Beveiligingsproblemen met gedeeld geheugen van NDIS Virtual Machine (VM)
In dit onderwerp worden de mogelijke beveiligingsproblemen besproken die verband houden met het toewijzen van gedeeld geheugen van een virtuele machine (VM) voor ontvangbuffers van VM-wachtrijen (VMQ). Het onderwerp bevat de volgende secties:
Overzicht van de beveiligingsproblemen met gedeeld geheugen in VM
hoe Windows Server 2012 en latere versies het beveiligingsprobleem oplossen
Opmerking In Hyper-V wordt een onderliggende partitie ook wel een VM genoemd.
Overzicht van de beveiligingskwesties met gedeeld geheugen tussen Virtuele Machines
VM's zijn geen vertrouwde software-entiteiten. Dat wil gezegd, een kwaadwillende VM mag geen invloed hebben op andere VM's of het beheerbesturingssysteem dat wordt uitgevoerd in de Hyper-V bovenliggende partitie. In deze sectie vindt u achtergrondinformatie en vereisten om ervoor te zorgen dat schrijvers van stuurprogramma's inzicht hebben in beveiligingsproblemen met VMQ en vereisten voor gedeeld geheugen. Zie het onderwerp Toewijzing van gedeelde geheugenresources in de sectie VMQ-stuurprogramma's schrijven voor meer informatie over gedeeld geheugen.
In de gevirtualiseerde omgeving kan het gedeelde geheugen van de virtuele machine worden bekeken of gewijzigd. Het weergeven of wijzigen van gegevens die aan andere VM's zijn gekoppeld, is echter niet toegestaan. VM's hebben ook geen toegang tot de adresruimte van het beheerbesturingssysteem.
Het headergedeelte van de ontvangen pakketten moet worden beveiligd. Een virtuele machine mag niet het gedrag van de Hyper-V uitbreidbare switch in een virtuele netwerkserviceprovider (VSP) beïnvloeden. Daarom moet VLAN (virtual LAN) filteren plaatsvinden voordat de netwerkadapter DMA gebruikt om de gegevens over te dragen naar het gedeelde geheugen van de VM. Ook het leren van MAC-adressen (Media Access Control) van de switch kan niet worden beïnvloed.
Als de Hyper-V uitbreidbare switchpoort die is verbonden met een virtuele machine een gekoppelde VLAN-id heeft, moet de hostcomputer ervoor zorgen dat het doel-MAC-adres en de VLAN-id van het binnenkomende frame overeenkomen met de respectieve kenmerken van de poort voordat de host het pakket doorstuurt naar de virtuele netwerkadapter van de virtuele machine. Als de VLAN-id van het frame niet overeenkomt met de VLAN-id van de poort, wordt het pakket verwijderd. Wanneer de ontvangstbuffers voor een virtuele netwerkadapter worden toegewezen vanuit het hostgeheugen, kan de host de VLAN-id controleren en het frame indien nodig verwijderen voordat de inhoud van het frame zichtbaar is voor de doel-VM. Als het frame niet naar de adresruimte van een virtuele machine wordt gekopieerd, kan het niet worden geopend door die VM.
Wanneer VMQ echter is geconfigureerd voor gebruik van gedeeld geheugen, gebruikt de netwerkadapter DMA om binnenkomende frames rechtstreeks over te dragen naar de VM-adresruimte. Deze overdracht introduceert een beveiligingsprobleem waarbij een VIRTUELE machine de inhoud van de ontvangen frames kan onderzoeken zonder te wachten tot de uitbreidbare switch de vereiste VLAN-filtering toepast.
Hoe Windows Server 2008 R2 het beveiligingsprobleem verhelpt
In Windows Server 2008 R2, voordat de VSP een VM-wachtrij configureert voor het gebruik van gedeeld geheugen dat is toegewezen vanuit de adresruimte van de virtuele machine, wordt de volgende filtertest voor de wachtrij gebruikt.
(MAC address == x) && (VLAN identifier == n)
Als de hardware van de netwerkadapter deze test kan ondersteunen vóór de DMA-overdracht naar de ontvangstbuffers, kan de netwerkadapter frames met ongeldige VLAN-id's verwijderen of naar de standaardwachtrij verzenden, zodat ze kunnen worden gefilterd door de uitbreidbare switch. Als het minipoortstuurprogramma slaagt in een aanvraag om een filter in te stellen met deze test in een wachtrij, kan de uitbreidbare switch gebruikmaken van gedeeld VM-geheugen voor die wachtrij. Als de netwerkadapterhardware de frames echter niet kan filteren op basis van zowel het doel-MAC-adres als de VLAN-id, maakt de uitbreidbare switch gebruik van gedeeld hostgeheugen voor die wachtrij.
De uitbreidbare switch inspecteert het MAC-bronadres van ontvangen frames om de routeringsinformatie voor het verzenden van frames te configureren, dat wil gezegd, het is vergelijkbaar met een fysieke leerswitch. Het is mogelijk om firewallfilterstuurprogramma's in de hoststack te installeren; Bijvoorbeeld boven het minipoortstuurprogramma voor de netwerkadapterhardware en onder het uitbreidbare switchstuurprogramma. Firewallfilterstuurprogramma's hebben toegang tot gegevens in een ontvangen frame vóór de uitbreidbare switch. Als de volledige ontvangstbuffer voor elk frame wordt toegewezen vanuit de VM-adresruimte, heeft een kwaadwillende VM toegang tot onderdelen van het frame die worden onderzocht door een filterstuurprogramma of de uitbreidbare switch die in de host wordt uitgevoerd.
Om dit beveiligingsprobleem op te lossen, moet de netwerkadapter bij het gebruik van gedeeld VM-geheugen voor een VM-wachtrij het pakket opsplitsen op een byte-offset die ten minste de grootte van de lookahead is. Dit is een vooraf vastgestelde vaste waarde. Eventuele lookaheadgegevens - dat wil zeggen gegevens die zich na de byte-offset voor de lookaheadgrootte bevinden - moeten met DMA worden overgebracht naar gedeeld geheugen dat is toegewezen voor lookaheadgegevens. De post-lookaheadgegevens (de rest van de framepayload) moeten met DMA worden overgebracht naar gedeeld geheugen dat is toegewezen voor de post-lookaheadgegevens.
In de volgende afbeelding ziet u de relaties voor de netwerkgegevensstructuren wanneer de binnenkomende gegevens worden gesplitst in lookahead- en post-lookahead gedeelde geheugenbuffers.
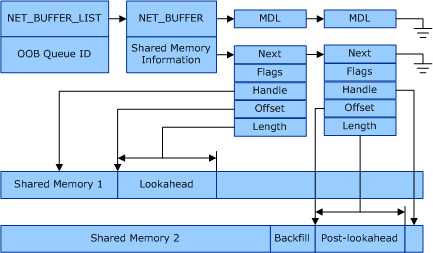
De overzichtsvereisten voor gedeeld VMQ-geheugen zijn als volgt:
Een netwerkadapter kan een ontvangen frame splitsen op een netwerkheadergrens die groter is dan de grootte van de lookahead. Wanneer dit echter wordt aangevraagd door NDIS, en zonder uitzondering, moeten alle frames die worden ontvangen en toegewezen aan een VMQ worden gesplitst op of buiten de grens van de lookaheadgrootte die NDIS aanvraagt.
De lookaheadgegevens moeten worden overgedragen met DMA naar gedeeld geheugen dat wordt toegewezen door de miniport driver. Het minipoortstuurprogramma moet opgeven in de toewijzingsoproep dat het geheugen wordt gebruikt voor lookaheadgegevens.
De post-lookaheadgegevens moeten worden overgedragen met DMA naar gedeeld geheugen dat wordt toegewezen door het minipoortstuurprogramma. Het miniport-stuurprogramma moet in de toewijzingsaanroep opgeven dat het geheugen wordt gebruikt voor post-lookaheadgegevens.
Minipoortstuurprogramma's mogen niet afhankelijk zijn van welke adresruimte NDIS zal gebruiken om de toewijzingsaanvraag voor gedeeld geheugen te voltooien. Dat wil gezegd: de adresruimte voor gedeeld geheugen voor lookahead- of post-lookahead-gegevens is specifiek voor implementatie. In veel gevallen kan NDIS of de uitbreidbare switch voldoen aan alle aanvragen, inclusief aanvragen voor gebruik na lookahead, vanuit de adresruimte van het hostgeheugen.
De volgorde waarin frames worden ontvangen op een VMQ-ontvangstwachtrij, moet behouden blijven wanneer de frames in die wachtrij worden aangegeven op de stuurprogrammastack.
De netwerkadapter moet voldoende backfill-geheugenruimte toewijzen in elke post-lookaheadbuffer. Met deze toewijzing kunnen de lookaheadgegevens naar het achtervulgedeelte van de buffer na lookahead worden gekopieerd, en kan het frame in een aaneengesloten buffer aan de virtuele machine worden geleverd.
Als er geen mechanisme in hardware is om te voldoen aan deze vereisten voor gedeeld VMQ-geheugen, kan de hardware die DMA voor spreidingsvergaap aan de ontvangstzijde ondersteunt, dezelfde resultaten bereiken door twee ontvangstbuffers toe te wijzen voor elk ontvangen frame. In dit geval is de grootte van de eerste buffer beperkt tot de aangevraagde lookaheadgrootte.
Als de netwerkadapter op geen enkele manier kan voldoen aan deze vereisten voor gedeeld VMQ-geheugen, wijst de VSP geheugen toe voor de VMQ-ontvangbuffers van de hostadresruimte en kopieert de ontvangen pakketten van de netwerkadapter-buffers naar de VM-adresruimte.
Hoe Windows Server 2012 en latere versies het beveiligingsprobleem oplossen
Vanaf Windows Server 2012 wijst de VSP geen gedeeld geheugen meer toe van de VM voor de VMQ-ontvangstbuffers. In plaats daarvan wijst de VSP geheugen toe voor de VMQ-ontvangstbuffers van de hostadresruimte en kopieert vervolgens de ontvangen pakketten van de ontvangstbuffers van de netwerkadapter naar de VM-adresruimte.
De volgende punten zijn van toepassing op VMQ miniportstuurprogramma's die worden uitgevoerd op Windows Server 2012 en latere versies van Windows:
Voor NDIS 6.20 VMQ-minipoortstuurprogramma's is geen wijziging vereist. Wanneer de VSP echter een VM-wachtrij toewijst door een OID-methodeaanvraag (object-id) van OID_RECEIVE_FILTER_ALLOCATE_QUEUEuit te geven, wordt de LookaheadSize- lid van de NDIS_RECEIVE_QUEUE_PARAMETERS-structuur ingesteld op nul. Dit dwingt een miniportdriver om het pakket niet te splitsen in pre-lookahead- en post-lookahead-buffers.
Vanaf NDIS 6.30 mogen VMQ-minipoortstuurprogramma's geen ondersteuning adverteren voor het splitsen van pakketgegevens in pre-lookahead- en post-lookaheadbuffers. Wanneer een minipoortstuurprogramma de VMQ-mogelijkheden registreert, moet het deze regels volgen wanneer de NDIS_RECEIVE_FILTER_CAPABILITIES structuur wordt geïnitialiseerd:
Het minipoortstuurprogramma mag de NDIS_RECEIVE_FILTER_LOOKAHEAD_SPLIT_SUPPORTED vlag niet instellen in het vlaggen veld.
Het minipoortstuurprogramma moet de leden MinLookaheadSplitSize en MaxLookaheadSplitSize op nul instellen.
Zie Bepalen van de VMQ-mogelijkheden van een netwerkadaptervoor meer informatie over het registreren van VMQ-mogelijkheden.