Claims-Based Authorization In Claims-Aware Applications and Services
Back to [[Windows Azure Active Directory Solutions For Developers]]
Scenario
In this scenario application requires to implement complex authorization rules logic, something that cannot be satisfied using only roles. The application enforces access by calculating the outcome - grant or deny access - based on the information available in the request including the claims in the incoming token.
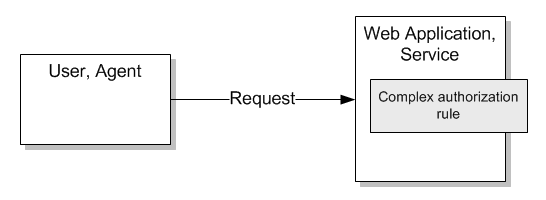
- The application uses claims-based authentication
- Role Based Access Control (RBAC) cannot satisfy authorization requirements
- Authorization outcome - grant or deny access - is calculated based on complex rules and the data available in the token.
Solution Approach
The solution relies on ClaimsAuthorizationManager - WIF' extensibility point. You develop custom ClaimsAuthorizationManager and register it in web.config. You can optionally express the rules as a policy in the web.config so that the custom ClaimsAuthorizationManager can read them at run time and enforce them for the incoming requests. For detailed step-by-step walkthrough read How To: Implement Claims Authorization in a Claims-Aware ASP.NET Application Using WIF and ACS.
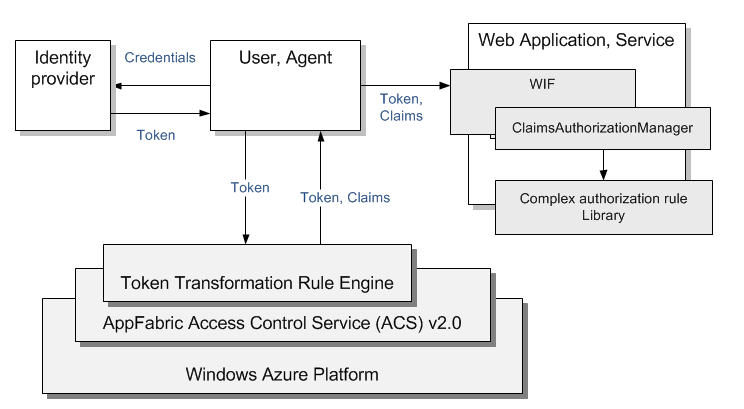
- Application uses WIF
- Application uses ClaimsAuthorizationManager as an extensibility point
- Implement custom ClaimsAuthorizationManager and define authorization policy in the configuration file
- Call CheckAccss in the code to enforce the authorization policy.
Analysis
Implement claims-cased authorization when role base access control (RBAC) is insufficient to satisfy authorization requirements. Read more about RBAC in Role-Based Access Control (RBAC) Authorization In Claims-Aware Applications
How-To's
- How To: Implement Token Transformation Logic Using Rules
- How To: Implement Claims Authorization in a Claims-Aware ASP.NET Application Using WIF and ACS
Code Samples
- Code Sample: Claims based Authorization in Windows Identity Foundation SDK