Goodbye Network Service!
IIS 6.0 introduced a lot of features to increase reliability and security. As an architectural change the worker process w3wp.exe was introduced. To increase security IIS 6.0 by default launched the worker process using the NTAuthority\Network Service account. Network Service is a low privilege predefined account that was introduced in Windows 2003. All guidance/documentation recommend running the worker process under the Network Service.
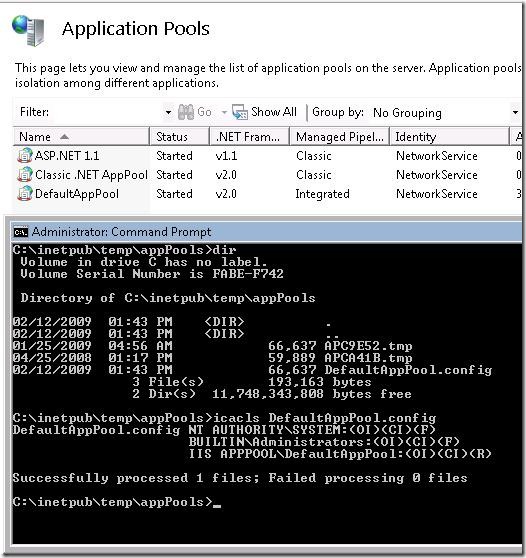
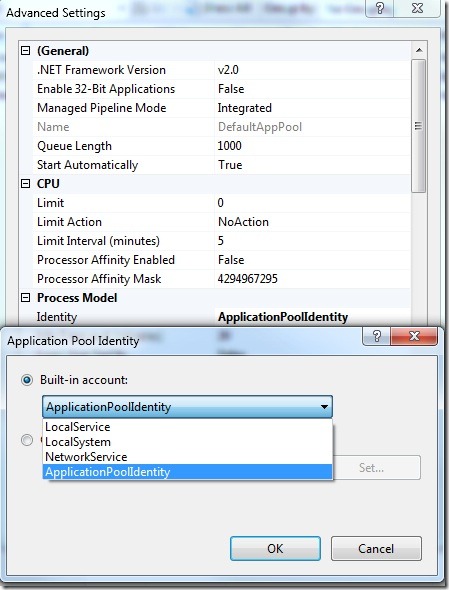
With IIS 7.0 a new concept of ApplicationPoolIdentity was introduced. IIS 7.0 creates an ephemeral configuration file in C:\inetpub\temp\appPools and uses it. The configuration file is ACL’ed using the ApplicationPoolIdentity (IIS APPPOOL\ApplicationPoolName).
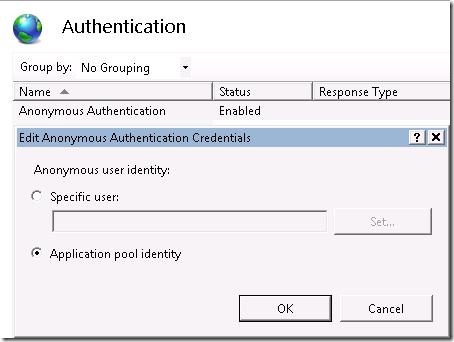
This adds a new layer of security as now the configuration file is only accessible by that application pool. The ApplicationPoolIdentity can also be used as the account for Anonymous Authentication.
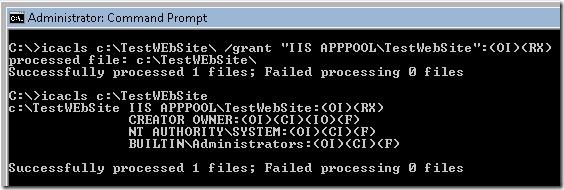
Instead of using the generic IUSR account you can now ACL your content using the ApplicationPoolIdentity.
This would mean your content will only be available to the TestWebSite Application Pool. If any other application pool tried to access/run the content a 401.3 Unauthorized error message will be thrown. But in IIS 7.0 we still use Network Service to launch the w3wp.exe process.
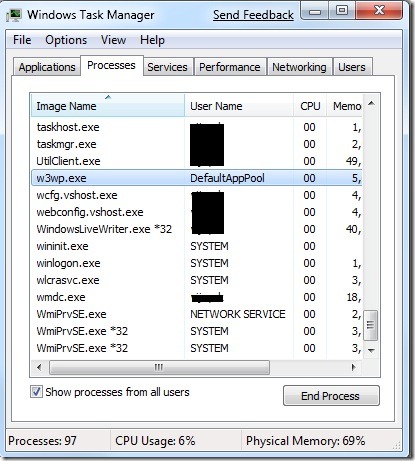
With IIS 7.5 security is being tightened further and now the w3wp.exe process by default uses the ApplicationPoolIdentity to run. Going forward in Windows Server 2008 R2 and Windows 7 by default the worker process will now be run as the ApplicationPoolIdentity which is a Managed Service Account. Managed Service Accounts are a new concept in Win 7 / Windows 2008 R2 you can read more about them here https://technet.microsoft.com/en-us/library/dd367859.aspx
What this means is that you now need to ACL your content based on this ephemeral ApplicationPoolIdentity account (IIS APPPOOL\ApplicationPool ) instead of the NTAuthority\Network Service.
In the near future IIS will by default distance itself from Network Service. But you still do have the option to change the identity back to Network Service.
Comments
Anonymous
February 13, 2009
PingBack from http://www.clickandsolve.com/?p=7757Anonymous
February 13, 2009
Does this change how you access external resource, ie SQL Server. With Network Service, we grant access to databases via domainmachinename$. Does this work the same?Anonymous
February 13, 2009
No. Even here it will be domainmachine$Anonymous
March 13, 2009
IIS 6.0 introduced a lot of features to increase reliability and security. As an architectural changeAnonymous
March 26, 2009
IIS 6.0 introduced a lot of features to increase reliability and security. As an architectural changeAnonymous
June 03, 2009
This new feature is available in Vista / win2008 SP2 no need to wait for windows 7, we just tried it on 2008 sp2 and it works like a charmAnonymous
July 19, 2009
The comment has been removedAnonymous
March 07, 2010
So... IIS7 + AppPoolId = W3wp.exe is NETWORK SERVICE IIS7.5 + AppPoolId = W3wp.exe is AppPoolId Does that mean constrained delegation will work with AppPoolId in IIS7 but won't work with AppPoolId in IIS7.5. That means in IIS 7.5 you should use NETWORK SERVICE if you are doing constrained delegation, correct?Anonymous
January 18, 2011
Geee... at first I was scared I'll have to master icacls.exe since the DefaulAppPool user is not visible in the list when trying to setup filesystem permissions via GUI (security tab). Also this user is not visible in the compmgmt.msc console. However it becomes visible after you assing it (OI)(RX) and possibly any priviledges. Well not the most intuitive solution but at least it works. BTW. I bet most admins in my company just instantly switched to Network Service :)