How to Create and Deploy PFX Certificate Profiles in Intune Standalone
~ Karan Rustagi
I get this a lot from customers who would like to push certificates to mobile devices to work with Resource Access Profiles, S/MIME etc. but can’t have an on-premises Internet facing server that runs Network Device Enrolment Service. If you are facing the same challenge, Intune has a less known feature called PKCS #12 (PFX) based certificate deployment that can be used in this scenario. In the previous releases, it needed an Administrator to supply a .PFX file which would then be deployed to device but this has now changed in standalone Intune. You no longer need to supply a .PFX file. Intune with the help of Intune Certificate Connector will get a certificate issued from Certificate Authority for User which will then be pushed to device. There is no need to setup NDES.
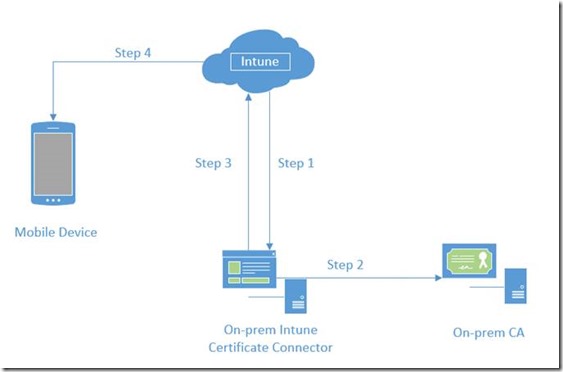
Administrator creates and deploys a PKCS #12 (.PFX) certificate profile to user.
Step 1: Intune service connects to on-premise Intune Certificate Connector
Step 2: On-premise Intune Certificate Connector connects to on-premise CA to get a certificate issued
Step 3: After certificate is issued, it is uploaded to Intune service via connector
Step 4: Certificate is pushed to device
Configure your infrastructure
Before you can configure certificate profiles you must complete the following tasks. In the example discussed below, we will deploy PFX profile to a Windows Phone 10 device.
Task 1 - Configure certificate templates on the certification authority
Task 2 - Enable, install, and configure the Intune Certificate Connector
Task 3 – Create and deploy a Trusted Root CA certificate Profile and a PKCS #12 (.PFX) profile
Task 1 - Configure certificate templates on the certification authority
1. On the issuing CA, use the Certificate Templates snap-in to create a new custom template or copy an existing template and then edit an existing template (like the User template), for use with PFX deployment.
The template must have the following configurations:
a. Specify a friendly Template display name for the template.
b. On the Subject Name tab, select Supply in the request.
c. On the Extensions tab, ensure the Description of Application Policies includes Client Authentication or any other usage you require.
Note: Allow private key to be exported needs to be ticked under Request Handling for PFX deployment to work.
2. Review the Validity period on the General tab of the template. By default, Intune uses the value configured in the template. However, you have the option to configure the CA to allow the requester to specify a different value, which you can then set from within the Intune Administrator console. If you want to always use the value in the template, skip the remainder of this step.
To configure the CA to allow the requester to specify the validity period, on the CA run the following commands:
a. certutil -setreg Policy\EditFlags +EDITF_ATTRIBUTEENDDATE
b. net stop certsvc
c. net start certsvc
3. On the issuing CA, use the Certification Authority snap-in to publish the certificate template.
a. Select the Certificate Templates node, click Action-> New > Certificate Template to Issue, and then select the template you created in step 1.
b. Validate that the template published by viewing it under the Certificate Templates folder.
4. On the CA computer ensure that the computer that hosts the Intune Certificate Connector has enroll permission, so that it can access the template used in creating the .PFX profile. Set that permission on the Security tab of the CA computer properties.
Note: To revoke certificates the Service Account needs Issue and Manage Certificates rights for each certificate template used by a certificate profile.
Task 2 - Enable, install, and configure the Intune Certificate Connector
5. Enable support for the Certificate Connector:
a. Open the Intune administration console, click Admin > Certificate Connector.
b. Click Configure On-Premises Certificate Connector.
c. Select Enable Certificate Connector, and then click OK.
6. Download, install and configure the Certificate Connector.
a. Open the Intune administration console, and then click Admin > Mobile Device Management > Certificate Connector > Download Certificate Connector.
b. After the download completes, run the downloaded installer (ndesconnectorssetup.exe). For .PFX certificates, run the installer on the computer that is able to connect with the Certification Authority. Choose the .PFX Distribution option then click Install and configure rest of settings in wizard.
7. Open a command prompt and type services.msc, and then press Enter, right-click the Intune Connector Service, and then click Restart.
Task 3 – Create and deploy a Trusted Root CA certificate Profile and a PKCS #12 (.PFX) profile
8. Export the Trusted Root CA certificate as a .cer file from the issuing CA, or any device that trusts your issuing CA. You do not export the private key. You will import this certificate when you configure a Trusted CA certificate profile.
Please note this step is optional for PFX itself but needed for e2e scenario to work if you need the cert to be trusted on your client
9. Create a trusted certificate profile:
a. Open the Intune administration console, and click Policy > Configuration Policies > Add.
b. Configure following policy type:
Windows > Trusted Certificate Profile (Windows Phone 8.1 and later)
10. Provide the requested information to configure the trusted certificate profile. In the Certificate file setting, import the Trusted Root CA certificate ( .cer) that you exported from your issuing CA in Step 8.
11. When you are finished, click Save Policy and Deploy.
12. Create a .PFX certificate profile:
a. Open the Intune administration console, click Policy > Configuration Policies > Add.
b. Configure following policy type:
Windows > PKCS #12 (.PFX) Certificate Profile (Windows 10 Desktop and Mobile and later)
13. Provide the information requested on the policy form.
Note:
a. Certification authority - Specify internal FQDN of Certificate Authority server. Eg: Server1.domain.local
b. Certification authority name - Specify certificate authority name as displayed in certification authority MMC. Look under Certification Authority(Local)
14. When you are finished, click Save Policy and Deploy.
PKCS #12 (.PFX) Certificate Profiles are currently supported on Windows 10 Desktop and Mobile and Android only. Future service update will add support for iOS.
Note: PKCS #12 (.PFX) Certificate Profiles are now supported on iOS
Date - 29/04/2016
Comments
- Anonymous
May 23, 2016
Hi, you say that setting up NDES is not necessary in this scenario, but then in step #1 you say "edit an existing template for use with NDES" and then in step #4 you mention that the NDES service account needs "Issue and Manage Certificates" rights. Why would editing templates for NDES and granting the NDES service account rights be required in a scenario that does not need NDES?Thanks- Anonymous
May 24, 2016
Hi Joe,Thanks for pointing. i have made change to post and it should now reflect PFX instead of NDES.For PFX deployment - you need a cert template like you would in NDES.
- Anonymous
- Anonymous
May 24, 2016
The comment has been removed- Anonymous
June 20, 2016
Hi Ian,Specify CA server internal FQDN under Certification AuthorityCertification authority name: Specify CA server name as displayed in certification authority MMC.Look under Certification Authority (Local).- Anonymous
June 22, 2016
Thanks Karan, got it working a treat now. I've also migrated to a 2012 R2 CA as our 2008 CA was missing the NDES patch originally (which all of my original testing was with). However I couldn't install the patch as it was killing the server. A combo of 2012R2 CA and PFX policy works fine with the correct settings. As a foot note - can you add your comments into the blog, or an Intune whitepaper.
- Anonymous
- Anonymous
- Anonymous
July 09, 2017
Hi Karen - trying this SOP but no success. We don't issue our PKI certificates on premise for SMIME but rather get them issued by a third party, DoD approved ECA. Any suggestions you can make for us to be able to use iOS native email app with SMIME and managed by Intune? We've tried to use Outlook for iOS but occasionally receive blank emails that are digitally signed. Unfortunately, we're still awaiting the day Outlook for iOS/Android gets the SMIME feature...- Anonymous
November 22, 2017
This may need us to know more/deeper details. Could i ask you to raise an Advisory ticket with Intune support team on this so they can work with you?
- Anonymous