Troubleshoot installation issues with the App Installer file
If you find any issues when installing an application from the App Installer file, this topic will provide some troubleshooting guidance that may help.
Prerequisites
To be able to sideload apps in Windows 10, the user device must satisfy the next requirements:
Windows 10:
- The certificate used to sign the package must be trusted by the device. See the Trusted certificates section below for more details.
- The Windows 10 version must support the
.appinstallerfile schema and the distribution protocol.
Windows 10 1909 and earlier:
- The device must be enabled for Developer Mode or Sideloading apps. See Enable your device for development to learn more.
Common issues
There are some common issues when sideloading an application for first time in the user machine. The next few sections describe the most frequent issues and their solutions.
Windows version
Each Windows 10 release improves on the sideloading experience, in the table below you will find which features are available in each major release. If you try to sideload an app using a method not supported in your version of Windows 10, you will get a deployment error.
| Version | Sideload Notes |
|---|---|
| Build 17134 (April 2018 Update, version 1803) | The .appinstaller file can be accessed over UNC/Share folders. Configurable update checks are also available. |
| Build 16299 (Fall Creators Update, version 1709) | Introduced the .appinstaller file to provide automatic updates to your app. This version only supports HTTP endpoints. Update checks are not configurable and happens each 24 hours. |
| Build 15063 (Creators Update, version 1703) | The App Installer app is able to download app dependencies (only in release mode) from the Store. |
| Build 14393 (Anniversary Update, version 1607) | Introduced the App Installer app to install .appx and .appxbundle files, .appinstaller file is not supported. |
| Build 10586 (November Update, version 1511) | Sideload is only available through PowerShell using the Add-AppxPackage command. |
| Build 10240 (Windows 10, version 1507) | Sideload is only available through PowerShell using the Add-AppxPackage command. |
Trusted certificates
App packages must be signed with a certificate that is trusted by the device. Certificates provided by common Certificate Authorities are trusted by default in the Windows operating system.
However, if the certificate used to sign an app package is not trusted, or is a locally-generated/self-signed certificate used during development, the app installer may report that the package is untrusted and will prevent it from being installed:
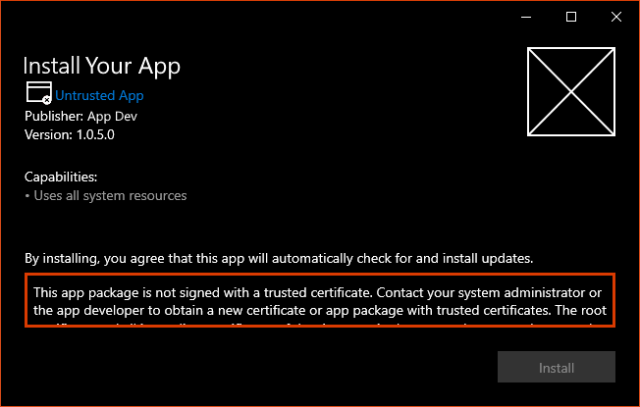
To solve this issue, a user with local administrator rights to the device must use the Computer Certificates tool to import the certificate into one of the following containers:
- Local Computer: Trusted People
- Local Computer: Trusted Root Authorities (not recommended)
Important
Do not import package signing certificates into the User Certificate store. The App Installer does not search User Certificates when verifying package identity.
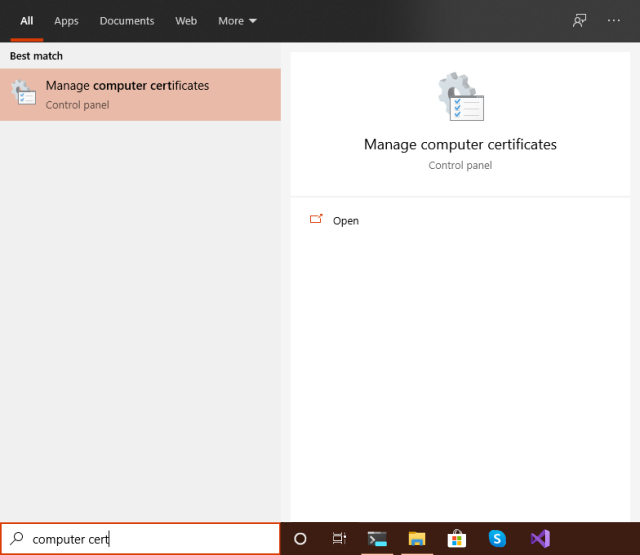
The Computer Certificates management tool can be easily found by searching from the Start Menu:
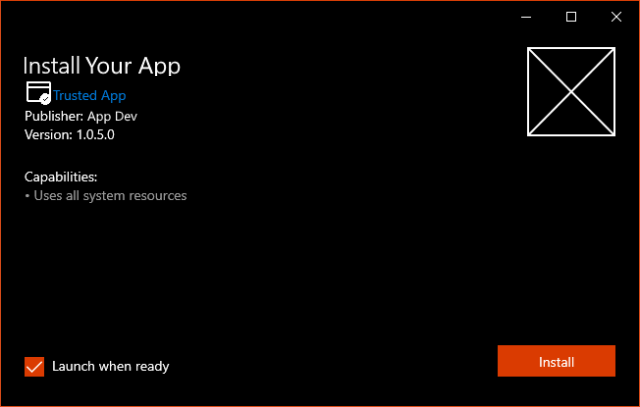
Once the signing certificate is successfully imported, re-running the app installer will show that the package is trusted and can be installed:
Dependencies not installed
Windows 10 applications can have framework dependencies based on the application platform used to generate the app. If you are using C# or VB, the app will require the .NET Runtime and .NET framework packages. C++ applications require the VCLibs.
Important
If the app package is built in Release mode configuration, the framework dependencies will be obtained from the Microsoft Store. However, if the app is built in Debug mode configuration, the dependencies will be obtained from the location specified in the .appinstaller file.
Files not accessible
When installing from an HTTP endpoint, it is important to verify that all required files are accessible. The easiest method to verify this is by following the links provided in the HTML page generated by Visual Studio. You must check these files:
- an
.appinstallerfile, found atAdditional Links > App Installer Fileon the Visual Studio generated page - an
.appx,.appxbundle,.misxormsixbundlefile, found atAdditional Links > Package Bundleon the Visual Studio generated page
Note
Depending on your configuration, there might be more than one .appx, .appxbundle, .misx or msixbundle file involved in your deployment. Ensure that all of them are accessible.
Files served with wrong MIME type
When installing from an HTTP endpoint, all files are required to be served with their correct MIME type in the Content-Type header by the webserver.
Files served without Content-Length header
When installing from an HTTP endpoint, all responses need to include a correct Content-Length header. This includes GET as well as HEAD requests. Ensure that all of them specify their Content-Length correctly. Failing to do so can lead to errors like App installation failed with error message: Appinstaller operation failed with error code 0x80072F76. Detail: Unknown error (0x80072f76) or others.
App installation failed with error message: The parameter is incorrect
Since vanity URLs are not supported at this time, when using the ms-appinstaller protocol, the source parameter MUST end in .appinstaller. It doesn't matter if you redirect to a file ending with .appinstaller. That will also fail in the same way. The only way to fix this is to make sure the original url ends with .appinstaller.
Isolate App Installer app issues
If the App Installer cannot install the app, these steps will help identify the installation issue.
Verify app package file installation
Download the app package file to a local folder and try to install it using the Add-AppxPackage PowerShell command.
Download the
.appinstallerfile to a local folder and try to install it using theAdd-AppxPackage -AppinstallerPowerShell command.
App Installer event logs
The app deployment infrastructure emits logs that are often useful for debugging installation issues via the Windows Event Viewer: Application and Services Logs -> Microsoft -> Windows -> AppxDeployment-Server. Additional log files are created in this folder: %LocalAppData%\Packages\Microsoft.DesktopAppInstaller_8wekyb3d8bbwe\LocalState\DiagOutputDir