Privé-eindpuntverbindingen toevoegen
Azure Database for PostgreSQL - Flexible Server is een Azure Private Link-service. Dit betekent dat u privé-eindpunten kunt maken, zodat uw clienttoepassingen privé en veilig verbinding kunnen maken met uw flexibele Azure Database for PostgreSQL-server.
Een privé-eindpunt voor uw flexibele Azure Database for PostgreSQL-server is een netwerkinterface die u kunt injecteren in een subnet van een virtueel Azure-netwerk. Elke host of service die netwerkverkeer naar dat subnet kan routeren, kan communiceren met uw flexibele server, zodat het netwerkverkeer niet via internet hoeft te gaan. Al het verkeer wordt privé verzonden met behulp van Microsoft backbone.
Zie voor meer informatie over Azure Private Link en Azure Private Endpoint veelgestelde vragen over Azure Private Link.
Selecteer uw flexibele Azure Database for PostgreSQL-server.
Selecteer Overzicht in het resourcemenu.
De status van de server moet beschikbaar zijn, zodat de menuoptie Netwerken moet worden ingeschakeld.
Als de status van de server niet beschikbaar is, is de optie Netwerken uitgeschakeld.
Notitie
Elke poging om de netwerkinstellingen van een server te configureren waarvan de status niet beschikbaar is, mislukt met een fout.
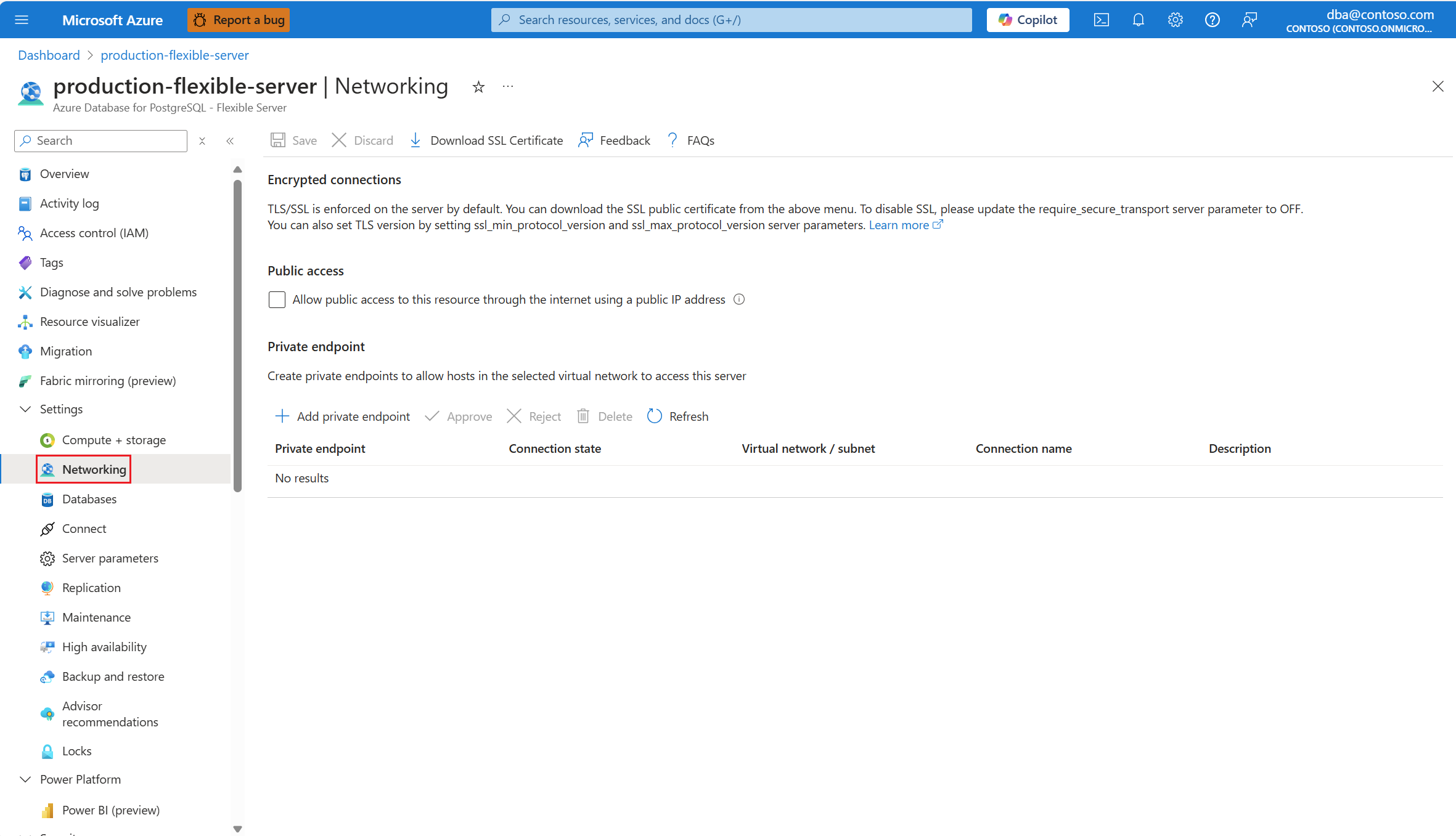
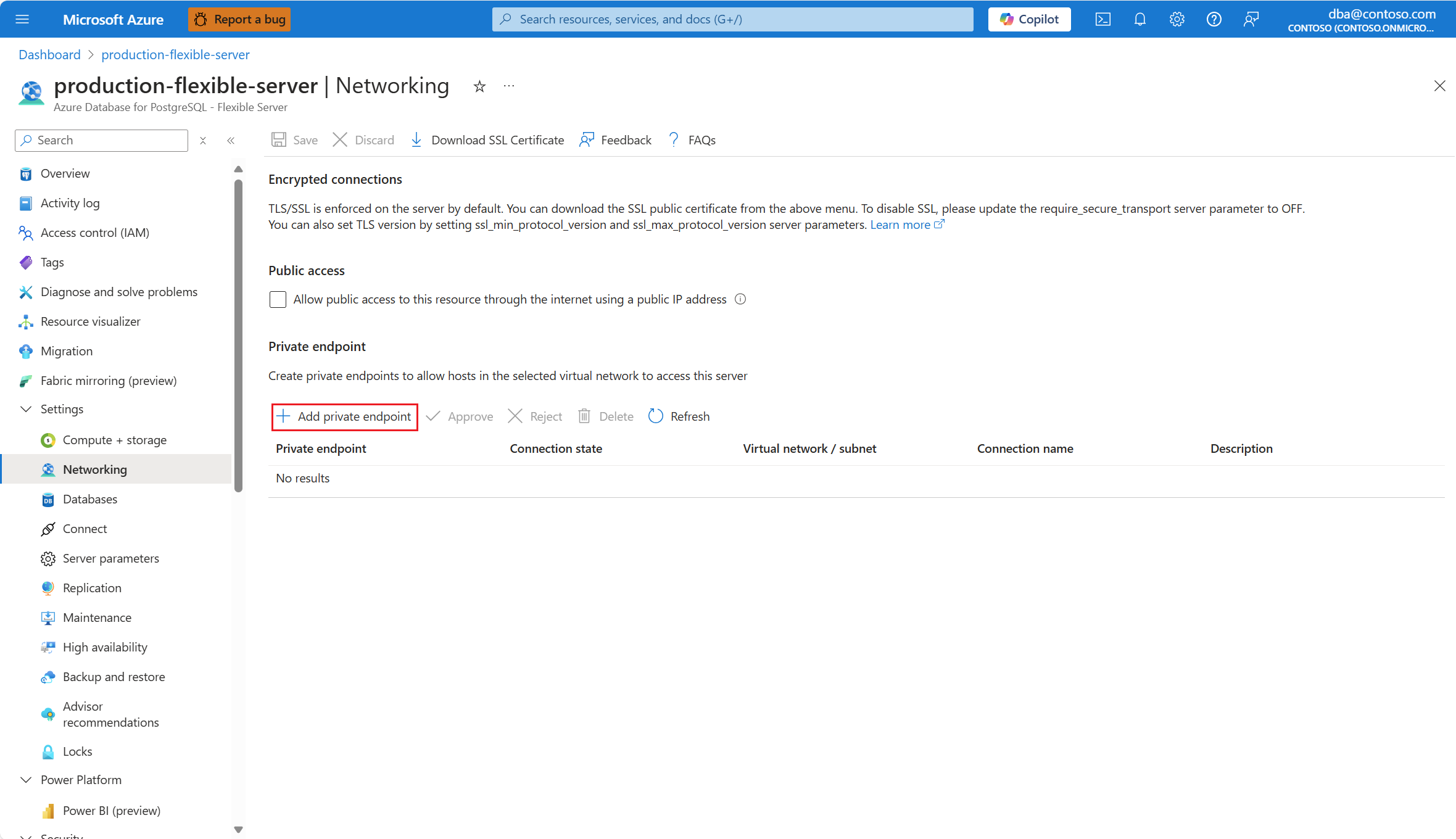
Selecteer Netwerken in het resourcemenu.
Als u over de vereiste machtigingen beschikt om een privé-eindpunt te implementeren, kunt u dit maken door privé-eindpunt toevoegen te selecteren.
Notitie
Zie Azure RBAC-machtigingen voor Azure Private Link voor meer informatie over de benodigde machtigingen voor het implementeren van een privé-eindpunt.
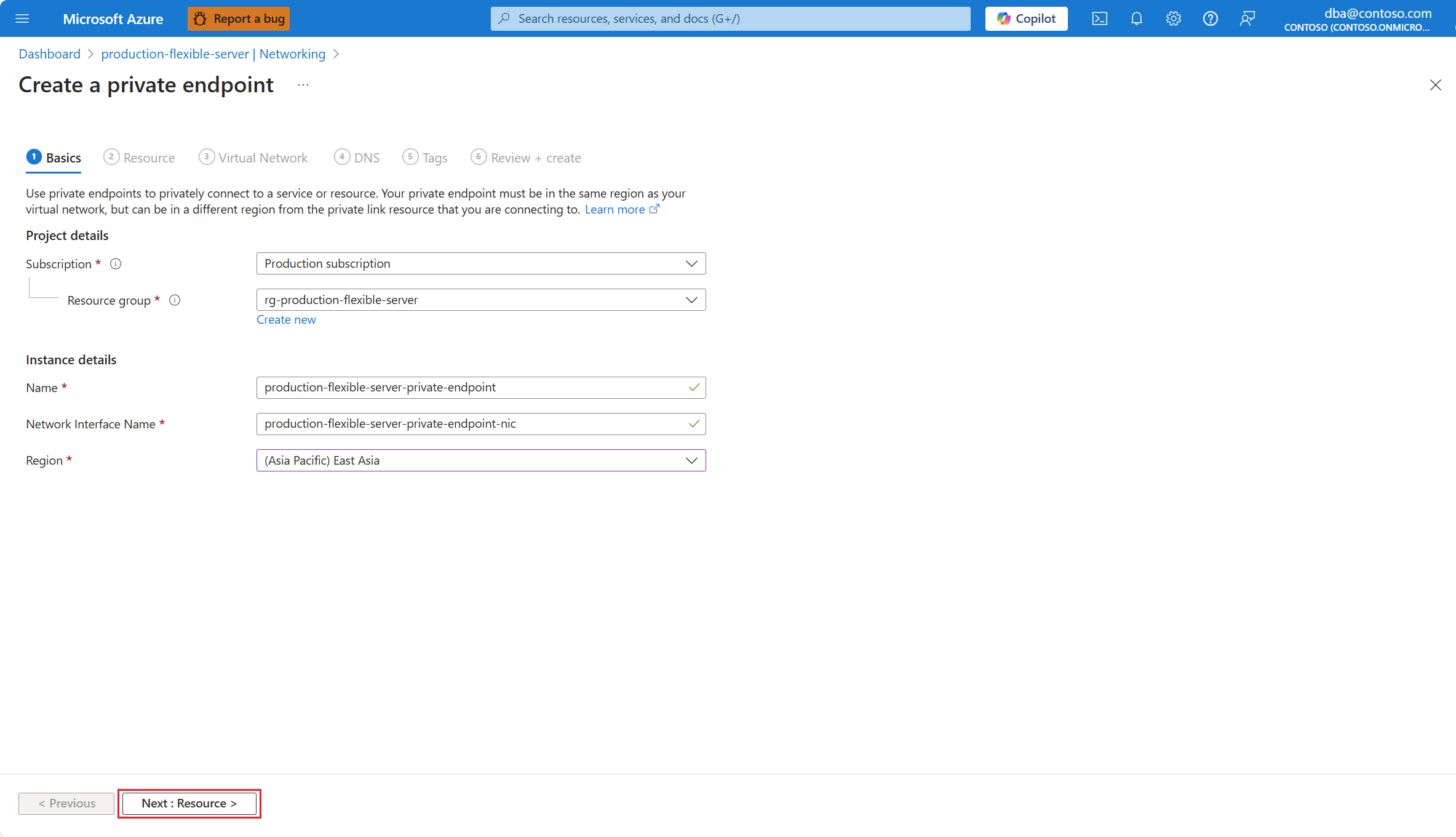
Vul op de pagina Basisinformatie alle vereiste gegevens in. Selecteer vervolgens Volgende: Resource.
Gebruik de volgende tabel om inzicht te krijgen in de betekenis van de verschillende velden die beschikbaar zijn op de pagina Basisbeginselen en als richtlijnen voor het vullen van de pagina:
Instelling Voorgestelde waarde Beschrijving Abonnement Selecteer de naam van het abonnement waarin u de resource wilt maken. Hiermee wordt automatisch het abonnement geselecteerd waarin uw server is geïmplementeerd. Een abonnement is een overeenkomst met Microsoft voor het gebruik van een of meer Microsoft-cloudplatforms of -services, waarvoor kosten worden berekend op basis van een licentiekosten per gebruiker of op resourceverbruik in de cloud. Als u meerdere abonnementen hebt, kiest u het abonnement waarin u wilt worden gefactureerd voor de resource. Resourcegroep De resourcegroep in het geselecteerde abonnement waarin u het privé-eindpunt wilt maken. Dit kan een bestaande resourcegroep zijn of u kunt nieuwe maken selecteren en een naam opgeven in dat abonnement dat uniek is onder de bestaande resourcegroepnamen. Hiermee wordt automatisch de resourcegroep geselecteerd waarin uw server is geïmplementeerd. Een resourcegroep is een container met gerelateerde resources voor een Azure-oplossing. De resourcegroep kan alle resources voor de oplossing bevatten of enkel de resources die u als groep wilt beheren. U bepaalt hoe resources worden toegewezen aan resourcegroepen op basis van wat voor uw organisatie het meest zinvol is. Over het algemeen voegt u resources toe die dezelfde levenscyclus delen met dezelfde resourcegroep, zodat u ze eenvoudig als groep kunt implementeren, bijwerken en verwijderen. Naam De naam die u wilt toewijzen aan het privé-eindpunt. Een unieke naam waarmee het privé-eindpunt wordt geïdentificeerd waarmee u verbinding kunt maken met uw flexibele Azure Database for PostgreSQL-server. Netwerkinterfacenaam De naam die u wilt toewijzen aan de netwerkinterface die is gekoppeld aan het privé-eindpunt. Een unieke naam die de netwerkinterface identificeert die is gekoppeld aan het privé-eindpunt. Regio De naam van een van de regio's waarin u privé-eindpunten kunt maken voor Azure Database for PostgreSQL - Flexible Server. De regio die u selecteert, moet overeenkomen met die van het virtuele netwerk waarin u het privé-eindpunt wilt implementeren. Vul op de pagina Resource alle vereiste gegevens in. Selecteer vervolgens Volgende: Virtueel netwerk.
Gebruik de volgende tabel om inzicht te krijgen in de betekenis van de verschillende velden die beschikbaar zijn op de pagina Resource en als richtlijnen voor het vullen van de pagina:
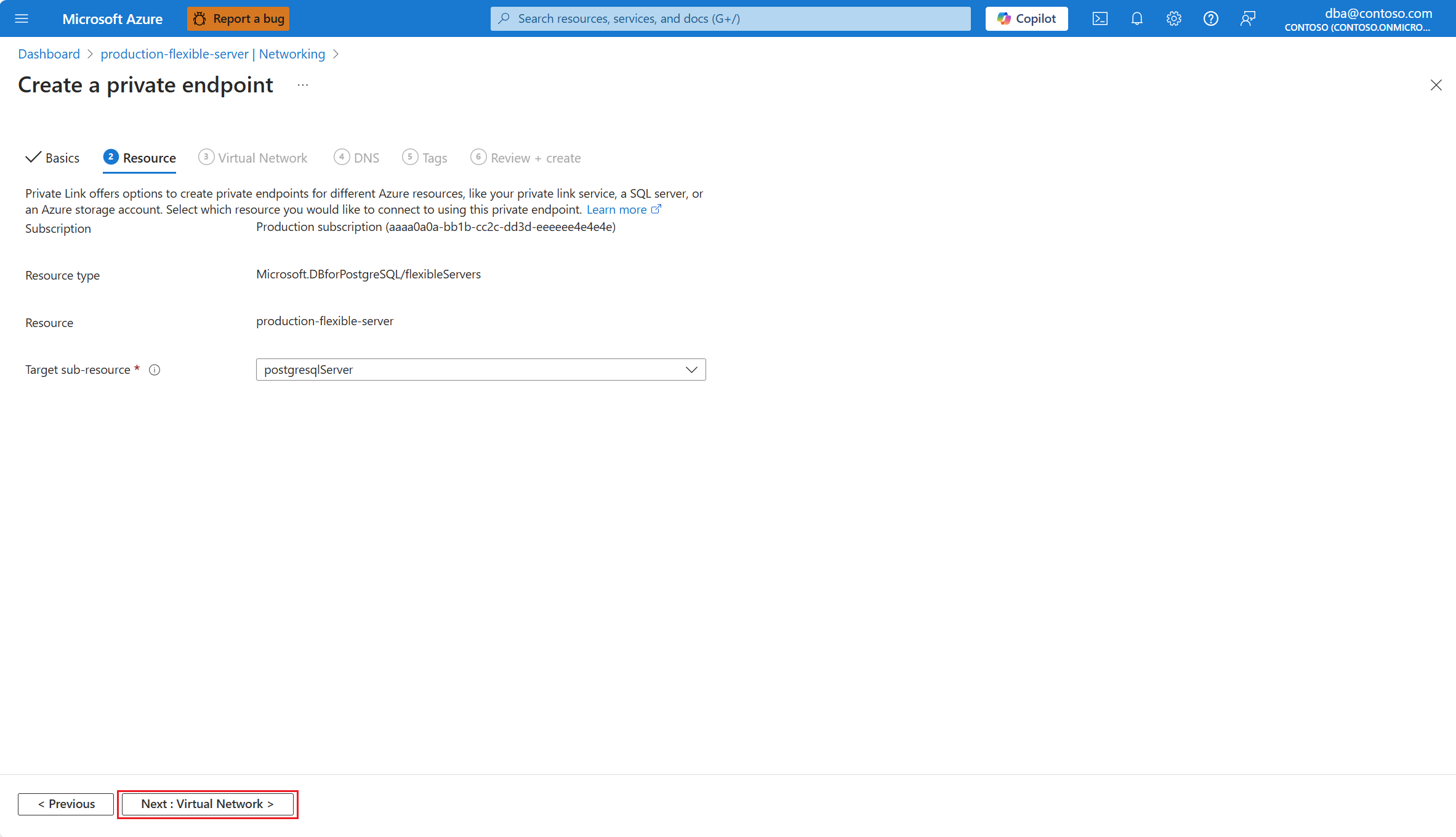
Instelling Voorgestelde waarde Beschrijving Resourcetype Automatisch ingesteld op Microsoft.DBforPostgreSQL/flexibleServersDeze waarde wordt automatisch voor u gekozen en komt overeen met het type resource dat een flexibele Azure Database for PostgreSQL-server is, in de ogen van Azure Private Link. Resource Automatisch ingesteld op de naam van de flexibele Azure Database for PostgreSQL-server waarvoor u het privé-eindpunt maakt. De naam van de resource waarmee het privé-eindpunt verbinding maakt. Doelsubresource Automatisch ingesteld op postgresqlServer.Het type subresource voor de geselecteerde resource, waartoe uw privé-eindpunt toegang heeft. Vul op de pagina Virtueel netwerk alle vereiste gegevens in. Selecteer vervolgens Volgende: DNS.
Gebruik de volgende tabel om inzicht te krijgen in de betekenis van de verschillende velden die beschikbaar zijn op de pagina Virtual Network en als richtlijnen voor het vullen van de pagina:
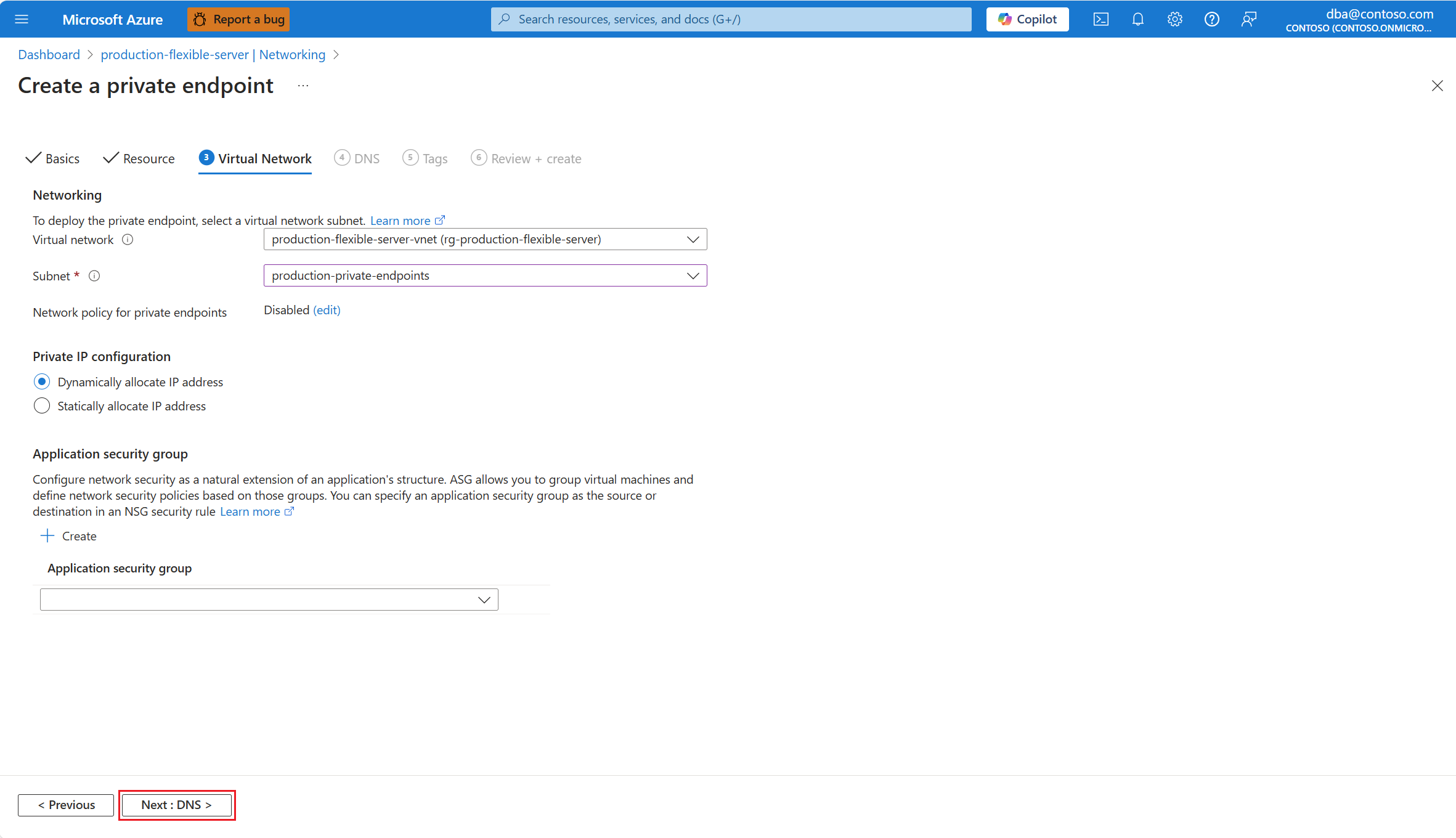
Instelling Voorgestelde waarde Beschrijving Virtueel netwerk Automatisch ingesteld op het eerste virtuele netwerk (gesorteerd in alfabetische volgorde) dat beschikbaar is in het abonnement en de geselecteerde regio. Alleen virtuele netwerken waarvoor u machtigingen hebt, worden weergegeven in het momenteel geselecteerde abonnement en de geselecteerde regio. Subnet Automatisch ingesteld op de naam van de flexibele Azure Database for PostgreSQL-server waarvoor u het privé-eindpunt maakt. Alleen subnetten in het geselecteerde virtuele netwerk worden vermeld. Netwerkbeleid voor privé-eindpunten Standaard zijn netwerkbeleidsregels uitgeschakeld voor een subnet in een virtueel netwerk. U kunt netwerkbeleid alleen inschakelen voor netwerkbeveiligingsgroepen, alleen voor door de gebruiker gedefinieerde routes of voor beide. Als u netwerkbeleid wilt gebruiken, zoals door de gebruiker gedefinieerde routes en ondersteuning voor netwerkbeveiligingsgroepen, moet ondersteuning voor netwerkbeleid zijn ingeschakeld voor het subnet. Deze instelling is alleen van toepassing op privé-eindpunten in het subnet en is van invloed op alle privé-eindpunten in het subnet. Voor andere resources in het subnet wordt de toegang beheerd op basis van beveiligingsregels in de netwerkbeveiligingsgroep. Zie Netwerkbeleid voor privé-eindpunten beheren voor meer informatie. Privé-IP-configuratie Automatisch ingesteld op dynamisch toewijzen van een van de beschikbare IP-adressen in het bereik dat is toegewezen aan het geselecteerde subnet. Dit IP-adres is het ip-adres dat is toegewezen aan de netwerkinterface die is gekoppeld aan het privé-eindpunt. Het kan dynamisch worden toegewezen vanuit het bereik dat is toegewezen aan het geselecteerde subnet of u kunt bepalen welk specifiek adres u eraan wilt toewijzen. Nadat het privé-eindpunt is gemaakt, kunt u het IP-adres niet wijzigen, ongeacht welke van de twee toewijzingsmodi u selecteert tijdens het maken. Toepassingsbeveiligingsgroep Er is standaard geen toepassingsbeveiligingsgroep toegewezen. U kunt een bestaande kiezen of u kunt er een maken en deze toewijzen. Met behulp van toepassingsbeveiligingsgroepen kunt u netwerkbeveiliging configureren als een natuurlijk verlengstuk van de structuur van een toepassing, waarbij u virtuele machines kunt groeperen en netwerkbeveiligingsbeleid kunt definiëren op basis van die groepen. U kunt het beveiligingsbeleid op grote schaal opnieuw gebruiken zonder handmatig onderhoud van expliciete IP-adressen. Het platform verwerkt de complexiteit van expliciete IP-adressen en meerdere regelsets, zodat u zich kunt richten op uw bedrijfslogica. Zie Toepassingsbeveiligingsgroepen voor meer informatie. Vul op de PAGINA DNS alle vereiste gegevens in. Selecteer vervolgens Volgende: Tags.
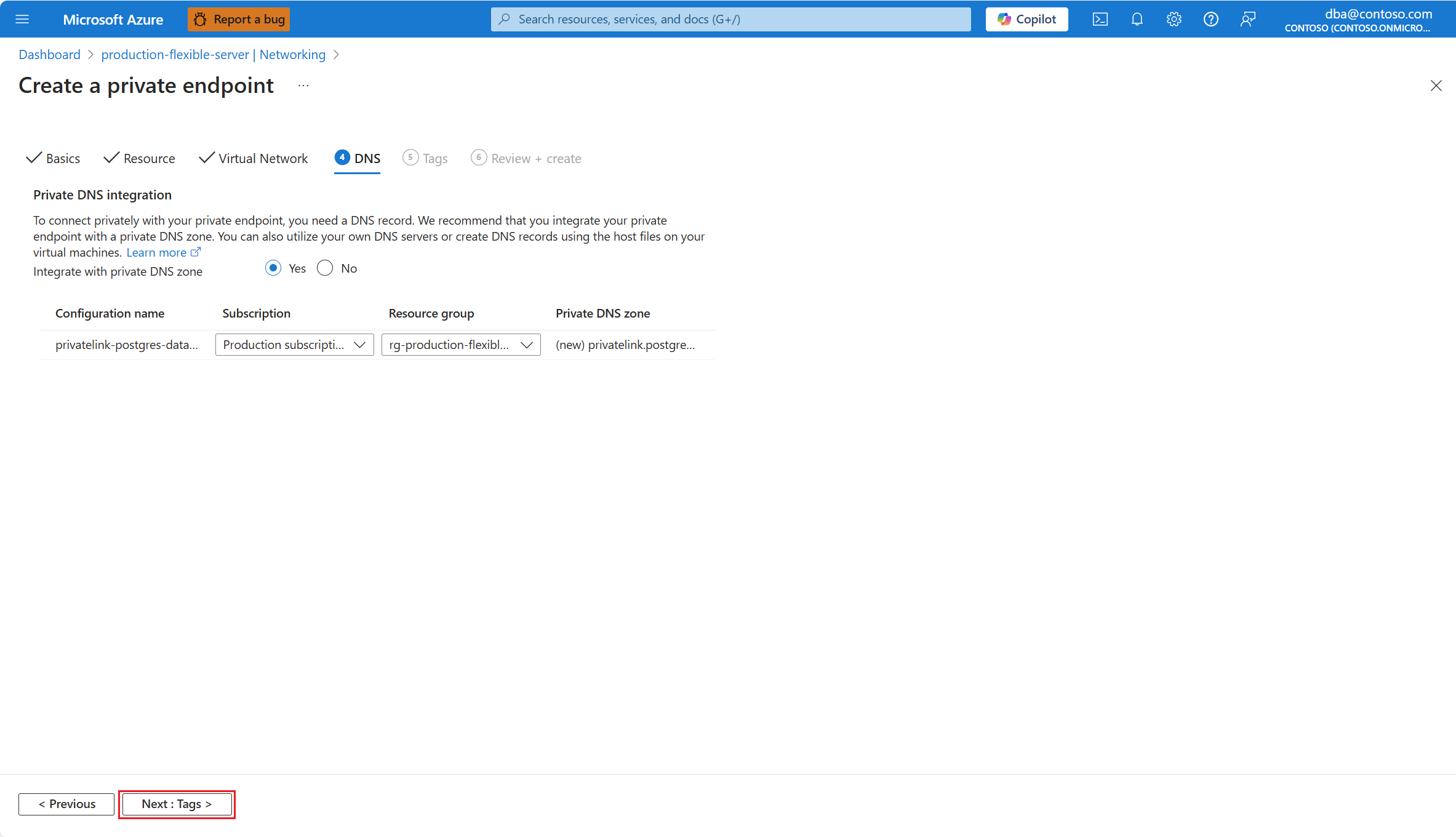
Gebruik de volgende tabel om inzicht te krijgen in de betekenis van de verschillende velden die beschikbaar zijn op de DNS-pagina en als richtlijnen voor het vullen van de pagina:
Instelling Voorgestelde waarde Beschrijving Integreren met privé-DNS-zone Standaard ingeschakeld. Selecteer Ja als u wilt dat uw privé-eindpunt wordt geïntegreerd met een privé-DNS-zone van Azure of Nee als u uw eigen DNS-servers wilt gebruiken, of als u de naam van het eindpunt wilt omzetten met behulp van hostbestanden op de computers waaruit u verbinding wilt maken via het privé-eindpunt. Zie DNS-configuratie voor privé-eindpunten voor meer informatie. Als u privé-DNS-zoneintegratie configureert, wordt de privé-DNS-zone automatisch gekoppeld aan het virtuele netwerk waarin u het privé-eindpunt maakt. Configuratienaam Automatisch ingesteld op privatelink-postgres-database-azure-com.De naam die is toegewezen aan de DNS-configuratie die is gekoppeld aan de privé-DNS-zone. Abonnement Selecteer de naam van het abonnement waarin u de privé-DNS-zone wilt maken. Hiermee wordt automatisch het abonnement geselecteerd waarin uw server is geïmplementeerd. Een abonnement is een overeenkomst met Microsoft voor het gebruik van een of meer Microsoft-cloudplatforms of -services, waarvoor kosten worden berekend op basis van een licentiekosten per gebruiker of op resourceverbruik in de cloud. Als u meerdere abonnementen hebt, kiest u het abonnement waarin u wilt worden gefactureerd voor de resource. Resourcegroep De resourcegroep in het geselecteerde abonnement waarin u de privé-DNS-zone wilt maken. Dit moet een bestaande resourcegroep zijn. Hiermee wordt automatisch de resourcegroep geselecteerd waarin uw server is geïmplementeerd. Een resourcegroep is een container met gerelateerde resources voor een Azure-oplossing. De resourcegroep kan alle resources voor de oplossing bevatten of enkel de resources die u als groep wilt beheren. U bepaalt hoe resources worden toegewezen aan resourcegroepen op basis van wat voor uw organisatie het meest zinvol is. Over het algemeen voegt u resources toe die dezelfde levenscyclus delen met dezelfde resourcegroep, zodat u ze eenvoudig als groep kunt implementeren, bijwerken en verwijderen. Privé-DNS zone Automatisch ingesteld op privatelink.postgres.database.azure.com.Deze naam is de naam die is toegewezen aan de privé-DNS-zoneresource. Vul op de pagina Tags alle vereiste gegevens in. Selecteer vervolgens Volgende: Beoordelen en maken.
Gebruik de volgende tabel om inzicht te krijgen in de betekenis van de verschillende velden die beschikbaar zijn op de pagina Tags en als richtlijnen voor het vullen van de pagina:
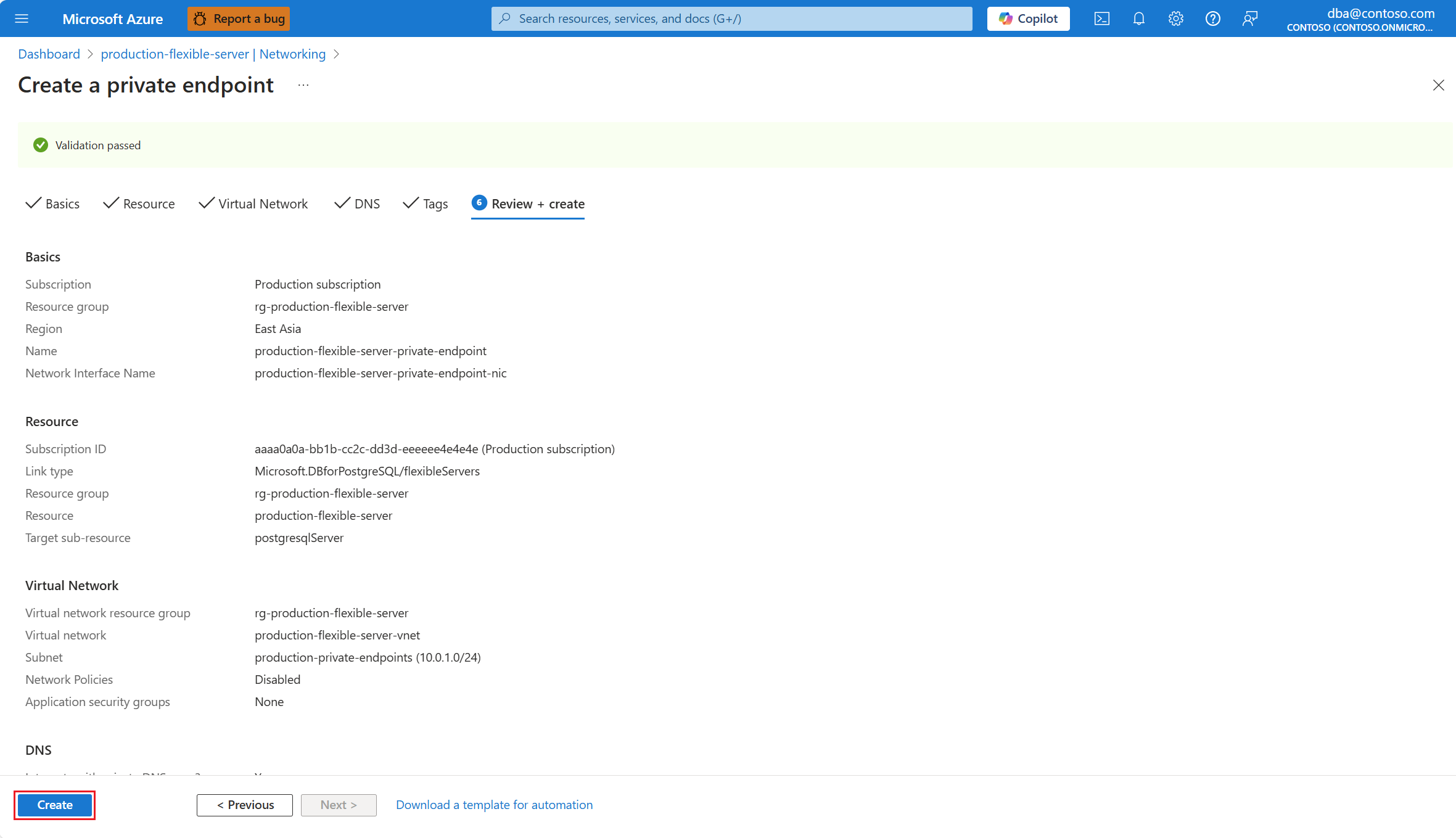
Instelling Voorgestelde waarde Omschrijving Naam Leeg laten. De naam van de tag die u wilt toewijzen aan uw privé-eindpunt en privé-DNS-zone (als u de integratie van de privé-DNS-zone op de DNS-pagina hebt geselecteerd). Value Leeg laten. Waarde die u wilt toewijzen aan de tag met de opgegeven naam en die u wilt toewijzen aan uw privé-eindpunt en privé-DNS-zone (als u de integratie van de privé-DNS-zone op de DNS-pagina hebt geselecteerd). Resource Laat standaard staan. U kunt selecteren aan welke resources u de opgegeven tag wilt toewijzen. Dit kan het privé-eindpunt, de privé-DNS-zone (als u de integratie van de privé-DNS-zone op de DNS-pagina ) of beide hebt geselecteerd. Controleer op de pagina Controleren en maken of alles is geconfigureerd zoals u wilt. Ten slotte selecteert u Maken.
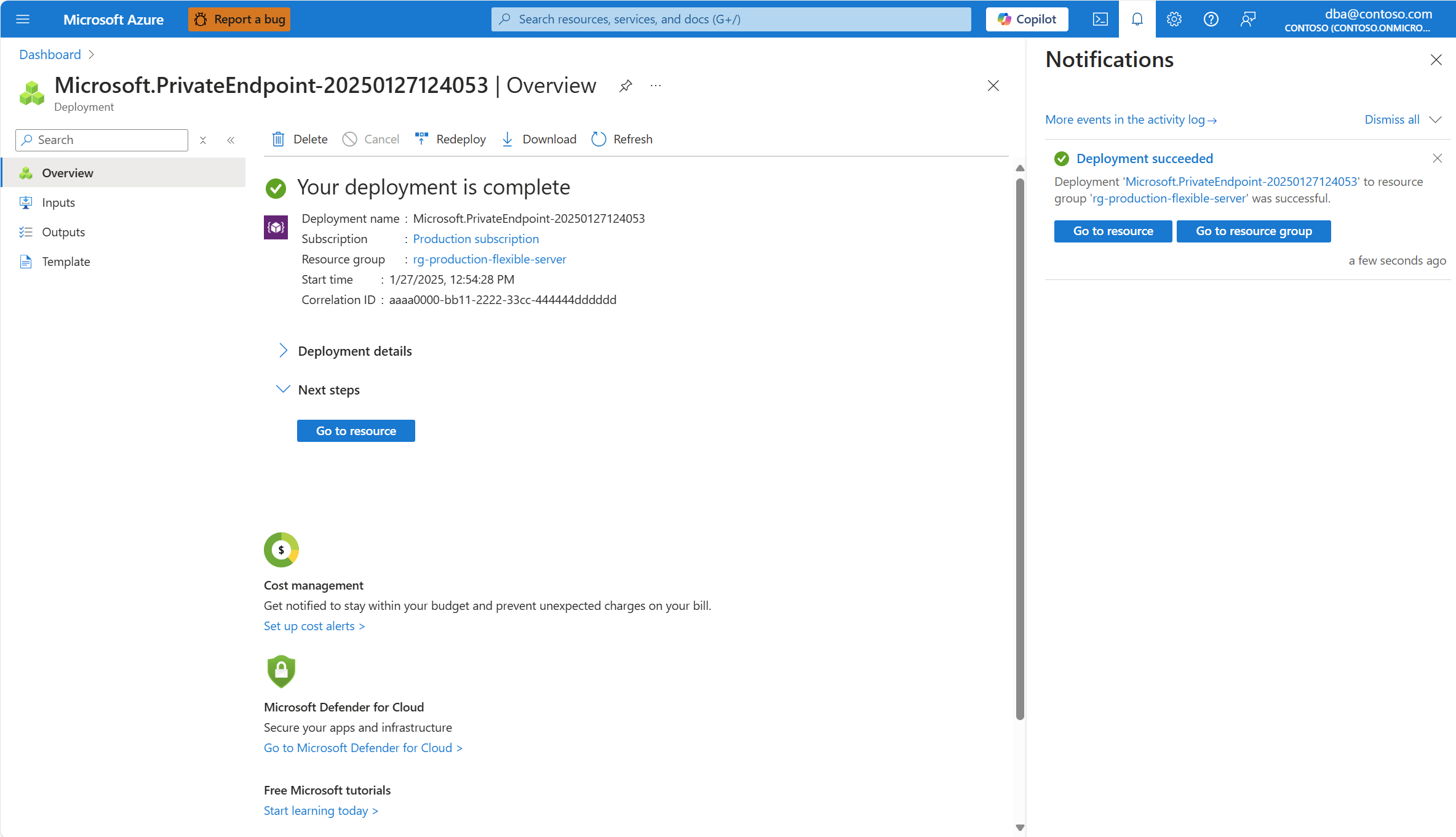
Er wordt een implementatie gestart en u ziet een melding wanneer de implementatie is voltooid.
Gerelateerde inhoud
- Netwerken.
- Openbare toegang inschakelen.
- Openbare toegang uitschakelen.
- Voeg firewallregels toe.
- Firewallregels verwijderen.
- Privé-eindpuntverbindingen verwijderen.
- Privé-eindpuntverbindingen goedkeuren.
- Privé-eindpuntverbindingen weigeren.