The Game of Phishing – How to beat your Opponent
With more than 1.4 Billion clear text user credentials accumulated and up for grabs in the dark web clearly indicates that the hunt for credentials from genuine users/Organizations is the most important phase of the the cyber kill chain.
Verizon Data Breach Investigation report 2017 says that 81% of breaches that have occurred involved compromised credentials and in 75% of them perpetrators were outsiders.
Phishing emails are proving to be most effective way to grab credentials of users and then use them to carry out attacks on them and their organization.
If you are new to this term, This should help.
The Mind Game
Over the years, the art of phishing has evolved and adversaries are now using more sophisticated ways to trick human mind in making a wrong judgement.
If you are fan of National Geographic’s popular show “Brain Games” like me, they've showed how amazing ways human brain functions. How a part of brain questions everything, sees with suspicion before making any decision and how another part of brain which simply accepts the fact and assumes it as true and takes the action.
For E.g, When you are about to cross the road, A part of brain looks at this scenario with suspicion and caution. It only makes decision to cross the road after determining that there is no threat to life from incoming vehicle. Lets call this part of the brain – Part 1
However on a different scenario, when you pickup a TV remote and about the press the power button, does you brain sees this act with same level of caution and suspicion? No, right? This time the other part of the brain makes the decision by assuming that when you press the button, the TV will turn on and nothing bad will happen. Lets call the part of the brain Part-2.
Adversaries are now using various physometeric tactics to let your Part 2 of brain acts and makes you take quick decision to act swiftly on the email and supress your other side of the brain which makes you question it.
Lets play a game.
Can you tell which of the following screenshot of the Office 365 Logon Page is a Phishing Page and which one is authentic webpage?
Fig.1
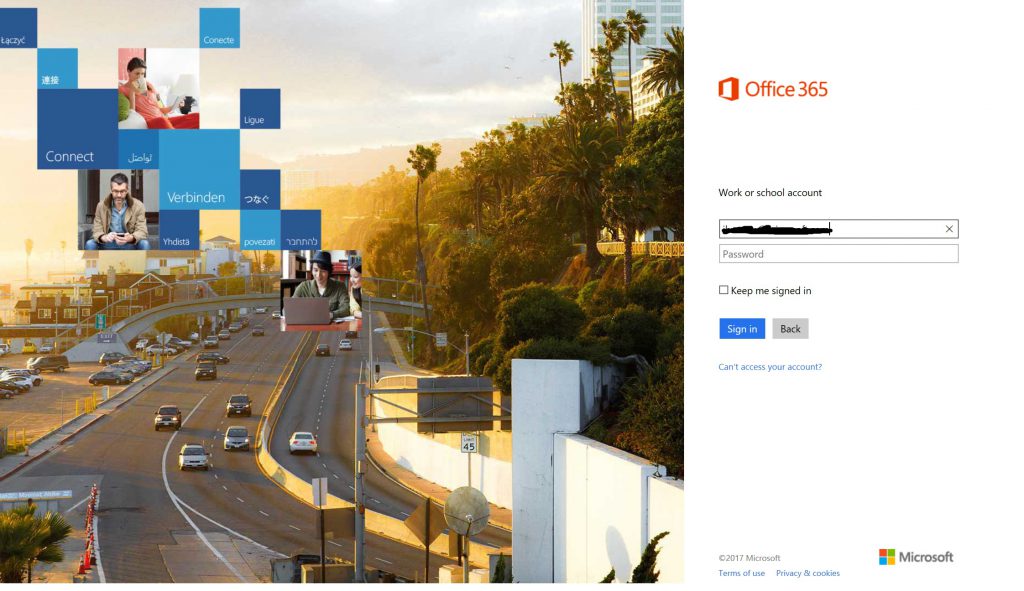
Fig 2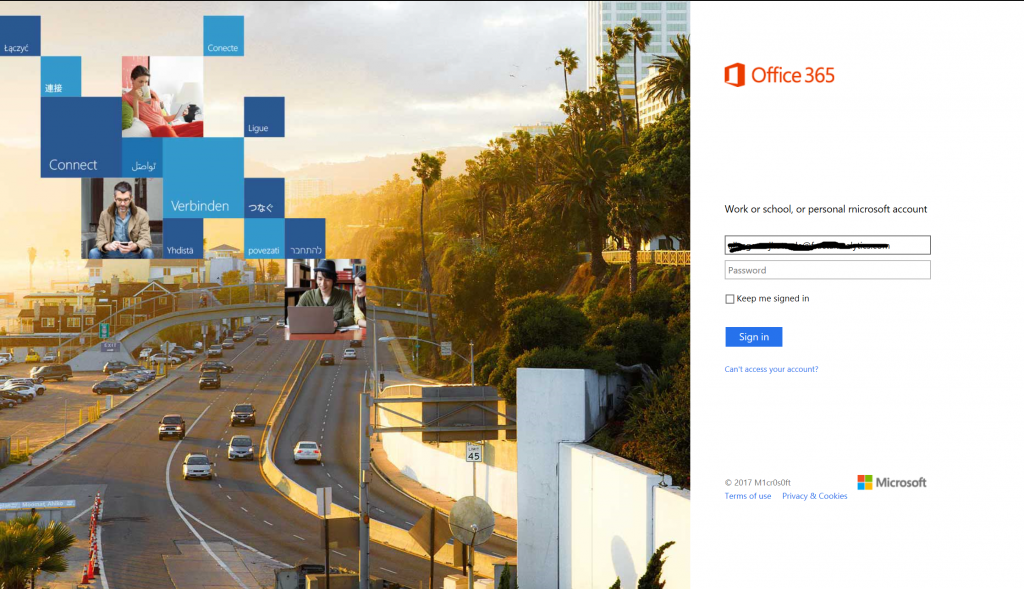
If you happen to land on one of these webpages and provide your credentials, You have just made a life of a attacker easy by handing over one of your organizations critical asset, your Username and Password.
So what could really happen when someone else have your credentials?
1. They can logon to your mailbox and use your email account to send with emails with Malicious attachments to all your colleagues. Since all your colleagues trusts you they will not use their Part 1 of brain to think twice before opening those attachments.
2. They can use your mailbox to attack your friends/family similar way.
3. They can use your mailbox to spear phish senior leaders of your organization to grab their credentials and elevate privileges.
4. They can VPN and connect to your corporate network as you and initiate exploration and then exploitation activities or just spreading a worm based ransomware in the network.
5. and much more ![]()
How to be better than the game?
Detecting Signs on a Phishing Email
1. Sense of Urgency - Look for the sense of urgency in the email. If the email is asking you take an action in hurry with words like immediately, Urgently etc, be cautious.
2. Grammatical errors or spelling mistakes- More often or not, attackers from non native English speaking regions tend to make spelling or grammatical mistakes in their emails or on the Phishing site.
3. Spoofed Email Sender - Do not trust the email sender name on your email header. While it might look its coming from known sender but when you expand the Email Name, you may see a different email address (spoofed)
4. Obfuscated URLs : What you see my not be what you get. Hover your mouse on the Links to see the actual URL its taking you to. If you see Base64 in URL, move away.
5. Detailed Email Header – If you are ready to dive deep, Look at the detailed email header to review the complete mail flow and sender Info including IP address and Sender Domain.
6. Email formatting – Emails coming from various reputated organizations goes through multiple review w.r.t formatting. if the email looks weirdly formatted it may be anomalous.
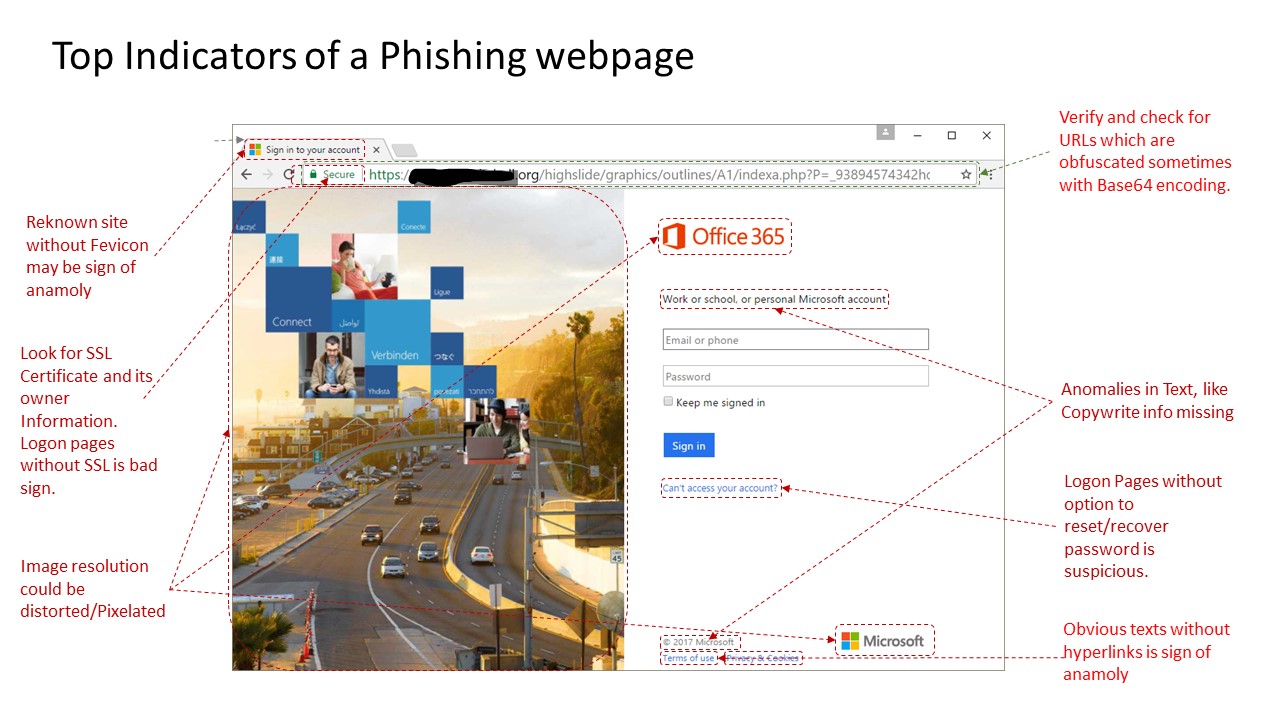
Detecting Signs of a Phishing website.
If you do end up on a site by clicking on those URLs in your email, following tips can help detecting it a Phishing Site.
Yes, it would be really taxing to check every email with suspicion and open every links in the email and verify the webpage for signs of phishing.
If you are an Office 365 customers, Advanced Threat protection of O365 protects against phishing attacks by analyzing the URLs in the emails and blocks the access to the malicious website at the time of click.
If you’d like to see a short demo on how Office 365 ATP Safe link protects against Phishing attack, check this video
To learn more about the Safe Link capabilities of Office 365 ATP, check here
PS: If you have not been able to figure out yet, Figure 2 is a phishing page :)
Cheers
Iftekhar