Certificate Services Lifecycle Notifications
Applies to Windows 8 and Windows Server 2012
Overview
Certificate lifecycle management is a troublesome issue for many IT professionals, especially when certificates expire. While certificates can often be renewed automatically, the applications that depend upon these applications are often not aware of the renewed certificate. This prevents the application from utilizing the renewed certificate and eventually the old certificate expires, which often results in a service outage. Another issue with certificate lifecycle management is a lack of notification before a certificate is about to expire.
Starting in Windows 8 and Windows Server 2012, administrators can utilize certificate services lifecycle notifications to help manage certificate over their lifecycle for users and computers. By using Windows® PowerShell cmdlets, administrators can register certificate notification tasks to be run upon certificate services lifecycle events. For example, an administrator could register a task that would run a Windows PowerShell script to renew and reconfigure a certificate for an application when the existing certificate is about to expire.
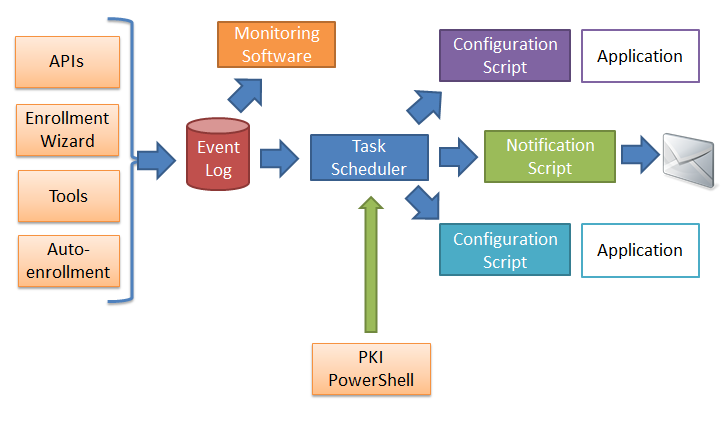
Certificate services lifecycle notifications leverage both the Event Viewer and Task Scheduler as shown in the following diagram:
This architecture allows multiple options for integration:
- Monitoring software: Software products, such as Microsoft System Center 2012, can monitor certificate lifecycle events directly from the event log .
- Configuration scripts: Administrators can configure Windows PowerShell scripts that modify system or application settings based on specific certificate lifecycle events.
- A configuration script can be deployed using PKI Windows PowerShell cmdLets for expiration and replace events.
- Task scheduler can be used directly to launch scripts for any lifecycle notification.
- Notification scripts: Administrators can configure a script to notify them via email or a log.
- Applications: Developers of applications that take advantage of certificates can use Event Log APIs to monitor the status of certificates they are using.
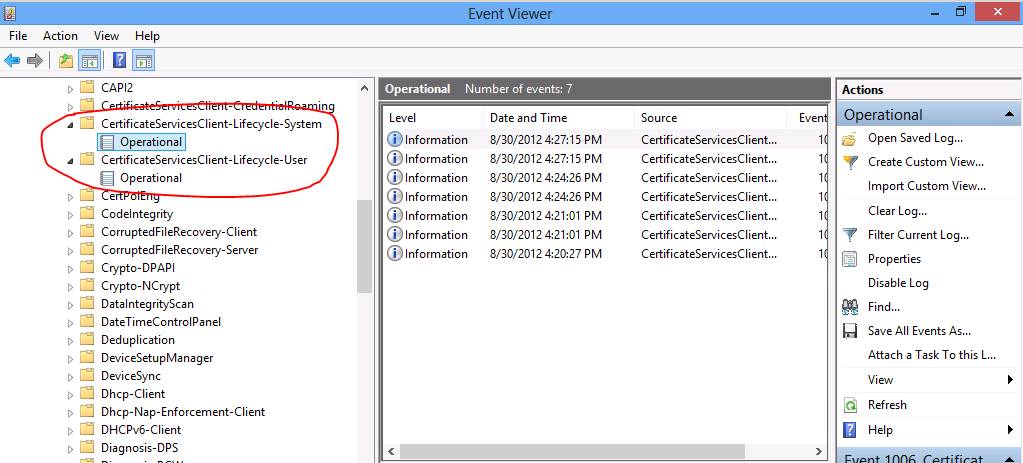
Event Viewer
Starting in Windows 8 and Windows Server 2012, two new event logs have been added to allow for certificate services lifecycle events. These new logs are located in the Event Viewer application under Applications and Service Logs , Microsoft, Windows as:
- CertificateServicesClient-Lifecycle-System
- CertificateServicesClient-Lifecycle-User
Each log has a subordinate Operational log where the certificate services events are recorded.
The events that are reported include:
| Event |
ID |
Level |
Detail |
Sources |
| New | 1006 | Informational | • Action (see sources column) • Template • Subject names • Enhanced Key Usages (EKUs) • Thumbprint |
Enrollment or renewal via autoenrollment (action=enroll) • Enrollment or renewal via MMC enrollment (action=enroll) • Enrollment or renewal via certreq.exe (includes both -enroll and -accept) (action=enroll) • Enrollment via Get-Certificate CmdLet • For each certificate with a private key imported from a PFX file via (action=import): o Import-PFXCertificate o Import Wizard o Certutil.exe –importPFX • Move or Copy of a certificate that has a private key by using (action=MoveOrCopy): o Move-Item CmdLet o Copy or move in MMC snap-in |
| Replace | 1001 | Informational | • Action (see sources column) For old and new certificate: • Template • Subject names • EKUs • Thumbprint |
• Renewal via autoenrollment (action=renew) • Enrollment for a superseding (action=supersede) • Renewal via MMC enrollment (action=renew) • Renewal via certreq.exe (action=renew) • Manually replacing on cert with another using Replace-Certificate PowerShell CmdLet (action=replace) |
| Close to expiration | 1003 | Warning | • Template • Subject names • EKUs • Thumbprint • Store • Expiration |
Autoenrollment, when Renew expired certificates, update pending certificates, and remove revoked certificates is NOT selected. |
| Expired | 1002 | Error | • Template • Subject names • EKUs • Thumbprint • Store • Expiration |
Autoenrollment, when Renew expired certificates, update pending certificates, and remove revoked certificates is NOT enabled. |
| Deleted | 1004 | Informational | • Template • Subject names • EKUs • Thumbprint |
• Autoenrollment • Certificate deletion in MMC (computer and user MY stores only) • Certificate deletion with remove-item in PowerShell certificate provider (computer and user MY stores only) • Move-item CmdLet of the PowerShell certificate provider • Certificate deletion when in the Export Wizard user choses an option that says to delete a certificate. |
| Archived | 1005 | Informational | • Template • Subject names • EKUs • Thumbprint |
Autoenrollment, when Renew expired certificates, update pending certificates, and remove revoked certificates is enabled. |
| Exported | 1007 | Informational | • Template • Subject names • EKUs • Thumbprint |
• Export-PFXCertificate • Export Wizard (PFX case only) • Certutil.exe -exportPFX |
Notes:
- Except for expiration and close to expiration notifications, only certificates in MY store are covered.
- Only certificates exported with private keys generate the exported event.
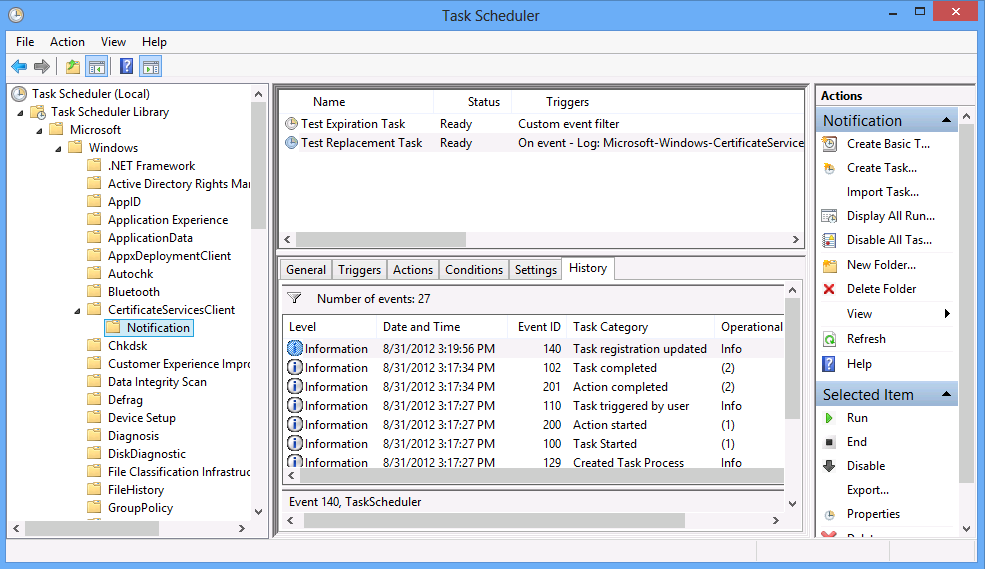
Task Scheduler
In the Task Scheduler there is a new task category called Notifications in the Task Scheduler Library, Microsoft, Windows, CertificateServicesClient.
These tasks can be created using the Windows PowerShell cmdlet New-CertificateNotificationTask. To review certificate services notification tasks that have already been created on a computer, you can use the Get-CertificateNotificationTask cmdlet. To remove a certificate services notification task, you can use the Remove-CertificateNotificationTask.
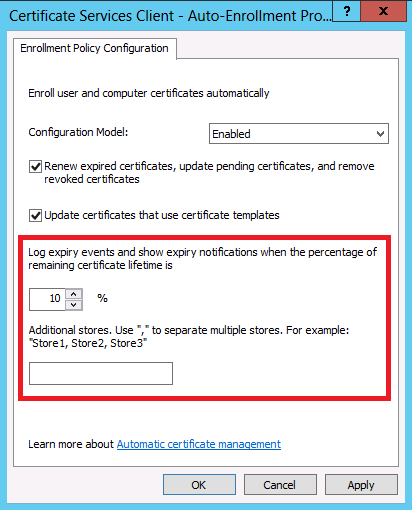
Settings for Autoenrollment added to Group Policy
In Group Policy in the Certificate Services Client - Auto-Enrollment Policy, you can configure the percentage of lifetime left on the certificate before a warning is displayed. You can also configure additional certificate stores to be monitored. The CurrentUser\My and LocalMachine\My stores are monitored by default when the policy is enabled.
You can enable expiration percentage calculation as well as the additional certificate stores to be monitored in the following locations:
- For user certificates, use User Configuration, Policies, Windows Settings, Security Settings, Public Key Policies, Certificate Services Client - Auto-Enrollment
- For computer certificates, use Computer Configuration, Windows Settings, Security Settings, Public Key Policies, Certificate Services Client - Auto-Enrollment
You can configure the Log expiry events and show expiry notifications when the percentage of the remaining certificate lifetime setting as appropriate. You can also use the Additional Stores section to configure additional certificate stores that you want to monitor for certificate expiration notifications.
Windows PowerShell Script for IIS Binding
To understand how certificate lifecycle notification could be useful, consider the renewal of a certificate for a web site that uses Internet Information Services (IIS). Although a certificate can be automatically renewed, it does not automatically rebind to the IIS site utilizing the certificate. A Windows PowerShell script could be utilized to replace the certificate binding upon certificate renewal. For example, consider the following script, named UpdateIISCert.ps1.
#
**# This script will have these parameters passed to it:
#
# OldCertHash - thumbprint of the certificate that has been renewed
# NewCertHash - thumbprint of the certificate that renewed the old certificate
#
param([string]$OldCertHash, [string]$NewCertHash)
import-module webadministration# get a binding that is using the old cert**
$res = (dir IIS:\SslBindings | where-Object {$_.Thumbprint -match $OldCertHash})
#find new cert
$newCert = dir “cert:\LocalMachine\My\NewCertHash”
#for each binding that was using the cert
if($newCert -ne $null)
{
$res | ForEach-Object {$_.Thumbprint = $newCert.Thumbprint; $_ | set-item;}
}
An administrator could then run the following Windows PowerShell command to register the script with the task scheduler:
New-CertificateNotificationTask -Type Replace -PSScript "c:\Scripts\UpdateIISCert.ps1" -Name UpdateIISCert -Channel System
When the task is created, it includes the thumbprint definition for the $OldCertHash. The Windows PowerShell script is automatically run when any certificate in the Cert:\LocalMachine\My store is replaced. If the certificate thumbprint that was replaced matches the certificate thumbprint of $OldCertHash, then the IIS binding is updated to the certificate that matches $NewCertHash.
Scripting considerations
When creating scripts that will automatically reconfigure the certificates for your organization's users or computers, you should ensure the scripts are:
- written and tested to work exactly as expected
- secure from unauthorized use by properly securing them with access control lists
- digitally signed to prevent inappropriate modification
Specific additional considerations are elaborated in the following sections.
Windows PowerShell script security
Certificate services notifications are designed to trigger Windows PowerShell scripts to perform administrative tasks, such as binding a renewed certificate to an application. Since these Windows PowerShell scripts are run with system privileges, they could be a target for an attacker to run malicious code. Administrators should be cautious to ensure they set the appropriate permissions on the scripts to help prevent the scripts from being used for other than their intended purposes.
To prevent scripts from being tampered with, you can use digital signing on your PowerShell scripts. For information about signing PowerShell scripts, see Windows PowerShell Sign Here, Please.
Denial of service potential
Events that are logged in the Event Viewer CertificateServicesClient-Lifecycle-User log can trigger scripts that run for all users. Since a certificate services lifecycle notification event can trigger a script, when the script is run, it could affect other users on that computer. This could become an issue on a shared computer, such as when multiple users are using a remote desktop services (RDS) server. This is unlikely to be a problem because the scripts that are triggered by certificate services lifecycle notification events should not consume enough computer resources to severely affect other users of that computer. System administrators should be aware of the potential for this issue and take appropriate steps to mitigate this issue, such as:
- Test certificate lifecycle notification scripts to ensure they do not cause error conditions that will consume resources unnecessarily.
- Review the Task Scheduler Library's scheduled tasks to ensure that inappropriate tasks are not configured to run when a certificate services client notification event occurs.
- Review the Task Scheduler to ensure that scheduled tasks are not failing.
- When scripts are published to remote servers, only secure communications should be used.
Do not use CertificateServicesClient-Lifecycle-User Event Log Channel for non-repudiation
The CertificateServicesClient-Lifecycle-User Event log channel is shared by any logged on user. Any logged on user can write an event log entry that appears to have been generated by another user. Therefore, you should not rely on this log to prove that a particular user performed a particular action.
Document using SID in the system context of the events when updating user bindings
A script configured to run based on events in the CertificateServicesClient-Lifecycle-User Event log channel will be run for all logged on users. The script should verify the user account does have the particular certificate, before making any changes. Also, the information in the Details section of the CertificateServicesClient-Lifecycle-User Event log channel can be spoofed (as previously explained), so those details should not considered sufficient for security purposes. The script should verify the certificate exists and verify its details. The script should also be configured so that running multiple times does not cause problems.