The End of Support for Older TLS Versions in Office 365
by David Branscome, with a callout to Joe Stocker at Patriot Consulting for the heads-up!
The SSL/POODLE Attack Explained
UPDATE: As per the support article listed here (https://support.microsoft.com/en-us/help/4057306/preparing-for-tls-1-2-in-office-365) We will be extending support for TLS 1.0/1.1 through October 31, 2018 in order to help ensure our customers are adequately prepared for the changes.
As most of you know, there was a significant vulnerability identified in the SSL 3.0 protocol back in 2014, named POODLE (Padded Oracle On Downgraded Legacy Encryption).
The problem was this: SSL 3.0 is basically an obsolete and insecure protocol. As a result, it has been, for the most part, replaced by its successors, TLS 1.0 and TLS 1.2. The way a client-server encryption negotiation sequence would typically work is that the client would contact a server, and through a handshake process, agree on the highest level of security over which they both can communicate. So, for example, a client makes a request to a server and says, “I’d like to use TLS 1.2 for our communication, but I can also use TLS 1.0, if you need to.” The server responds with, “I don’t speak TLS 1.2, but I do speak TLS 1.0, so let’s agree to use that.” They then use that downgraded protocol as their preferred encryption method. The downgrade sequence could ALSO downgrade the encryption to use SSL 3.0, if necessary.
However, even in situations where client and server both support the use of the newer security protocols, an attacker with access to some portion of the client-side communication could disrupt the network and force a downgrade to the SSL 3.0 encryption. This is typically referred to as a man-in-the-middle attack, because the attacker sits on the network between two parties and captures their communication stream. This is an altogether separate type of attack, unrelated to the POODLE vulnerability itself, and must be defended against using other methods.
Anyway, now that the attacker has successfully forced SSL 3.0 encryption to be used, and the attacker has access to the communication stream, the attacker can attempt the POODLE attack and get access to decrypted information between the client and the server.
When this vulnerability came out, there was a significant amount of work done worldwide to mitigate the impact and scope of the issue. The vulnerability in SSL 3.0 itself couldn’t be remediated because the issue was fundamental to the protocol itself. Because of this, the best solution for organizations was simply to disable support for SSL 3.0 in their applications and systems.
So That Was 3 Years Ago….
As described in the links at the bottom of this article, Microsoft still supports the use of TLS 1.0 and 1.1 for clients connecting to the Office 365 service. However, due to the potential for future downgrade attacks similar to the POODLE attack, Microsoft is recommending that dependencies on all security protocols older than TLS 1.2 be removed, wherever possible. This would include TLS 1.1/1.0 and SSL v3 and V2.
The problem here is that many operating systems and applications have a hardcoded protocol version to ensure interoperability or supportability. In Windows 8 and Windows Server 2012 and higher, the default protocol that is used is TLS 1.2 – which is good.
However, in Windows 7 and Windows 2008 R2, TLS 1.0 was the default protocol. In fact, TLS 1.1. and 1.2 were actually configured as “disabled”. See the table below:
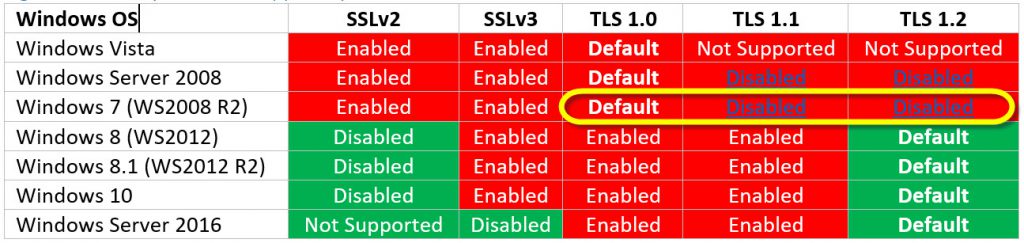
As outlined in the article “Preparing for the mandatory use of TLS 1.2 in Office 365”, this is going to present a problem if your organization is still using Windows 7/Vista clients. Why?
Because on October 31, 2018, Microsoft Office 365 will be disabling support for TLS 1.0 and 1.1. This means that, starting on October 31, 2018, all client-server and browser-server combinations must use TLS 1.2 or later protocol versions to be able to connect without issues to Office 365 services. This may require certain client-server and browser-server combinations to be updated.
Our internal telemetry of client connections indicates that this shouldn’t be a problem for most organizations, since the majority are not using TLS 1.0 or 1.1, anyway. However, for the network you manage it’s probably a good idea not to simply assume everything will be great. 😊
As an example, if you’re using any on-premises infrastructure for hybrid scenarios or Active Directory Federation Services, make sure that these infrastructures can support both inbound and outbound connections that use TLS 1.2.
How Do I Know if I Need to Take Action?
A new IIS functionality makes it easier to find clients on Windows Server 2012 R2 and Windows Server 2016 that connect to the service by using weak security protocols.
There are also some simple checks available from Qualys Labs to check browser compatibility - https://www.ssllabs.com/ssltest/viewMyClient.html as well as the certificate and encryption configuration on your servers with SSL certificates - https://www.ssllabs.com/ssltest/ .
Hopefully these checks will help you to ensure that your organization is ready when the change is made to the Office 365 services early next year.
Additional Resources
Preparing for the mandatory use of TLS 1.2 in Office 365 https://support.microsoft.com/en-us/help/4057306/preparing-for-tls-1-2-in-office-365
Solving the TLS 1.0 Problem https://www.microsoft.com/en-us/download/confirmation.aspx?id=55266
Disabling TLS 1.0/1.1 in Skype for Business Server 2015 - Part 1 and 2
Implementing TLS 1.2 Enforcement with SCOM
Exchange Server TLS Guidance
Intune TLS Guidance https://blogs.technet.microsoft.com/intunesupport/2018/06/05/intune-moving-to-tls-1-2-for-encryption/
Preparing for TLS 1.0/1.1 Deprecation - O365 Skype for Business https://techcommunity.microsoft.com/t5/Skype-for-Business-Blog/Preparing-for-TLS-1-0-1-1-Deprecation-O365-Skype-for-Business/bc-p/223608
Comments
- Anonymous
February 07, 2018
Does this affect SMTP connections from 3rd parties as well, example: receiving mail from a 3rd party mail server which does only support TLS 1.0 or maybe does not even support encryption for mail delivery?- Anonymous
February 07, 2018
Yes, RabanserD, it affects the SMTP connections as well.
- Anonymous
- Anonymous
February 11, 2018
Could you help confirm which date is correct? This article says March 1, 2018. However, " https://support.microsoft.com/en-us/help/4057306/preparing-for-tls-1-2-in-office-365 "says, "October 31, 2018, Microsoft Office 365 will no longer support TLS 1.0 and 1.1."Thank you.- Anonymous
February 12, 2018
Hi Bobby! Yes, we did modify the support date and extended it through October 31, 2018 to make sure all our customers have time to prepare adequately for the change. I will adjust the article.
- Anonymous