Oderoor - all it's Kraked up to be?
Greetings from (sorta) sunny Melbourne, Australia! We’re the newest addition to Microsoft’s Security Research and Response global team. In arbitrary seating order we have: Jakub Kaminski, Scott Molenkamp, Hamish O’Dea, Heather Goudey, Raymond Roberts, David Wood, Chun Feng, Oleg Petrovsky, Hermineh Tchagatzbanian, Hil Gradascevic and Matt McCormack. In the same order we have: Skinny Latte w/ 1, Espresso, Skinny Latte w/1, Skinny Latte w/1, Latte w/1, Hot Chocolate, Latte, Cappuccino, Cappuccino and Latte. Try carrying all those coffees at once – it’s not easy.
After our inclusion of the Win32/Nuwar (alias Storm) family last September (https://blogs.technet.com/antimalware/archive/2007/09/20/storm-drain.aspx) and the dent we put in the Win32/Cutwail (alias Pandex) network in January this year, we thought we’d continue the anti-spam motif by targeting the Win32/Oderoor (ominously dubbed ‘Kraken’) network. Research shows botnets with cooler names are way scarier.
“Spam networks you say?” “Why spam networks?” – Oh, convenient question random person! Glad you asked! In our recently published Security Intelligence Report (https://www.microsoft.com/security/portal/sir.aspx *) it was found that around 96% of inbound messages to Exchange Hosted Services were blocked because they had spam on them. Spam all over them. The SIR also found that approximately 80% of all spam that (tries to) go through Hotmail is from a botnet of some sort. I know it’s hard to believe, but those are graphs and charts people. Graphs with bars. Bars of truth. Research shows that statistics never lie.
Since the bad guys aren’t paying for the hardware or bandwidth, they can send spam to their hearts content. All that’s needed is one in every few billion emails to fool someone into buying the pills (which don’t work by the way...) or giving up their bank account details (some nice man from Nigeria emailed them personally!) to make it a worthwhile industry.
In case you weren’t aware, the always interesting Joe Stewart over at SecureWorks recently published a list of the top spam botnets (https://secureworks.com/research/threats/topbotnets/). As is to be expected our old friends Nuwar and Cutwail were there, along with THE KRAKEN. Joe’s estimate was that the size of the network was around 185,000 nodes, and spewing around 9 billion emails per day. Research shows that 9 billion emails is, in fact, a large number of emails. There was some contention over at the Damballa (https://www.damballa.com ) camp, who thought the network was more like 400,000 nodes strong. Either way, that is a lot of infected machines.
Being the helpful lads they are, the guys over at DVlabs (https://dvlabs.tippingpoint.com/) thought they’d get to the bottom of the ‘Mystery of the Disappearing Botnet Nodes’ and take a peek at the network from the inside (https://dvlabs.tippingpoint.com/blog/2008/04/28/kraken-botnet-infiltration). Whilst this doesn’t really help us with the number estimate, they did manage to obtain 65,000 unique infected IP addresses, so now we only have to account for the other missing 125,000-335,000 nodes. With so many nodes around you’d figure people would be tripping over them all over the place. Sadly not. :(
When we first identified Oderoor as a distinct family back in September 2007, links to the bots were being spammed through IM and the files themselves were encrypted to the wazoo (well, they still are doing both of those things). It didn’t take long for us to get a hold of the situation, but for the most part vendor detection remained very low. For months afterwards, we were one of the few vendors to be detecting new variants as they came in (turns out we had got samples from as far back as May that year, however the encryption was fairly rudimentary). As is to be expected, the family shone brightly on our radar and was being considered for MSRT inclusion at around the time that Joe published his article. So it all worked out rather nicely :).
Finally, our perspective on the Win32/Oderoor botnet; what MSRT has found. The numbers tend to go up and down, so I’ve included the first week wrap-up. Extrapolating (since we know how these things tend to pan out), we can probably expect in the order of 300k distinct machines this month that were cleaned of Oderoor.
|
| ||
|
|
| |
|
|
|
|
|
|
|
|
So our size estimate is somewhere in the middle of the SecureWorks and Damballa numbers. Of course our numbers are not the definitive answer. Whilst we run on 500 million machines and can get a pretty good idea of what’s going on, there are still a lot of machines out there that aren’t running MSRT; possibly because they don’t have automatic updates turned on.**
Question: How do these numbers compare to ‘Storm’ in the first few days?
Answer: Pretty close :)
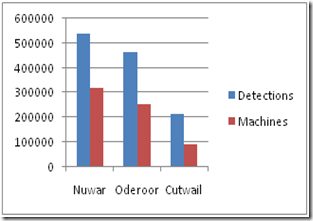
If we take a look at the first week removal results from Nuwar, we can get an idea of the relative size of the network. The Cutwail removal numbers are included to complete the spam trio. I’ve also included the graph because graphs are impressive.
| |||||||||||||||||||||||||
So it would appear the Win32/Oderoor network is slightly smaller that the Win32/Nuwar network – around the 80% mark. It should be noted that the Nuwar numbers are a lower-bound (due to the way we detect them), so in reality it is likely slightly smaller again. The detections per machine are higher for Nuwar because there was/is more components than Oderoor’s standalone executable. Speaking of the standalone executable - as tends to happen with these things, the Oderoor authors put out a new version the day after MSRT’s release: Backdoor:Win32/Oderoor.gen!E. We love these games of cat and mouse. Vendor detection is still a bit sketchy.
And how well did Oderoor fare with respect to the other families in MSRT this month? It made the top 4 which is very impressive considering the other types of malware that are being targeted:
| #1 | Win32/Zlob |
| #2 | Win32/Vundo |
| #3 | Win32/Renos |
| #4 | Win32/Oderoor |
| #5 | Win32/Busky |
| #6 | Win32/Rbot |
| #7 | Win32/Cutwail |
We’re in contact with the guys over in DVLabs who are going to take a look at their data to see if they noticed a drop from inside the network after MSRT’s release. We’re eagerly awaiting a post on their blog (https://dvlabs.tippingpoint.com/blog).
So was that Kraken botnet all it was Kraked up to be? I think yes. If we look at hype vs MSRT results, this botnet received a lot less hype than Nuwar’s network, but achieved pretty high infection numbers. If anything, it might even be understated. However hype is dependent on a botnet having something that makes it unique and interesting, such as Nuwar’s distributed peer-to-peer architecture. Encrypted communications over port 447 are ok but peer-to-peer is better I reckon. So perhaps it was just the right amount of hype. Juuuust right.
All Kraked out,
Matt McCormack
* - watch the Bret and Vinny show while you’re there. Vinny is our boss. He’s alright.
**- Seriously, running un-patched computers and being connected to the Internet is asking for trouble. It really is such a bad idea. It takes next to no time for an un-patched machine to get infected by some worm or another; this is one of the reasons we release MSRT to try and clean up the eco-system.
Comments
- Anonymous
January 01, 2003
PingBack from http://www.peper-it.nl/lijst-van-top-10-spam-botnets.html