Uwaga
Dostęp do tej strony wymaga autoryzacji. Może spróbować zalogować się lub zmienić katalogi.
Dostęp do tej strony wymaga autoryzacji. Możesz spróbować zmienić katalogi.
Client created rules, that Auto-Forward email from users mailboxes to an external email address, are becoming an increasingly common and fruitful data exfiltration method being used by bad actors today and something we see quite a lot of in the Office 365 Service.
There are a lot of legitimate reasons for using rules that externally Auto-Forward email, such as mergers an acquisitions etc. However they also represent a risk that needs careful and vigilant management by the admins of your tenant to ensure they are not being misused.
These rules can be created through several interfaces, a desktop client, Outlook Web Access even an admin can use PowerShell to implement via the 'New-InboxRule' cmdlet. Users themselves are often unaware of the rules they have in place (lets face it, who in their desktop client regularly reviews their own rules?) so it is very easy to miss them, either accidentally created rules that Auto-Forward externally or intentionally created rules created by a bad actor after compromising an end users account or breaching a high privileged account such as the tenant admin.
One of the most recent scenarios we have seen, involved a bad actor compromising a tenant admin account, the tenant had Auto-Forward disabled on the default (*) Remote Domain, which offered some protection from client rules externally forwarding email, however the bad actor then created a new Remote Domain, with the namespace of where they wished to exfiltrate data to, enabled the Remote Domain to allow Auto-Forward emails and voila, started to implement client rules that would then Auto-Forward to that namespace.
Mitigation
The Office 365 service, does offer you a myriad of built in ways to control the impact of Auto-Forwarded email to external addresses, like all good security measures, you will likely need a combination of all/some of these to adopt the security posture that your organization feels is appropriate for your needs, defense in depth is key as always:
- Remote Domains - If you as an Organization do not want to allow Auto-Forward emails at all, ensure the setting 'Allow automatic forwarding' is disabled on your Remote Domain settings, such as 'Set-RemoteDomain Default -AutoForwardEnabled $false' or via the Admin Center. Also ensure you are reviewing this as part of your scheduled security reviews, you should be checking the Default Remote Domain and other Remote Domains you may have active have your desired settings in place. A compromised tenant admin account, could see these settings altered.
- Review Client Auto Forwarding Rules - Half the challenge in developing any security posture is understanding your Organizations risk and exposure. Using a script called 'DumpDelegatesandForwardingRules.ps1'from here https://github.com/OfficeDev/O365-InvestigationTooling will allow you to perform an audit of just how many of your clients have rules that Auto-Forward externally. This script can take a while to complete, as it iterates through each mailbox to check the rules (rules are stored in a users mailbox as a hidden item).
- RBAC - You can use RBAC to limit the impact as well, by adding a new management role based of the MyBaseOptions and restricting the parameters DeliverToMailboxAndForward, ForwardingAddress, ForwardingSmtpAddress.
- Transport Rules - We have another tool at our disposal here, by using a Transport Rule. Implementing a Transport Rule based around the following can stop emails that are set to be Auto-Forwarded to an external address. In summary you create a rule based on the following logic. IF The Sender is located ‘Inside the organization’ AND IF The Recipient is located ‘Outside the organization’ AND IF The message type is ‘Auto-Forward’ THEN Reject the message with the explanation ‘External Email Forwarding via Client Rules is not permitted’. This will stop delivery of the Auto-Forward message and issue an NDR as the cherry on top. There are numerous great blog articles out there on how to achieve this.
How Can Secure Score Help?
Using Secure Score https://securescore.office.com helps increase your organization’s security by encouraging you to use the built-in security features in Office 365 (many of which you already purchased but might not be aware of).
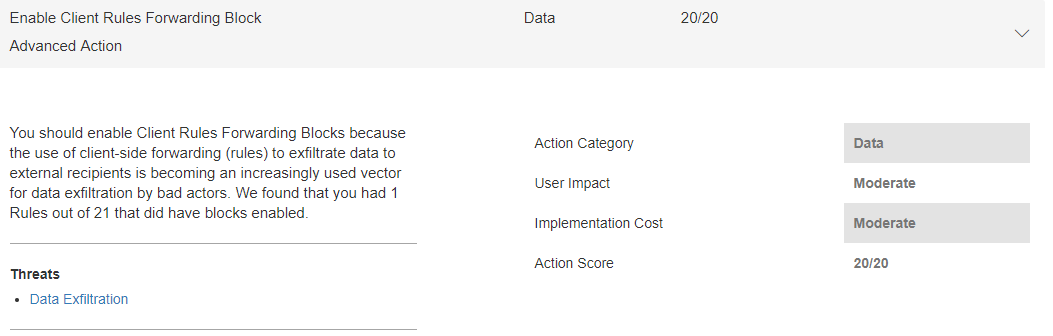
We have implemented a new Security Control in Secure Score called 'Client Rules Forwarding Blocks'. It basically takes mitigation 4 from above and turns that into a one click experience, allowing you to quickly implement a Transport Rule to help mitigate client created rules that Auto-Forward to external addresses. By using this control it will allow you create the Transport Rule above, you can then subsequently tweak the rule directly, for example if you wished to change the NDR text. This feature is now live within Secure Score.
You can find this Security Control in the Advanced Action section of your queue.
So, there we go some steps you can take to help mitigate the risk of managing Client External Forwarding Rules within your Organization. Remember, a layered approach is key to helping adopt your Organizations security posture.
Comments
- Anonymous
July 25, 2017
Very neat article. Thanks for the post - Anonymous
September 09, 2017
Agreed, a really good article and a useful feature, though it may be worth explaining how to add exceptions, as I know at least one person that's had issues with this Thanks for the article.