System Center Updates Publisher 2007 and WSUS Self-Signed Cert Option
What exactly do you need to do to get your environment ready to use the System Center Updates Publisher (SCUP) with the WSUS Self-Signed Cert (WSSC) option? There are a few key steps.
First, you have to configure SCUP to sign patches with the WSSC. To do that, select the settings option from the console screen
On the Update Server tab, select create to create the WSSC
Once complete, you should have a new WSSC as shown
This action creates the WSSC in the WSUS > Certificates note of the Certificates.msc as shown
So the certificate we need is now created, but we aren’t ready to go yet. Next we have to make sure the WSSC cert is included in the Trusted Publishers > Certificates and the Trusted Root Certificate Authorities > Certificates store. In my case, all components are on the same server so it’s a simple process to export the cert and import it to the other two stores. To export the cert, just right click on it and select to export – take all the defaults and save the cert to a .cer file. To import, just right click on the Trusted Publishers and Trusted Root Certificate Authorities nodes, respectively, and select to import and point to the file.
So now SCUP should be configured to sign updates with the WSSC and publish updates to the SCCM Software Update point and you can deploy them to clients. But, the clients aren’t ready to receive them and will reject the update if it arrives. To get the client ready to receive updates you need to transfer the WSSC to the clients certificate store as well. You can do this manually or even through software distribution using the certutil command.
To deploy the certificate with software distribution, do the following.
- Export the WSUS Publishers Self-signed certificate and public key to a directory on the local computer.
- Copy the Certutil.exe and Certadm.dll files to the same directory as the exported files. Certutil.exe is a command-line program that is installed as part of Certificate Services in the Windows Server 2003 family and both files are installed in %windir%\system32, by default.
- Create a software distribution package containing the files from step 1 and step 2. For more information, see How to Create a Package (https://go.microsoft.com/fwlink/?LinkId=108444)
- Add a software distribution program that runs the following command-line: certutil.exe -addstore TrustedPublisher wsus.cer, where TrustedPublisher is the name of the certificate store and wsus.cer is the name of the exported certificate. For more information about creating a software distribution program, see How to Create a Program (https://go.microsoft.com/fwlink/?LinkId=108446). For more information about certutil.exe, see the Certutil Web site on TechNet (https://go.microsoft.com/fwlink/?LinkId=108447)
- Create an advertisement for distributing the package and program to the appropriate collection. For more information, see How to Create an Advertisement (https://go.microsoft.com/fwlink/?LinkId=108449).
You may also have to include the WSSC in the Trusted Root Certificate Authorities node as well, which can be done with easy adjustments to the package if needed. Be sure and test first to determine exactly what is needed for your environment.
Once you have the certificates deployed, now you just have to adjust local policy to allow signed cupdates from an intranet Microsoft update service location. You can find that setting as shown below.
To test that everything is working, deploy a SCUP patch to a test client and review the WUAHandler.log. If all is configured properly, you should see the patch install if needed. If there are problems you will notice errors similar to the following in the log.
Failed to download updates to the WUAgent datastore. Error = 0x800b0109.
Going to search using WSUS update source.
Synchronous searching of all updates started...
Successfully completed synchronous searching of updates.
1. Update: 94d2b302-8f25-430a-aa7c-c158bdd6d65f, 1 BundledUpdates: 0
1. Update (Missing): Widget Builders Security Patch (94d2b302-8f25-430a-aa7c-c158bdd6d65f, 1)
Failed to download updates to the WUAgent datastore. Error = 0x800b0109.
Going to search using WSUS update source.
Synchronous searching of all updates started...
Successfully completed synchronous searching of updates.
1. Update: 8e77762b-f2a5-45b2-8d45-6e42869c549d, 1 BundledUpdates: 0
1. Update (Missing): Widget Sample Update (8e77762b-f2a5-45b2-8d45-6e42869c549d, 1)
Async installation of updates started.
The error code of 800b0109 translates to the following in error lookup so definitely points to the cert/group policy not being setup correctly.
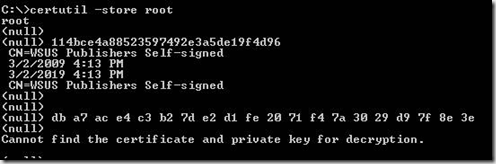
If you want to script a solution to verify the certificates are in the right stores you can use the certutil command again to do it. the certutil command can dump the contents of the store and your script can search the output for the WSSC. The command line for certutil plus the relevant output are below.
Failed to download updates to the WUAgent datastore. Error = 0x800b0109.
Going to search using WSUS update source.
Synchronous searching of all updates started...
Successfully completed synchronous searching of updates.
1. Update: 94d2b302-8f25-430a-aa7c-c158bdd6d65f, 1 BundledUpdates: 0
1. Update (Missing): Widget Builders Security Patch (94d2b302-8f25-430a-aa7c-c158bdd6d65f, 1)
Failed to download updates to the WUAgent datastore. Error = 0x800b0109.
Going to search using WSUS update source.
Synchronous searching of all updates started...
Successfully completed synchronous searching of updates.
1. Update: 8e77762b-f2a5-45b2-8d45-6e42869c549d, 1 BundledUpdates: 0
1. Update (Missing): Widget Sample Update (8e77762b-f2a5-45b2-8d45-6e42869c549d, 1)
Async installation of updates started.
The error code of 800b0109 translates to the following in error lookup so definitely points to the cert/group policy not being setup correctly.
Certutil –store TrustedPublisher
This looks to check the Trusted Publishers store and display all certs present
In addition, you would need a method to verify the GPO is enabled - that could be scripted as well.
Comments
- Anonymous
August 03, 2012
Is the WSUS self signed cert always 512 bit RSA?