Analyze NETSH traces with Wireshark or Network Monitor, convert ETL to CAB
I wrote a post about how I captured a NETSH trace here "Capture a NETSH network trace". I like to use Wireshark to analyze my network traces, this post describes how I analyzed a NETSH .ETL trace file in Wireshark.
NOTE: Wireshark is not a Microsoft product it is a 3rd party tool.
Basically, I exported the .ETL file into a .CAB file using Microsoft Message Analyzer, downloadable from here.
Here is a link to the archived version of Network Monitor 3.4.
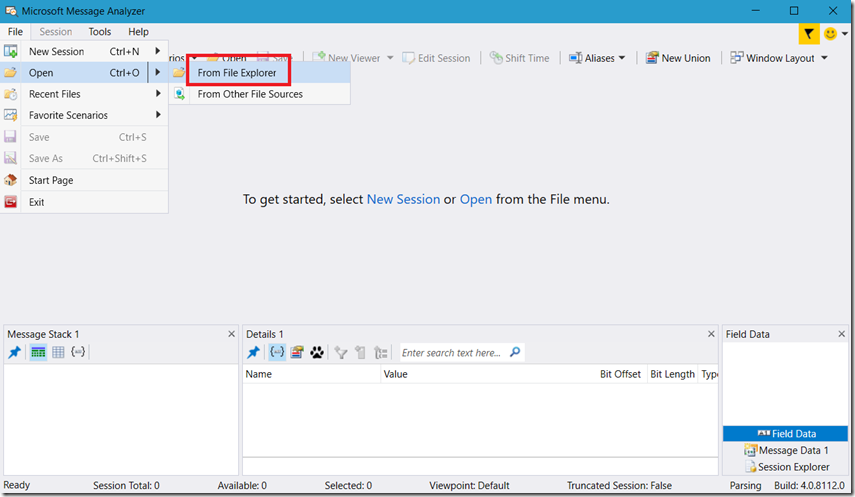
First, after installing Microsoft Message Analyzer, open it and select File –> Open –> From File Explorer, as see in Figure 1.
Figure 1, how to analyze export open an NETSH .ETL ETL trace in Wireshark or Network Monitor
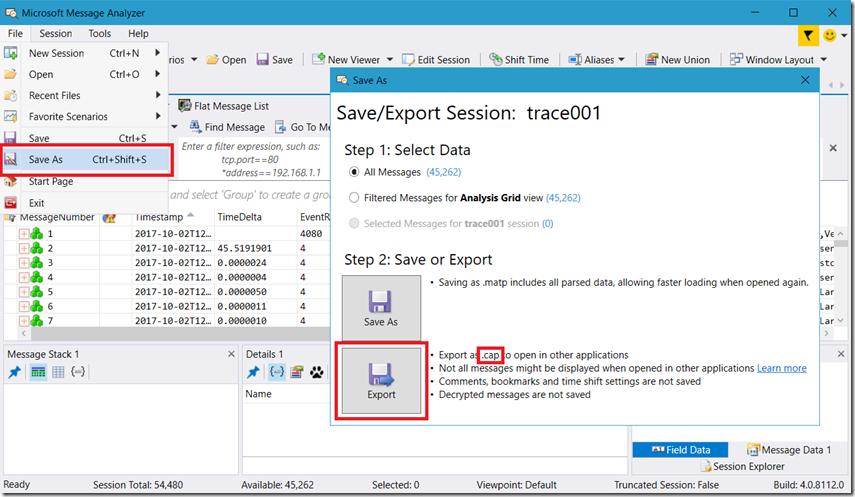
Select the ETL trace and open it in Microsoft Message Analyzer. Once loaded, select File –> Save As and then Export, as shown in Figure 2.
Figure 2, how to analyze export an NETSH .ETL ETL trace in Wireshark or Network Monitor
Once exported, open the .CAP file in Wireshark or Network Monitor. See my other post here that explains some about how I analyzed the trace.
Comments
- Anonymous
October 31, 2018
When I open an ETL file using Event Viewer, it recommends converting to the new event log format. If I let it do the conversion, it creates an EVTX and a CAB file. Is the CAB created by message analyzer different from the one created by Event Viewer in that process?