ELAM Driver
Hello again. It’s Rafal Sosnowski from Microsoft Dubai Security PFE Team and today I will be explaining what is the ELAM driver.
ELAM – Early Launch Anti-Malware is a piece of code that is loaded in the pre-boot environment and is responsible for verification of other drivers before they are loaded into memory. ELAM driver is being called by the Kernel and it reports the status of the driver images: if they are safe or unsafe to load. ELAM driver has been introduced in Windows 8 and is not dependent on UEFI nor BIOS implementation.

The early launch AM drivers are started soon after the NTOS kernel starts. For each subsequent boot driver, the AM driver receives a callback from the Kernel Plug and Play manager to determine whether the boot driver should be initialized. The AM driver evaluates the boot driver and must return good, bad, or unknown status of the driver. Based on the returned classification and defined policy, the PnP manager decides whether to initialize the boot driver.
Classification:
ELAM driver can return status of the boot driver as good, bad, or unknown. This image evaluation is based on the malware signature data stored under: HKLM\ELAM\<VendorName>\. This registry hive is loaded by the winload.exe process at the same time as ELAM driver
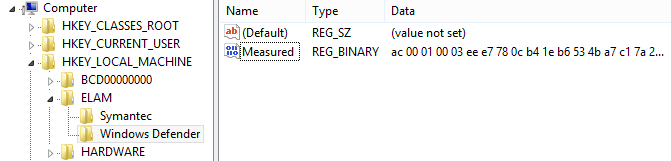
Within the key, the vendor will keep blacklists and/or whitelists of the drivers’ images and virus signatures. So far, ELAM cannot detect malware based on the heuristics or malware that has ability to polymorph so it relies on the image hashes and virus signatures.
Each ISV is responsible for updating and verifying its malware signature data for its ELAM driver. When the AM driver is initialized, it should verify the integrity of the malware signature data by validating a digital signature.
The ELAM hive is unloaded after its use by Early Launch Antimalware for performance reasons. If a user mode Antivirus service wants to update the signature data, it should mount the hive file from the c:\Windows\System32\config\ELAM. The storage and retrieval format of these data BLOBs is left up to the Antivirus Vendor, but the signature data must be signed so that the AM driver can verify the integrity of the data.
Defined Policy
When the status of the drivers is returned (good, bad, unknown), system will decide whether load particular driver or not, based on the policy stored in:
HKLM\SYSTEM\CurrentControlSet\Policies\EarlyLaunch\ DriverLoadPolicy
This Policy can be defined manually or via GPO under:
Computer Configuration \ Administrative Templates\ System \ Early Launch Antimalware\ Boot-Start Driver Initialization Policy

If the policy is not configured or disabled the boot drivers determined to be Good, Unknown or Bad but Critical are initialized and the drivers determined to be Bad are skipped.
Driver is marked as critical if internal routine of ELAM driver determines that blocking this particular driver would cause system to halt / bluescreen.
An image is treated as unknown when an error is returned from the initialize image callback or when the signature data doesn’t exist in the registry.
After classification of drivers has been finished and malicious drivers were blocked,the ELAM driver will unload. Anti-Malware engine should be started prior to the early launch AM driver being unloaded. This means that the runtime AM engine should be a boot driver that is verified by the early launch AM driver not a user mode process.
Default Windows ELAM driver:
By default, ELAM driver is provided by Windows Defender and is registered as WdBoot.sys driver. You can find it in %systemroot%\system32\drivers folder.

3rdparty ELAM drivers:
Microsoft requires that Early Launch Antimalware vendors be members of the Microsoft Virus Initiative (MVI). This membership ensures that the vendors are active antimalware community participants with a positive industry reputation and participate in antimalware initiatives.
For example, if we install Symantec Antivirus, it will register its own ELAM drive called SymELAM.sys:

If you want to register your own ELAM driver for testing purposes, use command:
sc create Elam-Test binpath=%windir%\\system32\\drivers\\TEST-ELAM.sys type=kernel start=boot error=critical group=Early-Launch
ELAM driver signing:
Every ELAM driver has to be signed by Microsoft Code-signing certificate. This certificate has to have special EKU (Extended Key Usage) indicating Early Launch Anti-Malware driver. If the ELAM driver is not signed with such certificate it will fail to load.
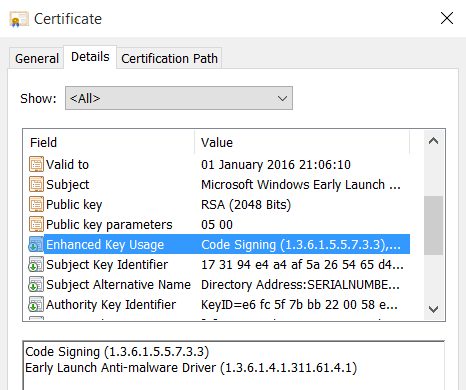
Winload checks the signatures of all boot drivers as they are loaded into memory. On 64-bit platforms all boot drivers must have valid signatures, their certificates must chain to a trusted root CA, and their certificates must contain the Codesigning enhanced key usage (EKU) extension. Signing is not required on 32-bit platforms. ELAM drivers are special in that they must be signed by Microsoft, and their signing certificates must also contain a special EKU indicating that it is an ELAM Driver (OID: 1.3.6.1.4.1.311.61.4.1). This is true for both 32-bit and 64-bit platforms.
Additional considerations:
Backup Driver Installation
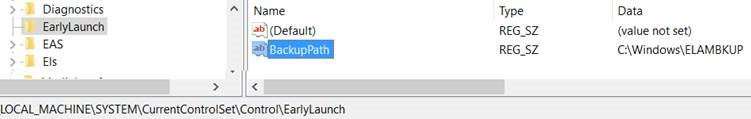
To provide a recovery mechanism in the event that the ELAM driver is inadvertently corrupted, the ELAM installer also installs a copy of the driver in a backup location. This will allow WinRE to retrieve the clean copy and recover the installation.
The installer reads the backup file location from the BackupPath key stored in
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\EarlyLaunch\BackupPath
Disabling ELAM:
Like Secure Boot, ELAM driver can be disabled by the owner of the platform. User can restart the machine and put it into Advanced Restart mode. Just restart your PC using combination of “Shift + Power > Restart” or execute:
Shutdown /r /o /t 0
and follow the menu path: Troubleshoot > Advanced Options > start up Settings > Restart

On next screen you can choose Disable early launch anti-malware protection:
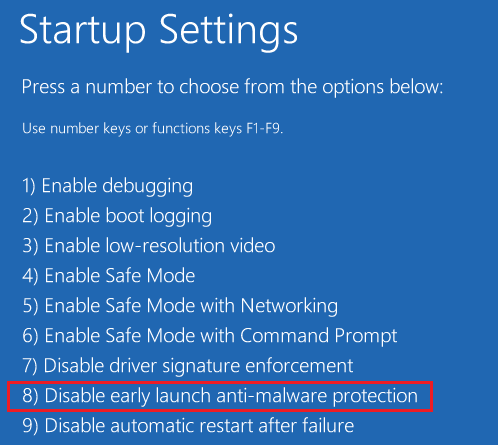
This has been implemented to remediate situations where ELAM blocks some important driver which prevent machine from botting. In this case you can disable ELAM, remove problematic driver and boot your PC normally. The next time you reboot your computer, Early Launch Anti-Malware Protection will automatically start again and continue protecting your computer. To remove the ELAM driver permanently you would have to unregister it from the system.
So to summarize: ELAM has antimalware capabilities and can block drivers from being loaded into memory before they are initialized. ELAM is part of the Microsoft Trusted Boot standard and can mark your drivers with status: good, bad or unknown and then allow or prevent from loading. ELAM can be disabled by the user that has physical access to the computer.
Comments
- Anonymous
January 03, 2017
Thank you for the post. I want to know something that I could not find in your post. In your post you mentioned that "Every ELAM driver has to be signed by Microsoft Code-signing certificate". Let's say I want to build an antivirus software, how can I create an ELAM driver? And how can I sign it with Microsoft Code-signing certificate?Regards - Anonymous
January 10, 2017
If you are antivirus vendor you can submit your sample ELAM driver via the WHQL Portal. We perform multiple checks of your package you have submitted including antimalware analysis. - Anonymous
January 30, 2017
Thank you for comment. I create a sample elam driver from the microsoft sample( https://github.com/Microsoft/Windows-driver-samples/tree/master/security/elam ). Then I create a test certificate with Early Launch Anti-Malware Driver EKU and finally follow the instructions to create a protected service ( https://msdn.microsoft.com/en-us/library/windows/desktop/dn313124(v=vs.85).aspx ). When I call InstallElamCertificateInfo function GetLastError send me 577 that means signature can not be verified. But I do not know if my test certificate can not be verified or the signatures which I enter the MicrosoftElamCertificateInfo in elam driver resource can not be verified?Please kindly guide me.Regards - Anonymous
February 03, 2017
You can enable CAPI2 log in the "ventvwr.msc and verify if certificate validation has passed or not. In the event log you will see which step is failing. Beware that this log produces a lot of events. - Anonymous
February 03, 2017
I figure out problem. My test certificate was wrong and I fixed it. Now I can install my anti-malware service as protected service. But when I call "StartService" function GetLastError returns 1053(The service did not respond to the start or control request in a timely fashion). But it do not wait until timeout it returns that error immediatelly. Do you have any suggessition about this situation? - Anonymous
February 17, 2017
Brian connect to the debugger and see what is blocking your service from starting. I recommend windbg - Anonymous
April 13, 2017
How to enable ELAM support on SCEP on Windows 8.1 and Server 2012 R2? - Anonymous
May 10, 2017
in SCEP 2012 R2 I believe it is enabled by default. Are you experiencing any issues with that? - Anonymous
July 06, 2017
Thank you, Rafal, for your article. Is it possible completely uninstall Windows Defender? We have a problem in testing our ELAM driver using Microsoft WHLK test. All specific ELAM tests failed but they failed with the same reason "Reason=Setup". Before the first ELAM test there is an error from test setup.The error says following: “Multiple ELAM drivers are initialized. Please ensure that only one ELAM driver is used for WHCK testing. For instance, the Windows Defender ELAM driver should be disabled if you want to certify your ELAM driver…”I disabled Windows Defender but the test failed again. WDboot.sys is not uninstall yet but its "Start" option moved from 0(boot) to 3 (on demand). I think if I could completely uninstall Windows Defender I could pass this error. I would appreciate any suggestion from you.