AIP: I know when you open my document, and I can revoke access! (Compliance + Sales = Seller Hero)
Have you sent an email to someone (perhaps a customer) that contained an important document and wish you could see if they have opened it? What if you accidently sent the document to the wrong audience, wouldn't it be nice to revoke access? Perhaps it's a sales quote and you want it to expire in 30 days? Well the future is here, and this is possible today using Azure Information Protection (AIP), included with Enterprise Mobility + Security, Microsoft 365, or a plan that includes AIP with Office 365. In this blog post we will explore from an end-user perspective how they can see if their recipient has opened the document, and how to revoke it's access.
Azure Information Protection enables your organization to classify it's data and apply security policy to that data, but more importantly gives the end-users visibility and control over how the data is consumed. This tool is extremely powerful for both IT and end-users, because it allows you to not only discover what data is in the organization, but classify it based on some criteria (i.e. Confidential, Secret, Top Secret and risk to organization) and apply policies that govern who can access what data based on the classification assigned.
This can be especially useful when you need help complying with regulations like GDPR. For more information about Azure Information Protection, I suggest reading the IT Pro documentation: What is Azure Information Protection? As I will not be covering full technical details here, such as how to configure the protection policy. I also highly suggest reviewing the AIP client user guide HERE.
You're telling me I can see who has opened my document?
Yes! If I send you a document, spreadsheet, PDF, PowerPoint, etc – I can see if you have opened that file, doesn't matter how it was sent either (email, file transfer over Skype, posted to Teams,etc). I can also see who has opened the file, by their identity, regardless if they were the intended recipient. I simply control this using the site https://track.azumrerms.com
When I browse to the site, and login, I can see a list of the documents I have protected using Azure Information Protection:
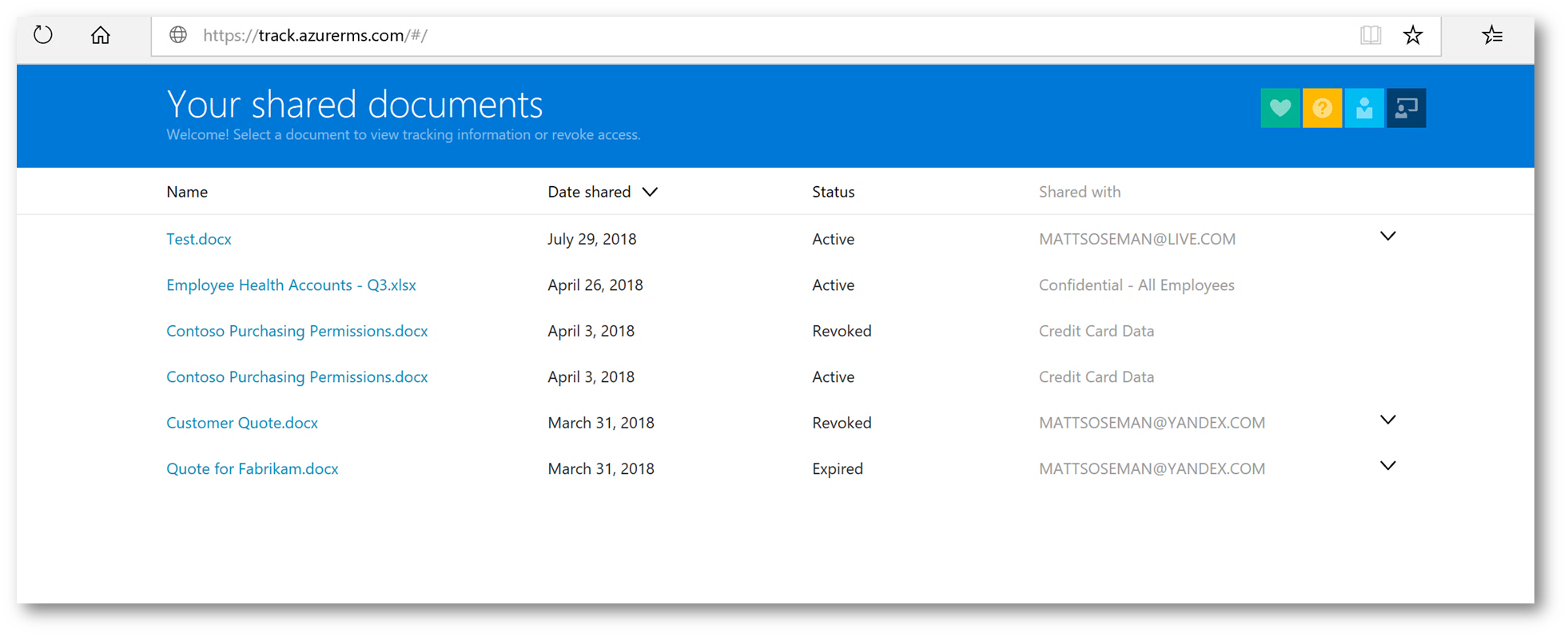
Clicking on one of the documents, I have access to see how many views (and by whom), how many (and by whom) were denied access to the document, among other controls. Let's click on the list at the top menu
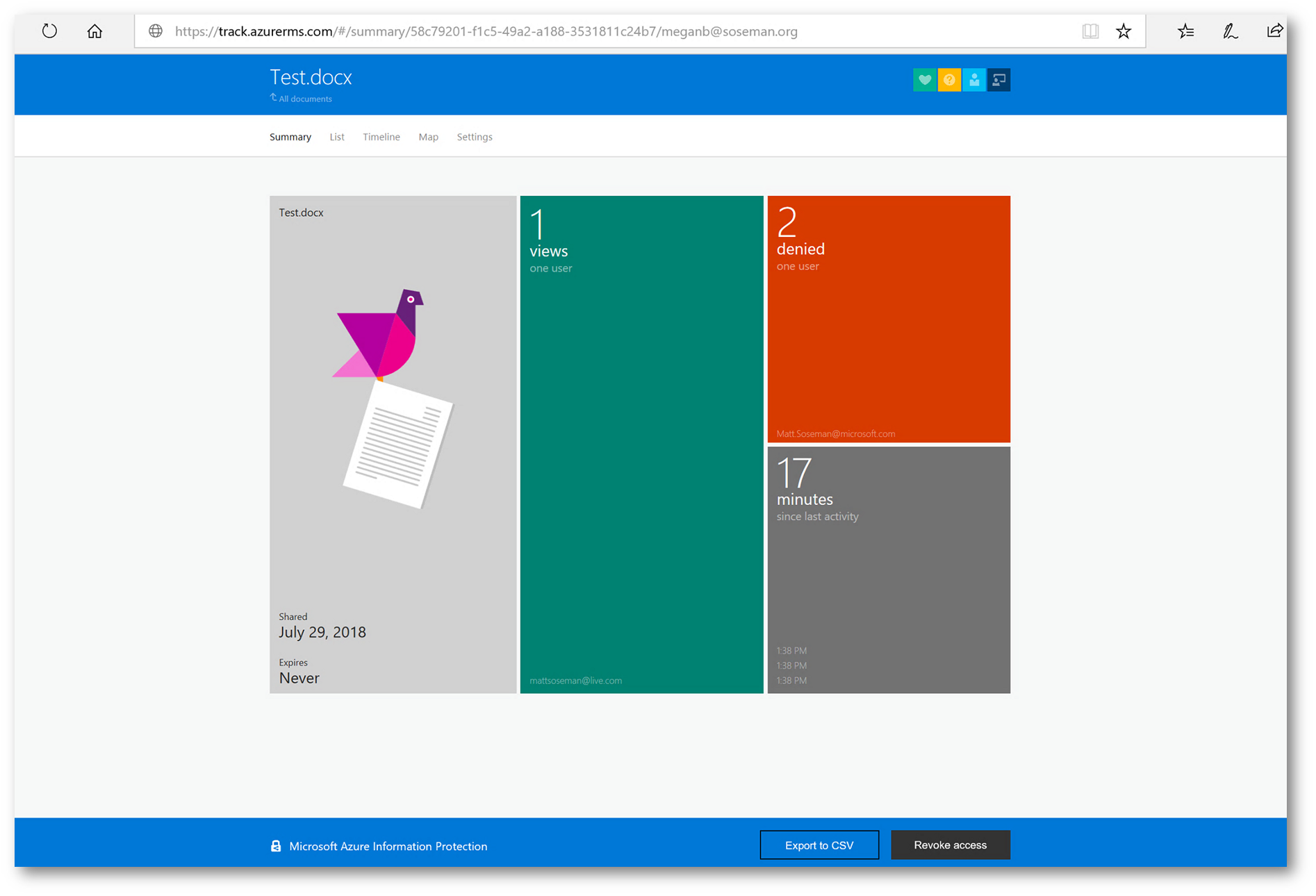
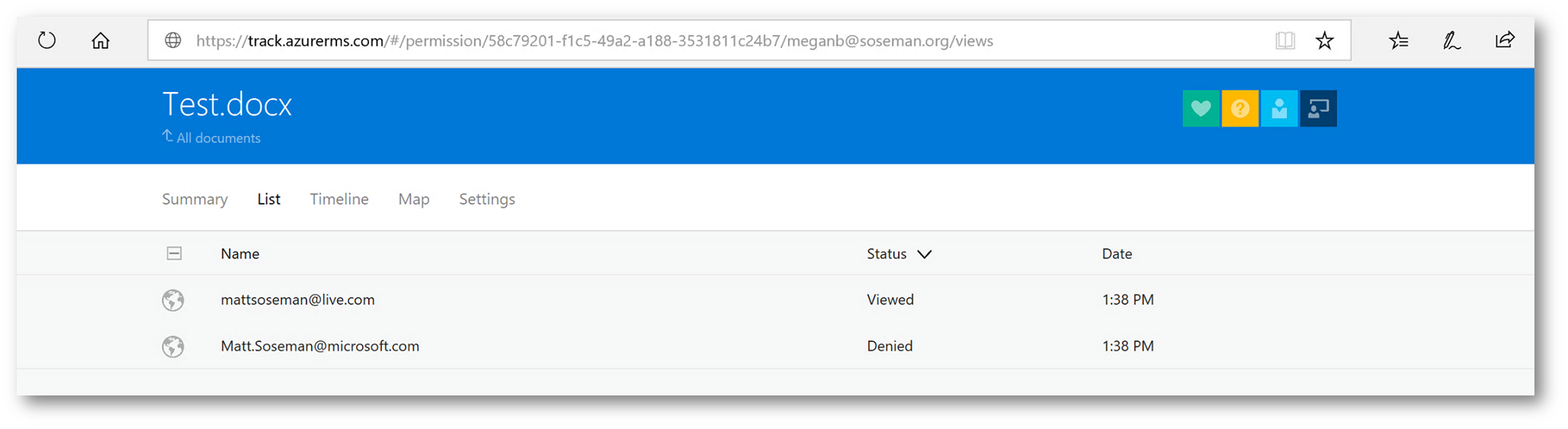
Here I can see who (by user identity, as signed into the Office applications) have attempted to access the document and whether or not they were successful. This is extremely useful!
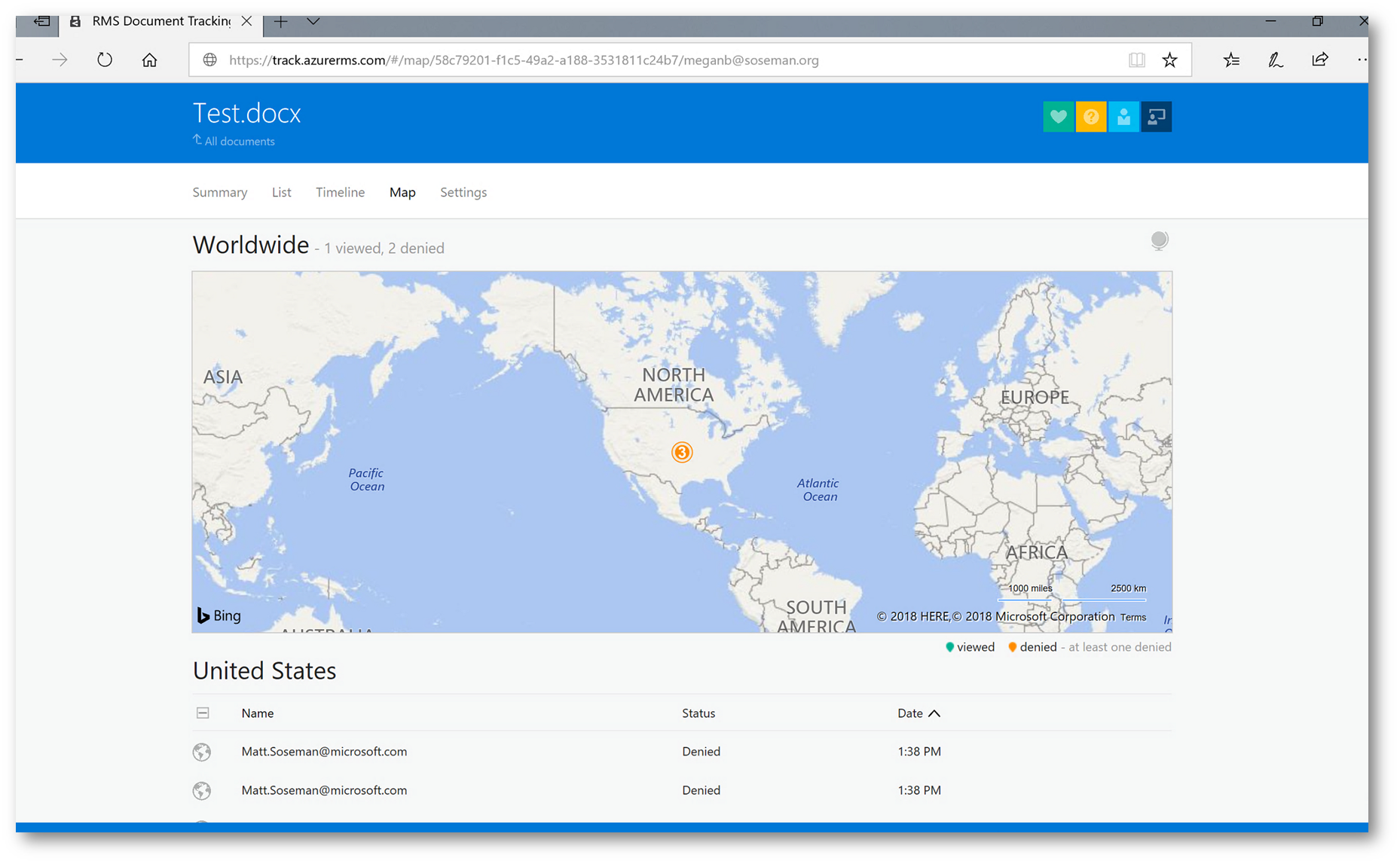
Clicking on Map at the top menu I can see where in the world the document has been accessed. If all my users were accessing from the US, and then one user was from outside the US – this could indicate a stolen identity or data breach, and I may want to revoke access to the document.
Clicking on Settings from the top menu, allows me to do something REALLY COOL: Whenever the document is accessed – I can receive an email notification! Why is this really cool? I might be a salesperson and this document might be a proposal to a client. If I never receive an email indicating you never opened the document, then I know you may not be interested and I need to adjust my sales approach. This is one of the features of the product (in my opinion) that sells itself. Having that type of intelligence can be critical to the closure of a deal.
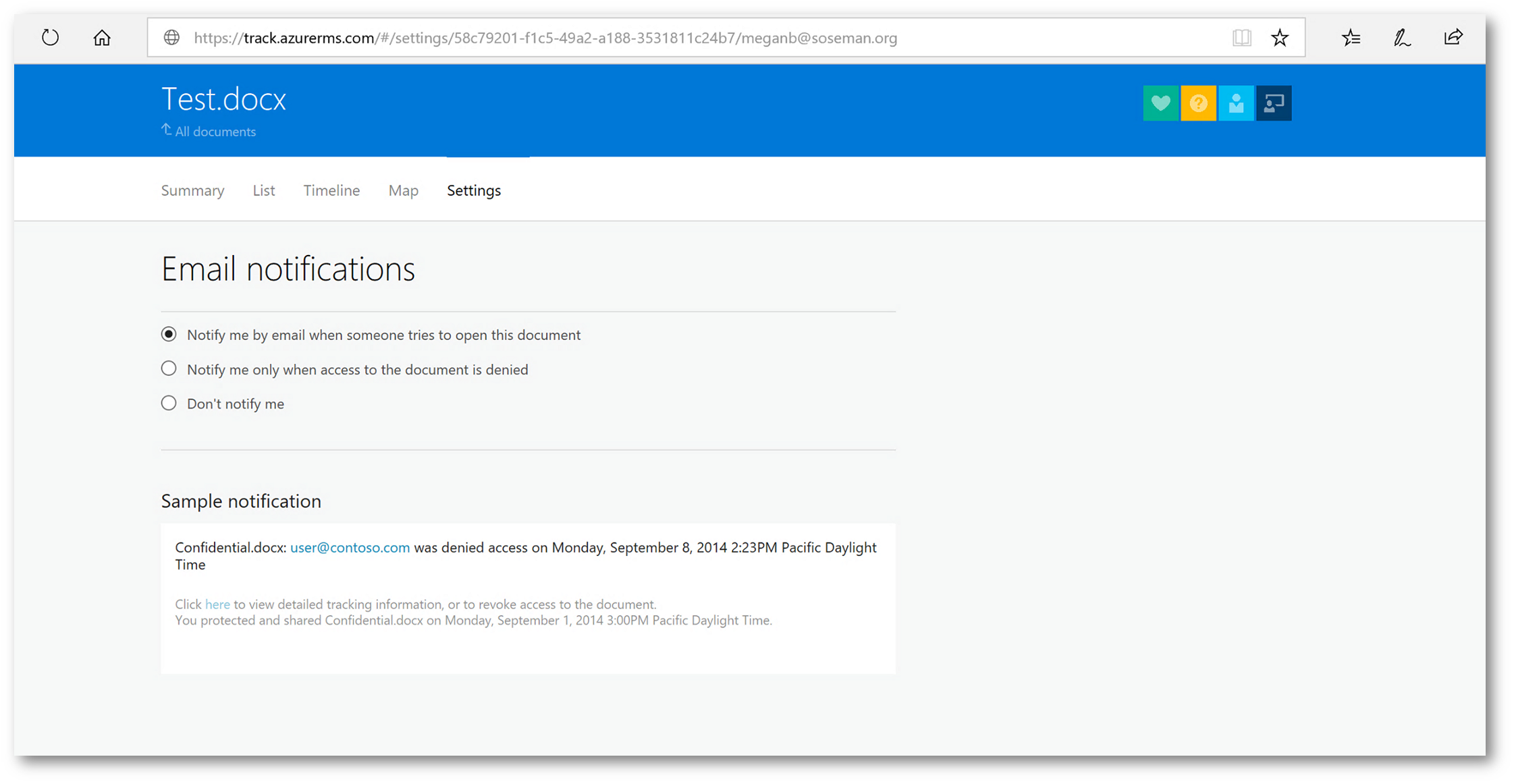
At the bottom of the page, I can revoke everyone's access to the document by the clicking Revoke Access button:

At the bottom, I click Confirm:
All access to the document has now been revoked:
How does this work?
All roads lead to identity:
When a file is protected using Azure Information Protection (AIP), the file is actually encrypted at the file level, and the encryption travels with the file where ever it goes. This encryption is tied to the user's identity in Azure Active Directory (AD). When the file is accessed, they are authenticating to Azure AD, and authorization is checked, the file is de-encrypted and the user can view the file. For more detailed technical information on how this encryption process works see How does Azure RMS work? Under the hood
So, if I give you a super sensitive file that has been protected using AIP, unless you have my identity – or have been granted authorization – you cannot open the file. This is (in my opinion) a game changer, as this means your organization's data can travel from device to device (personal home computer, work computer, mobile devices, USB sticks, etc) and the data will stay encrypted. It doesn't matter if the device is protected or not – because the file is already encrypted. It doesn't matter if I accidently send the file to someone I shouldn't have – because it's already encrypted.
What's required to do this? A few things as outlined in the technical documentation but most importantly: The recipient (inside or outside your organization) needs to have an identity account in Azure Active Directory.
What if the recipient does not have an Azure AD account?
If the file is being sent to someone outside your organization, and that recipient does not have an identity account in Azure Active Directory you have a few options:
The recipient can signup for "Azure RMS for Individuals" by browsing to this website and going through the wizard. Microsoft will check the email address to see if it's associated with an AIP subscription, or an Office 365 subscription that includes AIP. If it is not found, you can register and essentially an account in Azure Active Directory will be created for you. For more information about this process see: RMS for individuals and Azure Information Protection (Note, this DOES NOT sign your company up for anything, this is tied to a single identity so you can use the viewer or sign into a protected file)
If you do not want to go with option 1 (although, it's VERY easy!) then your second option is actually pretty interesting. When AIP is used with Exchange Online – and that document is sent using Office 365 Message Encryption, then you can sign in using a Gmail, Hotmail or Microsoft (Live) account! See New Capabilities Available in Office 365 Message Encryption
The last option, uses the Azure Information Protection client. You can manually specify the recipients who are authorized to access the file (by email address) and their associated permissions using the AIP client:
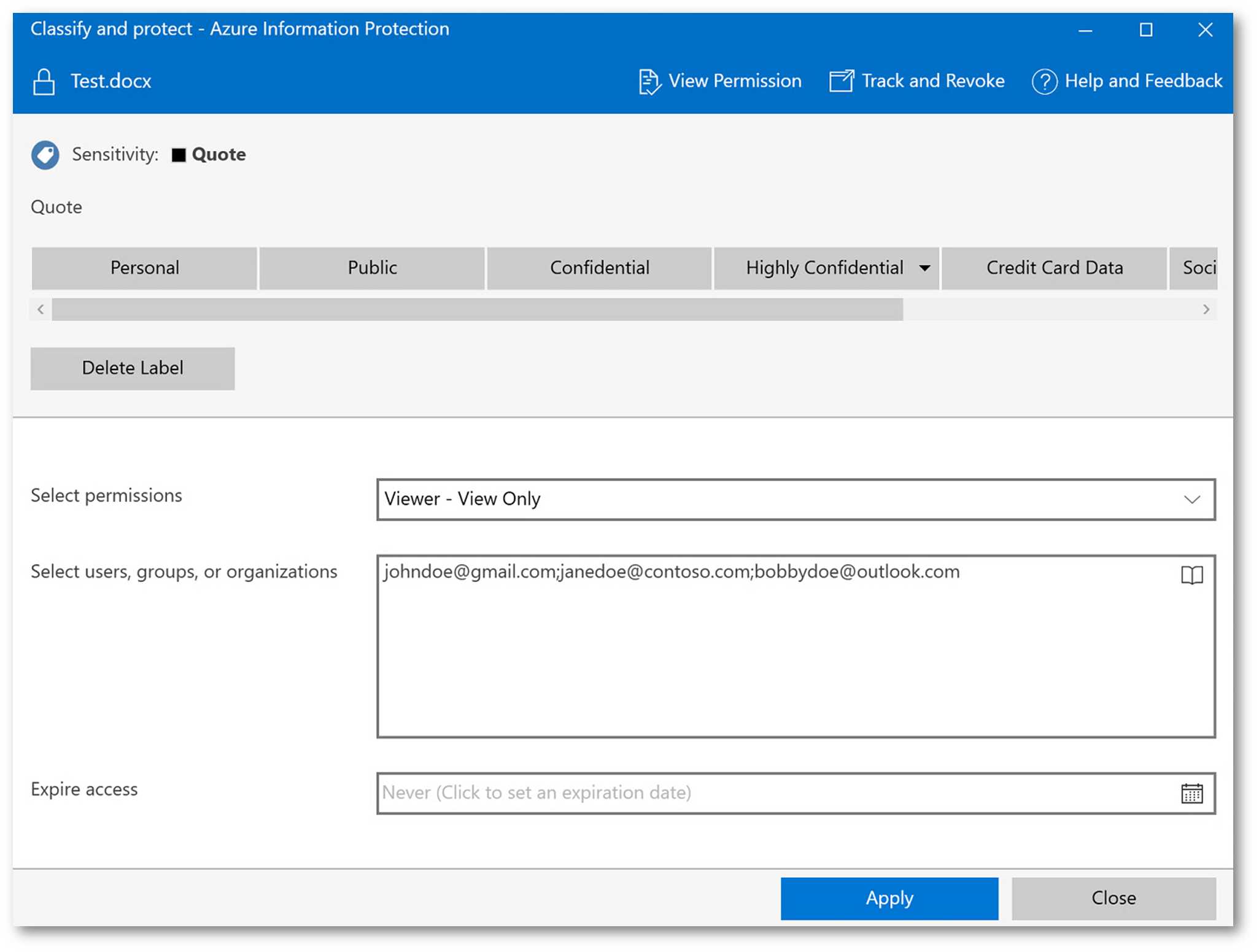
IMPORTANT: All three options require the user to sign into Office on their device (or use the Azure AIP Viewer) with the identity that is associated with the AIP protected file. So, if I receive a spreadsheet from you sent to johndoe@gmail.com, I need to sign into Excel on my device as johndoe@gmail.com.
NOTE: Notice above, there is an option to Expire Access. I can have the file expire after say, 30 days and no one can open it afterwards. This is again another important feature that adds tremendous value (salesperson that wishes to expire a quote after 30 days).
Conclusion:
As you can see, Azure Information Protection can provide tremendous value back to your organization with empowering employees to take control over their data and ensure it's security. However, this also enables them to be more productive through being able to seamlessly share the sensitive files outside the organization and track it's usage. This used to require different 3rd party products and trying to get them integrated with the environment was a challenge.
It's important to note, I have not shown all the back-end configuration that can be performed by IT to add additional value and to meet organizational requirements. Please review the technical documentation to learn more about the following: trusted domains, permissions based on classification type, Office 365 Message Encryption (and how typing the recipient's email address in the To line in Outlook automatically grants them permissions, etc.)
If you own AIP through Microsoft 365, Office 365 or Enterprise Mobility and Security – give this a try and tell me about your success in the comments below!