Secure Your Office 365 Tenant - By Attacking It (Part 1)
By David Branscome
I've been waiting several months for this day to arrive. The Office 365 Attack Simulator is LIVE!
If you log into your Office 365 E5 tenant with the Threat Intelligence licensing, it shows up here in the Security & Compliance portal. 
When you click on it, the first thing it will tell you is that there are some things you need to set up before you can run an actual attack. There’s a link that says, “Set up now” (in the yellow box shown below). After you click that link, it says the setup is complete, but you’ll have to wait a little while before running an attack. (I only had to wait about 10 minutes when I set it up) 
It also reminds you that you need to have MFA (multi-factor authentication) set up on your tenant in order to run an attack. This makes a lot of sense, since you want to ensure that anyone who runs the attack is a “good guy” on your network.
To set up MFA, follow the steps here:
Go to the Office 365 Admin Center
Go to Users> Active users.
Choose More> Setup Azure multi-factor auth 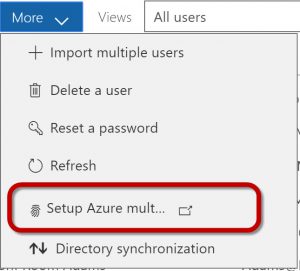
Find the people who you want to enable for MFA. In this case, I'm only enabling the admin account on my demo tenant.
Select the check box next to the people you want to enable for MFA.
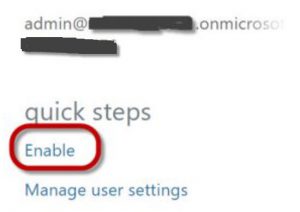
On the right, under quick steps, you'll see Enable and Manage user settings.
Choose Enable.
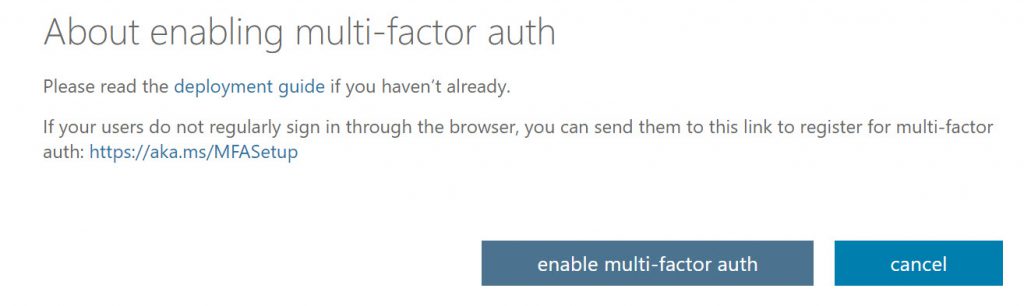
In the dialog box that opens, choose enable multi-factor auth.
The Attacks
Spear Phishing
With a spear phishing attack, I’m sending an email to group of “high-value” users - maybe my IT admins, the CEO/CFO, the accounting office, or some other user group whose credentials I want to capture. The email I send contains a URL that will allow me to capture user credentials or some other sensitive data as part of the attack. When I set up this attack, it needs to look like it’s coming from a trusted entity in the organization. Maybe I’ll set it up to make it appear as though it’s coming from the IT Security group asking them to verify their credentials.
Brute Force Password (a.k.a., Dictionary Attack)
In this attack, I’m running an automated attack that just runs through a list of dictionary-type words that could be used as a password. It is going to use lots of well-known variations, such as using “$” for “s” and the number 0 for the letter O. If you thought Pa$$w0rd123 was going to cut it as a secure password on your Office 365 account, this attack will show you the error of your ways.
This type of attack is pretty lengthy in nature because there are thousands of potential guesses being made against each user account. The attack can be set up to vary in frequency (time between password guesses) and number of attempts.
It’s important to note that if a password is actually found to be successful, that password is NOT exposed to anyone – even the admin running the attack. The reporting simply indicates that the attack was successful against Bob@contoso.com, for example.
Password Spray Attack
A password spray attack is a little different from the brute force password attack, in that it allows the admin/attacker to define a password to use in the attack. These would typically be passwords that are meaningful in some way – not simply an attempt using hundreds, or thousands of guesses. The password you use could be something like the name of a football team mascot and the year they won a championship, or the name of a project that people in one department are working on. Whatever criteria you select, you define what password or passwords should be attempted and the frequency of the attempts.
Ready? Let’s go hunting…
Launching a Password Spray Attack
First, I’ll try the password spray attack. I’ve set up several accounts in my test tenant with passwords that are similar to the one I’ll attempt to exploit – which is Eagles2018! . Notice that, by most criteria, that’s a complex password – upper and lower case, alphanumeric and it includes a special character, but it’s also a fairly easily-guessed password, since the Philadelphia Eagles won the Super Bowl in 2018 (though it pains me to say that).
I’ve set up a couple users with that password to ensure I get some results.
I go to my Attack simulator and click on Launch Attack.

The first screen is where I name the attack.
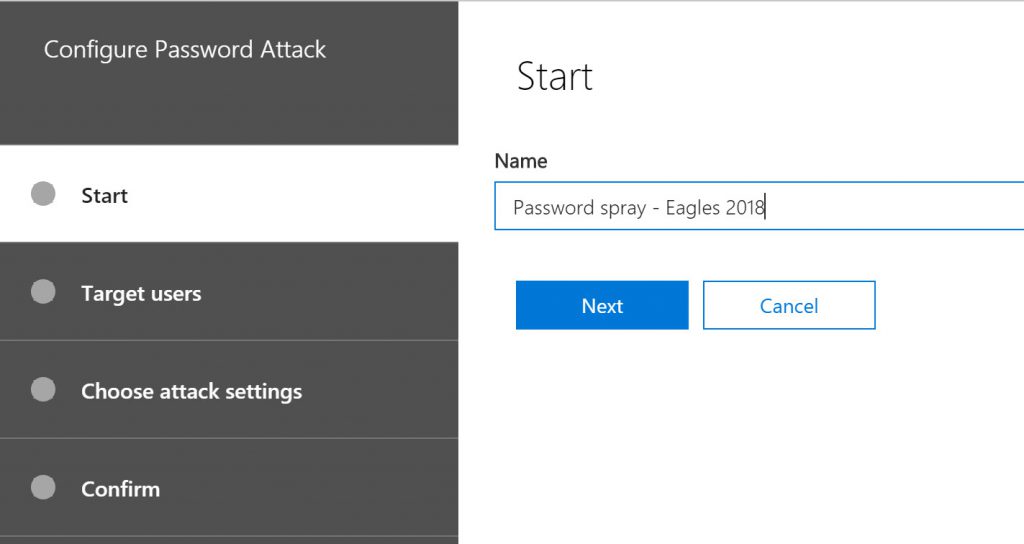
Next, I select the users I want to target. Notice that I can select groups of users as well.

Now I manually enter the passwords I want to use in the attack.
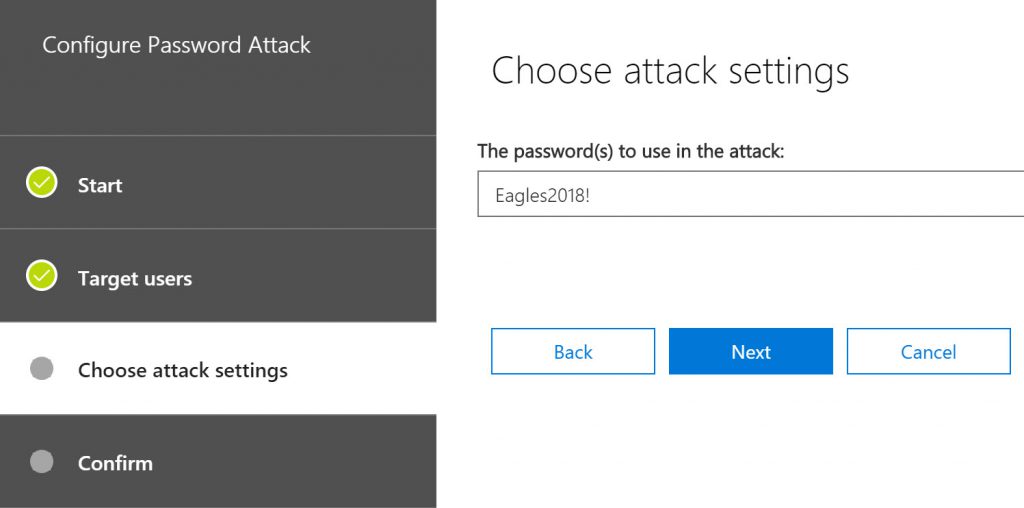
Confirm the settings, click Finish and the attack will begin immediately.
If I go back to my Attack Simulator console, I can see the attack running.
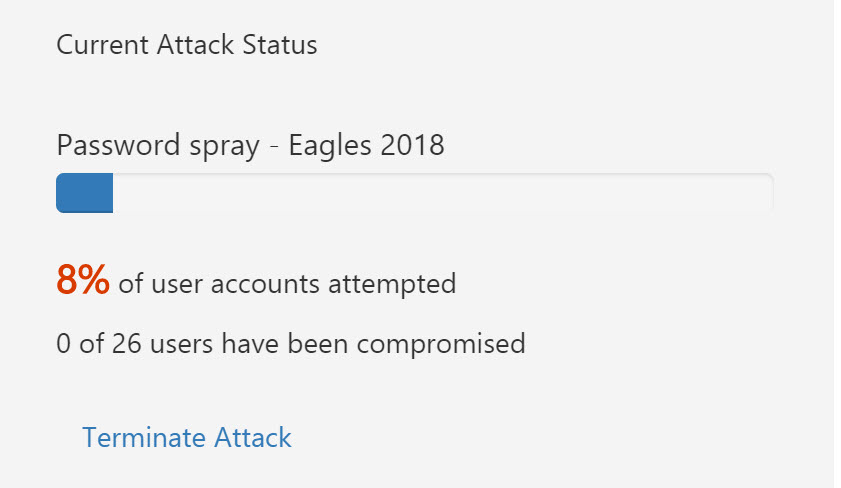
After the attack completes, I see the users who have been compromised using the password.
(Yes, I’ve reset their passwords now, so don’t try and get clever.) 😊
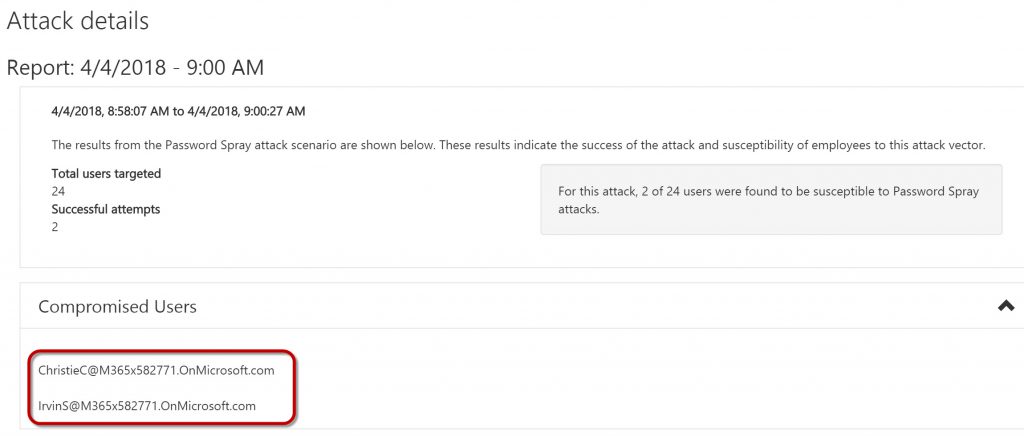
Now I politely encourage ChristieC and IrvinS to change their password to help ensure their account security.
Launching a Brute Force Password (Dictionary Attack)
Again, I’ve set up a couple accounts with some pretty common password combinations (P@ssword123, P@ssw0rd!, etc..)
I walk through the configuration of the attack, which is very similar to the Password Spray attack setup. 
I set up my target users as before, and then I choose the attack settings.
In this case, I uploaded a text file containing hundreds of dictionary passwords, but you can create a sampling of several passwords by entering them manually one at a time in the field above the Upload button. 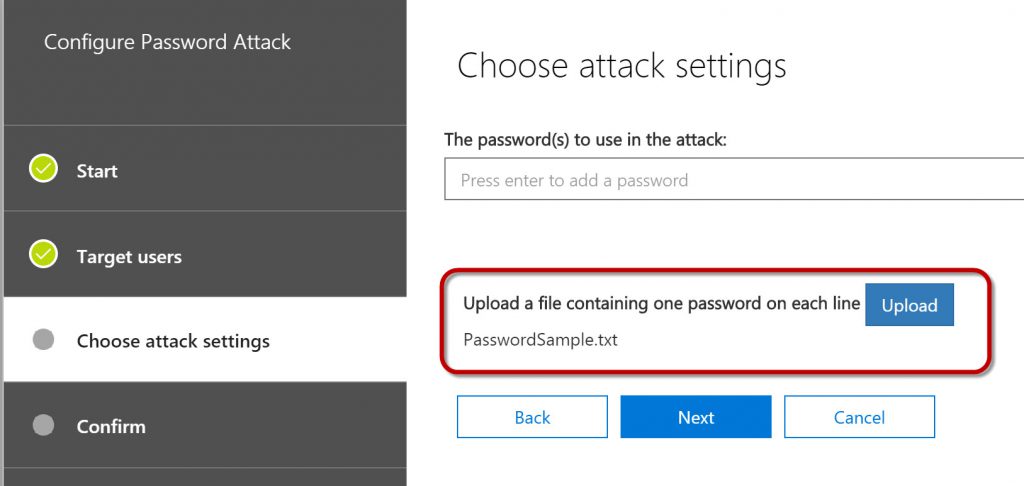
As the attack runs, you’ll see something like the screenshot below. Remember, if you have a large number of users and a very large wordlist for the dictionary attack, this attack will run for quite some time as the simulator cycles through all the possible variations for each user. 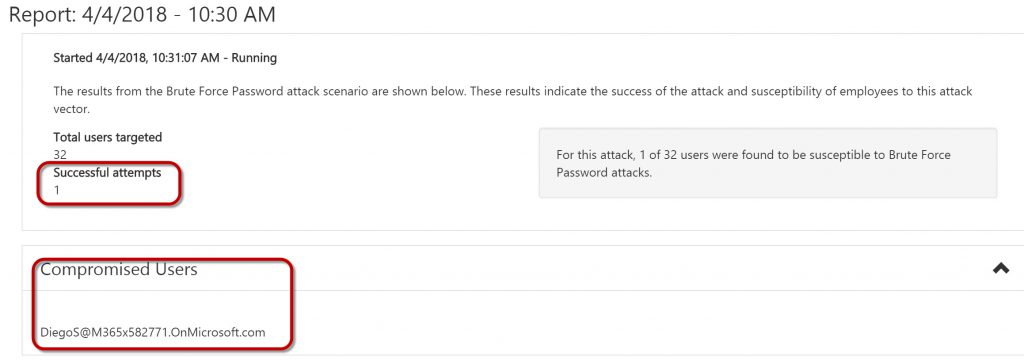
And again, when the simulation is complete, you’ll want to caution DiegoS on his lack of good password hygiene.
In my second blog post, I’ll show you how to do a Spear Phishing Attack. These are the REALLY sneaky ones….