Agile Architecture Method
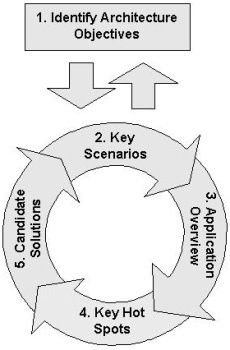
I presented our new patterns & practices Agile Architecture Method for the first time at the patterns & practices Summit. Our Agile Architecture Method is an iterative and incremental approach for designing architectures.
To summarize, it’s a technique that:
- Scopes and focuses your architecture exercise.
- Uses scenarios to drive the design and evaluate potential solutions.
- Helps you think through your choice of application type, deployment, architectural style and technologies.
- Helps you quickly iterate through potential solutions.
- Helps you map potential patterns.
I’ve summarized the approach below, and we’ve posted a step-step how to on CodePlex:
Input
Here’s the key input into the process:
- Use cases and usage scenarios
- Functional requirements
- Non-functional requirements (quality attributes such as performance, security, and reliability)
- Technological requirements
- Target deployment environment
- Constraints
Output
Here’s the key output of the process:
- Architecturally significant use cases
- Architecture hot spots
- Candidate architectures
- Architectural spikes
Summary of Steps
- Step 1. Identify Architecture Objectives.
- Step 2. Identify Key Scenarios.
- Step 3. Create an Application Overview.
- Step 4. Analyze Key Hot Spots.
- Step 5. Create Candidate Solutions.
Step 1. Identify Architecture Objectives
This is a scoping exercise. The purpose of this step is to figure out how much time and energy to spend on subsequent steps as well as guide your overall effort. You should know what you want in terms of outcomes. Here’s an example of potential goals:
- Build a prototype
- Identify key technical risks
- Test potential paths
- Share models and understanding
Step 2. Identify Key Scenarios
Identify relevant scenarios to focus your design on what matters most, and to evaluate your candidate solutions. In this case, you want to identify architecturally significant use cases. Architecturally significant use cases are those that meet the following criteria:
- They are important for the success and acceptance of the deployed application.
- They exercise enough of the design to be useful in evaluating the architecture.
You can draw key scenarios from your user stories, business stories and system stories.
Step 3. Create an Application Overview
Create an application overview. The application overview serves to make your architecture more real, connecting it to real-world constraints and decisions.
An application overview consists of the following steps:
- Determine your application type. First, determine what type of application you are building. Is it a mobile application, a rich client, a rich internet application, a service, a Web application, or some combination?
- Understand your deployment constraints. Next, understand your targeted deployment environment and determine what impact this will have on your architecture.
- Identify important architectural styles. Determine which architectural styles you will be using in your design. Will you build a service oriented architecture, client/server, layered, a message bus, or some combination?
- Determine relevant technologies. Finally, identify the relevant technology choices based on your application type, architectural styles and deployment constraints.
A good test of an application overview is whether you can whiteboard it.
Step 4. Analyze Key Hot Spots
Identify key hotspots based on quality attributes and the architecture frame. These are the areas where mistakes are most often made when designing an application.
Quality Attributes Frame
Understand the quality attributes that are important for your application and scenarios. For instance, most applications need to address security and performance and will be traded against usability, flexibility and other attributes that may be more or less important to you depending on your scenarios and requirements. You can use the following frame to identify key quality attributes to consider:
| Category | Considerations |
|---|---|
| Availability | How to design for failover support How to design a redundant site How to plan for backup and recovery How to design for runtime upgrades |
| Conceptual Integrity | How to isolate from external dependencies How to create a migration path from legacy technologies How evolve the system without breaking clients |
| Flexibility | How to handle dynamic business rules How to handle dynamic UI How to handle changes in data and logic processing How to handle changes in business requirements |
| Interoperability | How to allow applications to interoperate while still evolving separately How to isolate systems through the use of service interfaces How to isolate systems through the use of mapping layers |
| Maintainability | How to reduce dependencies between layers and components How to implement a pluggable architecture How to choose an appropriate communication model |
| Manageability | How to understand the key types of failure How to monitor system operation and health How to modify system behavior based on load |
| Performance | How to determine a caching strategy How to design high performance communication between layers How to design high performance data access How to manage resources effectively |
| Reliability | How to handle unreliable external systems How to audit requests and jobs How to redirect load How to handle failed communication How to handle failed transactions How to handle exceptions |
| Reusability | How to reduce duplication between components and layers How to share functionality across systems How to share functionality across components and layers |
| Scalability | How to design layers and tiers for scalability How to scale-up or scale-out How to handle spikes in traffic and load |
| Security | How to address authentication and authorization. How to protect against malicious input. How to protect sensitive data |
| Supportability | How to design auditing and logging How to design usable error messages |
| Testability | How to design for testability How to design unit tests How to design for UI automation |
| Usability | How to design for user empowerment How to improve responsiveness How to avoid common user experience pitfalls |
Architecture Frame
The architecture frame represents cross cutting concerns that will impact your design across layers and tiers. These are also the areas in which high impact design mistakes are most often made. Use the architecture frame to identify hot spots in your design that require additional attention to get right. You can use the following architecture frame to identify cross cutting concerns in your design:
| Category | Considerations |
|---|---|
| Authentication and Authorization | How to choose an authentication strategy. How to choose an authorization strategy. How to flow identity across layers and tiers. How to store user identities when not using Active Directory. |
| Caching and State | How to choose an appropriate caching technology. How to determine what data to cache. How to determine where to cache the data. How to determine the expiration policy. |
| Communication | How to choose appropriate protocols for communication across layers and tiers. How to design loose coupling across layers. How to perform asynchronous communication. How to pass sensitive data. |
| Composition | How to choose a composition pattern for the user interface (UI). How to avoid dependencies between modules in the UI. How to handle communication between modules in the UI. |
| Concurrency and Transactions | How to handle concurrency between threads. How to choose between optimistic and pessimistic concurrency. How to handle distributed transactions. How to handle long running transactions. |
| Configuration Management | How to determine what information needs to be configurable. How to determine where and how to store configuration information. How to protect sensitive configuration information. How to handle configuration information in a farm/cluster. |
| Coupling and Cohesion | How to choose an appropriate layering strategy for separation of concerns. How to design highly cohesive components and group them within layers. How to determine when loose coupling is appropriate between components within a layer. |
| Data Access | How to manage database connections. How to handle exceptions. How to improve performance. How to handle binary large objects (blobs). |
| Exception Management | How to handle exceptions. How to log exceptions. How to provide notification when required. |
| Logging and Instrumentation | How to determine which information to log. How to make the logging configurable. How to determine what level of instrumentation is required. |
| User Experience | How to improve task efficiency and effectiveness. How to improve responsiveness. How to improve user empowerment. How to improve look and feel. </> |
| Validation | How to determine where and how to perform validation. How to validate for length, range, format, and type. How to constrain and reject input. How to sanitize output. |
| Workflow | How to choose the appropriate workflow technology. How to handle concurrency issues within a workflow. How to handle task failure within a workflow. How to orchestrate processes within a workflow. |
Step 5. Create Candidate Solutions
Create a candidate architecture and along with architectural spikes and evaluate it against your key scenarios, hot spots, and deployment constraints. The outcomes of this step are:
- Baseline / Candidate Architectures
- Architectural Spikes
Iterative and Incremental Design
You can iteratively flesh out your architecture as you work through your design and discover more details that impact your architecture. You don’t have to design your architecture in a single iteration. Do not get lost in the details; focus on the big steps and build a framework on which you can base your architecture and design.
My Related Posts
New Release: patterns & practices App Arch Guide 2.0 Beta 1
patterns & practices App Arch Guide 2.0 Project
App Arch Guide 2.0 Overview Slides
Abstract for Application Architecture Guide 2.0
Cheat Sheet: patterns & practices Catalog at a Glance Posted to CodePlex
Cheat Sheet: patterns & practices Pattern Catalog Posted to CodePlex
Comments
Anonymous
November 05, 2008
PingBack from http://www.tmao.info/agile-architecture-method/Anonymous
November 05, 2008
Its interesting that I at first I would have put Application Overview at first in fact that is probably what I always do. However it may make more sense to do the way you do. And by the way the Quality Attributes and Architecture Frame are great references!Anonymous
November 07, 2008
@Georgely - Thanks! I know what you mean. Originally we had the app overview first -- it's nearly interchangeable, but the idea is to really focus on the architecturally significant use cases. They're a great scoping mechanism.Anonymous
November 08, 2008
Definitely agreed that this way scoping among the use cases seems much more efficient. Not to mention that whenever starting to design a system architecture even before the use cases one usually has at least a minimal understanding of the application and already constructs a rough model of how it should be working - even if not put down on paper in this initial phase yet.Anonymous
November 11, 2008
Application Architecture Guidance Communiqué: Issue 1 About the Application Architecture Guidance 2.0Anonymous
November 14, 2008
As part of our patterns & practices Application Architecture 2.0 project , we created a set of applicationAnonymous
November 20, 2008
The comment has been removedAnonymous
November 20, 2008
The comment has been removedAnonymous
November 20, 2008
The comment has been removedAnonymous
November 24, 2008
We’ve had multiple customers ask our app arch guide 2.0 team for smaller, more focused guides. Anonymous
November 26, 2008
Many customers requested app arch guide 2.0 team of Microsoft for smaller, more focused guides. As aAnonymous
June 22, 2016
wooow...i term this as a simplified scoping mechanisms..i like it