How to identify if your ADCS has issued any certificates with public keys <1024 bits (in preparation for KB2661254)
On August 14th October 14th an update will be released that will by default affect chain validation for public keys that are 1023 bits or less - please read http://blogs.technet.com/b/pki/archive/2012/06/12/rsa-keys-under-1024-bits-are-blocked.aspx and http://blogs.technet.com/b/pki/archive/2012/07/13/blocking-rsa-keys-less-than-1024-bits-part-2.aspx for more details and the MSRC blog on http://blogs.technet.com/b/msrc/archive/2012/06/12/certificate-trust-list-update-and-the-june-2012-bulletins.aspx as well as the IE blog on http://blogs.msdn.com/b/ieinternals/archive/2012/06/13/windows-internet-explorer-block-rsa-key-shorter-than-1024-bits.aspx.
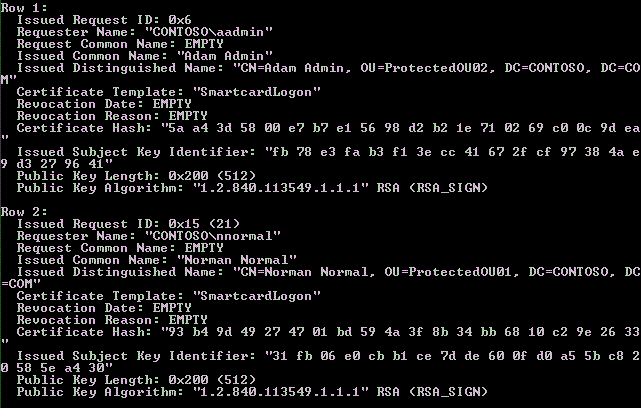
The following certutil command can be run against a Windows CA to dump out any certificates that it has issued with public keys smaller than 1024 bits that this update may affect (the ones with algorithm type RSA_SIGN).
Certutil -view -restrict "PublicKeyLength<1024,PublicKeyAlgorithm=1.2.840.113549.1.1.1"
-out "RequestID,RequesterName,Request.CommonName,CommonName,
DistinguishedName,UPN,NotBefore,NotAfter,SerialNumber,Disposition,
CertificateTemplate,RevokedWhen,RevokedReason,CertificateHash,SubjectKeyIdentifier,
PublicKeyLength,PublicKeyAlgorithm"
>%Computername%-CADBDump.txt
Note: if you´re running this on a Windows Server 2008 R2 CA then you can add "CSV" after the column list and before the pipe command to get an output format more suitable for import into Excel.
As you can see from the screenshot above, Smartcard Logon certificates from the original Windows 2000-style V1 certificate templates are 512 bits - if the V1 template has been duplicated then it will however default to 2048 bits unless specifically modified by the admin creating the template.
A quick shortcut for checking the size of the public keys in your local certificate stores on servers and clients is to run the Certutil command and pipe the output to a simple search command:
certutil -v -store my |findstr "Length: ObjectId: Principal DNS CN= Serial" (for the machine account certificate store)
certutil -v -store -user my |findstr "Length: ObjectId: Principal DNS CN= Serial" (for a user account certificate store)
certutil -v -store root |findstr "Length: ObjectId: CN= Serial"
certutil -v -enterprise -store root |findstr "Length: ObjectId: CN= Serial"
...if any of these yields a public key size smaller than 1024 then you should drill down closer to that entry (i.e. pipe the output to file and search closer to identify the certificate that needs to be replaced).
/instan
More information:
PKI Team Blog
http://blogs.technet.com/b/pki/archive/2012/06/12/rsa-keys-under-1024-bits-are-blocked.aspx
http://blogs.technet.com/b/pki/archive/2012/07/13/blocking-rsa-keys-less-than-1024-bits-part-2.aspx