Azure App Service Environment Available in Azure Government
I am very excited to report that I have just deployed an isolated App Service Environment (ASE) in Azure Government. Here are a few quick pointers on how to get started.
Azure App Service Environment (ASE) is an isolated deployment of App Service dedicated to a single subscription. It is ideal for applications that require virtual network isolation or need to scale to a large number of instances. Until recently this feature has only been available in Azure Commercial Cloud but it is not available in Azure Government. So far I have deployed it successfully in US Gov Virginia and DoD Central, but it should be available in all Government regions shortly.
I have previously written about how to use VSTS/TFS to do CI/CD with deployment to an isolated App Service Environment. At that time, this scenario was using Azure Commercial, but now you can implement the same workflow in Azure Government.
To get started quickly, you can use my ASE DevOps template. This template will deploy:
- An App Service Enviroment (ASE)
- A Web App in that ASE.
- A build agent (connected to a VSTS or VSTS instance)
- A jump box for testing purposes.
The deployment will look like the diagram below.
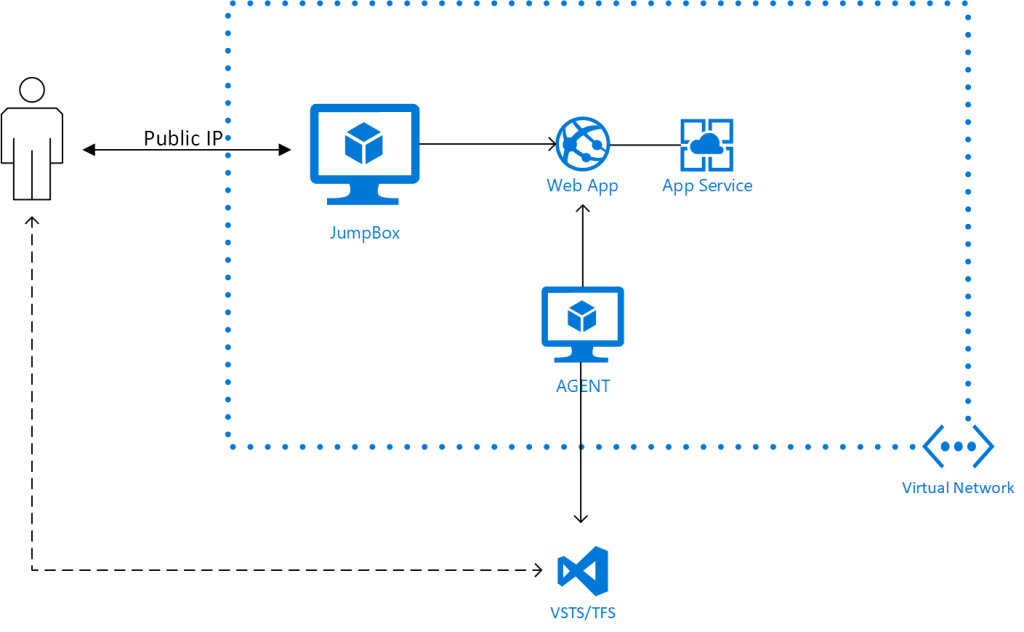 To use the template perform the follow preparation steps:
To use the template perform the follow preparation steps:
- Create a new project in VSTS (or TFS).
- Create a Personal Access Token (PAToken) in VSTS/TFS.
- Create a new Agent Pool in VSTS/TFS.
Then clone the template repository and run the preparation script:
[ps]
git clone https://github.com/hansenms/iac
cd iac\ase-devops
..\scripts\PrepareAseDeployment.ps1 -DomainName contoso-internal.us `
-AdminUsername EnterpriseAdmin -TSServerUrl https://YOUR-VSTS-INSTANCE.visualstudio.com `
-AgentPool AGENTPOOLNAME -PAToken YOUR-PERSONAL-ACCESS-TOKEN `
-OutFile C:\temp\magase.parameters.json
[/ps]
This prep script will create a self-signed certificate for the domain you would like to use. For production use you will want to get your certificate from a Certificate Authority. For free certificates, I recommend Let's Encrypt. I have written a bit about how to generate certificates for Web Apps with Let's Encrypt. After running the script you are ready to create a new resource group and run the deployment:
[ps]
New-AzureRmResourceGroup -Name vaase -Location usgovvirginia
New-AzureRmResourceGroupDeployment -Name myasedeploy `
-TemplateUri $(Get-GitHubRawPath .\azuredeploy.json) `
-TemplateParameterFile C:\temp\magase.parameters.json `
-ResourceGroupName vaase
[/ps]
The command line above uses my Get-GitHubRawPath tool to generate the GitHub.com path for the template. You can read more about that tool and why to use it in this blog post. If you just want the tool, you can install it with:
[ps]
Install-Module HansenAzurePS
[/ps]
Alternatively, you can use the actual GitHub.com URL for the template: https://raw.githubusercontent.com/hansenms/iac/master/ase-devops/azuredeploy.json.
This deployment will take a while to complete, it has been on the order of 1.5 hours when I have tried.
After deployment log into the Jump Box and add the IP address and host name of the web app to the c:\Windows\System32\drivers\etc\hosts file. In my case, I added:
[plain]
10.0.1.11 ase-site.contoso-internal.us
10.0.1.11 ase-site.scm.contoso-internal.us
[/plain]
With the hostname entries added, you should be able to open up a browser on the jump box and hit the ASE website:

The deployment above should register the self-signed certificate as the default ILB certificate, but in my case, the default ILB certificate was not binding appropriately to the sites deployed in the ASE. A simple restart of the ASE fixed that. If you are getting errors that the certificate is for a different site. Try to restart the ASE (which will restart the front-ends).
Since we are using the ASE DevOps template, you can set up a CI/CD pipeline from VSTS (or TFS). It is beyond the scope of this blog post to walk through all the steps, but a quick way to create a .NET Core Web App is using the dotnet command line tool:
[ps]
cd C:\temp
mkdir dotnet-mag
cd .\dotnet-mag\
dotnet new mvc
[/ps]
Add the git repository of a VSTS/TFS project and push code:
[ps]
git init .
git add .
git commit -m "Initial commit"
git remote add origin https://YOUR-VSTS-INSTANCE.visualstudio.com/\_git/PROJECT-REPO-NAME
git push origin master
[/ps]
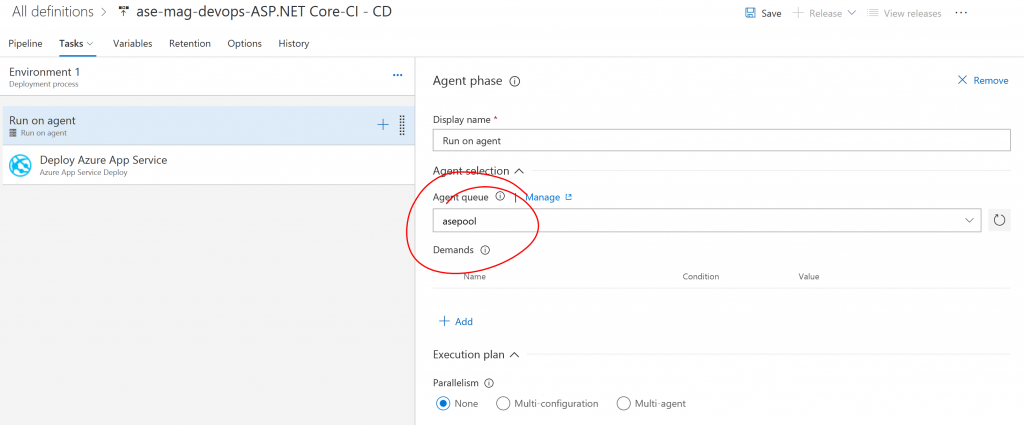
You can then set up a standard .NET Core build configuration and for the build, you can use the Hosted VS2017 build agents (in VSTS). For the deployment configuration, you should pick the build agent deployed in the virtual network:
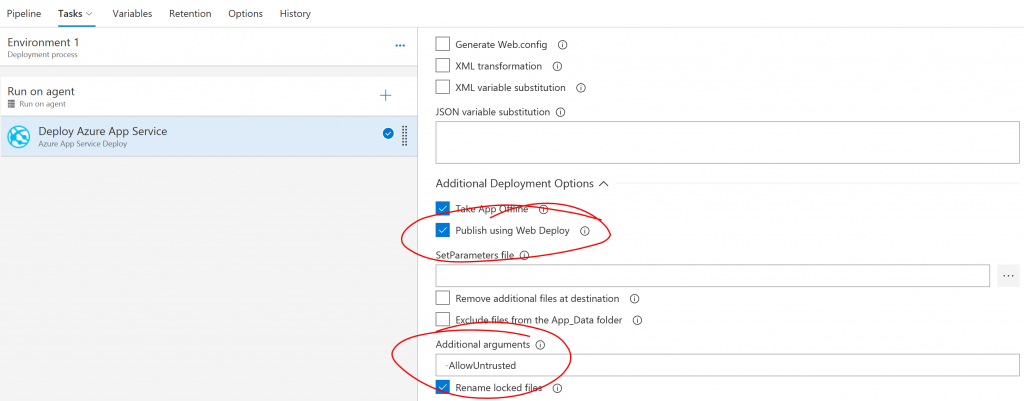
And if you are using a self-signed certificate, it is also necessary to use the "-allowUntrusted" configuration setting for the deployment:
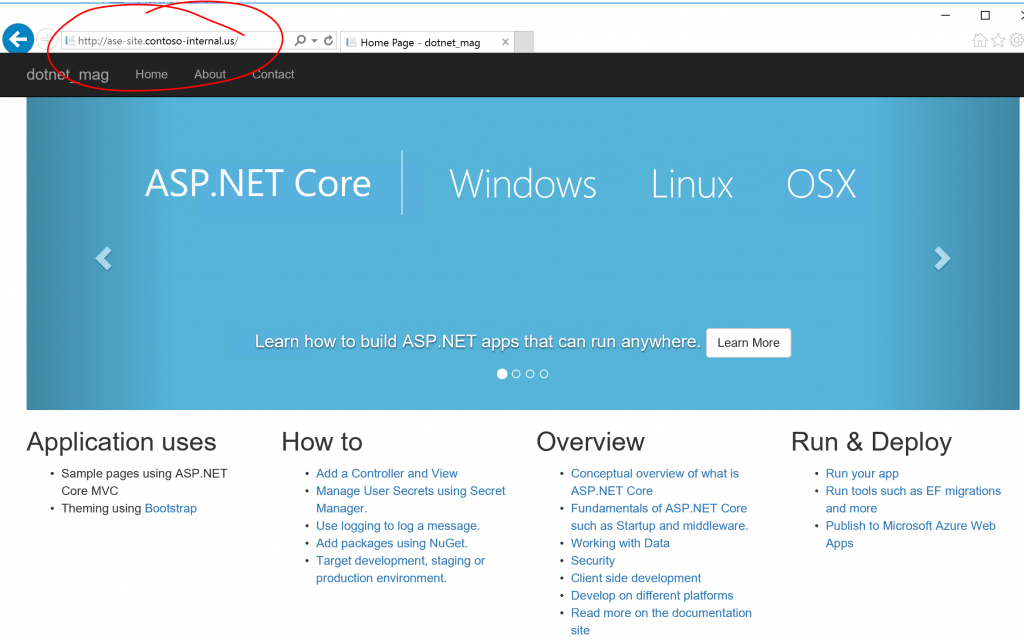
After deployment, you should be able to hit the ASE web site again from the jump box and see that the .NET Core application has deployed:
And that's it. You now have an isolated App Service Environment (ASE) running in Azure Government with VSTS CI/CD pipeline. I will be posting more about ASE for Government applications, but this demonstrates that the basic pieces are in place. Let me know if you have question/comments/suggestions.
Comments
- Anonymous
March 01, 2018
Nice write up. Looking MAG this morning (3/1), I could not find ASEs exposed in the portal like they are in Commercial. Are ASEs in MAG only accessible programmatically?- Anonymous
March 01, 2018
As far as I know, it is not available in the portal yet. You will have to create the ASE with a template, but some configuration steps can be done in the portal after that.- Anonymous
March 01, 2018
The comment has been removed- Anonymous
March 01, 2018
The comment has been removed
- Anonymous
- Anonymous
- Anonymous
- Anonymous
March 03, 2018
Hi,Can you please clarify if this refers to ASE v1 or v2? Also, is there any official MS documentation about this release?I ask as I am currently working with a client and we are eagerly waiting ASE v2 in MAG.Thanks,Dave.- Anonymous
March 03, 2018
It is v2. There is no v1 in MAG as far as I know. The documentation will be updated once the roll-out is complete.- Anonymous
March 03, 2018
Thank you so much Michael. This is indeed very good news.Dave.
- Anonymous
- Anonymous