Identity Federation & Single Sign on Deployment for Hybrid Search in Office 365 –SharePoint Online –Part3
Part1 and Part2 of this post talks about how we can configure two-way Hybrid search with Directory synchronization password sync. Note single sign on is not a core configuration requirement for Hybrid search , it enhances the sign in experience for the users when they access the content that are rendered in search results from SharePoint Online. As mentioned in part 1 of the post the user re-hydration process is the key for hybrid search results for which Dirsync is a key requirement . However when we look at sign in experience for a user from on-premise while he accesses resources in SharePoint online, he would need to type in his user name manas@mbspoincloud.comand password every time . He can of course choose remember me and save password but he still lacks the Single Sign In experience in SharePoint Online.
In this post we will be configuring Identity Federation to provide single sign on experience to the users. Steps below talks about configuring a single ADFS server, of course the best practices would be to deploy ADFS server in a farm and for extranet users configure ADFS proxy. With the steps below Single sign on experience will be available to only intranet users, of course you can expose the ADFS STS endpoint to Intranet so that intranet users can still authenticate while they are not logged in to company’s intranet . So let’s take a look at what is required when you would want to configure ADFS and provide the single sign on experience.
Your on –premise domain has already been added and verified following the steps in part 1 of this post. Following are the key requirements for ADFS install.
· Active Directory Domain must be at least in Windows 2003 mixed or native mode.
· You should have a Windows 2008 server or Windows server 2008R2 to install and configure ADFS.
· You need to download ADFS installer from https://www.microsoft.com/en-us/download/details.aspx?id=10909
· You need to create “A” record for the STS endpoint for your on –premise ADFS server
Install Active Directory Federated Services 2.0 (ADFS 2.0)
Post downloading the installer execute AdfsSetup.exe.
1. In the Open File – Security Warning dialog box, click Run.
2. On the Welcome to the ADFS 2.0 Setup Wizard page, click Next.
3. On the End-User License Agreement page, select the I accept the terms in the License Agreement check box, and then click Next.
4. On the Server Role page, review the two options for Federation server and Federation server proxy. Verify that Federation server is selected and then click Next.
5. On the Install Prerequisites Software page, review the prerequisites list and click Next.
6. On the Completed the ADFS 2.0 Setup Wizard page, verify that the Start the ADFS 2.0 Management snap-in when this wizard closes check box is not selected, and then click Finish.
The next key task would be to obtain a certificate. You can choose to procure a certificate from a public certification authority or use a domain certificate if you have the infrastructure. For this example I have a certification authority configured on-premise. In case you do not have a certification authority configured in your on –premise domain you can generate a certificate request and procure a certificate from public certification authority.
Create or Procure a SSL Certificate
On the machine where ADFS 2.0 has been installed you need to follow the steps below.
Open Internet Information Services (IIS) Manager. In the Navigation pane, click local machine name .In the Results pane, under IIS, double-click Server Certificates.
In the Actions pane, click Create Domain Certificate.
In the Request Certificate window, on the Distinguished Name Properties page. You can request a wildcard certificate for your domain *. mbspoincloud.com Fill information in the Organization, Organizational unit, City/locality and State/province fields and click Next.
On the Online Certification Authority page, Under Specify Online Certificate Authority, click Select and choose the certification authority for your domain. Type a friendly name to identify your certificate and click on Finish.
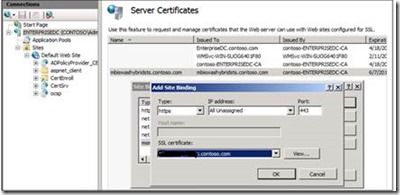
The next task would be to assign the Certificate to the Default Web Site.In the Navigation pane in IIS manager, expand local machine name select Sites and then select Default Web Site. In the Actions pane, choose Bindings. In the Site Bindings window, click Add.
In the Add Site Binding window, click the Type drop-down list box and then click https. From the SSL certificate drop-down list box select the certificate you created above.
Once certificate is installed properly you can proceed with the AD FS configuration. To launch the AD FS configuration wizard, click Start, click Administrative Tools, and then click ADFS 2.0 Management. In the ADFS 2.0 management console, in the Results pane, click ADFS 2.0 Federation Server Configuration Wizard. On the Welcome page, verify that Create a new Federation Service is selected and then click Next.
On the Select a Stand-Alone or Farm Deployment page, click the Stand-alone federation server radio button and then click Next.
On the Specify the Federation Service Name page, verify that SSL certificate and Federation Service name and then click Next.
On the Ready to Apply Settings page, review the configuration and then click Next. On the Configuration Results page, review the results and click Close. Successful configuration of ADFS setup would look like the prinstscreen below.
Installation of the Microsoft Online Services Module for Windows PowerShell
Now that we have installed ADFS 2.0 we have to establish a trust with Office 365. To do so we would need to install the below components.
Install the Microsoft Online Services Sign-In Assistant : The Microsoft Online Services Sign-In Assistant provides end user sign-in capabilities to Microsoft Online Services, such as Office 365 and is a pre-requisite for Azure Active Directory module for powershell. Download the Microsoft Online Services Sign-In Assistant from https://www.microsoft.com/en-us/download/details.aspx?id=28177
Windows Azure Active Directory Module for Windows PowerShell. In order to convert your on-premise domain to federated and establish a trust with Office365 you would need Windows Azure Active Directory Module for Windows PowerShell . As mentioned in https://technet.microsoft.com/en-us/library/hh967619.aspx you can use the cmdlets to accomplish Windows Azure AD tenant-based administrative tasks such as user management, domain management and for configuring single sign-on. Once you have installed the Sign in assistant you can download Azure Active Directory Powershell from https://g.microsoftonline.com/0BX20en/229
Once downloaded you can execute AdministrationConfig-EN.msi. On the Welcome to the Microsoft Online Services Module for Windows PowerShell Setup page, click Next , follow the instructions and complete the Setup.
Convert your On-premises domain to Federated Domain
If you have chosen to add a shortcut you should see PowerShell shortcut on the desktop. In the Windows PowerShell prompt, type the following command and then press Enter.
Connect-MSOLService
In the Enter Credentials window, enter the user name and password of your Office 365 Global Administrator
Run the following command (this command prompts for the Host name of your ADFS Server).
Set-MsolADFSContext
Execute the following command, where the domain should be your on premise domain.
Convert-MSOLDomainToFederated -DomainName mbspoincloud.com
Once the domain has been converted to federated, you should see a message “Successfully updated mbspoincloud.com” domain message on your screen.
In case you see an error while the conversation is happening, browse to the following folder location to review the log C:\users\userAccount\documents\MicrosoftOnline. Open the latest MSOL-IdentityFederation-date log file. Review the log file and search for the word “error” to narrow your search on what problems are occurring.
Now any on-premise user should be able to leverage single sign on experience . Note since I have not shared the steps to publish ADFS end point to Internet which has best practices around ADFS proxy this setup will only be accessible to users within the company’s intranet . If user manas@ mbspoincloud.com now browses to SharePoint Online site collection from company’s intranet (https://<tenantdomain>.sharepoint.com )and types in his username he should see the message “Redirecting ..We’re taking you to your organization sign-in page.”
The sign in should now work and user should be able to access the SharePoint Online Site collection. Now you notice the difference that the same user is able to seamlessly sign in without additional password prompt because of IdP (Identity Provider) and RP (Relying Party) trust that we have setup to provide end user with Single Sign on experience. Once the user signs and clicks on search drop-down list box he should be able to have the same search experience. The search result should be displayed from both verticals (online, on-premise) identical to image below.
I have shared Microsoft Threat management Gateway (TMG) as Reverse proxy for this post . We are testing additional reverse proxy and I would post the test results shortly in my next post.
POST BY : MANAS BISWAS [MSFT]
Comments
Anonymous
March 08, 2014
I'd purely tell you all “awesome information”Anonymous
March 21, 2014
Hi Manas, Thank you for sharing the information. Question though, Were you able to configure Two-Way Hybrid configuration with SAML Authentication. So, in this case was your SharePoint On-Premise Extranet URL https://spweb.mbspoincloud.com setup to use NTLM or SAML authentication.Anonymous
April 13, 2014
Hello Sunny, My site collection is configured with NTM . It will not work with SAML users, and you are only going to be able to do hybrid with Windows users. This is because for hybrid you have to do a directory synchronization. As long as user rehydration process is working we are good . The user is determined based upon a directory synchronization of AD users and finding a matching user in the remote farm.