The Name on the security certificate is invalid or does not match the name of the site - PART 1
Whilst building a test environment for a customer i came across this error ‘The Name on the certificate is invalid or does not match the name of the site’ so thought I'd write up how I resolved it.
The environment was Exchange 2007 SP1 and I was configuring certificates and Outlook Anywhere. For the purposes of the lab I was using an internal certificate authority, but in live the customer is going to use 3rd party certs on the exchange servers, not an internal PKI. The goal here was to try and reduce the number of names in the certificate due to cost.
The first thing to do was to generate the certificate
The certificate I created didn't have any names in the SAN field of the certificate. Here’s an example of the command i ran:-
New-ExchangeCertificate -GenerateRequest -Path c:\CompanyA.csr -KeySize 2048 -SubjectName "c=GB, s=London, l=London, o=Nwtraders, cn=nlb.nwtraders.msft.com" -PrivateKeyExportable $True
This generated the .csr file, which i then uploaded into the internal PKI cert auth (note for live the cert would be generated by a 3rd party cert auth).
In order to generate the cert i connected to the PKI server as shown below
Then selected request a certificate
The selected advanced certificate request
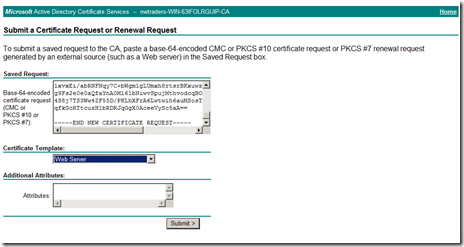
Then selected Submit a certificate request by using a base-64-encoded CMC or PKCS #10 file, or submit a renewal request by using a base-64-encoded PKCS #7 file.
I then pasted the cert requested that i generated earlier (C:\CompanyA.csr) into the field shown below. I also selected Web Server under certificate template and clicked submit
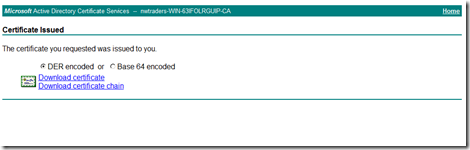
Then selected Download certificate
Then download .cer file and imported into the local certificate store by running the following PowerShell command:-
Import-ExchangeCertificate -Path c:\certnew.cer -Password:(Get-Credential).password
Note: C:\certnew.cer is the cert that we have just downloaded in the previous steps
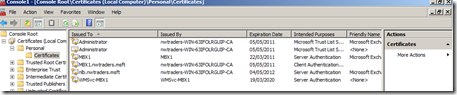
You can verify the cert has been installed 2 ways, run the following exchange PowerShell command to list the certs installed on that server:-
Get-exchangecertificate | fl
Output from the command for the cert i just installed:-
AccessRules : {System.Security.AccessControl.CryptoKeyAccessRule, System
.Security.AccessControl.CryptoKeyAccessRule, System.Securi
ty.AccessControl.CryptoKeyAccessRule}
CertificateDomains : {nlb.nwtraders.msft}
HasPrivateKey : True
IsSelfSigned : False
Issuer : CN=nwtraders-WIN-63IFOLRGUIP-CA, DC=nwtraders, DC=msft
NotAfter : 04/05/2012 11:40:33
NotBefore : 05/05/2010 11:40:33
PublicKeySize : 2048
RootCAType : Registry
SerialNumber : 6175BFDA000000000007
Services : IMAP, POP, IIS, SMTP
Status : Valid
Subject : CN=nlb.nwtraders.msft, OU=nwtraders, O=nwtraders, L=nwtrad
ers, S=UK, C=GB
Thumbprint : 595EA47CF0C04F64DC3D6D2995F7C4B172CA0F92
The 2nd way is using the MMC to add the local computer cert store
See part 2 for enabling the cert and configuring Exchange to use the CN name in the cert you have generated
Written by Daniel Kenyon-Smith