NTFSSecurity Tutorial 1 - Getting, adding and removing permissions
Summary
Managing file and folder permissions in Windows PowerShell is not that easy, and there are numerous articles and blog posts describing how it works by using the .NET classes. This is far from being comfortable, and there is one major and one minor restriction:
- Path length
- Generic rights
This post introduces the NTFSSecurity module, which provides a bunch of cmdlets for managing permissions on NTFS drives. It does not use the Windows PowerShell way to access the file system, and it works around the MAX_PATH, which is 260 characters. (For more information, see Naming Files, Paths, and Namespaces). This is achieved thanks to AlphaFS.
This post examines displaying permissions and granting users permission.
Installation
You can download the module from the Script Center Repository: File System Security PowerShell Module. Please unblock the file before extracting it.
For more information about installing Windows PowerShell modules, see Hey, Scripting Guy! How Can I Install Windows PowerShell Modules on Multiple Users' Computers?
Some backgrounds
Windows stores the permissions in the discretionary access control list (DACL), which is part of the Security Descriptor. The Security Descriptor also includes the system access control list (SACL), where the auditing is configured, and member information. This post is about permissions and it does not discuss the SACL or member information.
The DACL contains access control entries (ACEs) that define the permissions someone has on the object. Each ACE contains the following values:
- Account: Who is granted or denied access. Windows does not store the user’s SamAccountName, but rather, the SID.
- Rights: The permissions granted or denied.
- Type: Grant or deny access.
- IsInherited: True if the ACE is inherited from a parent object.
- InheritanceFlags and PropagationFlags: These bits control the inheritance. The NTFSSecurity module converts the bits into something more readable that is discussed later in this post.
By default, a security descriptor on the file system inherits permissions from the parent object. Users who have full access on drive C also have full access to all subfolders if the inheritance is not disabled.
Managing permissions
Reading the permissions of a single item
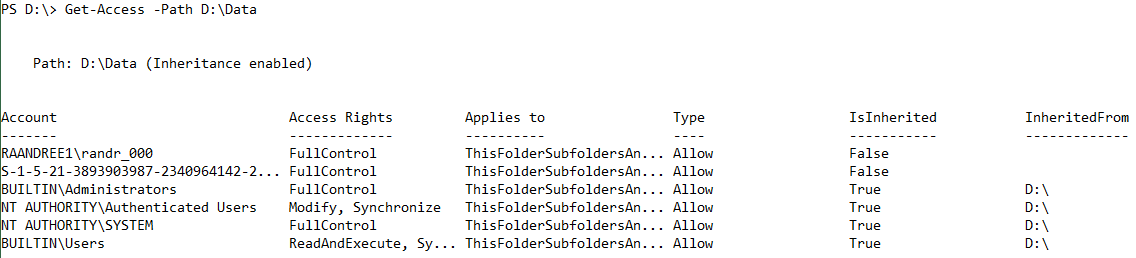
The first and easiest task is to retrieve the DACL from a specific file. The cmdlet that the NTFSSecurity module provides for retrieving existing permissions is Get-NTFSAccess. You can pipe a file or folder to that cmdlet or work with the Path parameter:
Get-Item D:\Data | Get-NTFSAccess
Get-NTFSAccess -Path D:\Data
The output might look like this:
The output is grouped by the file or folder, which is important when getting the permissions of more than one object. Next to the path is information about if the file or folder inherits the permissions from the parent object. My example shows that four of the displayed ACEs have been inherited from drive D.
Some more details about the columns:
- Account: The account that has been granted or denied access to the item. As mentioned, Windows does not store the user’s name, but rather, the SID. If the SID can be translated into the name, NTFSSecurity shows it; otherwise, the SID is displayed.
- AccessRights: These are the actual permissions that the account has been granted or denied. The list behind this field also supports generic rights.
- Applies to: The .NET Framework stores the inheritance information in two-bit fields: InheritanceFlags and PropagationFlags. These fields are quite difficult to interpret, so NTFSSecurity converts them into something that is known from the Windows Explorer:
- ThisFolderOnly
- ThisFolderSubfoldersAndFiles
- ThisFolderAndSubfolders
- ThisFolderAndFiles
- SubfoldersAndFilesOnly
- SubfoldersOnly
- FilesOnly
- Type: Either Allow or Deny
- Inherited: If the ACE is inherited from the parent, this is True. The first two ACEs have been defined explicitly in the folder.
- InhertedFrom: This column only contains information if IsInherited is True, and it indicates where the ACE is inherited from.
Reading the permissions of a multiple item
All NTFSSecurity cmdlets support pipelining. If you need to get the permissions from multiple items, you do not need to run a ForEach loop. You can simply pipe the files and folders to Get-NTFSAccess.
dir C:\Data | Get-NTFSAccess
Get-NTFSAccess provides ways to filter the ACEs. A common scenario is to get the ACEs of a specific account or only those that have not been inherited.
If you want to display only permissions that have been added explicitly and hide all the inherited permissions, use the ExcludeInherited switch:
dir | Get-NTFSAccess –ExcludeInherited
If you want to display only the permissions assigned to a certain user, use the Account parameter:
dir | Get-NTFSAccess -Account raandree9\randr_000
Note: This displays the permissions as defined in the ACL. This is not the effective permissions. Effective permissions will be discussed in an upcoming post.
Granting access
Granting access to a file or folder is also quite easy to do by using the Add-NTFSAccess cmdlet. Add-NTFSAccess provides the following parameters:
- Account: This can be a user account name (SamAccountName) or a SID. The user account name has to contain the domain (domain\username). Built-in SIDs are also supported, such as Everyone, NT AUTHORITY\SYSTEM, or BUILTIN\Administrators. For more information, see Well-known security identifiers in Windows operating systems.
- AccessRights: This parameter takes one or more of file system rights, for example, FullControl, Modify, or Read. If you want to assign multiple rights, provide them in a comma-separated list.
Note: Use Tab expansion or the ISE to get a list of all available values.
- AccessType: Allow or deny
- AppliesTo: This parameter sets the scope of the ACE. The options are the same as Windows Explorer provides. By default (when not defined), the scope is ThisFolderSubfoldersAndFiles.
Note: Use Tab expansion or the ISE to get a list of all available values.
- PassThru: By default, the cmdlet does not return any data. If the PassThru switch is used, the cmdlet displays the ACL after adding the ACE.
The next commands give the well-known group, Authenticated Users, read access to the folder C:\Data. The built-in administrators and the local group, Editors, are getting full control:
Add-NTFSAccess -Path C:\Data `
-Account 'NT AUTHORITY\Authenticated Users' `
-AccessRights Read
Add-NTFSAccess -Path C:\Data `
-Account 'BUILTIN\Administrators', 'raandree9\Editors' `
-AccessRights FullControl
Note: The modifying cmdlets of the NTFSSecurity Module do not return any data by default. If you want to get back the modified ACL, use the PassThru switch.
Removing Access
Removing access is similar to adding permissions. The command Remove-NTFSAccess takes the same parameters as Add-NTFSAccess.
To remove a user from the ACL, provide the path, the account name, and the permissions you want to remove, for example:
Remove-NTFSAccess D:\Data -Account RAANDREE0\randr_000 -AccessRights Read -PassThru
If the user has different permissions than those you want to remove, nothing happens. There needs to be an exact match.
Note: You cannot remove inherited permissions. Get-NTFSAccess informs about the source of the inherited permissions where the respective ACE can be changed or removed.
Remove-NTFSAccess accepts pipeline input. If you want to remove all permissions for a certain user account, you can read the permissions first and then pipe the results to Remove-NTFSAccess. This operation can also run reclusively:
Get-ChildItem -Path d:\ -Recurse |
Get-NTFSAccess -Account raandree0\randr_000 -ExcludeInherited |
Remove-NTFSAccess
Note: The cmdlets in the NTFSSecurity module do not provide a way to process files and folders reclusively. You have to use Get-ChildItem or Get-ChildItem2 with the Recurse switch. (The Get-ChildItem2 cmdlet is part of the NTFSSecurity module, and it will be discussed in a future post).
NTFS Inheritance
After you set permissions on a parent folder, new files and subfolders that are created in the folder inherit these permissions. If you do not want them to inherit permissions, set ApplyTo to “ThisFolderOnly” when you set special permissions for the parent folder. In cases where you want to prevent certain files or subfolders from inheriting permissions, disable (or block) the inheritance.
There are two types of permissions:
- Explicit permissions: Set by default when the object is created by user action.
- Inherited permissions: Propagated to an object from a parent object. Inherited permissions ease the task of managing permissions and ensure consistency of permissions among all objects within a given container.
To add an ACE that does not affect any child elements, use the following command:
Add-NTFSAccess .\Data -Account raandree1\install -AccessRights Modify -AppliesTo ThisFolderOnly
If the AppliesTo parameter is not used, the ACE applies to “ThisFolderSubfoldersAndFiles,” like when using the Windows Explorer to add permissions. All child elements will inherit the ACE created by the following command:
Add-Access -Path .\Data -Account BUILTIN\Administrators -AccessRights FullControl
To verify which child items have inherited the ACE, you can get and pipe all child elements recursively to Get-NTFSAccess. With the following command, Windows PowerShell reads only the inherited ACEs that are assigned to the built-in administrators group that are inherited from D:\Data:
dir -Recurse | Get-NTFSAccess -Account BUILTIN\Administrators -ExcludeExplicit | Where-Object InheritedFrom -eq 'D:\Data'
The next post will explore how to report, enable, and disable inheritance in folders (the NTFSSecurity module provides the same feature as the Windows Explorer). I will also discuss taking ownership of files without losing the ACL.
Comments
Anonymous
December 05, 2014
Summary
In my previous post, Use PowerShell to Get, Add, and Remove NTFS Permissions , I talked aboutAnonymous
December 23, 2014
Hi Raimund as always you are doing a fantastic job.
To avoid misunderstanding, would you mind replacing "reclusively" by "recursively", a few times in this story?Anonymous
January 08, 2015
Are you able to remove groups? I can't seem to be able to get it to remove a groupAnonymous
June 02, 2015
I have a very special case, I have GenericAll and FullControl for the group Everyone (S-1-1-0) in two seperate entries and i can't delete either of it. I think it has something to do with the fact that I should delete them both at once but if I have understood the script correctly, it is not possible to do something like this remove-ace c:test -Account S-1-1-0 -AccessRights FullControl GenericAlAnonymous
June 13, 2015
Sorry new to the blog, maybe changing the subject completely but I have a problem recently with turning back on my antivirus (Avast) back on on my PC's services without this I can't obviously 'Tick' both the antivirus & firewall as required to be on at start up & continuous can anybody help please....Anonymous
October 08, 2015
I didn't catch how to remove all Inherited acl using this module? May be someone did it.
I tryed this
1. Get-NTFSAccess -Path $.Folder | where IsInherited -eq $True | Remove-NTFSAccess
2. Get-NTFSAccess -Path $.Folder | Remove-NTFSAccess
doesn't work
Please help.Anonymous
October 08, 2015
Hi Helen,
like Raimund stated in his article above:
Note: You cannot remove inherited permissions. Get-NTFSAccess informs about the source of the inherited permissions where the respective ACE can be changed or removed.
Saying - if you want to remove an inherited permission you have to do this on the folder where the inheritance started or you break inheritance on the folder you want to handle.
Suggesting to use Disable-Inheritance with -RemoveInheritedAccessRules switch.
Hth.
Michael
PFE | Have keyboard. Will travel.Anonymous
October 09, 2015
Thank's a lot to Michael. Now it does work as I wanted.Anonymous
December 03, 2015
I need to set NSFS on a lot of MountPoint disks - Have you a solution for that?
\server.ad.domain.comshare$mpAnonymous
January 12, 2016
Is there a way to get effective rights of a given (domain) account?(e.g.. user x has accessrights Modify to folder y, because user x is member of group z )Anonymous
January 22, 2016
The comment has been removed- Anonymous
January 24, 2016
Hi,have you unbloked the Zip file before extracting it? If any file of the module is still blocked, loading it does not work. http://www.hanselman.com/blog/RemovingSecurityFromDownloadedPowerShellScriptsWithAlternativeDataStreams.aspx-Raimund
- Anonymous
Anonymous
February 29, 2016
The comment has been removedAnonymous
March 24, 2016
Bonjour,Est il possible de supprimer des droits "non hérité" ?Je cherche sur internet mais sans succès pour le moment.MerciAnonymous
March 24, 2016
The comment has been removed- Anonymous
March 24, 2016
The comment has been removed - Anonymous
March 24, 2016
The comment has been removed- Anonymous
April 21, 2016
Sorry for the late reply. Do you still have the issue? I have done quite a lot exports / imports and did not face issues so far. To speed this up you can also reach me at raandree@live.com.
- Anonymous
- Anonymous
Anonymous
April 25, 2016
I am wondering if this script is expecting just a single word for the domain name.. ie. domain\user?? In my case, our domain is something.something.com or the old NETBIOS of something_com. Looks like the script doesn't like the periods or underscores??Anonymous
June 30, 2016
After following the install instructions, downloading, then unblocking the module. I'm trying to run Get-NTFSAccess -Path D:\Data script to my specified drive/folder but results are:Get-Access : The term "Get-Access" is not recognized as the name of a cmdlet, function, script file, or operable program....Can you please help? Thank you in advance.- Anonymous
June 30, 2016
I have renamed the commands long ago to meet the common PowerShell naming standard. However I did not find the time to update this article. Please use Get-NTFSAccess. All commands are matching the pattern -NTFS.-Raimund- Anonymous
June 30, 2016
Thanks Raimund. It still didn't work states "CategoryInfo: ObjectNotFound: (Get-NTFSAccess:String), CommandNotFound Exception. FullyQualifiedErrorId: CommandNotFoundException".After unblocking and then extracting NTFSSecurity, the files extracted are: AlphaFS.dll, NTFSSecurity.dll, NTFSSecurity.format, NTFSSecurity.Init, NTFSSecurity, NTFSSecurity.types, NTFSSecurity-Help, PrivilegeControl.dll, ProcessPrivileges.dll and Security2.dll. Are these all the files that I should have? Am I missing any?I need to export all share folders, 2nd level subfolders and their corresponding permissions, access rights and if Inherited or not. I have used the below scripts but would like to have one that combines the output to a csv file. Can you please help?#1Get-ChildItem -Recurse | Select-Object -Property FullName, name, CreationTime, LastAccessTime, LastWriteTime, Attributes | Export-Csv structure.csv#2get-childitem \fileshare\folder -recurse | get-acl | select-object path,owner,accesstostring,group | export-csv “C:\security.csv”Thanks again in advance for your help and information!- Anonymous
July 01, 2016
Did you Import the Module in order to run the cmdlet?Import-Module NTFSSecurity
- Anonymous
- Anonymous
- Anonymous
June 30, 2016
Where did you copy the files after extraction to? it should be in one of the following folders:C:\Windows\system32\WindowsPowerShell\v1.0\ModulesC:\Program Files\WindowsPowerShell\Modules\NTFSSecurityC:\Users\Documents\WindowsPowerShell\ModulesDoes the module show up then calling "Get-Module -ListAvailable"?- Anonymous
July 01, 2016
Thanks Raimund for getting back to me. It worked! I did have the files extracted to the incorrect location. I'm new to PowerShell and trying to learn due to a project I've been assigned. This is very helpful. I really appreciate it! Thanks again. If I come across any other questions I will definitely ask you. Thanks!
- Anonymous
- Anonymous
Anonymous
July 11, 2016
How can I modify the below script to include: CreationTime, LastAccessTime and LastWriteTime as well as to exclude files. I just want folders and subfoldersGet-Item D:\Data | Get-NTFSAccessThanks in advance for your help!Anonymous
August 01, 2016
The comment has been removed- Anonymous
November 07, 2016
Sam, Did you manage to resolve this? I am getting the exact same error on one of my machines. Working fine on another...- Anonymous
April 07, 2017
Copia la carpeta descomprimida en la siguiente ruta: C:\WINDOWS\system32\WindowsPowerShell\v1.0\Modules y el módulo se cargará automáticamente.
- Anonymous
- Anonymous
Anonymous
October 23, 2016
Hello Raimund ,I am wondering if Get-ChildItem2 command include the -Include parameter is it possible in next revision?I want to filter ChildItems with extensions.- Anonymous
October 24, 2016
I have to admin, I have never used the Include parameter. What is your use case? Are you filtering for multiple extensions?- Anonymous
November 08, 2016
yes I want to filter multiple Extension. how can I do that I tried like this:-Get-ChildItem2 -Path "C:\Users\Rohan-PC\Desktop" -Filter " *.ps1, *.txt, *.pdf " -Recurse but not worked for me........results are blank only :( could you please help regarding this- Anonymous
November 08, 2016
Also tried like this:-Get-ChildItem2 -Path “C:\Users\Rohan-PC\Desktop” -Filter ' *.ps1' ,' *.txt,', ' *.pdf ' -Recurse- Anonymous
November 16, 2016
Raimund please help me :(
- Anonymous
- Anonymous
- Anonymous
- Anonymous
Anonymous
December 04, 2016
Hi Raimund, I'd like to use this module to control registry permissions via the default PSProviders, HKLM, HKCU. I was honestly surprised it didn't just work, but it gives an error."Get-Item HKLM:\SOFTWARE | Get-NTFSAccessGet-NTFSAccess : Unable to find the specified file."Would you consider this for a future update?- Anonymous
December 05, 2016
Sorry, this is why the cmdlets are name -NTFS. Nothing else as NTFS rights are supported. I know that there are some modules that handle both but this is quite hard to accomplish and has other downsides as permissions in the registry and NTFS are not the same.I have started a similar project for the registry. But this is not ready yet and needs someone with dev skills to take over. Interested? :)-Raimund
- Anonymous
Anonymous
December 07, 2016
Hello Raimond,I'm trying to use values from an array to set rights, but this not working.Could you please advise me how to change my statements?Code:$Folder = @("Home","Profiles")#Set RightsForEach ($Folder in $Folder) {Clear-NTFSAccess -Path "C:\Test$Folder" -DisableInheritanceAdd-NTFSAccess -Path "C:\Test$Folder" -Account 'Administrators','SYSTEM' -AccessRights FullControlAdd-NTFSAccess -Path "C:\Test$Folder" -Account 'domain\Folder_M_DL' -AccessRights Modify}Thank you.Alain- Anonymous
December 12, 2016
Can you be more specific about what is not working?As you are doing three changed on the same folder, I would recommend working with the security descriptor to write all changes at once:$sd = Get-NTFSSecurityDescriptor -Path D:\test$sd | Disable-NTFSAccessInheritance -RemoveInheritedAccessRules$sd | Clear-NTFSAccess$sd | Add-NTFSAccess -Account SYSTEM -AccessRights FullControl -AppliesTo ThisFolderSubfoldersAndFiles$sd | Add-NTFSAccess -Account randr -AccessRights FullControl -AppliesTo ThisFolderSubfoldersAndFiles$sd | Set-NTFSSecurityDescriptor-Raimund
- Anonymous
Anonymous
December 19, 2016
Hi Raimund,Great module, i however have some issues. I'm trying to set up access according to IGDLA.Ive created all groups, and all the shares, and my naming standard is L__NTFS_Read/write" and when I try to add the group access i get the following error:"Add-NTFSAccess : Cannot bind parameter 'Account'. Cannot convert value "name of group" to type "Security2.IdentityReference2". Error: "Some or all identity references could not be translated."$folders = Get-ChildItem -Directory C:\foreach ($folder in $folders) {$string1 = "L_"$folder.name $string2 = "_NTFS_Read"$Read = $string1 + $folder.name + $string2$readAdd-NTFSAccess $folder.fullname -Account '$read' -AccessRights Read -AppliesTo ThisFolderSubfoldersAndFiles }- Anonymous
December 19, 2016
L__NTFS_Read/write *- Anonymous
December 20, 2016
Hi Niklas,this means that windows could not translate the name into a SID. What happens if you cast the name into a SID manually?PS C:\Users\Install> [Security2.IdentityReference2]'G1 R_W'Sid AccountName LastError--- ----------- ---------S-1-5-21-1637053477-203267982-1749320357-1608 G1 R_W Why have you put the variable $read into single quotes when invoking Add-NTFSAccess? You should not use quotes at all as using them like you did it actually makes Add-NTFSAccess look for an account named $read.-Raimund- Anonymous
December 20, 2016
The comment has been removed- Anonymous
December 20, 2016
name stanard of the groups shoud be L__NTFS_Read/Write .(seems like i miss this each time)
- Anonymous
- Anonymous
- Anonymous
- Anonymous
Anonymous
January 27, 2017
I am having trouble removing FullControl permissions from a security group for a file share folder and subfolders below it. I ran the following command and let it finish, but when I look at the passthru results, no changes have been made. What could be the cause of this problem? I was able to test the command using a test user on a different directory and it worked fine.Here is the command I wrote:Remove-NTFSAccess -path '\domain\Share\OfficeShare' -Account $username -AccessRights FullControl -PassThru -VerboseAccount Access Rights Applies to Type IsInherited InheritedFrom ------- ------------- ---------- ---- ----------- ------------- Domain\OfficeGroup FullControl ThisFolderSubfoldersAn... Allow True VERBOSE: Disabeling all 0 enabled privileges...VERBOSE: ...finished- Anonymous
April 13, 2017
Late answer but maybe helpful for the future.The Remove-NTFSAccess call has be to exaclty like the access control entry you want to remove. It is easier to get the one you are searching for with Get-NTFSAccess and once you have filtered for the right one, pass it to Remove-NTFSAccess.
- Anonymous
Anonymous
March 15, 2017
Does anyone know why I would get a number when exporting the AccessRights instead of the actual rights? If I run this:dir -Directory $Directory | Get-NTFSAccess | Select-Object FullName, Account, AccessRights, IsInherited | Export-Csv -Path C:\Audit\exports\test.csvIn a console I get this:S:\Servicing\Clients\Deutsche Bank MMA\Shared_Servicing - Read Only ReadAndExecute, Synchronize TrueBut when I use powershell to fire up excel and move it into an excel file I get this:S:\Servicing\Clients\Deutsche Bank NT AUTHORITY\SYSTEM 2032127 TRUEWhat's that number?- Anonymous
April 15, 2017
I have just tried the same and the column "AccessRights" has readable values likeGenericAllModify, SynchronizeDelete, GenericExecute, GenericWrite, GenericRead2032127 is the value for FullControlPS D:> [Security2.FileSystemRights2]2032127FullControl
- Anonymous
Anonymous
March 30, 2017
During OSD I create folders and subfolders, share them, set the FSRM management properties, and finally use this module to set the NTFS permissions I want on these shared folders. I get the following error when trying to add "SYSTEM" to the permissions:Add-NTFSAccess : (1307) This security ID may not be assigned as the owner of this object: [\?\D:\Departments]And I get this for the remaining 5 shares.Does anyone have a quick work around?I'm using the command like this:$Path = D:\DepartmentsAdd-NTFSAccess -Path $Path -Account "SYSTEM" -AccessRights FullControl -AccessType Allow -AppliesTo ThisFolderSubfoldersAndFiles- Anonymous
April 12, 2017
What happens if you activate the restore privilege? Are you an admin on the target system?
- Anonymous
Anonymous
April 12, 2017
How do I give full control to Auditing Tabs- Anonymous
April 12, 2017
Add-NTFSAudit -Path .\AD-Performance\ -Account Everyone -AccessRights FullControl
- Anonymous
Anonymous
April 18, 2017
When I give permissions to C:\ for user "Creator Owner". It seems if Windows folder has a "Creator Owner" of TrustedInstalller, It would add both TrustedInstaller and Creator Owner. Same for all folders with different Owners. How to only have "Creator Owner" without it also adding the variable Owner in "Creator Owner" also. Add-NTFSAccess -Path C:\ -Account 'Administrators','System','Creator Owner' -AccessRights FullControlAnonymous
June 12, 2018
Hi, is it possible to Change the permissions from write,Synchronize to readandexecute,synchronize in one command?to remove the permissions with on command and add in a second command needs a lot of time?Many thanks- Anonymous
June 12, 2018
At the Moment I use two commands: Remove-NTFSAccess $Folder -Account $Account -AccessRights Synchronize,Modify -PassThru Add-NTFSAccess $Folder -Account $Account -AccessRights ReadAndExecute,Synchronize -AppliesTo ThisFolderSubfoldersAndFiles -PassThruis it possible to combine this command in one?
- Anonymous
Anonymous
February 09, 2019
The comment has been removed- Anonymous
March 03, 2019
The comment has been removed
- Anonymous
Anonymous
February 22, 2019
Hi,what is the best way to copy (after filtering) permission from one directory to another ?I would have liked to do get-ntfsAccess | where-object {$_account -like "domain*"} | add-ntfsaccess -path but add-ntfsaccess only support path from pipeline and not security ? (unlike remove-ntfsaccess)So what is the best way to do ? play with a for-each loop after the get-ntfsaccess ?It will be great if we have a simple solution :) usefull to migrate badly permission on an old file server to a new one Thanks for your help- Anonymous
February 22, 2019
sorry don't know why all formating is lost when I post my comment :/- Anonymous
March 03, 2019
The comment has been removed
- Anonymous
- Anonymous
Anonymous
March 19, 2019
Hi, I tried to apply this to a network share, but the inheritance gets removed, am I doing something wrong? Script and results below:PS C:\WINDOWS\system32> Get-NTFSAccess -Path "\gbtedvpfs01\test"Path: \gbtedvpfs01\test (Inheritance enabled)Account Access Rights Applies to Type IsInherited InheritedFrom ------- ------------- ---------- ---- ----------- ------------- BUILTIN\Administrators FullControl ThisFolderSubfoldersAn... Allow False unknown paren CORP\DLA_FS_List-Only ListDirectory, Synchronize ThisFolderSubfoldersAn... Allow False unknown paren CORP\FS IT RO ReadAndExecute, Synchronize ThisFolderSubfoldersAn... Allow True unknown paren CORP\FS IT RW Modify, Synchronize ThisFolderSubfoldersAn... Allow True unknown paren NT AUTHORITY\SYSTEM FullControl ThisFolderSubfoldersAn... Allow True unknown paren BUILTIN\Administrators FullControl ThisFolderSubfoldersAn... Allow True unknown paren PS C:\WINDOWS\system32> Add-NTFSAccess –Path "\gbtedvpfs01\test" -Account "corp\DLA_FS_List-Only" -AccessRights ListDirectory -AppliesTo ThisFolderAndSubfoldersPS C:\WINDOWS\system32> Get-NTFSAccess -Path "\gbtedvpfs01\test"Path: \gbtedvpfs01\test (Inheritance enabled)Account Access Rights Applies to Type IsInherited InheritedFrom ------- ------------- ---------- ---- ----------- ------------- BUILTIN\Administrators FullControl ThisFolderSubfoldersAn... Allow False CORP\DLA_FS_List-Only ListDirectory, Synchronize ThisFolderSubfoldersAn... Allow False All inherited object have gone, this does not happen on the local machine. Do I need to change my command?Anonymous
April 18, 2019
Hi all, is it possible to use NTFSSecurity command and options remotely? I mean in order to manage NTFS access and permissions on different servers in a farm acting on a single server? In case it is, can you please help me writing how? I am trying hard but unsuccessfully. Thanks in advance.MarcoAnonymous
May 11, 2019
Friends, help write a script to transfer the ACL from .wim to the current system.Required:- clear the current access rights of the current system- transfer permissions to files and folders for all users from .wim- inheritance rules for folders from .wim- the final step to transfer the owner of the folders (including the system folders: TrustedInstaller)What I have at the moment:$wPath = Read-Host "Enter original location for reading ACL (D: \ wim ) " # mounted image .wim$ACLPath = Read-Host "Enter the full name of the file in which to save the ACL (D: \ ACL_file) "function Recurse($path) { $fc = new-object -com scripting.filesystemobject $folder = $fc.getfolder($path) foreach ($i in $folder.files) {$i} foreach ($i in $folder.subfolders) { Write-Host $i.path $i if ( (get-item -Force $i.path).Attributes.ToString().Contains("ReparsePoint") -eq $false) { Recurse($i.path) } }}Recurse($wPath) | Get-NTFSAccess -ExcludeInherited | Export-Clixml $ACLPath".xml" $oldACL = Import-Clixml $ACLPath".xml"foreach ($p in $oldACL) { $p.Path | Clear-NTFSAccess }$oldACL | Add-NTFSAccessHelp seemed to me not complete (Add-NTFSAccess -? and Clear-NTFSAccess -?), could not understand how to apply the rules from .xml to files and folders in the root of the path C: , at the moment I manually edit the path in .xml