AzureADPoSh: Azure AD Applications Password Expirations
Quick Post, I was recently asked how to find all the Application’s Password Expiration Date in Azure AD. I'm not going to cover what this is or what this is used for (Integrating applications with Azure Active Directory) but if you open Azure AD and navigate to the Registered Applications and select one of the Applications this is what you will see. For large enterprises this could be a difficult task.
Here is the cmdlet I threw together to gather this info for all applications in an Azure AD Instance.
#if you havent installed azuread module
find-module azuread | Install-Module
#connect to Azure AD
connect-azuread
foreach($AADapp in Get-AzureADApplication){
Get-AzureADApplicationPasswordCredential -objectid $AADapp.objectid | select `
@{name='DisplayName';expression={$AADapp.DisplayName}},StartDate,EndDate
}
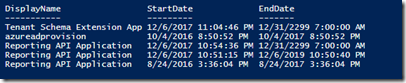
Results should look like this:
Looks like I have a few expired passwords, that I will want to address.
Updated 1/12/2018
I added a calculated property to flag an expired key as expired. I then added a separate set of code that goes and creates a new key and removes the old key. I would probably look for a threshold of at least 5 days before it is deleted
connect-azuread
$results = @()
foreach($AADapp in Get-AzureADApplication){
$results += Get-AzureADApplicationPasswordCredential -objectid $AADapp.objectid | select `
@{name='ObjectID';expression={$AADapp.objectid}},KeyId, `
@{name='DisplayName';expression={$AADapp.DisplayName}},StartDate,EndDate, `
@{name='Expired';expression={if($_.EndDate -lt $(get-date)){$true}}}
}
$newkeys = @()
foreach($key in ($Results | where {$_.Expired -eq $true})){
#create a new Key can add a startdate, enddate, customkeyidentifier as well
$newkeys += New-AzureADApplicationPasswordCredential -objectid $_.ObjectID
#delete the old Key
Remove-AzureADApplicationPasswordCredential -ObjectId $_.objectid -keyid $_.keyid
}
$newkeys
That is all I have for now. Hope you find this useful
-Chad