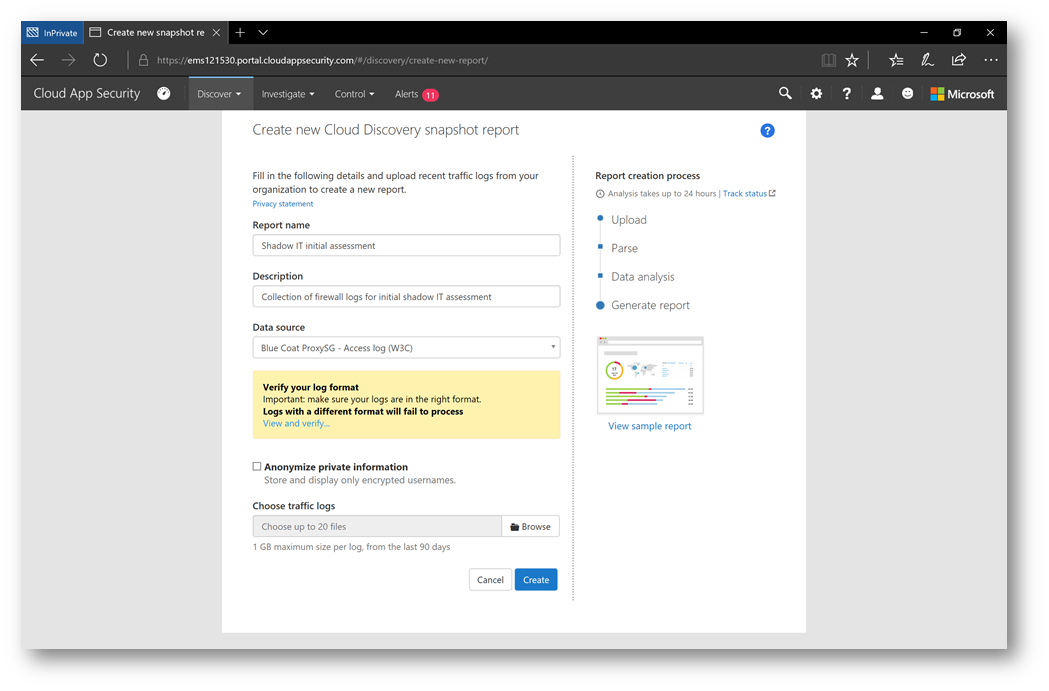
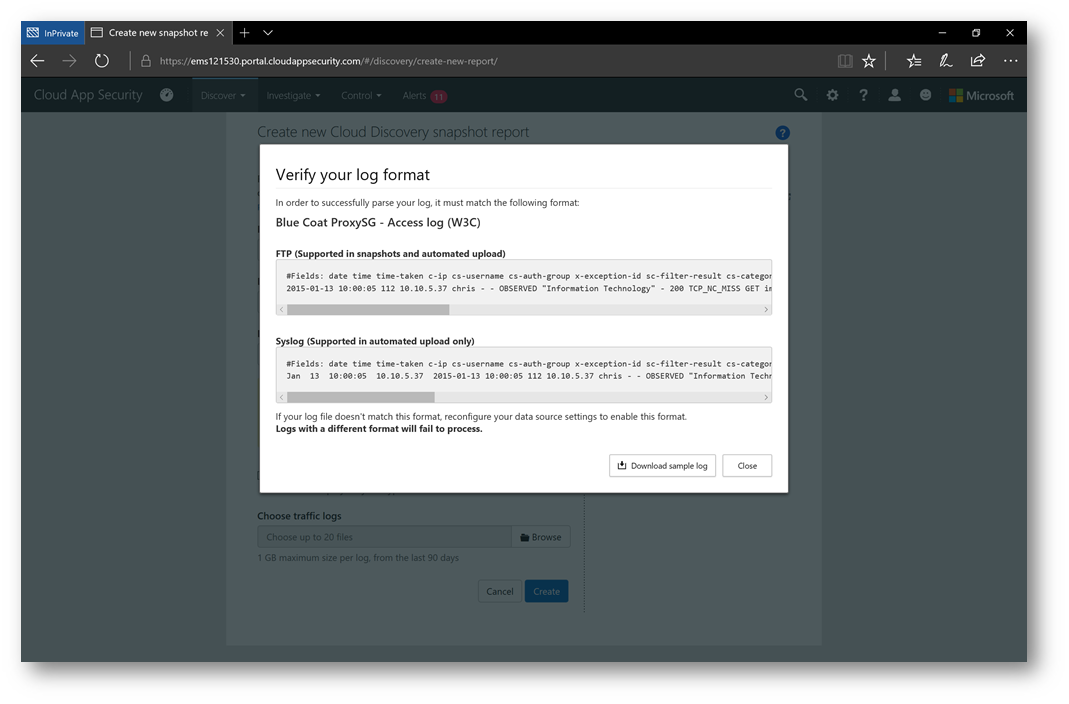
In the Create new Cloud Discovery snapshot report, fill out the required fields and select a data source. For my example I will choose a Blue Coat proxy access log. Now, if this were a real report, under Choose traffic logs I would browse for that log file to upload. However, for my example I will click view and verify… and then select download sample log – and then upload that sample log by clicking Create:
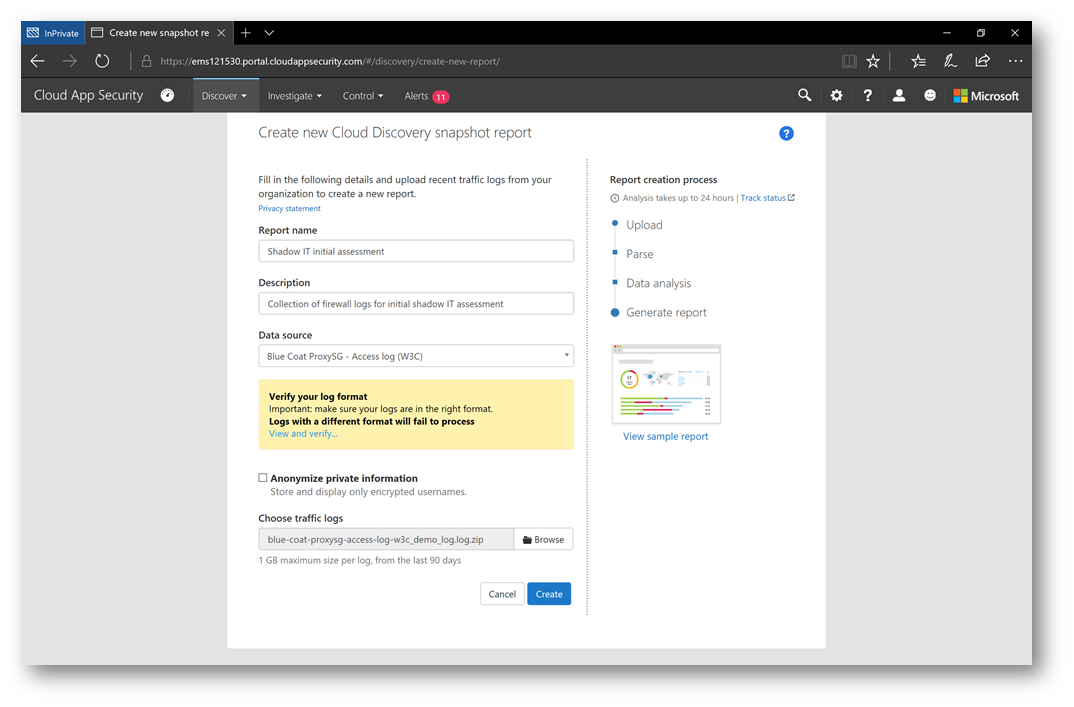
Note: Notice the Anonymize private information check box. This is interesting, and can mask the actual usernames of your users to keep them private or can be used in a security investigation. Click here to learn more.
Once uploaded, the data will start to be parsed and processed. It's important to note this process may take up to 24 hours. When the processing is completed, the status of the report will change to Ready. Click on Ready to then view the report.
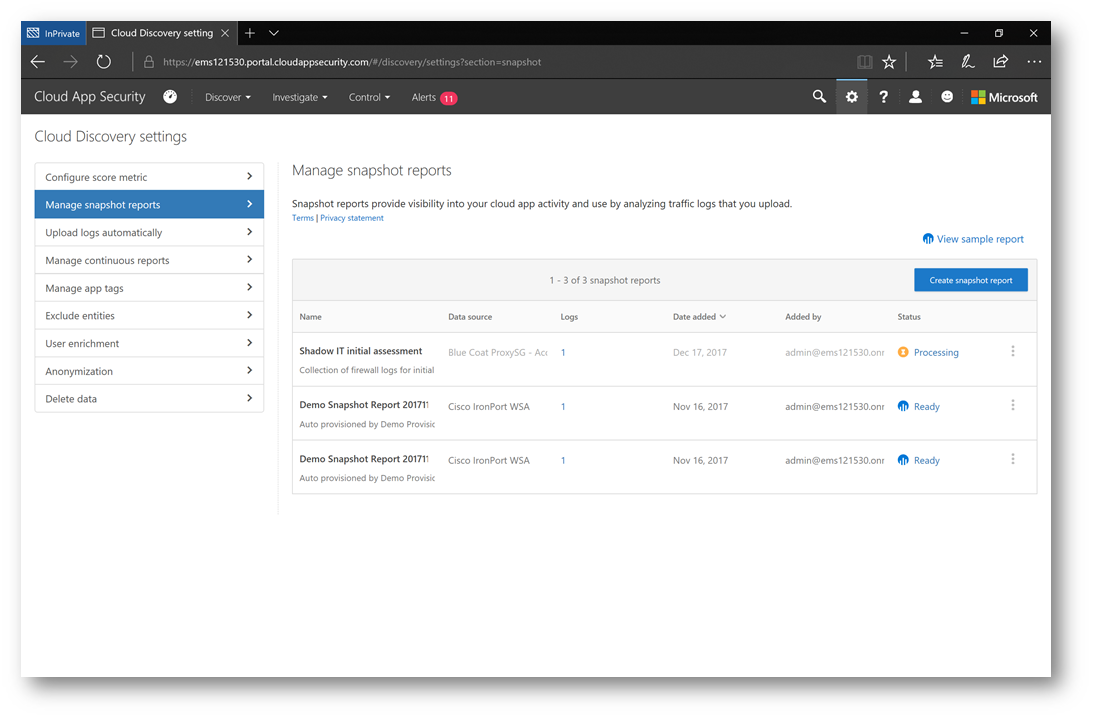
For demonstration purposes, while that report is processing, let's take a look at another report that is ready to view by clicking on Ready:
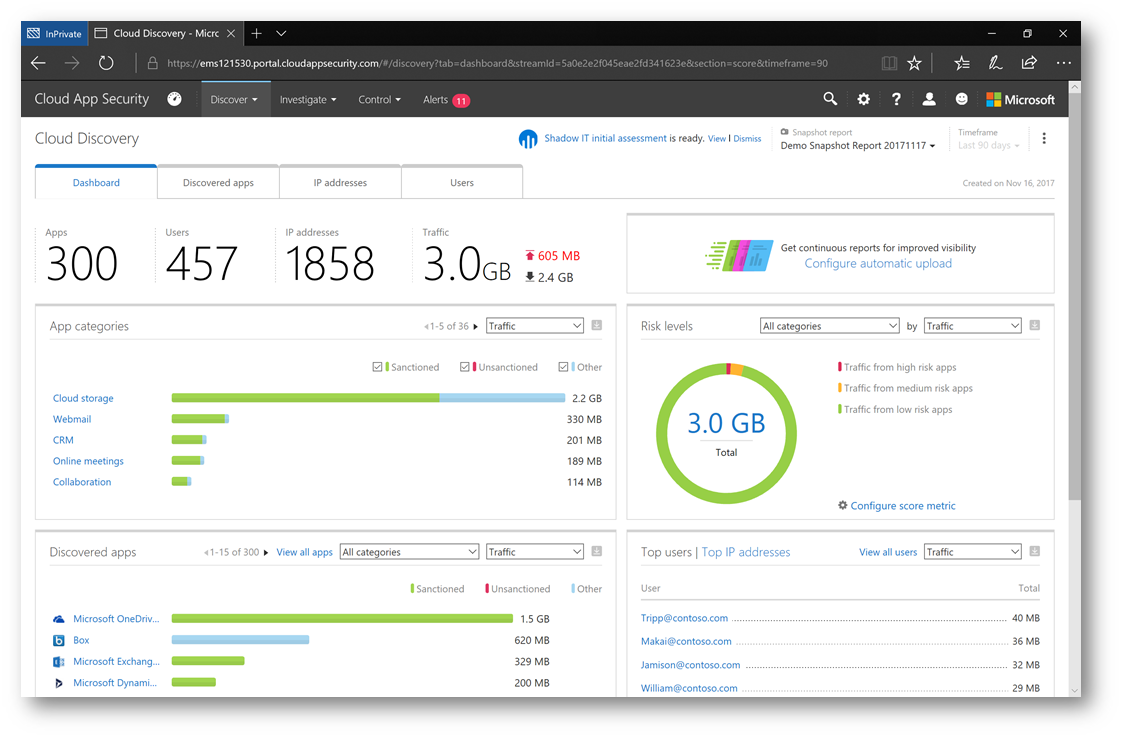
As you can see, the dashboard tab provides an excellent overview into the type of applications, specifically which applications that users are using – and even the top users who are using them. In the Discovered apps pane of the dashboard, let's take a closer look at the cloud applications users are using. I'm going to change the sort from Traffic to Users so we can view how many users are using each app.
Note: There's plenty more to the reports than what I am covering here, please refer to the documentation I previously mentioned for additional information.
IMPORTANT: Clicking on the  icon in any of the dashboard panes will allow you to export the data to a .csv file. This is useful to continue to parse through the data and generate custom visuals (perhaps for a presentation to a customer or your IT leadership).
icon in any of the dashboard panes will allow you to export the data to a .csv file. This is useful to continue to parse through the data and generate custom visuals (perhaps for a presentation to a customer or your IT leadership).
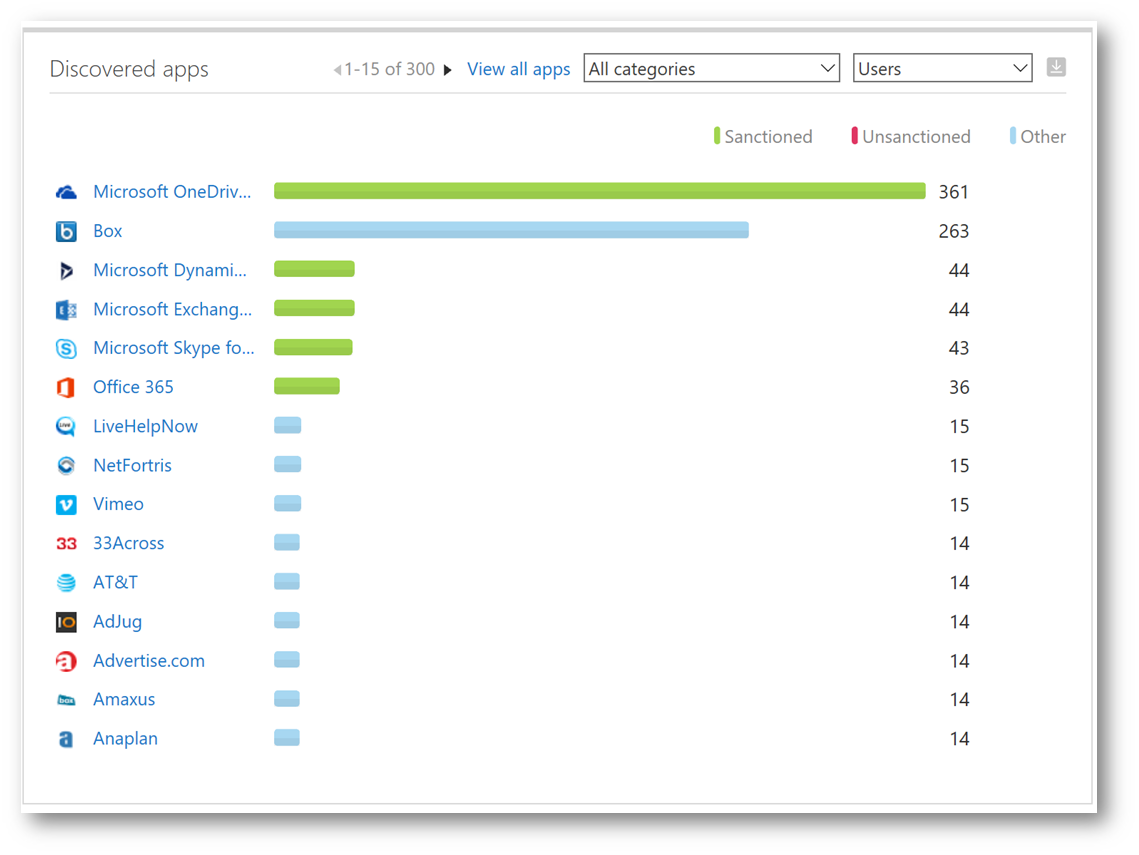
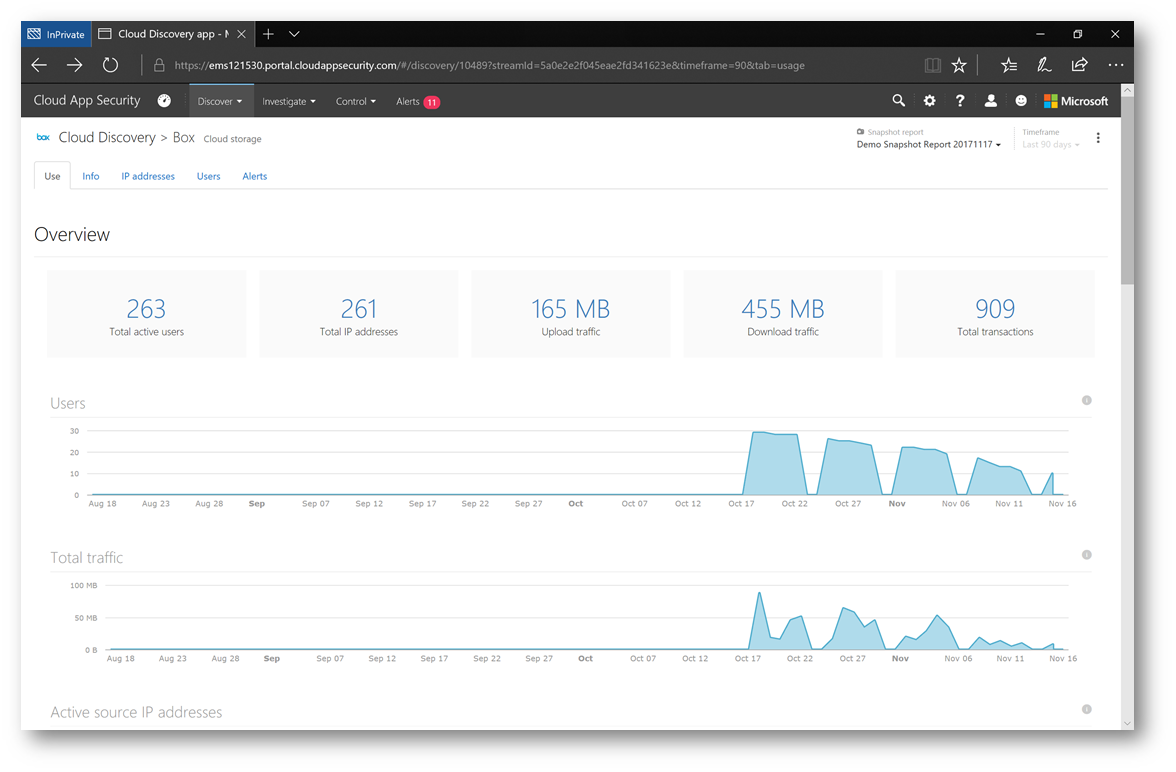
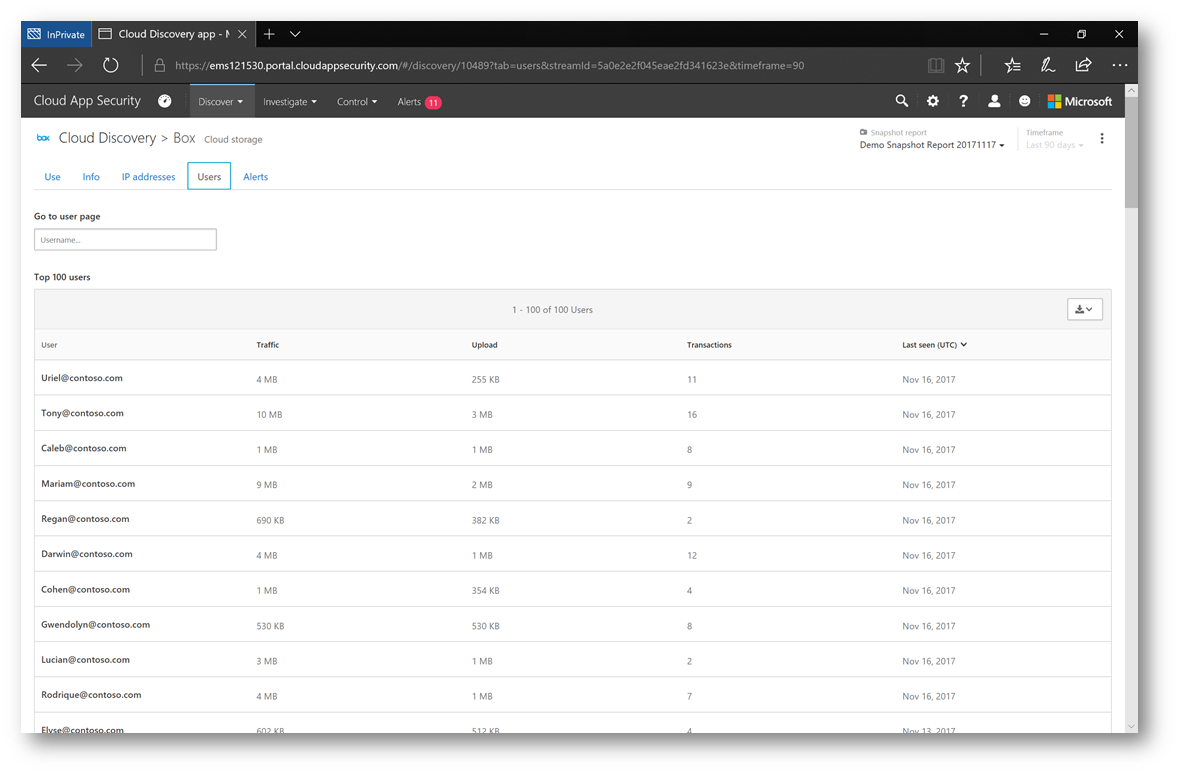
These applications are dived into three categories: Sanctioned (approved), Unsanctioned (non-approved), and Other. Within Contoso, OneDrive for Business is approved – and that's reflected below. However, the biggest unsanctioned application in use is Box, which is not approved. Let's click on Box to examine additional details. Below we can see details as to how many users, how much data traffic and even which users are using the application (by clicking on the Users tab):
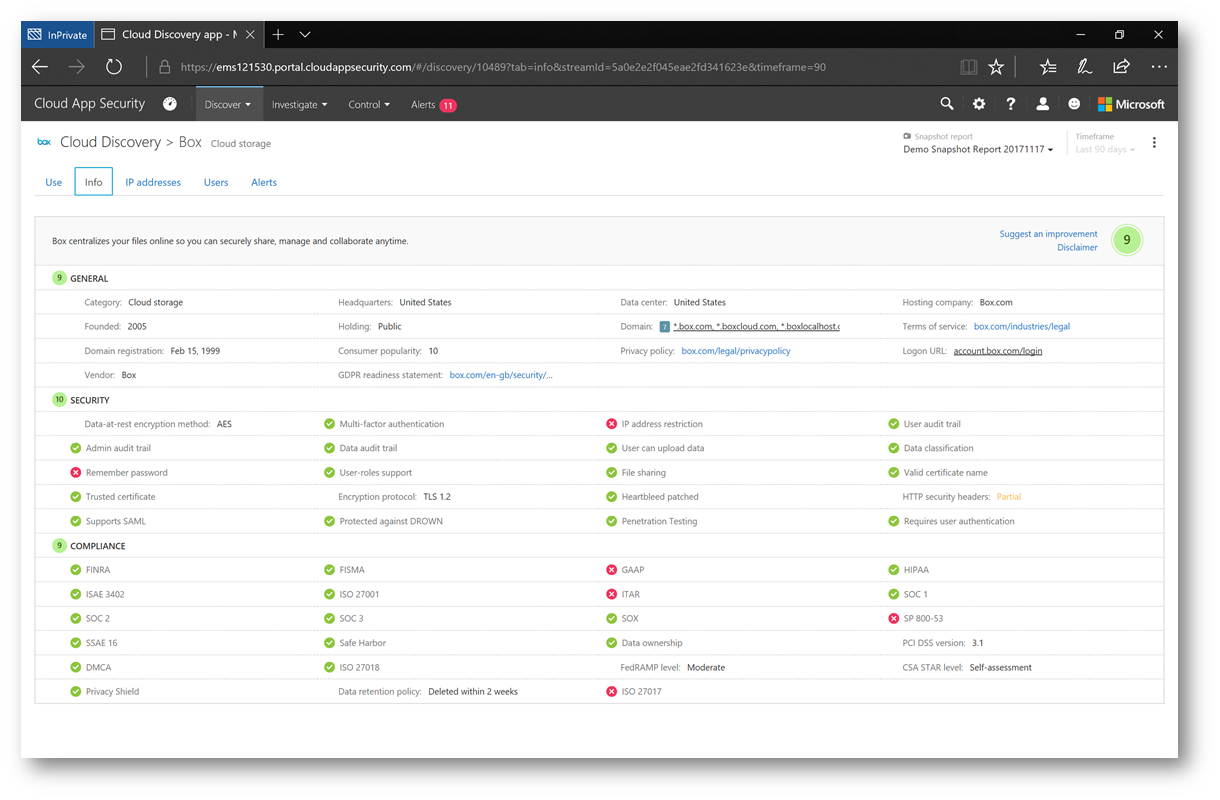
Clicking on the Info tab will give me details about the cloud application such as information about the company and various security and compliance details that will help me to understand the risk this application may have in my environment. Note, in the upper right corner the  , this is a risk score that CAS assigns. Cloud applications are evaluated against a catalog of over 15,000 applications and are ranked and scored based on more than 60 risk factors such as:
, this is a risk score that CAS assigns. Cloud applications are evaluated against a catalog of over 15,000 applications and are ranked and scored based on more than 60 risk factors such as:
- Holding status of the company (private/public)
- Encryption methods
- Industry and regulatory compliance certification status (i.e. SOX, SSAE,etc)
These risk scores can be customized and overridden, and you can even suggest an improvement on a risk if you disagree. Each item is ranked on a scale of 1-10 and carries a certain percentage weight for the overall risk score (also on a scale of 1-10)
Note: For more detailed information on risk scores click here.
Clicking the  next to an item, will display additional details of the risk:
next to an item, will display additional details of the risk:
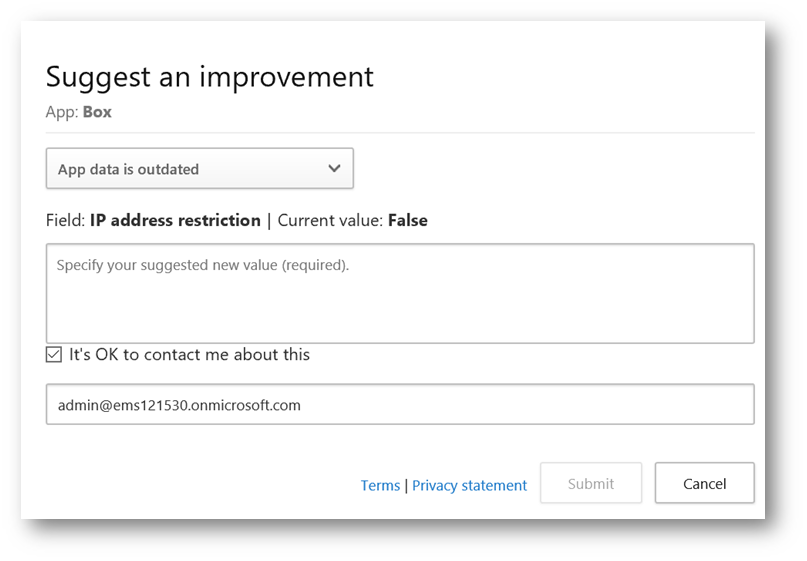
Clicking the  icon next to an item will display a window where you can give feedback such as specifying a suggested new value. For example, if you find a discrepancy in CAS when compared to the vendor's documentation on their website. When submitting feedback you can suggest a new risk factor, update the score , or specify the app is outdated – and also provide your email address to follow up if you like:
icon next to an item will display a window where you can give feedback such as specifying a suggested new value. For example, if you find a discrepancy in CAS when compared to the vendor's documentation on their website. When submitting feedback you can suggest a new risk factor, update the score , or specify the app is outdated – and also provide your email address to follow up if you like:
Speaking of risk factors, I mentioned how this can be customized. Clicking on the 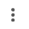 in the upper right corner and selecting Cloud Discovery Settings will display settings for your discovery – starting with Configuring Score Metric. For each of the categories such as Founded there is a slider that allows me to specify that category's importance (and weight to the score). Sliding all the way to the left will ignore that category. This could be useful based on the type of applications you find in your discovery, your industry and other preferences.
in the upper right corner and selecting Cloud Discovery Settings will display settings for your discovery – starting with Configuring Score Metric. For each of the categories such as Founded there is a slider that allows me to specify that category's importance (and weight to the score). Sliding all the way to the left will ignore that category. This could be useful based on the type of applications you find in your discovery, your industry and other preferences.
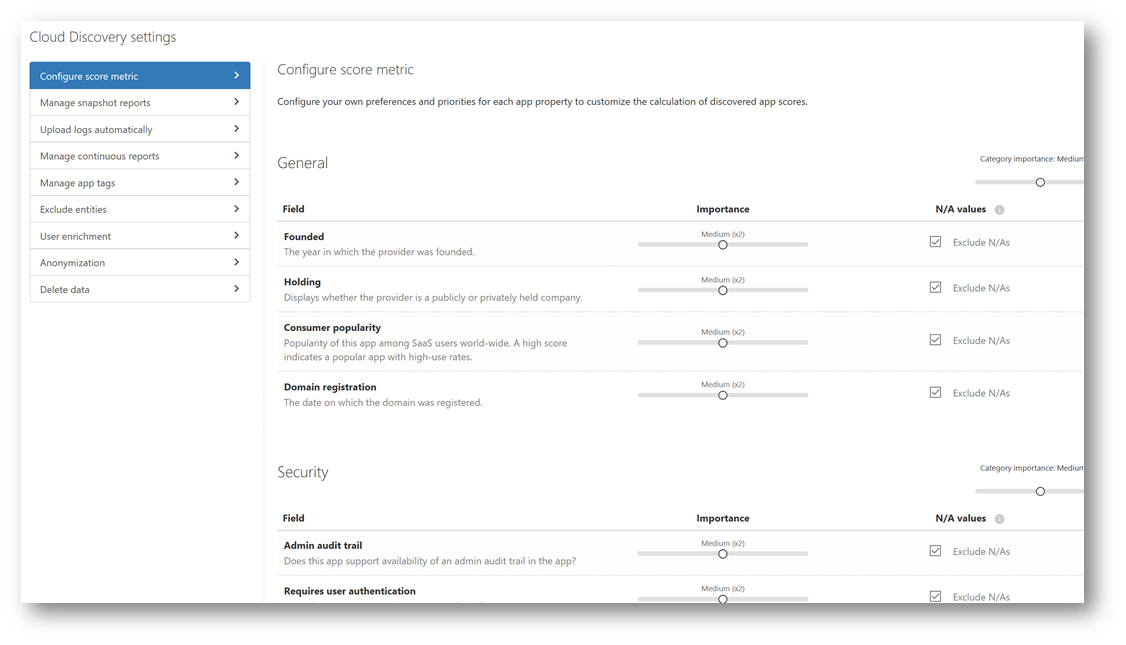
Clicking on the Discovery menu and selecting Cloud Discovery Dashboard will take us back to the main dashboard. Notice on the right side the doughnut chart, let's explore that a little deeper. I'm going to change the sort from Traffic to Apps. As I hover the cursor over "High, Medium and Low risk apps" the chart will change indicating how many apps fall into one of those three risk categories, further allowing me to develop an analysis of shadow IT within my environment. As I use that analysis to build a strategy for how to control and protect, filtering on the severity level (i.e. high) could allow me to prioritize which apps I want to solve for first.
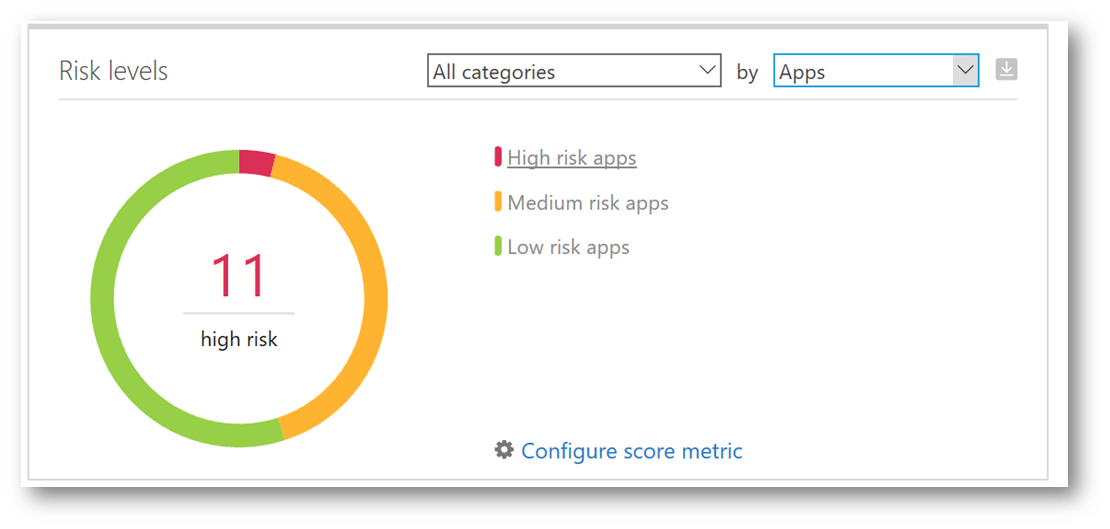
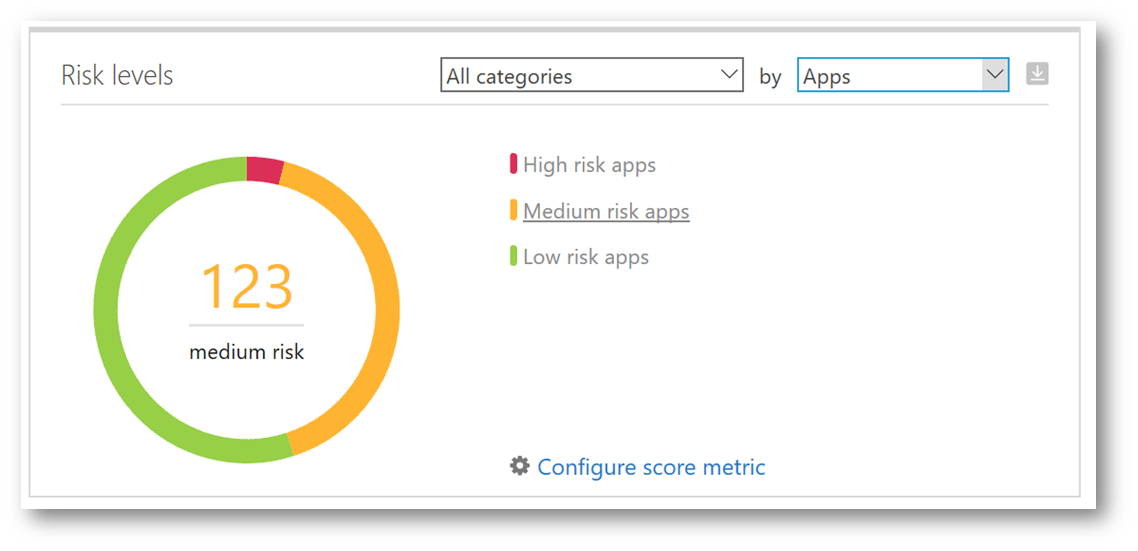
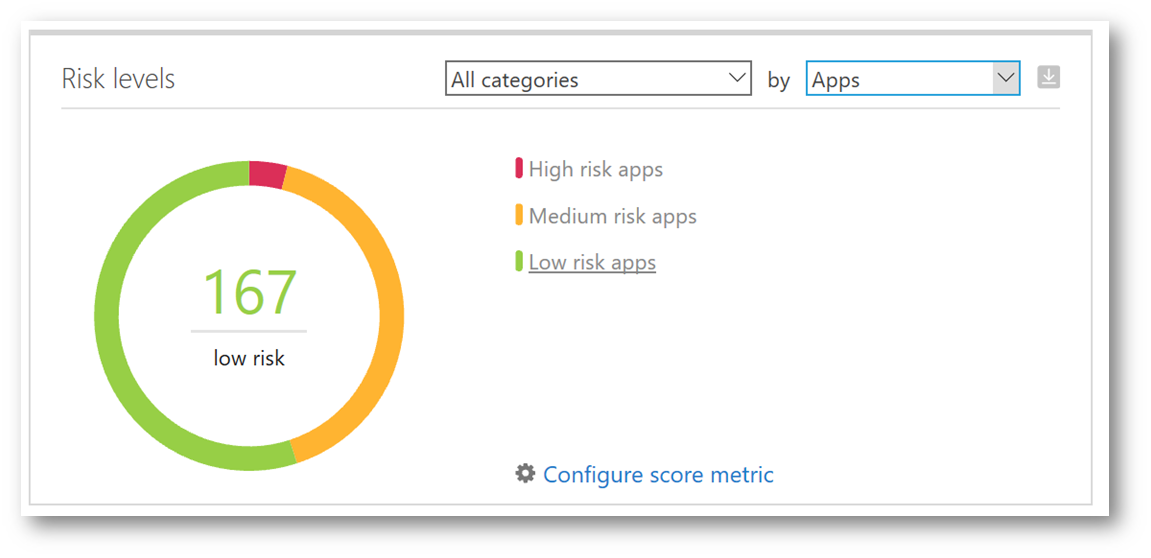
Clicking on High risk apps will display a breakdown of those discovered apps that meet the high risk criteria, on the Discovered Apps tab. Additional control of these apps can be performed from here such as tagging it as Sanctioned or Unsanctioned, and generating a block script (which is really cool!).
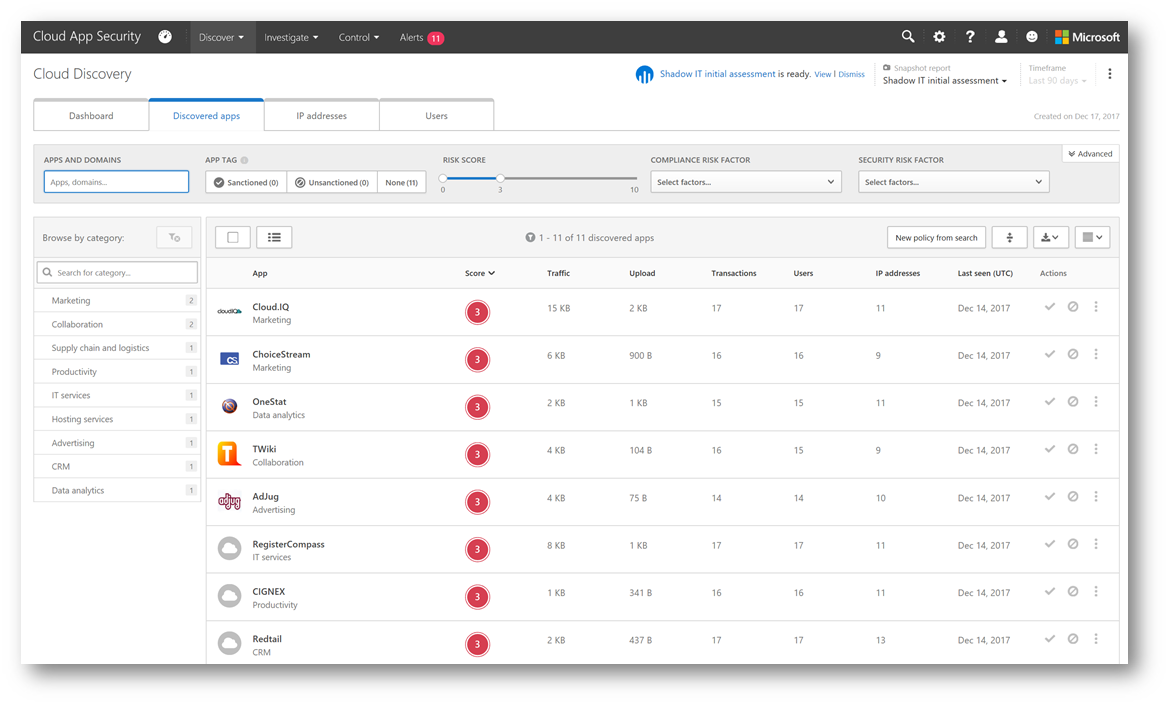
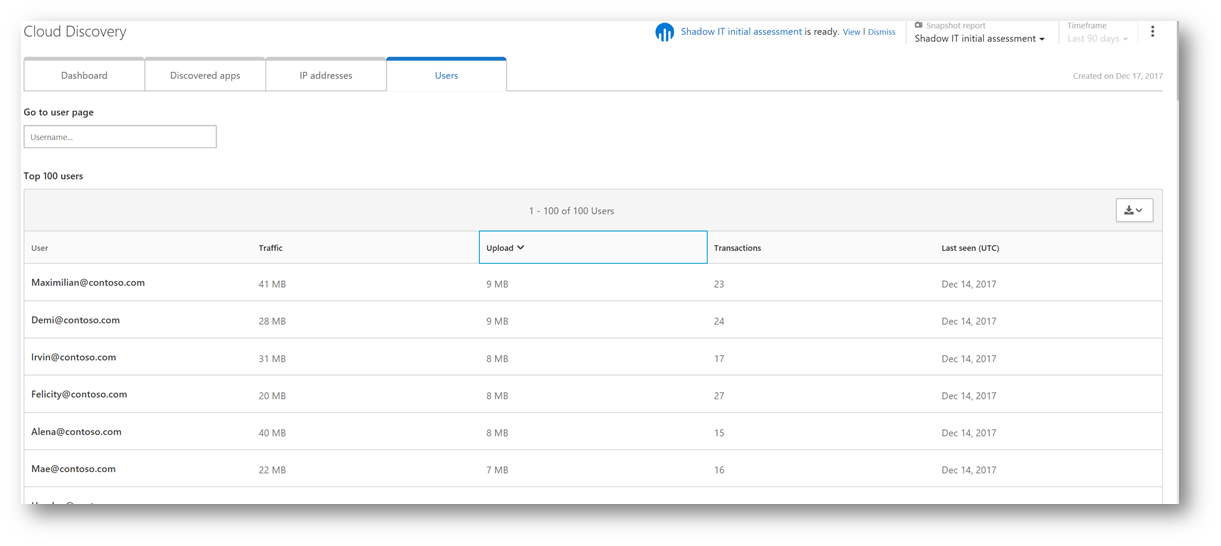
Lastly, as part of our initial discovery let's examine the users who are using these discovered apps. Clicking on the Users tab, will display the top 100 users in the environment who are accessing these apps. From here, I will sort based on highest upload (to see who is uploading the most amount of organizational data to the app) and then click that user to examine details – for example it appears Maximillian@contoso.com is uploading the most amount of data.
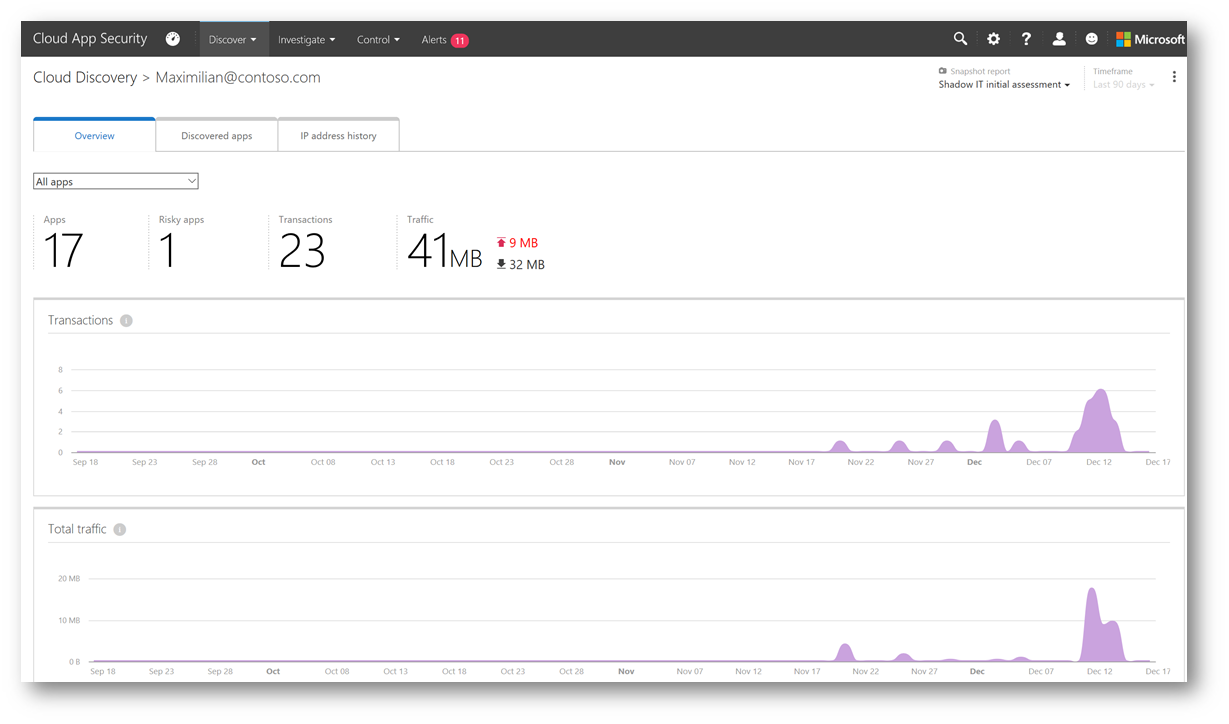
Clicking on Maximillian@contoso.com will display a dashboard specific to discovery of the apps that user is using and an overview of how much traffic and transactions are being performed.
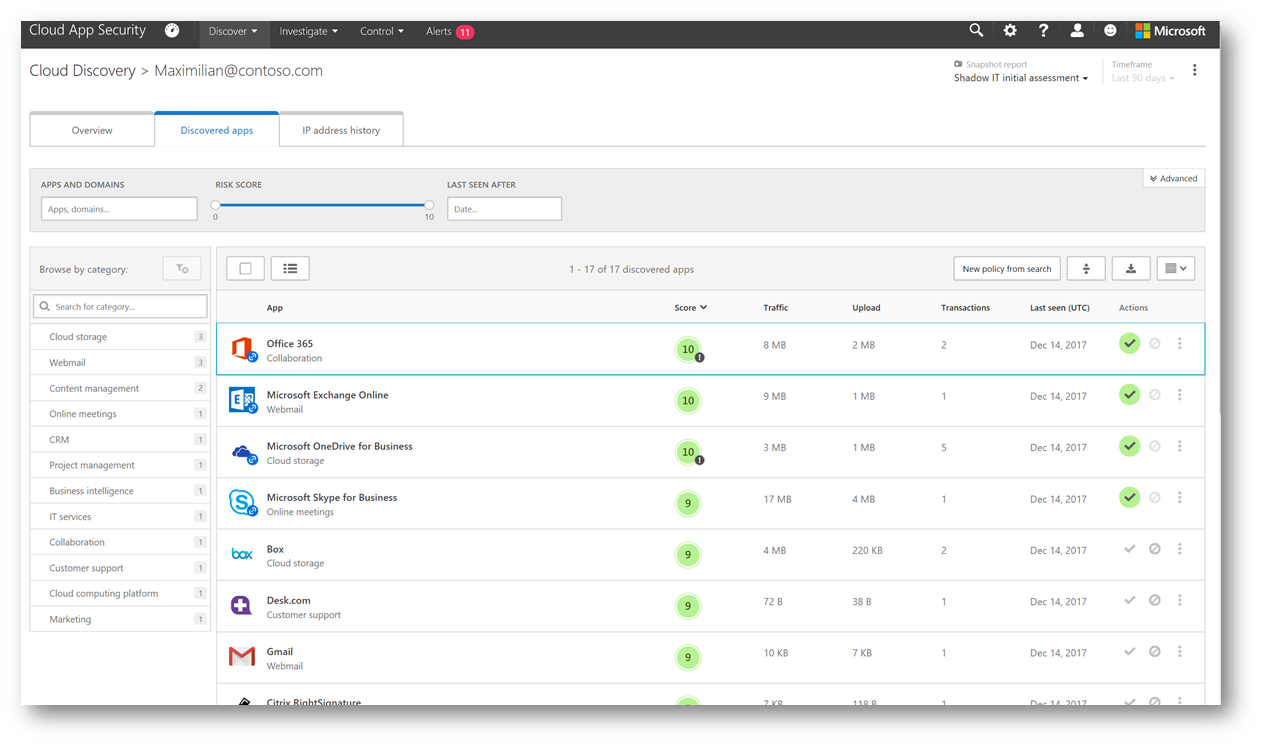
Clicking on the Discovered Apps tab allows me to see the cloud applications this particular user is using:
Conclusion
As you can see, Microsoft Cloud App Security can provide you with insights into both sanctioned (approved) and non-sanctioned (unapproved) cloud applications that your users are using to help you develop a strategy for mitigating shadow IT and ultimately enabling the users to do their best work, using the apps they want. In this blog post we covered at a high level the initial discovery, and in future blog posts I will discuss how to implement controls around those applications to search them for data, and provide protection policies for the data in those apps. Enjoy!