Scanning Tool to Detect Custom XML Markup in .DOCX and .DOCM files
Quick Start The Installer is located here. (update: A new version of the installer is here: https://blogs.technet.com/cfs-file.ashx/__key/CommunityServer-Components-PostAttachments/00-03-35-69-65/Custom-XML-Markup-Detection-Tool-Setup.zip) |
Background readingWhat is Custom XML- ... and the impact of the i4i judgment on Word , Regarding Custom XML Patch distribution and availability , Associating Data with Content Controls , Using Content Controls vs. Custom XML Elements , |
After we made a patch available for Word related to the recent court ruling, we were asked by a handful of customers if there is a way to identify document files or solutions which may be affected. One way to identify solutions within an organization that may be affected is to scan your existing XML format based Word files (.docx and .docm) for the presence of the markup in question.
On my blog today I am posting a no-cost, unsupported tool to help you scan repositories for documents which may contain markup that would be affected by the patch. We are also providing the source code for the tool in case you would want to modify it to scan for specific directories, or to add additional functionality to the tool. It is written in C#.
Results provided by the tool can help you to identify possible areas of impact for your specific IT environment.
The documents identified by the tool as containing custom XML markup are themselves not affected by the ruling, and require no action on your part. What positive scan results will indicate are documents that will behave differently when opened in patched and unpatched versions of Office.
Positive results concentrated on a single machine or set of machines may also indicate the presence of a solution or template generating the affected markup, and may indicate the presence of a solution that will perform differently when opened by a patched or unpatched version of Word.
The scanning tool will work when run by a local user on a local machine. For SharePoint and other systems whose directories are identifiable by a UNC path, the scanning tool can be used on a server to examine documents stored within those systems.
How to Use the Software
IT Administrators can configure a login or startup script for computers in their domain to copy the .exe file to a local machine, and to execute the command line tool. Alternatively, a startup or login script can be created to run the installer locally, and execute the command line tool. For more information on login and startup scripts, visit https://www.technet.microsoft.com, or https://technet.microsoft.com/en-us/magazine/dd630947.aspx.
1. Run a command prompt window (Run as Administrator)
2. Go to the directory where you have installed the Custom XML Markup Detection Tool
a. By default, this directory is "C:\Program Files\Microsoft\Custom XML Markup Detection Tool\"
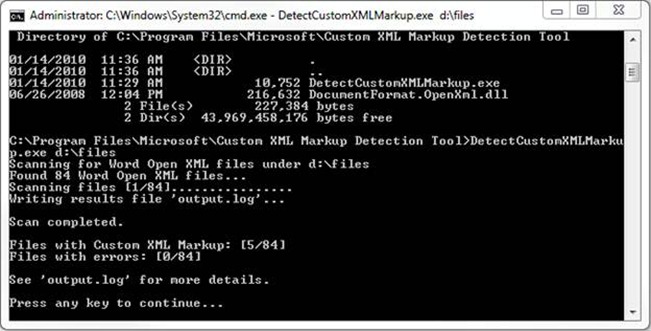
3. Run the tool with the following command: DetectCustomXMLMarkup.exe [directory path]
a. For example DetectCustomXMLMarkup.exe c:\temp
4. At this point, the tool will tell you how many files it is scanning and how many files it detected with Custom XML markup
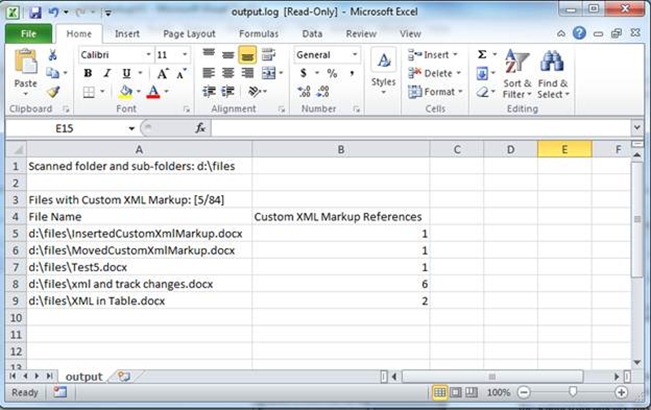
5. An "output.log" file will be created, in the same directory the tool was run, that summarizes the findings of the tool. This log file includes information on files that include Custom XML markup and/or files that the tool encountered errors while scanning. This log file is a tab delimited text file, which can be opened in Notepad or Excel. Here is an example log file opened in Excel:
Notes: The tool works with directories and UNC file paths.
The Installer is located here .
Custom XML Markup Detection Tool Setup.msi
Comments
Anonymous
January 01, 2003
thnx.Anonymous
January 01, 2003
Hi Ron, The tool does not modify the scanned documents in any way.Anonymous
January 22, 2010
Thanks for creating and posting this tool, Gray! I have one question; Does this tool modify any dates or flags on files that are examined? If so, what is modified?