Azure VMs - Active Directory members and getting time sync (ntp) right
I've recently had this question asked of me multiple times recently.
"If a VM in Azure is a member of a Domain, where does it get its time from, Azure (time.microsoft.com) or the NTP source set by AD?"
The answer is both, unless you make some changes.
Here are the specific time setting recomendations, buried inside this post /en-us/windows-server/identity/ad-ds/get-started/windows-time-service/accurate-time
Azure and Windows IaaS considerations
- Azure Virtual Machine: Active Directory Domain Services
If the Azure VM running Active Directory Domain Services is part of an existing on-premises Active Directory Forest, then TimeSync(VMIC), should be disabled. This is to allow all DCs in the Forest, both physical and virtual, to use a single time sync hierarchy. Refer to the best practice whitepaper “Running Domain Controllers in Hyper-V” - Azure Virtual Machine: Domain-joined machine
If you are hosting a machine which is domain joined to an existing Active Directory Forest, virtual or physical, the best practice is to disable TimeSync for the guest and ensure W32Time is configured to synchronize with its Domain Controller via configuring time for Type=NTP5 - Azure Virtual Machine: Standalone workgroup machine
If the Azure VM is not joined to a domain, nor is it a Domain Controller, the recommendation is to keep the default time configuration and have the VM synchronize with the host.
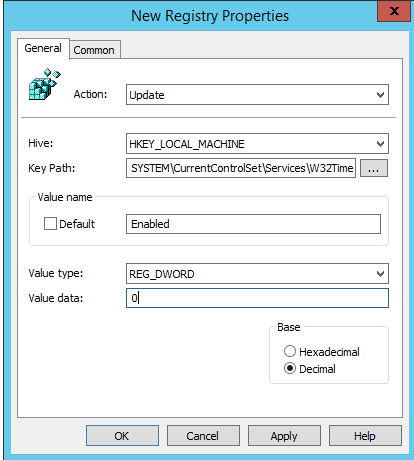
So in short, for Active Directory VMs in Azure, update the registry path: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\W32Time\TimeProviders\VMICTimeProvider and set the value for 'Enabled' to 0
To do this via Group Policy the setting looks something like this -