System security beyond the firewall
System security is an interesting topic and as most readers of this publication would appreciate, there is always a trade off in security. Security by default introduces overhead. The way we commonly decide the appropriate level of security to apply is to think about the amount of risk we are willing to take.
One of the commonly used concepts in security is defence in depth. The key underlying assumption of this concept is that at different areas or layers of the system we need to ensure there is adequate protection because there is no guarantee the previous layer is impenetrable. To secure an enterprise, we need to take a holistic approach that covers people, processes, policies and technology. This article covers aspects of security technology showing that security in the Enterprise require more than just a firewall which is the first line of defence. The following diagram illustrates the key areas of security within an Enterprise.
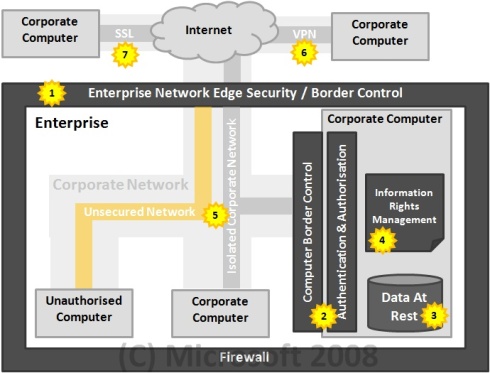
Let us take a tour through this diagram through the labelled numbers:
1. The most common mechanism to secure the enterprise is to install a perimeter firewall. This is useful in preventing unauthorised users from outside the corporate network from getting into the enterprise network. This is the first line of defence.
2. Most modern computers would have a firewall installed and also have a mechanism for users to be authenticated and authorised to use the computer. Authentication is about verifying the user identity. Authorisation is about ensuring the authority to perform a certain action or task. This is the second line of defence.
3. Most organisations would probably have no further protection mechanisms beyond the two described above. The data that resides in the computers and laptops are often left unprotected. Data at rest is a big issue with laptop computers, even though a data thief may not be able to access the laptop by trying to login through the operating system, there is nothing stopping them from taking the hard drive out and plugging it into another system and use that to access the information. One of the built in feature of the new Windows Vista operating system is a technology called BitLocker, which enables the entire hard drive to be encrypted, preventing data thief from getting access to any information on the hard drive. This technology can also be used to secure removable storage devices.
4. Information Rights Management (IRM) provides the ability to restrict information flow. This technology enforces information security policies and helps reduce the unauthorised re-distribution of information. This is an area where Microsoft is recognised as a leader in vision and implementation by Gartner.
5. The corporate network (outside the data centre) is normally left unprotected because it is usually supplemented with physical security, only authorised person can enter the office building. However it is common for business partners to enter our offices and join the network as guests. When they plug into the corporate network, how do you know their computer is free from viruses or malware? The technology exists with Microsoft Windows Servers to provide network isolation allowing only authorised corporate computers to communicate with each other. This means a virus or malware would not be able to communicate with authorised corporate computers, significantly reducing the chance for it to infect. The technology also provides the capability to only allow authorised corporate computers with the correct set of software installed to connect (E.g having Antivirus software with the latest update)
6. For travelling corporate users, a common mechanism to connect back to the company network is via a Virtual Private Network that allows secured communication over the Internet. However, some public places may block the VPN connection so the user would not be able to connect through.
7. Another mechanism to access corporate information and resources is through an application gateway. This allows browser based Intranet application to be accessed securely from the Internet and it also allows the types of information and functionalities that can be accessed by users when they are not connected directly in the internal network. Microsoft has recently launched a product that specifically handles this capability called the Microsoft Internet Application Gateway (IAG). This allows your Intranet applications to be accessed securely from the Intranet. It also allows the administrator to determine which specific functionalities and information is allowed to be viewed outside the corporate network without having to modify the application code.
Microsoft takes security seriously and embarked on a vigorous focus on security back in 2002 under the Trustworthy computing initiative introduced by Bill Gates. This initiative focuses on 3 key pillars: Technology Investments, Prescriptive Guidance and Industry Partnership. Technology investment focuses on the way Microsoft design and built software. Prescriptive guidance focuses on ensuring our customers and partners have access to education and training and providing the technology to easily access the latest security patches. Industry partnership focuses on ensuring we cooperate with other vendors to ensure our products work together seamlessly and securely. To learn more about this initiative please visit https://www.microsoft.com/security
Microsoft, EMC & CISCO recently released an announcement on SISA (Secure Information Sharing Architecture) that will offer one of the most comprehensive, security-enhanced, commercial, multi-vendor, end-to-end information-sharing technology architectures for helping protect and share sensitive government information. https://www.sisaalliance.com/