New Azure VPN Gateway SKU's provide much higher bandwidth for hybrid workloads
Background: Education customers, particularly Higher Education customers, tend to invest in Internet connectivity differently than the average company focused on making or selling widgets. Commodity Internet connectivity investments are measured in multiple Gigabits/Sec of bandwidth for many of these customers. A good number of my EDU customers are members of Internet2 (I2), a networking consortium providing members high performance private connectivity between members and service providers like Microsoft Azure and Office 365. It's not uncommon to see 10 Gb/s and even 100 Gb/s I2 peering at my research intensive Higher Education customers.
Wow - that's a lot of bandwidth for public IP endpoint services in Azure like Azure Storage (REST API), Azure Backups, Azure Site Recovery replication traffic, Azure App Service Web Sites, etc. But some hybrid workloads in Azure require secure, routable private network connectivity - for example VM's running databases, line of business applications and many traditional client/server application stacks that presume LAN connectivity between app tiers, dependent systems and even end users on-premises. What are the options for these workloads? There are three primary options: Site to Site VPN, 3rd party Network Appliances from the Azure Marketplace, and ExpressRoute. Check out Gaurav's post for more detail on all three here.
I'm going to focus on Site to Site VPN here because the previous IPsec tunnel throughput limits of our Azure Gateway option - 100 Mb/s and 200 Mb/s - were problematic for some customers. For light-churn workloads like Domain Controller replication these limits were not an issue, but for large server to server database replication jobs or file server to file server copy operations, these limits were not ideal. Now we have options up to 1.25 Gb/s. Excellent! But performance comes at a cost, what are the costs of these new SKU's? The good news is the Basic SKU remains unchanged in price as well as performance, but the VpnGw1 SKU costs the same as the old High Performance SKU and offers 250% more throughput! Here are the details from the pricing page:
VPN GATEWAY TYPE
PRICE
BANDWIDTH
S2S TUNNELS
P2S TUNNELS
Basic
~$26.79/mo
100 Mbps
Max 101-10: Included
Max 128
VpnGw1
~$141.36/mo
500 Mbps
Max 301-10: Included11-30: $0.015 per tunnel
Max 128
VpnGw2
~$364.56/mo
1 Gbps
Max 301-10: Included11-30: $0.015 per tunnel
Max 128
VpnGw3
~$930/mo
1.25 Gbps
Max 301-10: Included11-30: $0.015 per tunnel
Max 128
* Monthly price estimates are based on 744 hours of usage per month.
These changes got me so excited I wanted to see the new SKU's in action with some performance tests. Before I get to that, I want to strongly recommend that customers review the VPN Gateway documentation here and customers with existing Azure VPN Gateways deployed under the old SKU's need to check out the migration steps described there if they want to move to the new SKU's.
Test Environment
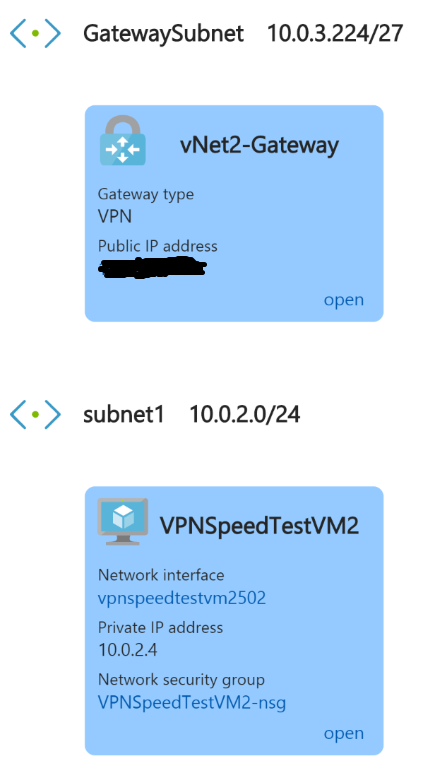
Unlike my customers, I don't have multi-Gb/s connectivity between my home lab and Azure, and I'm not interested in testing my cable provider's network - just the new Azure VPN Gateway SKU's. So I chose to test a VNet to VNet connection as described in the docs here. So I'll need a couple of vNets, subnets, Gateway subnet, VPN Gateways, VPN Connections and VM's. But who's got time to click through the portal to create that infrastructure for a quick test? So I searched the Azure Quick Start template gallery of hundreds of templates for a recent (new SKU's remember) VNet to VNet VPN scenario and found this one. It only has four parameters and sets up all the networking I needed for my test. Note that I selected VpnGw1 for the Gateway SKU parameter so that my Gateways would deploy at the SKU just above Basic (hey, my boss has to approve my Azure spend just like yours!). Those of you that have provisioned a VPN Gateway before know that it's slower to provision than some other Azure resources. It took about 45 minutes for my deployment to wrap up, but it sure was nice to have the IPsec tunnel up and no networking config needed! I added an Ubuntu Server 17.0 VM, size DS2v2 for it's "high" network throughput, into each vNet.
Here's a visual of the VNet and VM config:
Test Performance using iperf
At this point I feel compelled to state the obvious - your mileage may vary when testing performance and my results may not be exactly reproduced during a different lunar phase or proton flux condition. You may want to check your space weather conditions first :-) With that out of the way, let's get on to the bit-shipping!
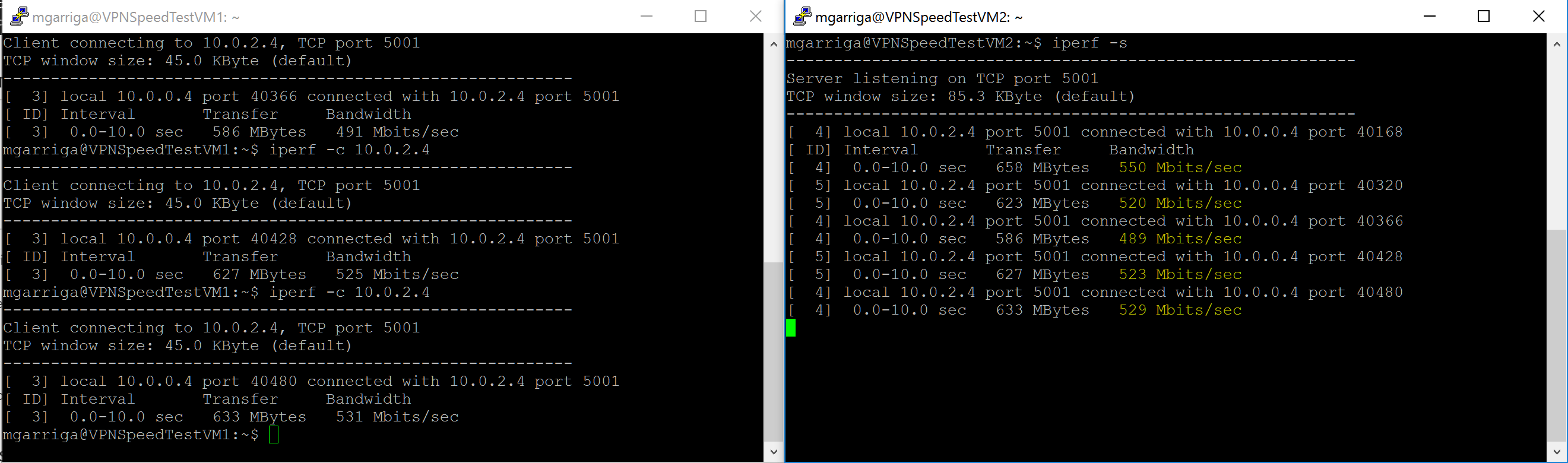
Installing and using iperf is super easy. I SSH'ed over to each VM and installed using "sudo apt-get install iperf" then I had VM2 be the "server" with "iperf -s" and VM1 was the client with "iperf -c VM2's private network IP Address" Naturally I ran the client multiple times to get a better average picture:
Conclusion
For customers with ample available Internet and/or I2 bandwidth, these new Azure VPN Gateway SKU's raise performance to where they can be a consideration for more hybrid workloads than in the past and testing shows that the gains are real and impactful.