Some Useful Features with Windows Group Policies
Applocker
Applocker was introduced in Server 2008 R2 with Windows 7 and its used for control of applications. Which means using applocker we can restrict required application/s to end users. Applocker provides several methods for administrators to restrict required applications such as File hash,publisher and path. We can apply applocker policy to computer/s in a organizational unit or a specific Active Directory user or Group.
How to configure Applocker policy
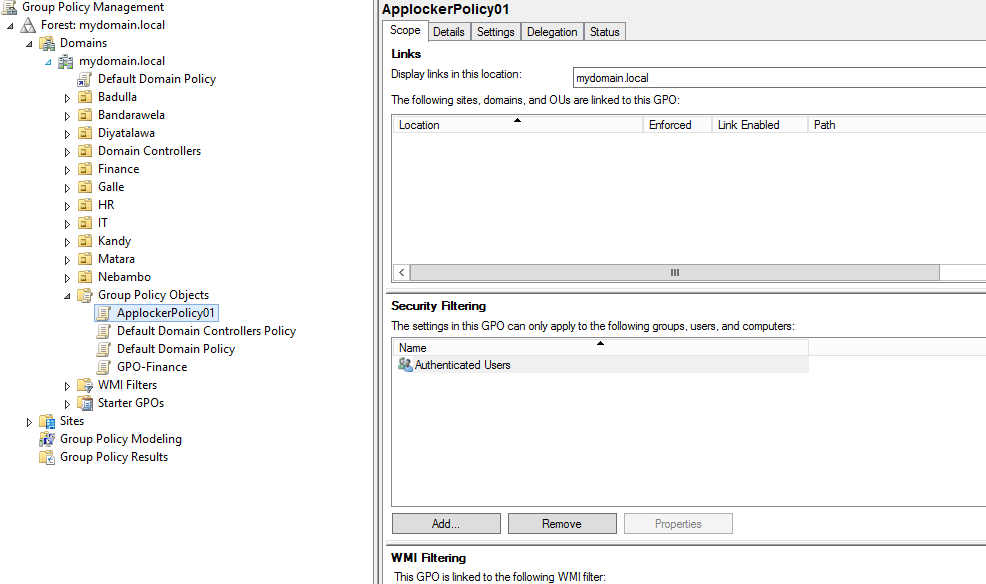
Login to the one of domain controller and open group policy management console
Create a group policy(Applockerpolicy01)
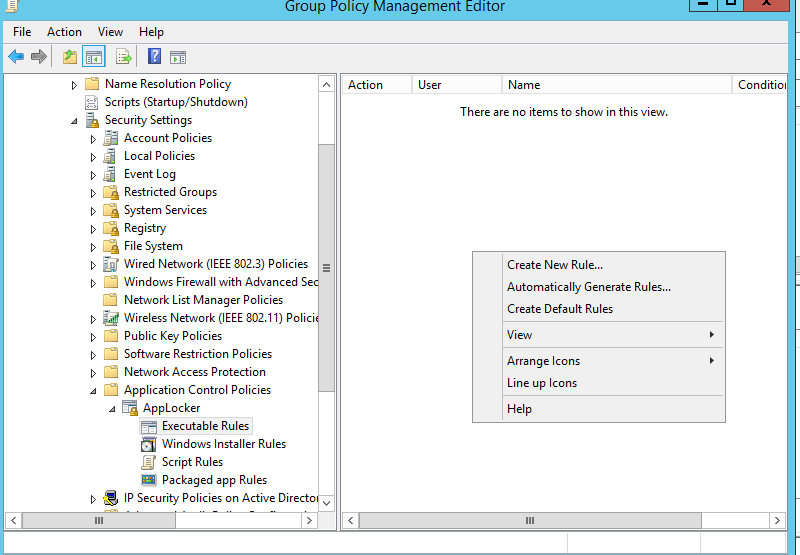
Edit the created group policy(Computer configuration>Windows Setting >Security Setting > Application Control Policies > Executable Rules)
Right click on the white space and select "Create New Rule"
Click on Next
Click on "Next"
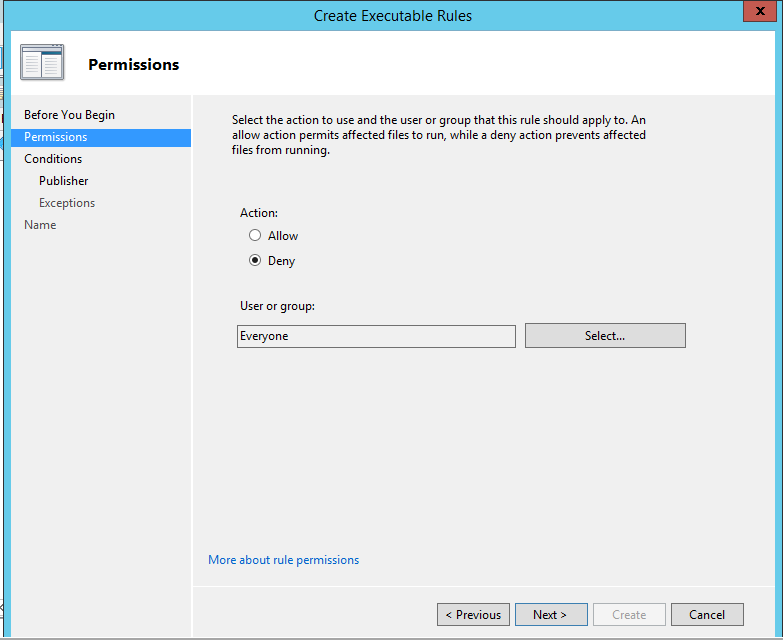
Select "Deny" and click on "Next"(If we want we can apply this policy on single ad user or group,therefore we have to browse ad user/groups,also we can restrict all the applications and create allow rules)
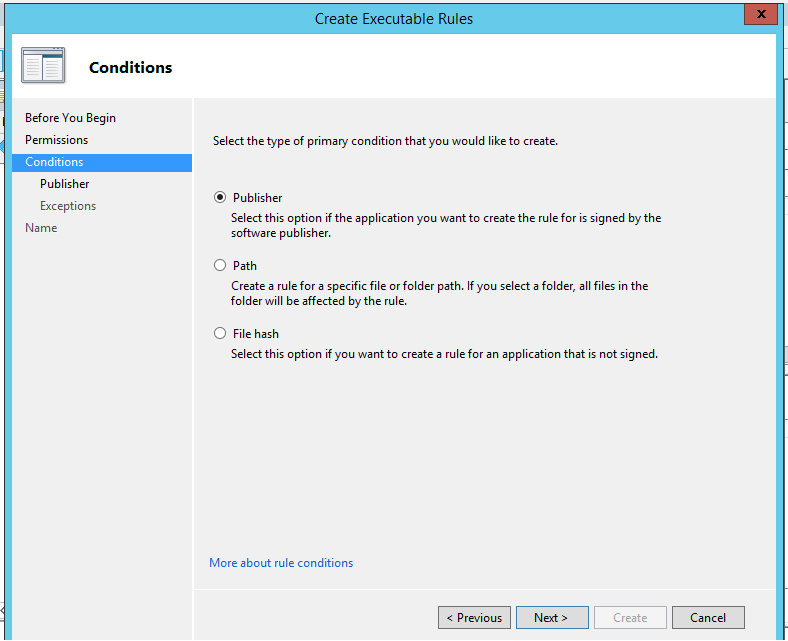
Select "Publisher" and click on "Next"(We can block the application using path and the file hash also
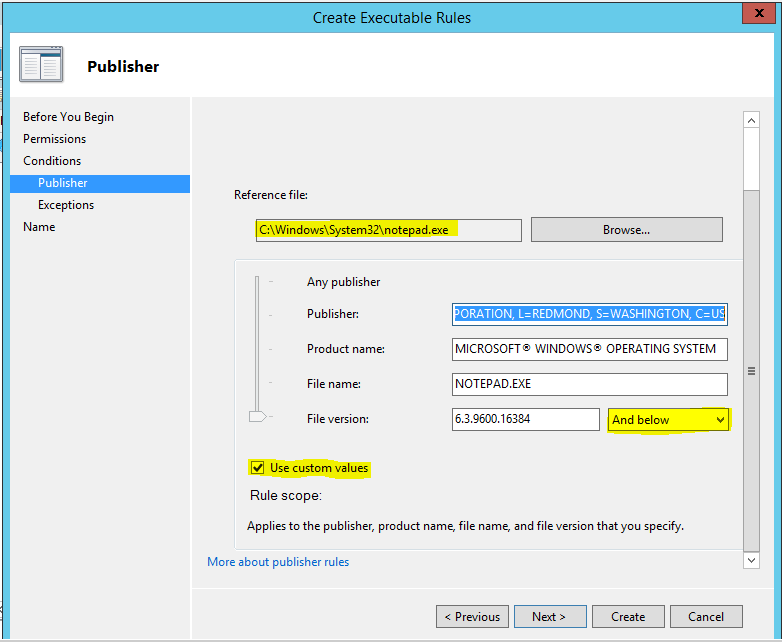
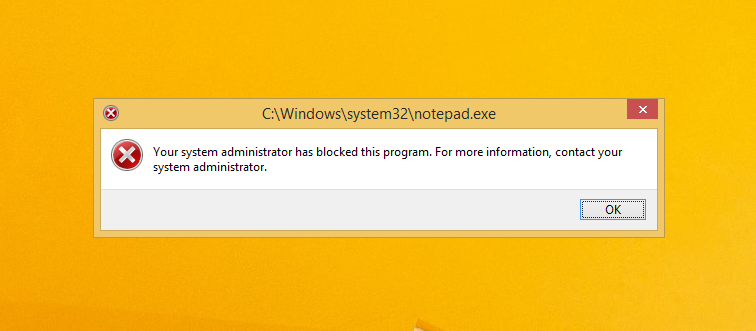
Browse and select the exe file which we want to block.(With this example we are blocking notepad.exe)
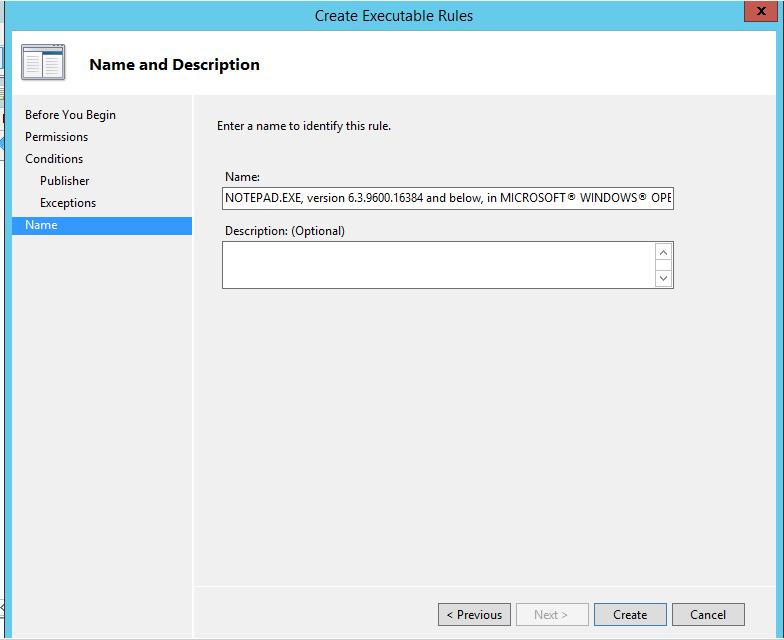
Select "Use Custom Value" check box and select "And Below" from file version drop down list(Other wise it will block on the exact version of the notepad only.Also if we like we can block all the Microsoft based applications.This needs to adjust the slide bar on the left side)
Click On Next
Click on "Create"
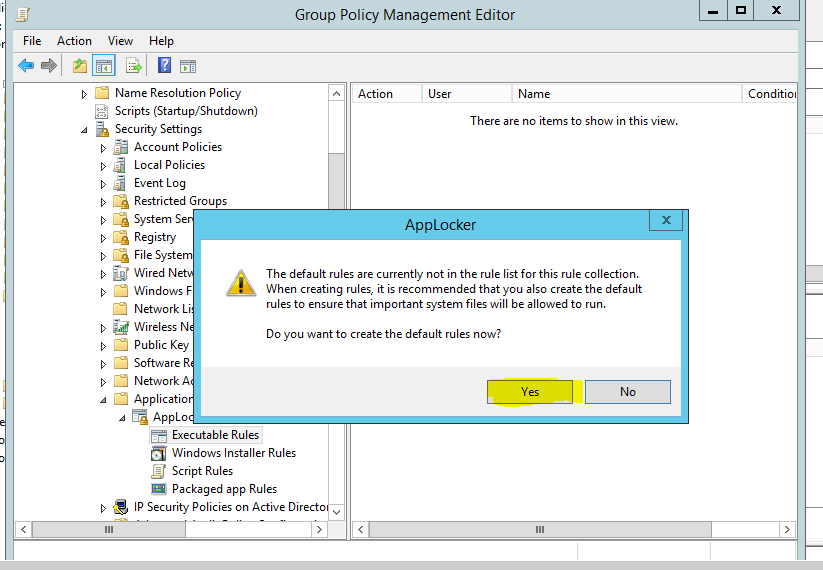
Click on "Yes" for create default rules
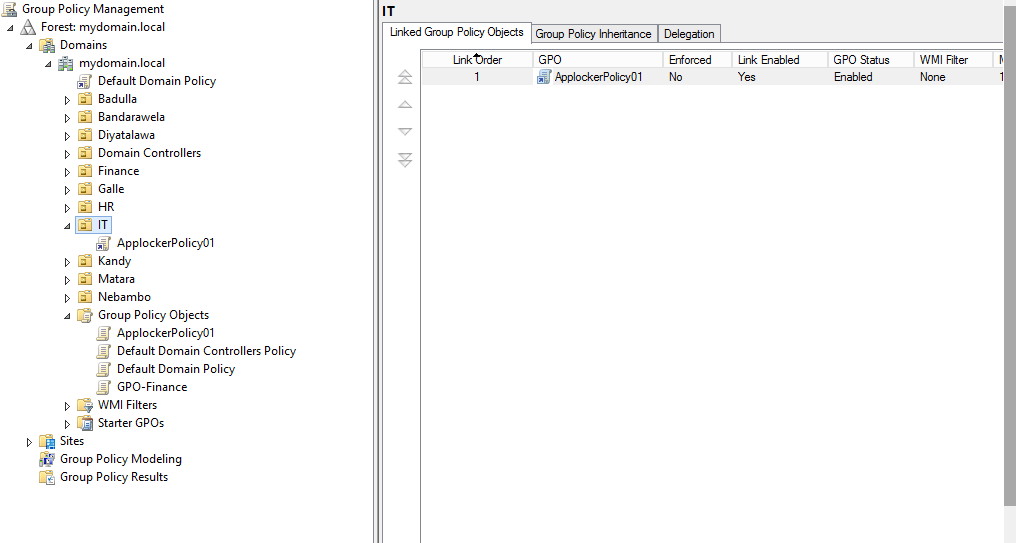
Apply group policy for required organizational unit
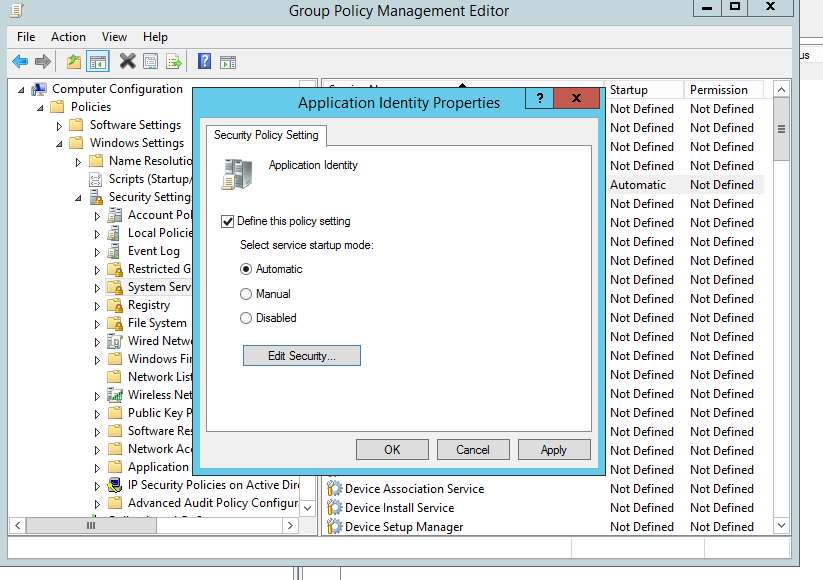
Applocker uses "Application Identity service" to verify the application. Therefore we have to start this service on the client side. We can do this using same policy also
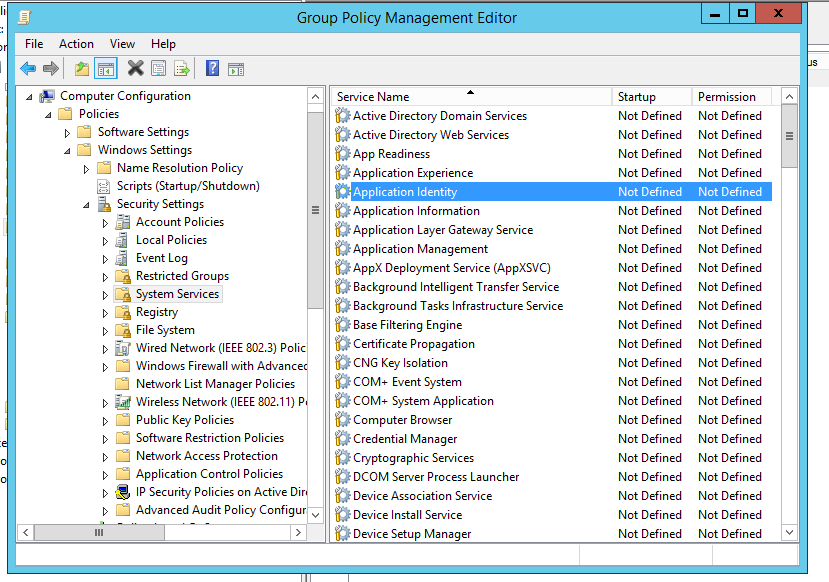
Edit the group policy(Computer Configuration>Policies>Windows Settings>Security Settings>System Services>Double click on the Application Identity Service)
Select the "Automatic" as start up type
After running Gpupde /force from the client side we can check the applockers functionality
**Restricted Group
**with the "Restricted Group" we can control membership of the groups such as local administrators. Using this policy we can restrict adding unnecessary users to privilege groups in the local computers
How to configure restricted groups
Open group policy management console
Create new group policy
Edit the policy(Computer configuration > Windows Settings > Security Settings >Restricted Groups)
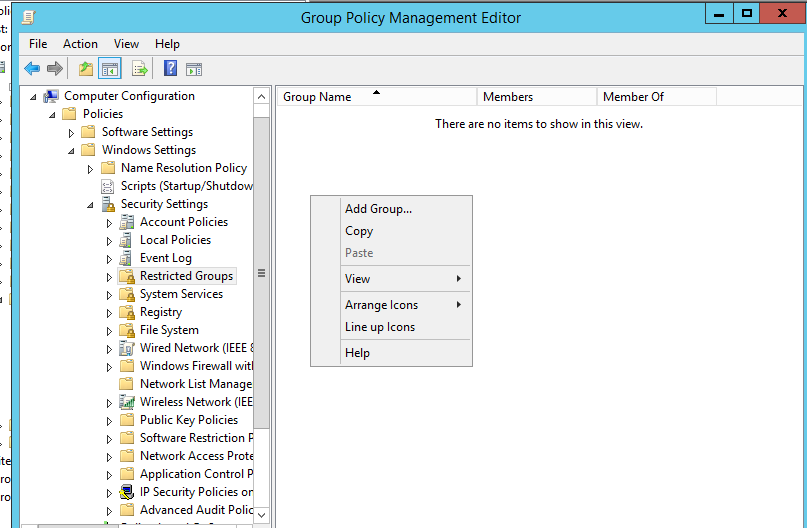
Right Click on right side white space
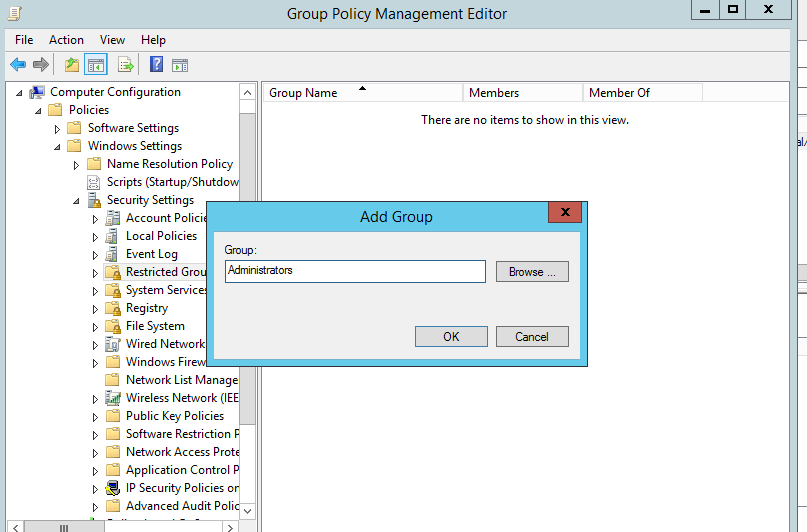
Select Add Grpup
Type Administrators on the Group text box(I'm going to change members of the local computers Administrators group)
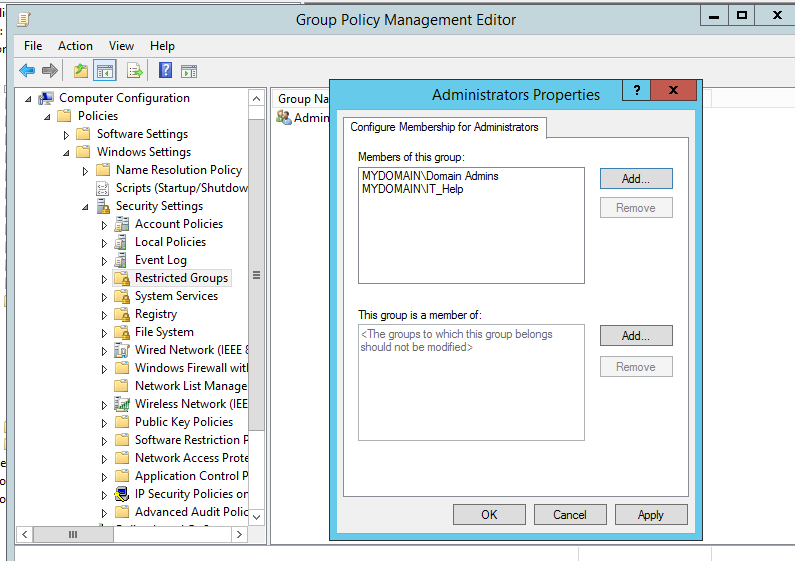
Add required users to "Members of this group" box(Remember to add Domain Admins also, because once we configured this policy it will remove all the users except default local Administrator from the administrators group)
Link this policy to required organizational unit\Domain\Site
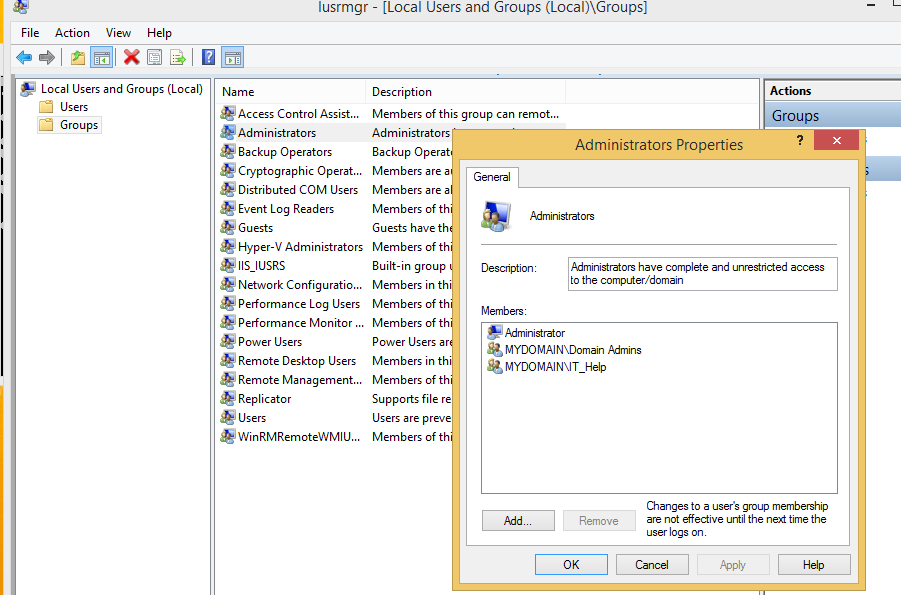
Check the functionality from one of the client computer(Before we configure this policy its better to add some other user/s to one of the client computers local administrators group, then we can see because of this policy those account will be removed from the group)