Block Windows 10 Public Store using Microsoft Intune (but still allow the business store)
Hi Windows 10 experts and lovers :)
Today I want to talk to you about a very exciting feature which has been released in Windows 10 managed by Microsoft Intune. Now it's possible to disable the Windows 10 public store while keeping access to the business store (Windows Store for Business) .
Side note: We also have released in Microsoft Intune the integration with Windows Store for Business, which let you finally deploy silently modern apps from the store to users without having them to manually install the app. A coworker made a great article about how to implement this integration.
To block the public store, you need to create a new custom Windows 10 policy in Microsoft Intune (we create a new one because this one will target users and not devices).
- Connect to Microsoft Intune management portal
- From "Policy", create a new "Custom Configuration" policy for Windows 10.
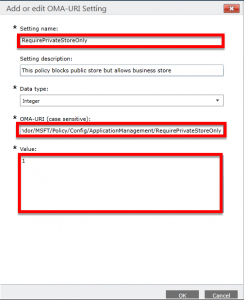
- Create a new OMA-URI setting. You will find details on the CSP policy reference page.
- OMA-URI: ./User/Vendor/MSFT/Policy/Config/ApplicationManagement/RequirePrivateStoreOnly
- Value: 1
- Then validate the policy.
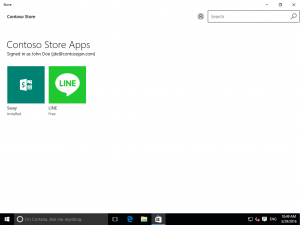
- And deploy that policy to a user collection. Here is the end result after you refresh MDM policy on a Windows 10 computer: public store's tabs has disappear but business store is still there :)
Everyday we're working hard to make Windows 10 more manageable using MDM. Hope you will enjoy this new feature :)
See you next time!
Comments
- Anonymous
April 07, 2016
Hi Hammoudi - this is fantastic, I've been asked about this repeatedly. Unless I missed it this setting isn't listed on the Windows 10 OMA-URI page on MSDN - do you know if it's going to be documented elsewhere? thanks- Anonymous
April 07, 2016
sorry Hammoudi - I meant to say that the link you have above to the CSP includes it, but the OMA-URI link within Intune itself doesn't seem to have it yet.- Anonymous
April 07, 2016
Hi Mark, thank you for visiting my blog :) You're right, the OMA-URI link within Intune console doesn't look up to date. This link doesn't contain any user settings apparently so you should always refer to the Windows 10 CSP site since custom Intune policies will always be able to set those CSP settings.
- Anonymous
- Anonymous
- Anonymous
May 05, 2016
Hi HammoudiI applied this policy in my tenant. I am using a Windows 10 enterprise eval version 1511 build 10586 VM and a Windows 10 version 1511 Phone. However, this policy is not reflecting on Windows 10 VM, it is not showing at all under devices->policies in the Intune console either. As for Windows Phone, the policy is applied with an error. Please help resolve. - Anonymous
July 28, 2016
Hi Samir,Great post! Thanks so much. I am attempting to deploy this policy but am getting a "Remediation Failed" error. Any idea what might be causing this? - Anonymous
August 12, 2016
Is it possible to configure this entirely in SCCM 2012? My organization has it setup to have Mobile Device Management handled through SCCM. I was able to create this policy in the Intune console, but I am unable to find a way to apply this to SCCM.- Anonymous
August 21, 2016
Hi I don't know if it applies to ConfigMgr 2012 but I found online a procedure to set OMA-DM using SCCM Current Branch with Intune. https://www.anoopcnair.com/2016/01/27/how-to-create-and-deploy-oma-dm-policy-with-sccm-current-branch-and-intune-hybrid/ Hope it helps!
- Anonymous