Windows-container netwerken
Van toepassing op: Windows Server 2025, Windows Server 2022, Windows Server 2019, Windows Server 2016
Belangrijk
Raadpleeg Docker Container Networking- voor algemene Docker-netwerkopdrachten, -opties en -syntaxis. Met uitzondering van gevallen die worden beschreven in niet-ondersteunde functies en netwerkopties, worden alle Docker-netwerkopdrachten ondersteund in Windows met dezelfde syntaxis als in Linux. De Windows- en Linux-netwerkstacks zijn echter verschillend en daarom zult u merken dat sommige Linux-netwerkopdrachten (bijvoorbeeld ifconfig) niet worden ondersteund in Windows.
Basisnetwerkarchitectuur
In dit onderwerp vindt u een overzicht van hoe Docker hostnetwerken in Windows maakt en beheert. Windows-containers werken op dezelfde manier als virtuele machines met betrekking tot netwerken. Elke container heeft een virtuele netwerkadapter (vNIC) die is verbonden met een Hyper-V virtuele switch (vSwitch). Windows ondersteunt vijf verschillende netwerkstuurprogramma's of -modi die kunnen worden gemaakt via Docker: nat, overlay-, transparante, l2bridgeen l2tunnel. Afhankelijk van uw fysieke netwerkinfrastructuur en netwerkvereisten met één versus meerdere hosts, moet u het netwerkstuurprogramma kiezen dat het beste bij uw behoeften past.
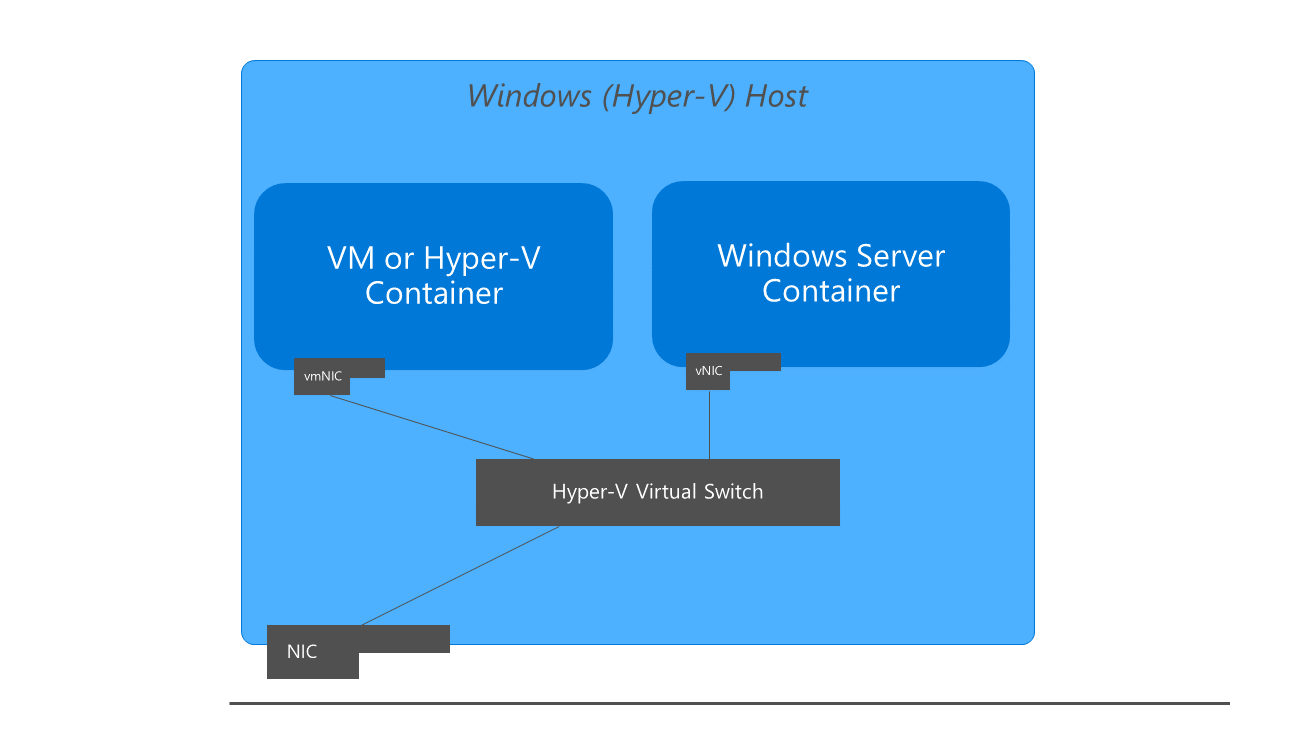
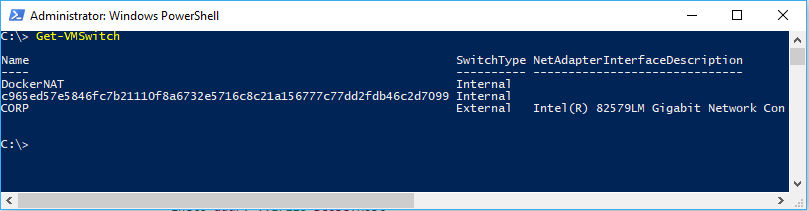
De eerste keer dat Docker Engine wordt uitgevoerd, wordt er een standaard NAT-netwerk gemaakt, nat, dat gebruikmaakt van een interne vSwitch en een Windows-onderdeel met de naam WinNAT. Als er al bestaande externe vSwitches zijn op de host die zijn gemaakt via PowerShell of Hyper-V Manager, zijn ze ook beschikbaar voor Docker met behulp van het transparante netwerkstuurprogramma en kunt u zien wanneer u de docker network ls opdracht uitvoert.
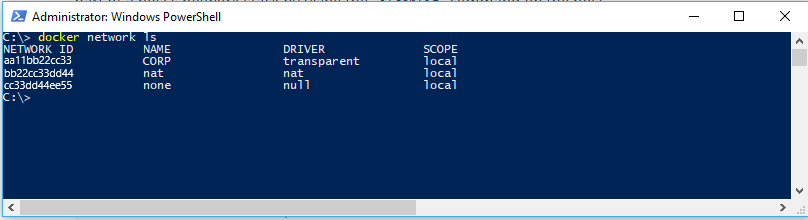
- Een interne vSwitch is er een die niet rechtstreeks is verbonden met een netwerkadapter op de containerhost.
- Een externe vSwitch is een die rechtstreeks is verbonden met een netwerkadapter op de containerhost.
Het nat-netwerk is het standaardnetwerk voor containers die worden uitgevoerd in Windows. Containers die worden uitgevoerd in Windows zonder vlaggen of argumenten om specifieke netwerkconfiguraties te implementeren, worden gekoppeld aan het standaard nat-netwerk en automatisch een IP-adres toegewezen uit het interne voorvoegsel-IP-bereik van het nat-netwerk. Het standaard interne IP-voorvoegsel dat wordt gebruikt voor NAT is 172.16.0.0/16.
Containernetwerkbeheer met hostnetwerkservice
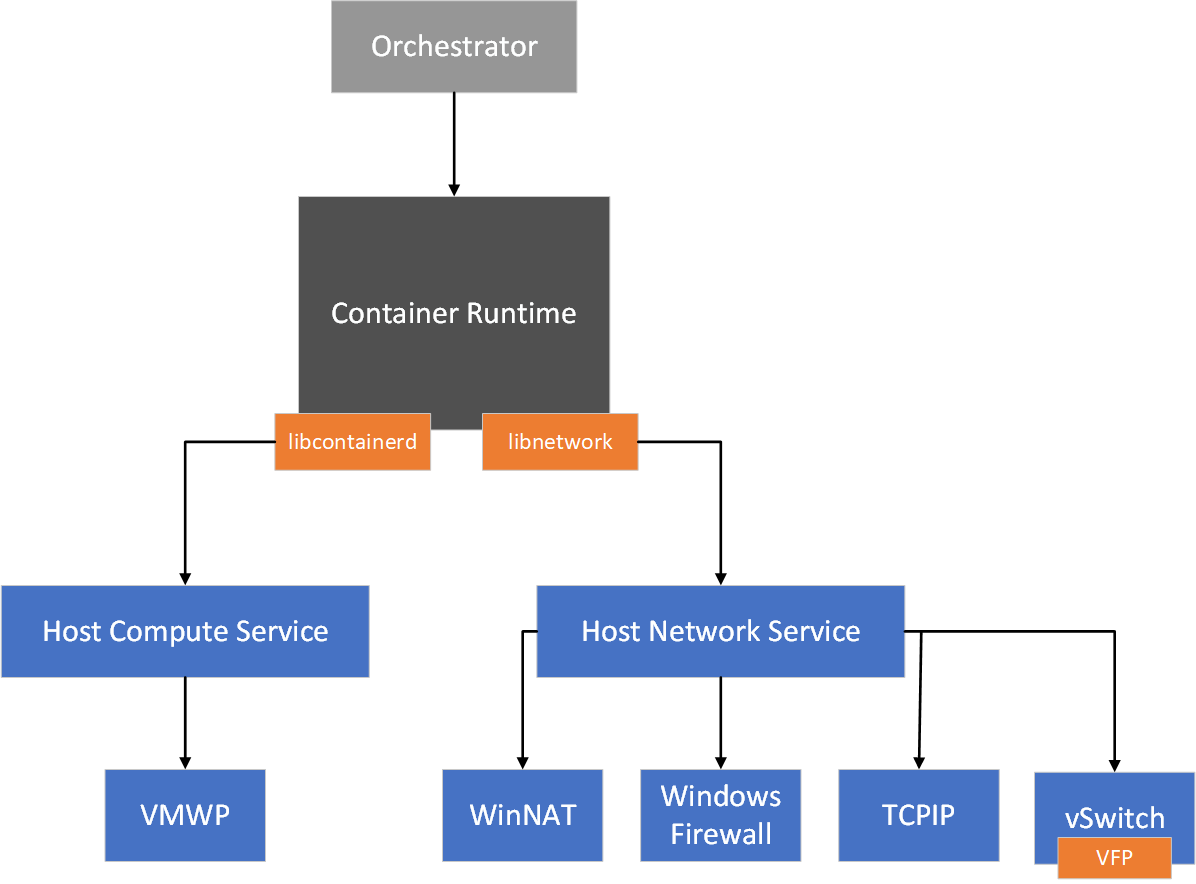
De Host Networking Service (HNS) en de Host Compute Service (HCS) werken samen om containers te maken en eindpunten aan een netwerk te koppelen. U kunt met HNS communiceren via de HNS PowerShell Helper-module.
Netwerk maken
- HNS maakt een Hyper-V virtuele switch voor elk netwerk
- HNS maakt NAT- en IP-adresgroepen zoals vereist
Eindpunt maken
- HNS maakt netwerknaamruimte per containereindpunt
- HNS/HCS plaatst v(m)NIC in netwerknaamruimte
- HNS creëert poorten (vSwitch)
- HNS wijst IP-adres, DNS-gegevens, routes, enzovoort toe (afhankelijk van de netwerkmodus) aan het eindpunt
Beleid maken
- Voor het standaardnetwerk voor network address translation (NAT) maakt HNS de WinNAT-poortdoorgeefregels en -toewijzingen met de bijbehorende toestaan-regels van de Windows Firewall.
- Voor alle andere netwerken maakt HNS gebruik van het Virtual Filtering Platform (VFP) voor het maken van beleid, waaronder taakverdeling, ACL's en inkapseling. Zie HCN-service-API (Host Compute Network) voor VM's en containersvoor meer informatie over HNS-API's en het schema.
Niet-ondersteunde functies en netwerkopties
De volgende netwerkopties zijn momenteel NIET ondersteund in Windows:
- Vanaf Windows Server 2022 hebben Windows-containers de volgende ondersteuning voor IPv6-netwerken:
- Containers die zijn gekoppeld aan l2bridge-netwerken ondersteunen de IPv6-stack.
- Containers die zijn gekoppeld aan transparante netwerken ondersteunen communicatie met behulp van IPv6 met zelf toegewezen IP-adressen, maar bieden geen ondersteuning voor door HNS geleverde IP-adrestoewijzing en andere netwerkservices, zoals Taakverdeling en ACL's.
- Windows-containers die zijn gekoppeld aan NAT- en overlaynetwerken bieden geen ondersteuning voor communicatie via de IPv6-stack.
- Versleutelde containercommunicatie via IPsec.
- hostmodus netwerken.
- Netwerken op gevirtualiseerde Azure-infrastructuur via het transparante netwerkstuurprogramma.
| Bevelen | Niet-ondersteunde optie |
|---|---|
docker run |
--ip6, --dns-option |
docker network create |
--aux-address, --internal, --ip-range, --ipam-driver, --ipam-opt, --ipv6, --opt encrypted |