The MSS settings
You can download the custom Administrative Template for the "MSS (Legacy)" settings here: MSS-legacy . Note that it is available only for "en-us" (US English).
Explanation:
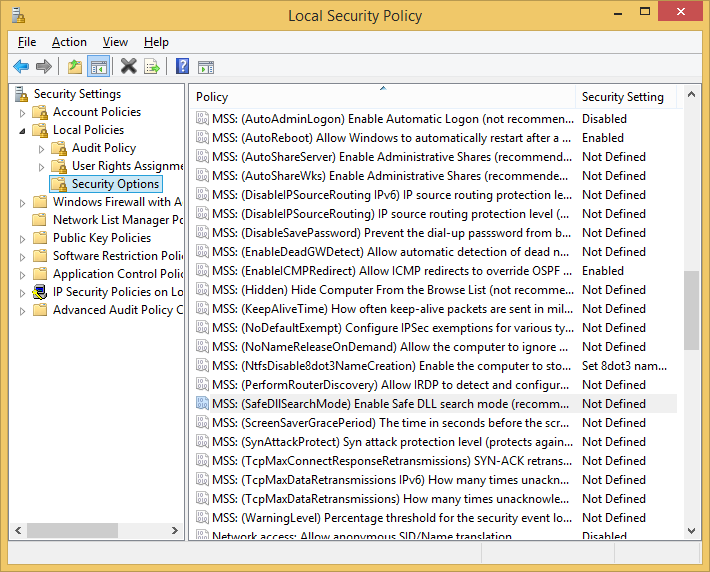
Many years ago, before the advent of Trustworthy Computing, some Microsoft security experts identified about 20 Windows registry values (many or perhaps all of which were undocumented at the time) that could be tweaked for what was then perceived to be significant security gain. For manageability, they developed a script that added these entries to the local security settings editor with descriptive names prefixed with "MSS:" as seen in the screenshot below. [Historical note: I believe they landed there because these tweaks predated Windows 2000, Group Policy, and Administrative Templates.]
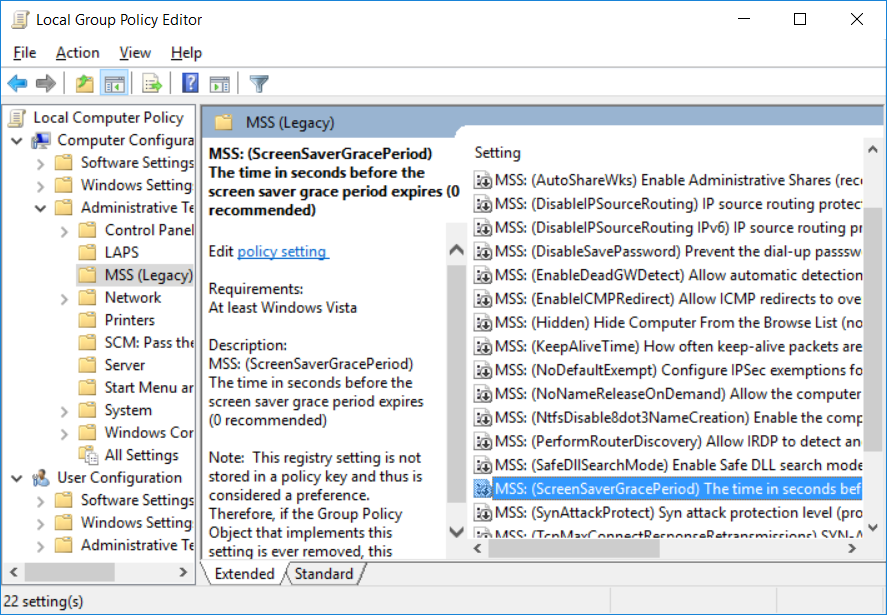
Many of the settings remained part of our security configuration guidance until our "reset" with the Windows 10 recommendations. As part of the reset, we also created a custom ADMX and ADML and moved the settings from the Security Options section of the policy editor to Administrative Templates, as shown in this screenshot:
The reason we did this was because adding them to Security Options relied on a technique that is no longer supportable. The script that had added them to the security editor did so in part by modifying %windir%\inf\sceregvl.inf, a text file. With the introduction of service identities in Windows Vista and Windows Server 2008, Windows configured many OS-owned resources as read-only to everyone except to the TrustedInstaller service. When a resource is configured this way, Windows explicitly tells you that even if you're an administrator, modifying the resource is unsupported. Sceregvl.inf is one of those resources, so the script was updated to take ownership and change the permissions of the file so that the script could edit its content.
The new custom ADMX and ADML file reference the same registry settings as the older script, but in a manner that is supportable. We have included these files in the download packages with our Windows 10 and Windows Server 2016 baselines, and offer them here separately for your convenience. Note that our baselines no longer include recommendations to configure many of the MSS settings we had recommended in the past, as they have no security value against contemporary threats. The few that are still configured in our baseline have limited benefit at most.
Comments
- Anonymous
October 04, 2016
THANK YOU!! Getting the security compliance manager installed on a domain controller was proving to be quite the pain. I'm thrilled these settings were finally released as an admin template! - Anonymous
October 08, 2016
I saw that Windows 10 was mentioned ... so I might too ask what I've been questioning ... if I am using Windows 8.1, do I HAVE TO upgrade to Windows 10?[Aaron Margosis] No. - Anonymous
February 27, 2017
Cool!@ I love group policy, this is a little before my time, and I am gonna enjoy checking out a little piece of early Group Policy settings History, Although it says up there the following... Note that our baselines no longer include recommendations to configure many of the MSS settings we had recommended in the past, as they have no security value against contemporary threats. The few that are still configured in our baseline have limited benefit at most. Still a cool part of history that I must have missed since I began as an admin between 2003 and 2008. - Anonymous
June 08, 2017
I know these get dropped in the Policy Definition folder, but there are two different locations for these folders. For clarity can you update the article to explain to users where the .ADMX and .ADML should be placed?